NFL said the app was now fixed.
We'll test the app to see if there are any remaining large security flaws we can find.
You will do four tests, and capture four images:
Search for "NFL App"
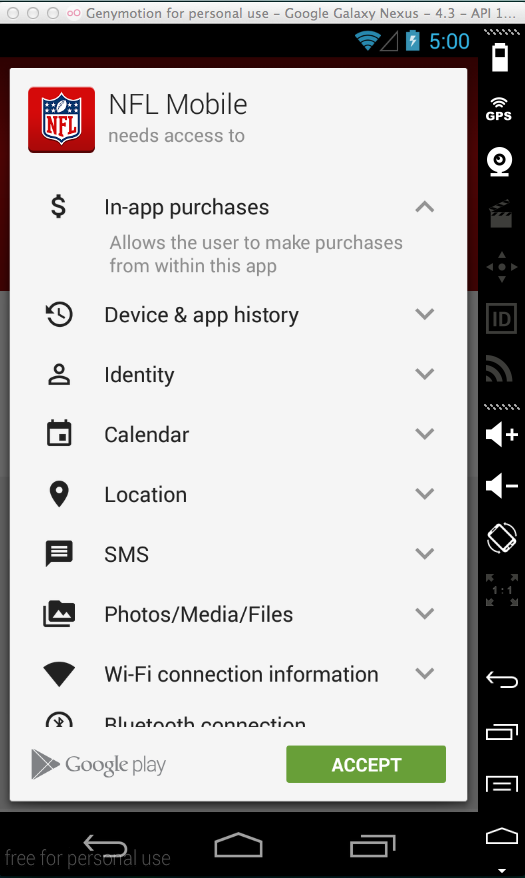
Install the app. Notice that it has a lot of permissions, including "in-app purchases", as shown below.

Accept the permissions and finish installing the app, as shown below.

Launch the NFL app.
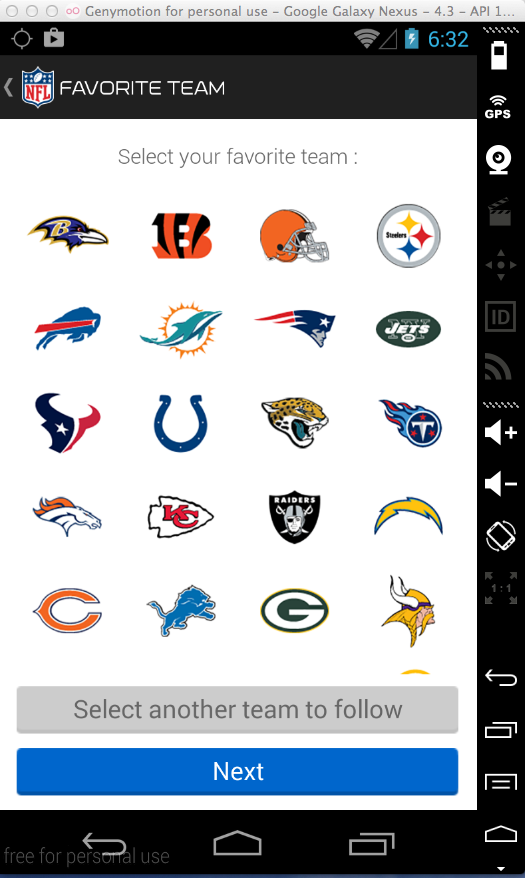
It will ask you to select a favorite team, as shown below.
Click a team and then click Next.
A box pops up saying it wants to send Push Notifications.
Click OK.
If a notice comes up. Click "OK, Got it.".
If box pops up about the Super Bowl, click Cancel.
You are now at the NFL App Home screen, as shown below.
