This project uses a far more powerful obfuscator named DashO. It's a commercial product, but there's a 15-day free trial :).
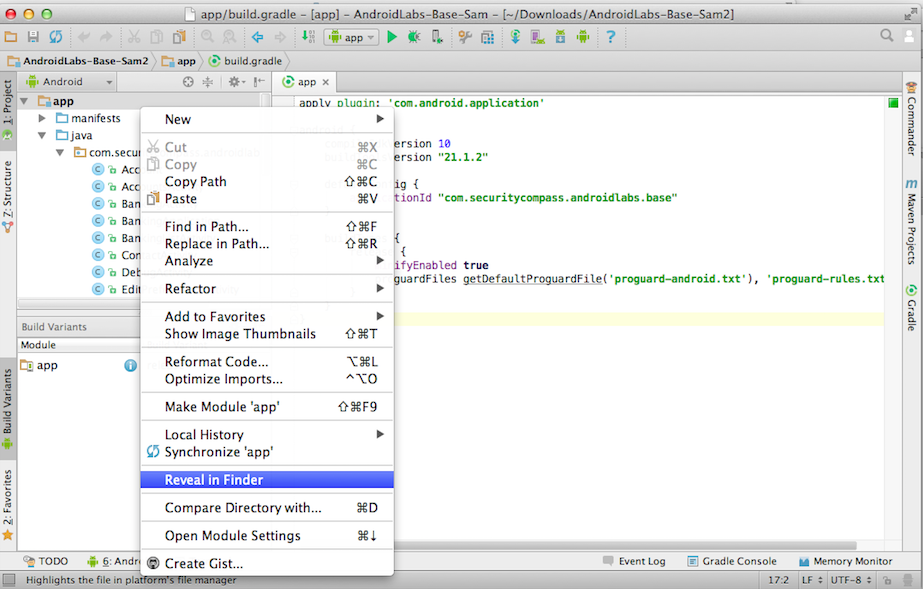
In the top left pane, right-click app and click "Reveal in Finder", as shown below.
(On a PC, I suppose the name of this item will be different.)

The "app" folder appears, as shown below.
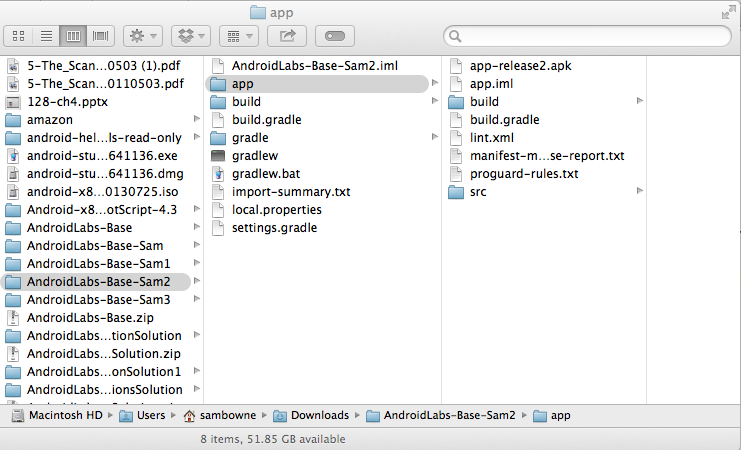
Notice that this folder also contains these items:
Click Build, "Make Module 'app".
