
If I were Google, I wouldn't let an app offer in-app purchases with this outrageously poor security. Perhaps at some point they will be humiliated enough to demand that.
Open Google Play and search for Stitcher. Install it, as shown below.

The version I used was 3.8.0, but I greatly doubt they'll bother fixing this problem any time soon.
Start Wireshark. Begin sniffing on the interface that goes to the Internet on your computer.
In the filter bar, enter this:
frame contains stitcher
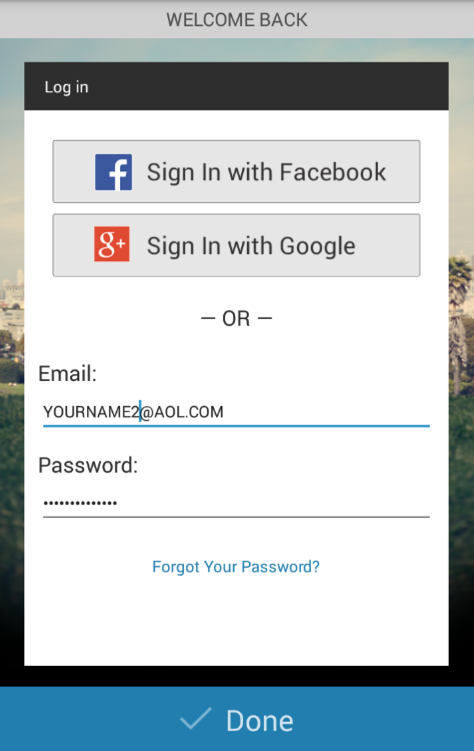
Enter test credentials containing your name, as shown below. Click Done.
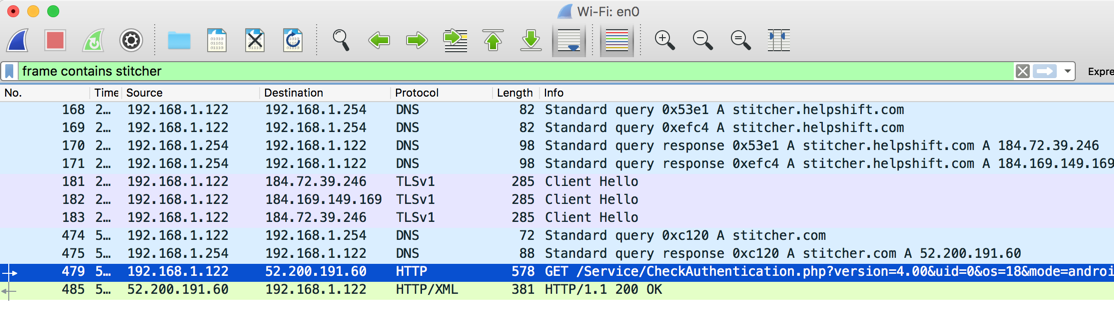
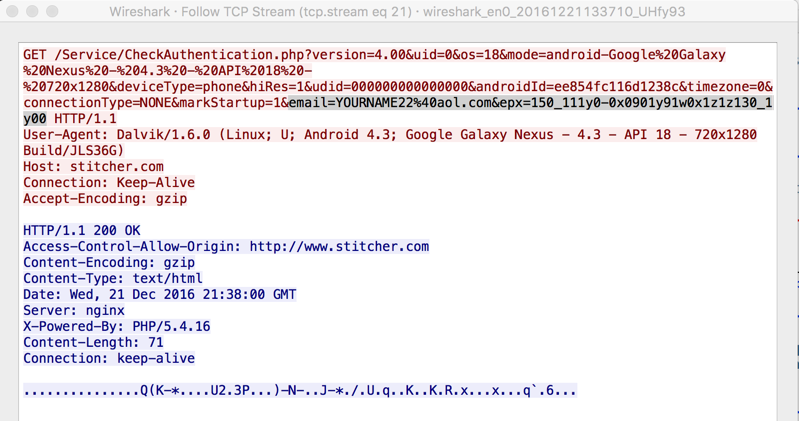
Wireshark shows an HTTP GET request going to /Service/CheckAuthentication.php, as shown below.
In Wireshark, from the menu bar, click Capture, Stop. Right-click that GET request and click Follow, "TCP Stream".
The request contains the email address in plaintext, and the password as a long series of letters and numbers, as shown below. The password is sent in the "epx" parameter, obscured in some manner, but is it really properly encrypted?
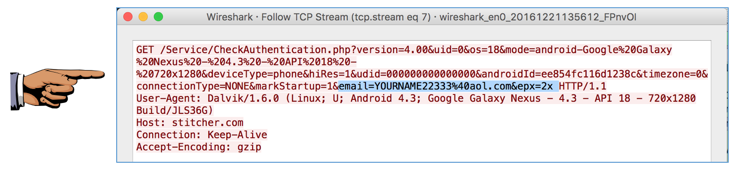
Restart Wireshark capturing, and log in with an email containing your name and a one-character password of:
aCapture the login in Wireshark, as shown below.
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 6", replacing "YOUR NAME" with your real name.
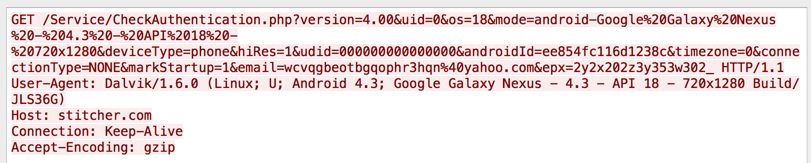
Do more examples as required to figure out the algorithm, and find the password I sent from the network capture shown below.
Password epx a 2x b 2y c 2z aa 2x2x ab 2x2y ac 2x2z aaaaaa 2x2x2x2x2x2x
Put the correct password in the body of your email message.