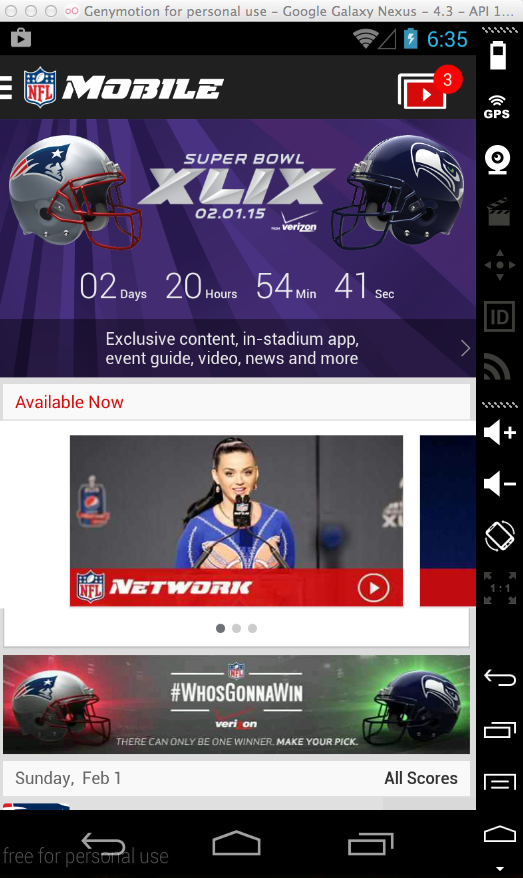
If you are not, refer to project 1x for the instructions.
Click Settings, as shown below.
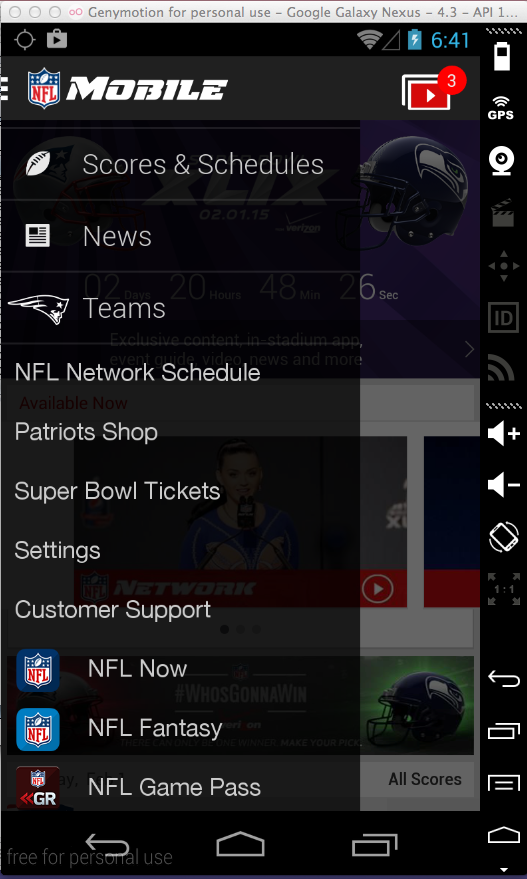
In SETTINGS, check "Sign-in to NFL.com", as shown below.
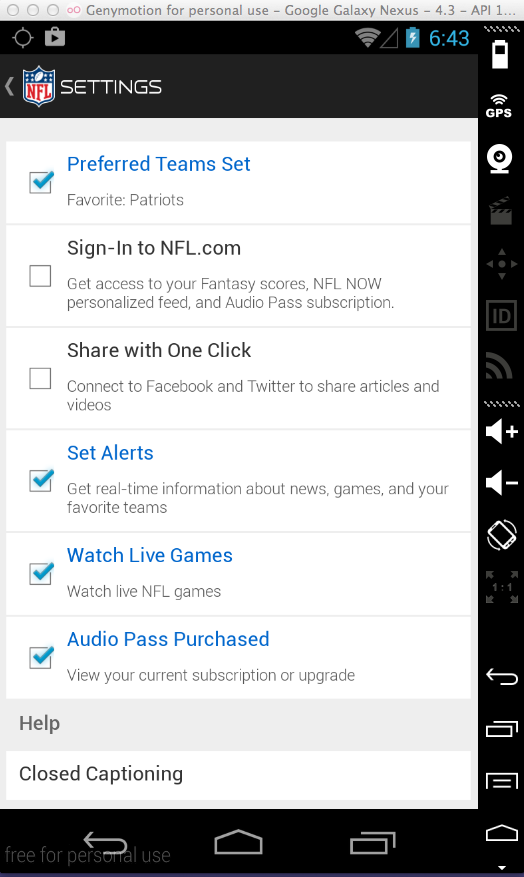
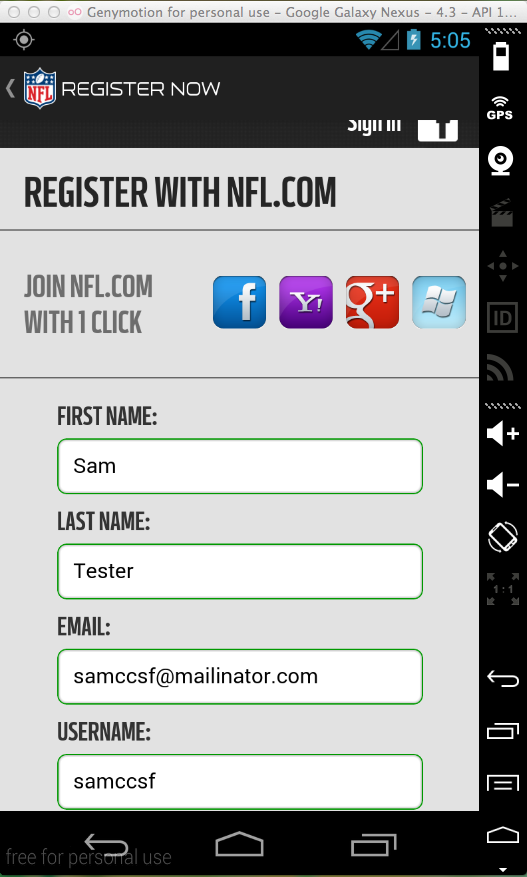
In the next screen, click "Register Now".
Register an account, as shown below.
Use a password you can easily remember, such as TOPSECRET123