https://www.preemptive.com/products/dasho
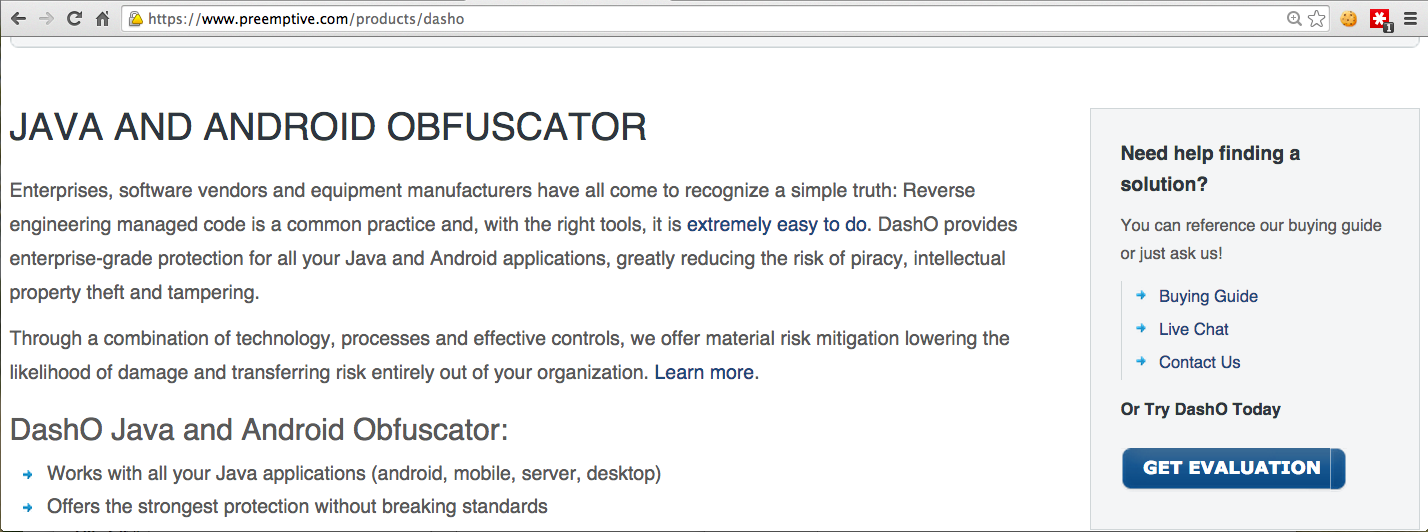
On the right side, click "GET EVALUATION", as shown below.
You will need to Register an account and log in. Then click Downloads and click Evaluations.
On the left side, in the "DashO Professional for Java" section, click "DOWNLOAD JAR".
Double-click the DashOProEval_7.5.1_setup.jar file.
Install the software with the default options.
On a Mac, open Applications. Open the DashO folder. Double-click "DashO Pro.jar".
On a PC, I assume clicking Start and typing DASHO will lead you to the correct file.
Agree to the agreement.
It asks for a serial number. Check your email for a message titled "Thank you for evaluating PreEmptive Solutions". The serial number should be in it.
If it does not, click File, "New Project", Wizard.
In the "Welcome to the New Project Wizard" page, click Next.
In the "Select Application Type" page, click "An Android application" and click Next.
In the "Select Android Project" page, accept the default build environment of Gradle.
Click the Browse... button and navigate to the folder containing your app, which you located earlier in these instructions.
Open the app folder.
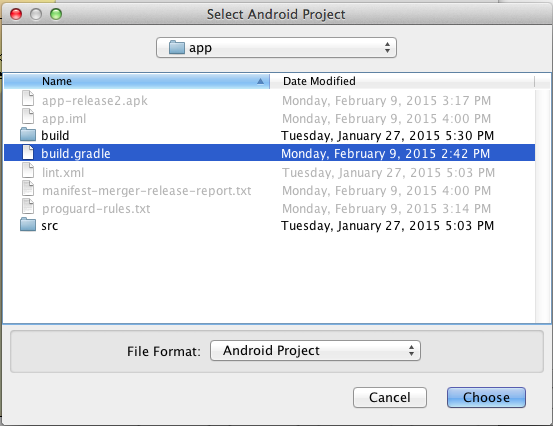
Click the build.gradle file, as shown below.
Click Choose.
In the "Select Android Project" page, click Next.
In the "Add Jars" page, click Next.
In the "Select Entry Points" page, click Next.
In the "Summary" page, click Finish.
The project opens in DashO, as shown below.
