So please use one of these apps instead. They all used plaintext network transmission on Feb 10, 2019, but eventually they may be fixed or removed.
Download this APK file:
Drag and drop that file onto your Android Emulator to install the app.
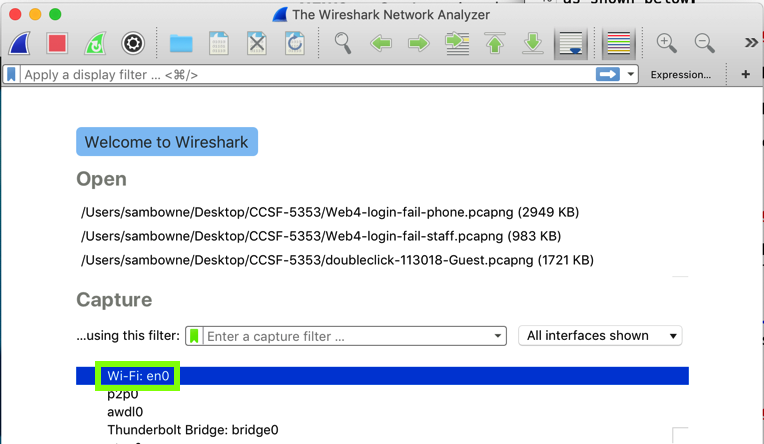
In the main Wireshark window, double-click the network interface that is being used to reach the Internet. On my system, it is "Wi-Fi: en0", outlined in green in the image below.

Wirehark starts displaying packets. At the top, in the Filter bar, enter this display filter:
http
On your Android device, in the vulnerable app, use the "Create Account" page to make an account.
Wireshark shows two POST requests, as shown below.
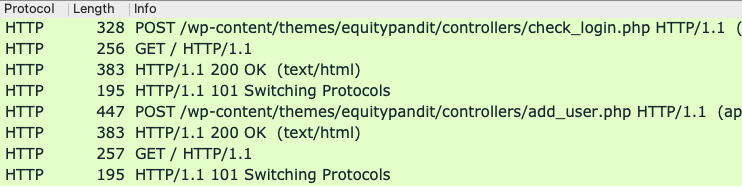
In the top pane of Wireshark, right-click the second POST request, the one ending in "add_user.php". and click Follow, "TCP Stream".
Troubleshooting
If you don't see any packets, try these fixes:
- Click the red square button to stop the capture
- From the menu, click Capture, Options
- Choose a different network adapter
- If the "Link-layer header" is set to "802.11...", scroll to the right and uncheck the monitor box
The request appears, containing your credentials, as shown below.
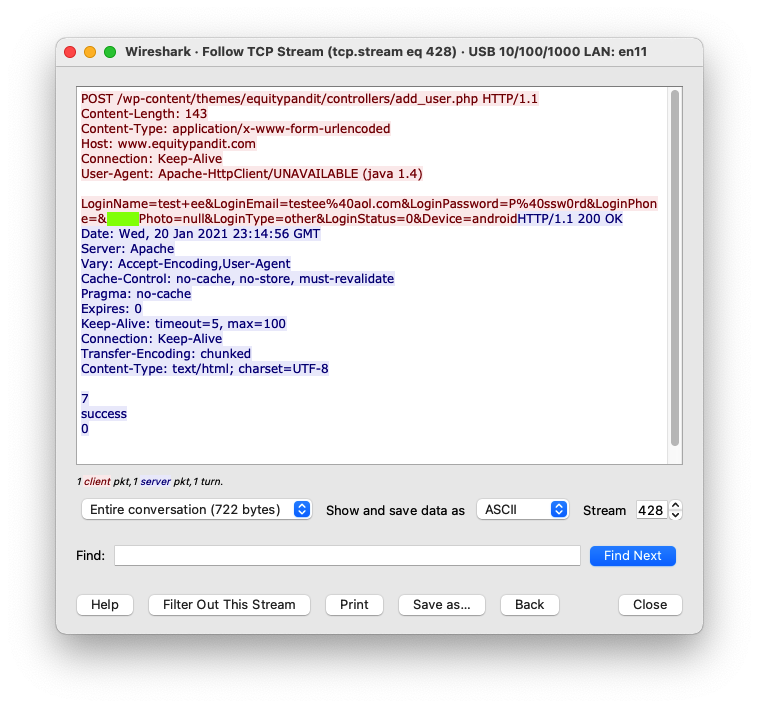
M 105: Parameter Name (15 pts)
Find the text covered by a green box in the image above. That's the flag.