Troubleshooting
When I was at Starbuck's on an unreliable wireless network, the App froze up a few times.To fix that, go to the Home screen, click the circle, open Settings, click Apps, and force the app to stop.
Then re-launch it.
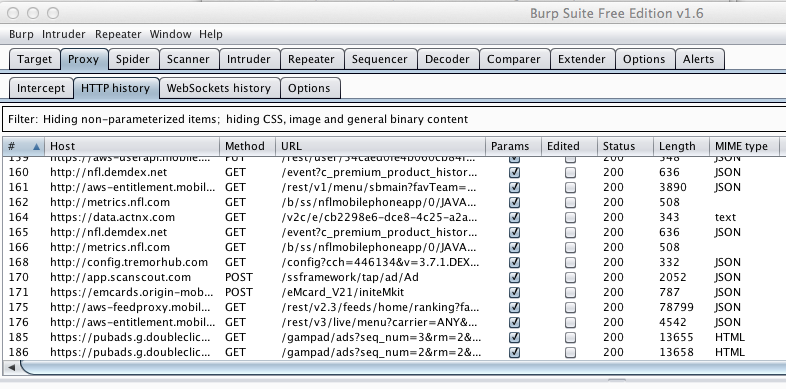
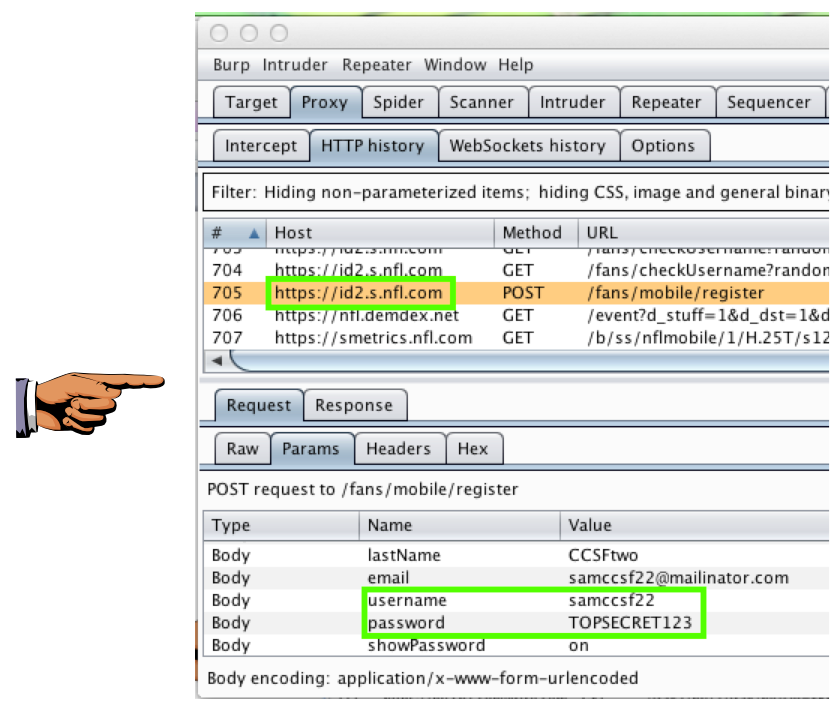
Capture an image like the one below that shows the password being sent, and that indicates whether it was sent via HTTP or HTTPS.
