M7: Observing the Delhaize Log (15 pts)
What You Need for This Project
- An Android emulator or device to test the app on
- Android Debug Bridge to observe the log
- You should have that already set up from previous projects
Windows Users
This project works in BlueStacks, but not in Nox.
Purpose
We'll install a ridiculously insecure
app and watch it throw passwords into
the log.
This is a very unsafe practice, because the log
is visible to all applications on the device,
so any malicious app could steal your
credentials from it.
Background
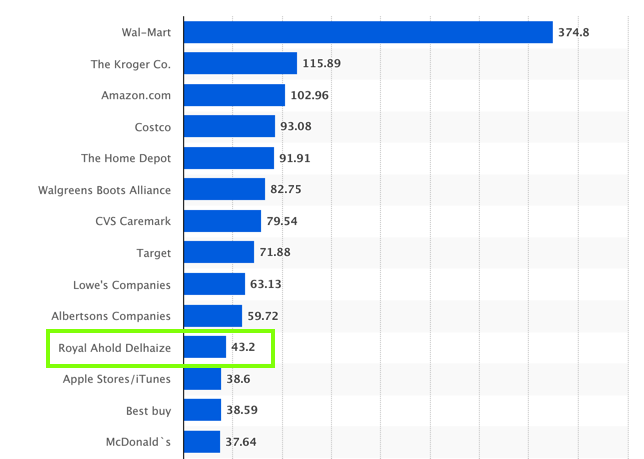
Delhaize is the 11th largest American retailer,
based on
2017 U.S. retail sales,
as shown below.
Responsible Disclosure
I notified Delhaize of this problem
in 2017
but they haven't fixed it yet,
as of Jan 14, 2019.
Start VMware
Always launch your Kali virtual machine before
you start Genymotion, to avoid VirtualBox networking
errors.
Installing the Vulnerable App
On your Android device, in Google Play,
search for delhaize,
as shown below.

The app has over 100K installs,
as shown below.
Here's the exact version I used, in case
they ever fix this problem, which is
not likely.
Install the app.
Connecting to your Android Device with ADB
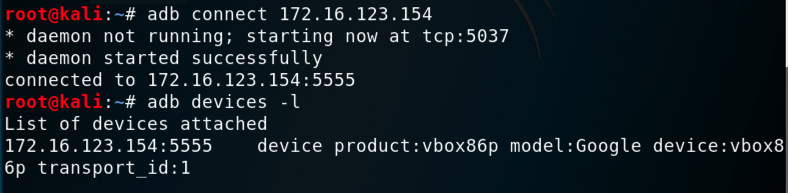
On Kali, in a Terminal, execute these commands,
replacing the IP address with the IP address
of your Genymotion Android device:
adb connect 172.16.123.154
adb devices -l
You should see your Genymotion device in the
"List of devices attached",
as shown below.
Viewing the Android Log
On Kali, in a Terminal, execute this command:
adb logcat
You see a lot of log messages scrolling by,
as shown below.
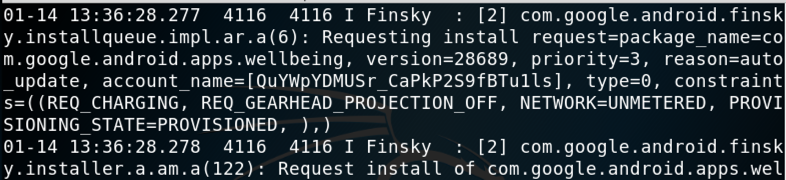
This is the syslog, shared by all apps on
the device. It's a public are, and should
not be used for private data.
Press Ctrl+C to stop the log messages.
Viewing Passwords in the Android Log
On Kali, in a Terminal, execute this command:
adb logcat | grep password
The terminal sits quietly, waiting for
log messages that contain "password",
as shown below.
Logging in to Delhaize
On your Android device, launch the
Delhaize app.
At the top left, click Menu,
as shown below.

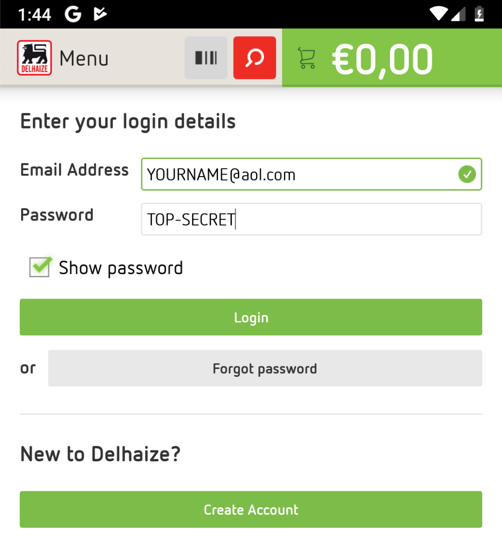
Click Login.
Enter test credentials, as shown below.
Click the green Login button.
In Kali, the credentials appear,
as shown below.
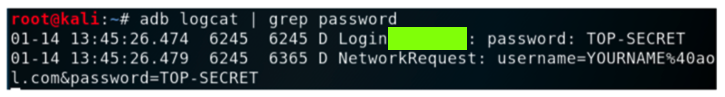
Find the text covered by a green box
in the image above. Enter it into
the form below to record your success.
M4: Recording Your Success (15 pts)
Use the form
below to record your success.
Posted 1-14-19 by Sam Bowne
Note for Windows users added 2-13-19
Converted to a CTF 2-28-19