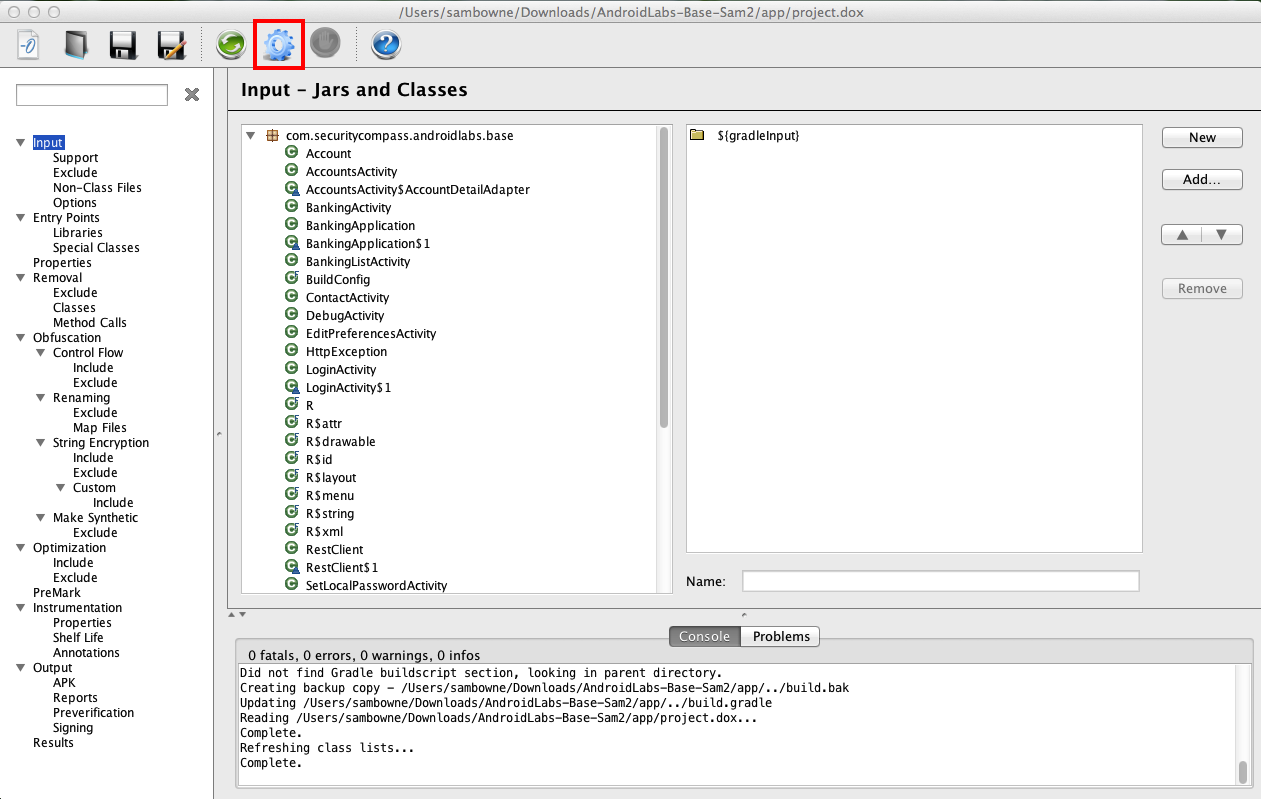
At the top of the window, click the gear icon, outlined in red in the image below.
A box pops up warning you that the obfuscated output will not run after a date 30 days in the future. Click OK to close it.