When I did it, it was using HTTPS, as shown below.
Save a full-desktop image. On a Mac, press Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 2xa", replacing "YOUR NAME" with your real name.
I didn't find any data in this insecure location.
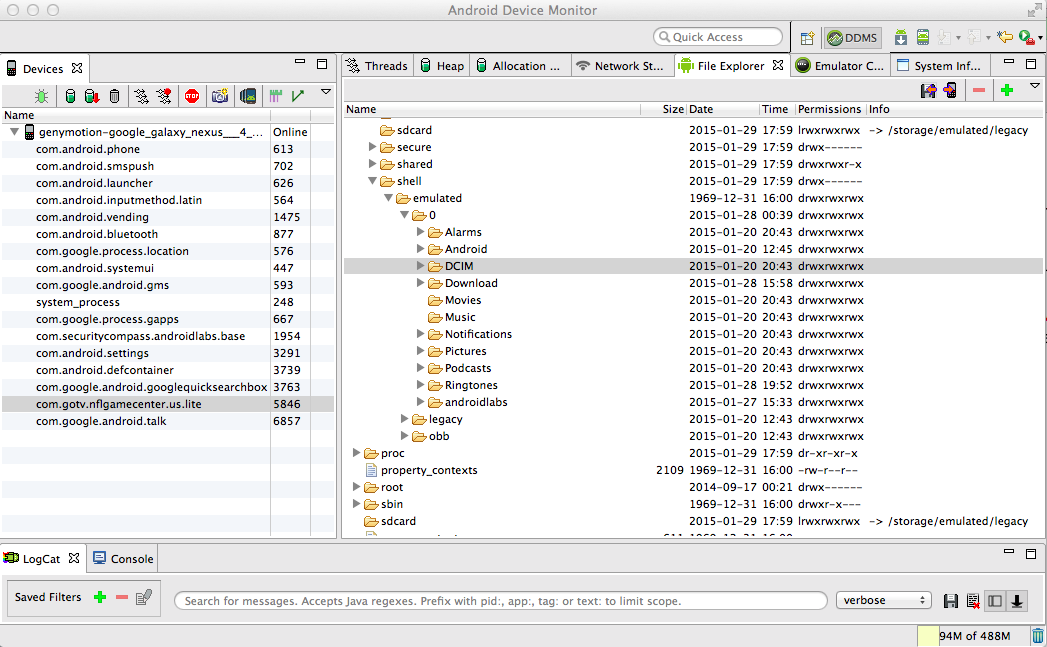
In the /data/data folder, find the nfl folder, as shown below.
Download all the data in that folder and look through it.
