I tested this app:

2.1 MSTG-STORAGE-1: System credential storage facilities need to be used to store sensitive data, such as PII, user credentials or cryptographic keys.The Mobile Top 10 2016-M4-Insecure Authentication explanation says:
"...mobile applications should never store a user’s password on the device; Ideally, mobile applications should utilize a device-specific authentication token..."In 2018, the German chat platform Knuddels.de was fined €20,000 for storing user passwords in plain text.
The following steps can be used to determine how the application stores data locally on a jailbroken iOS device:I used a jailbroken iPhone running iOS 12.4.4 with no passcode.
- Trigger the functionality that stores potentially sensitive data.
- Connect to the iOS device and navigate to its Bundle directory (this applies to iOS versions 8.0 and above): /var/mobile/Containers/Data/Application/$APP_ID/
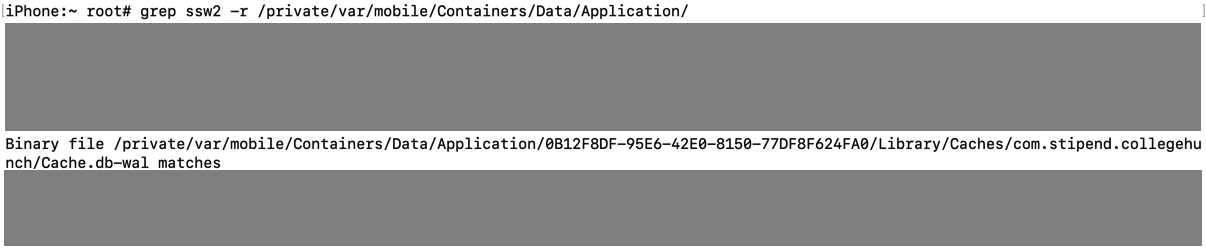
- Execute grep with the data that you've stored, for example: grep -iRn "USERID".
- If the sensitive data is stored in plaintext, the app fails this test.
I created an account. As shown below, the password was stored on the iPhone.