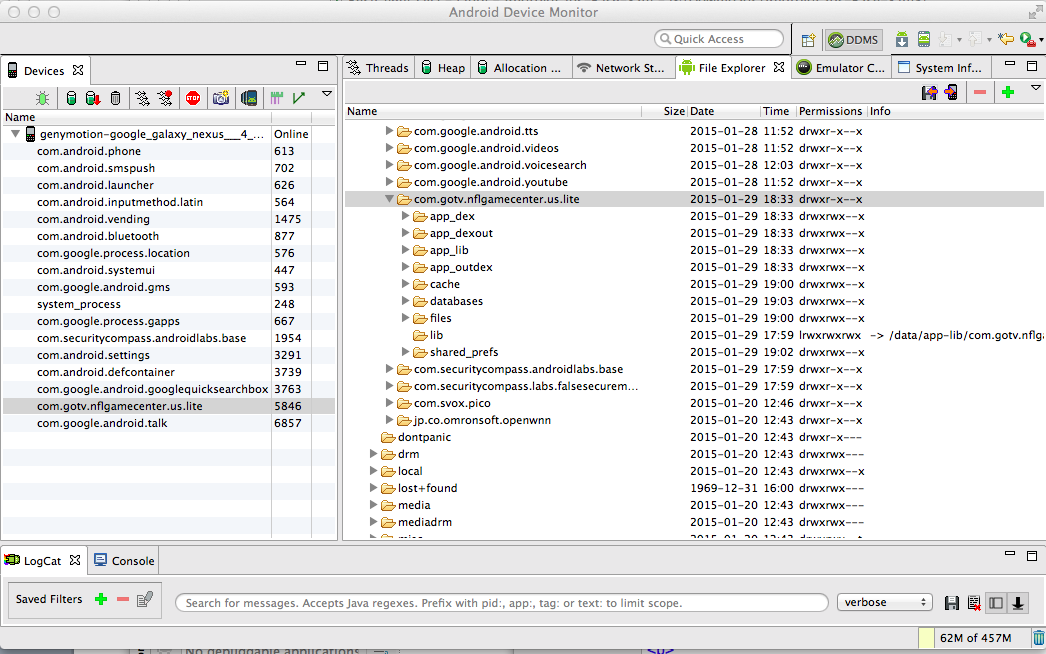
There are various files in there, but they all open well enough in a text editor to see the contents.
I didn't find any passwords in them.
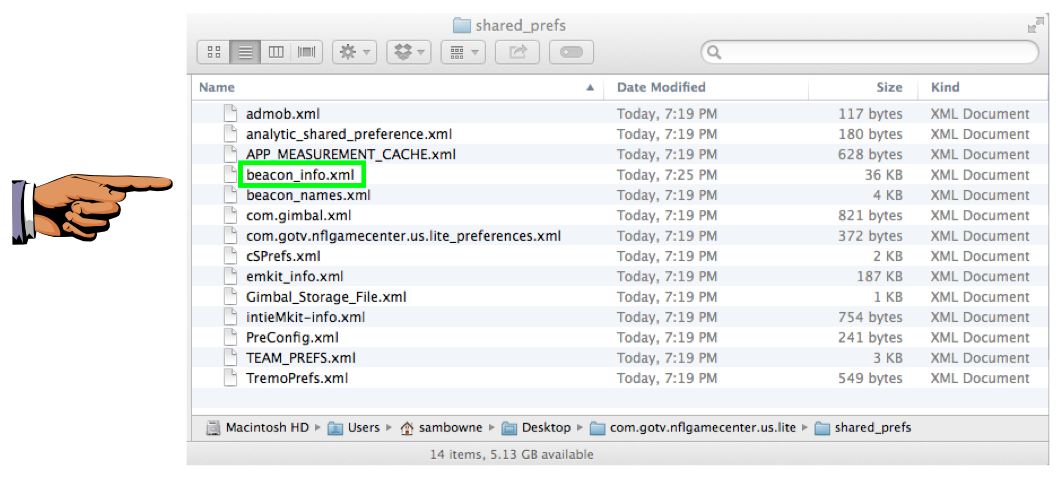
To show that you got the files, capture an image like shared_prefs folder. It may conain the file I highlighted, but it may not.
Save a full-desktop image. On a Mac, press Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 2xb", replacing "YOUR NAME" with your real name.
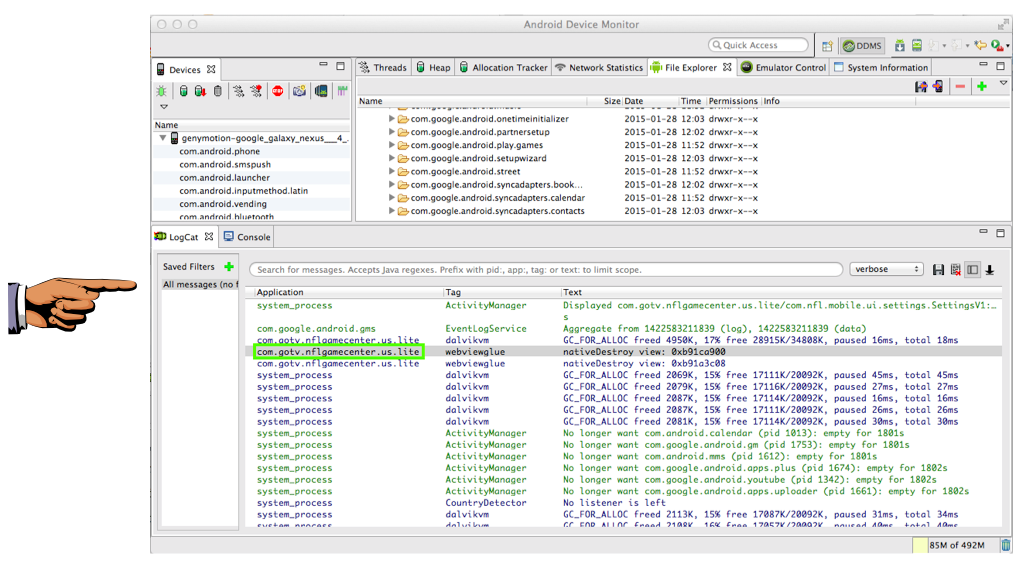
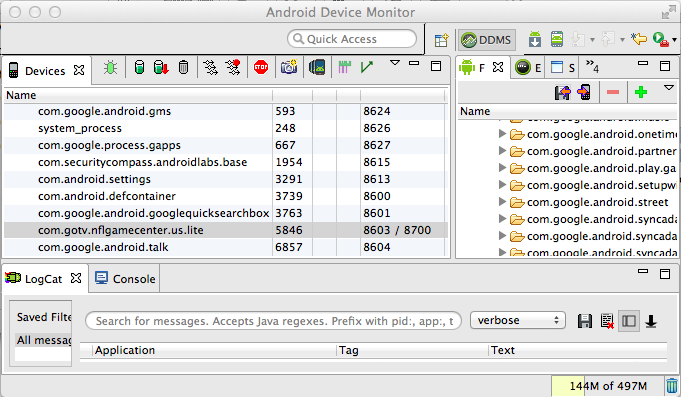
Look in the Application column to find events logged by the NFL app.
I didn't find anything troubling--all the logged events were generic, without anything sensitive.
Find a log entry by the NFL app, such as the one shown below, and capture that screen to turn in.
Save a full-desktop image. On a Mac, press Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 2xc", replacing "YOUR NAME" with your real name.
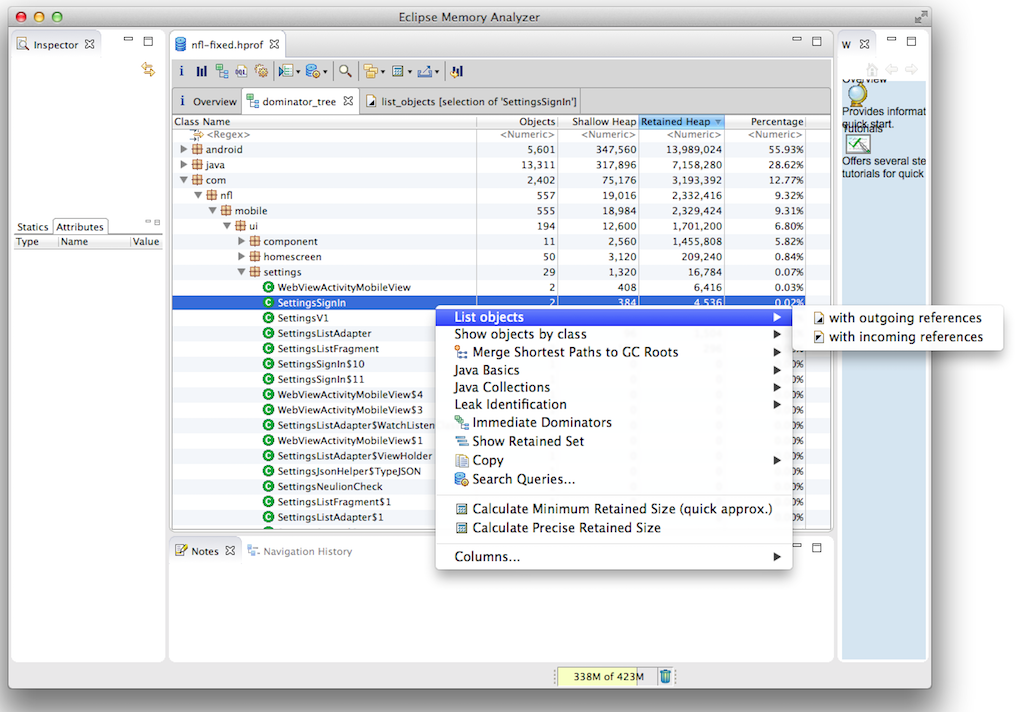
Convert the file and open it in Eclipse Memory Analyzer.
There are a lot of objects in the NFL container. Look through them a bit and see if you can find anything interesting.
The only thing I found that looked hopeful was SettingsSignIn, as shown below.
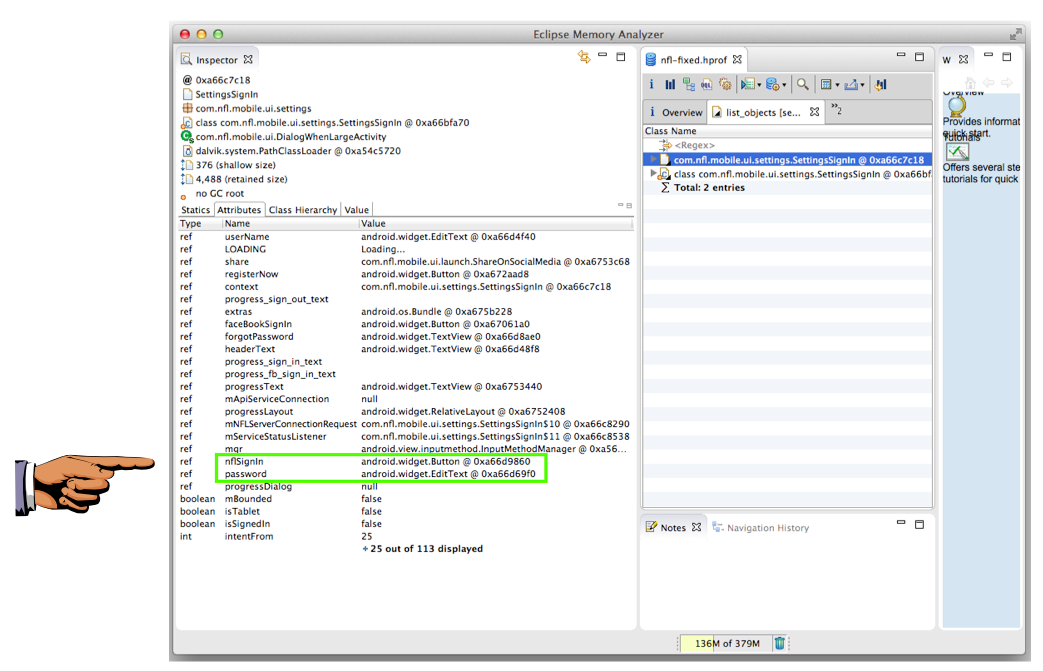
Find the RAM contents labelled nflSignIn and password, and capture an image, as shown below.
But notice that the password is not visible, instead, only a reference to a widget.
Save a full-desktop image. On a Mac, press Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 2xd", replacing "YOUR NAME" with your real name.