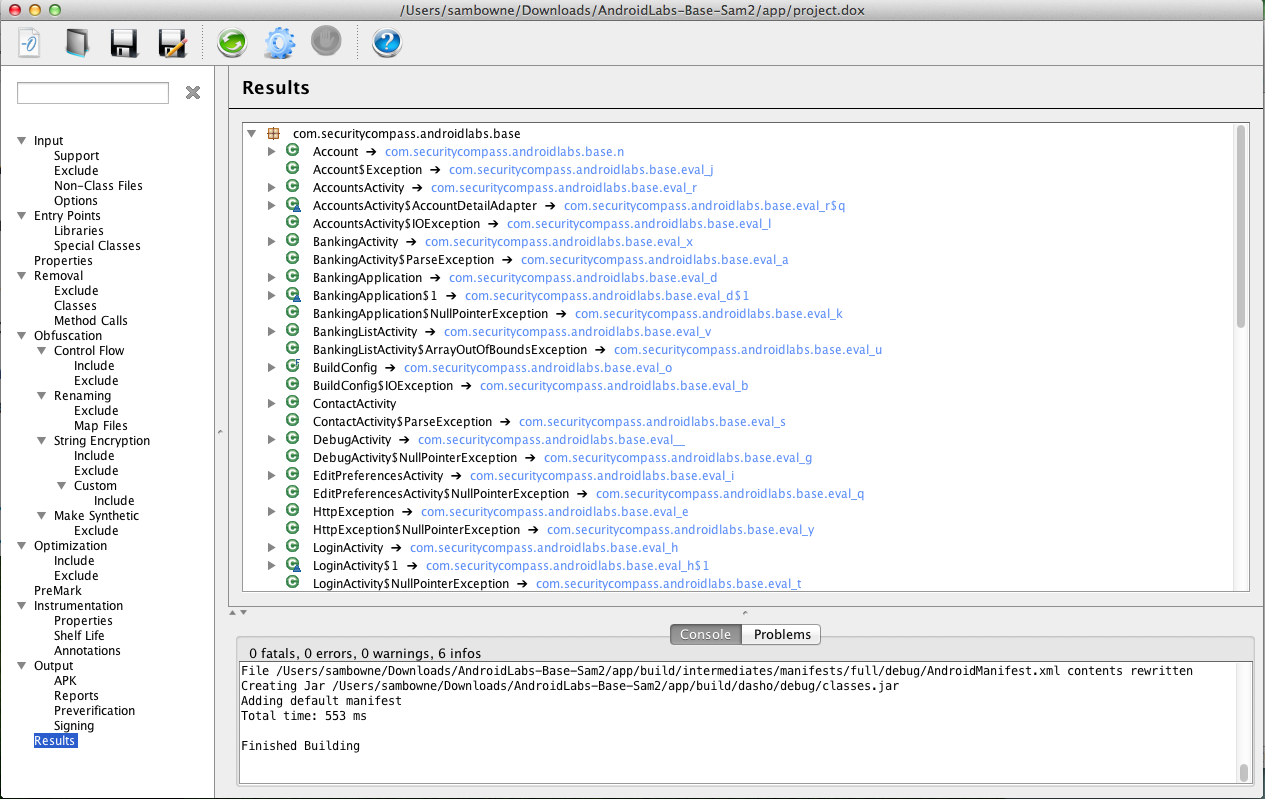
The top right pane shows the Results: DashO has renamed all the methods, as shown below.
Click Build, "Make Module 'app'".
In the "Generate Signed APK Wizard" page, click Next.
In the next page, click "Choose existing..." and navigate to the key you created previously. Fill in the key alias and password, as shown below, and click Next.
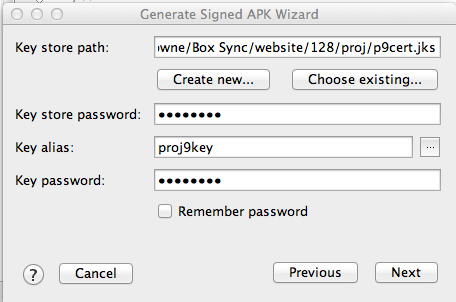
Click Finish.
A box pops up saying "Signed APK's generated successfully".
My apktool file is in my Downloads folder, so I made a subfolder there named p6x to put the APK file in.
In a Terminal or Command Prompt window, navigate to the folder containing the APK file.
Execute this command:
java -jar ../apktool_2.0.0rc3.jar d app-release-unaligned.apk
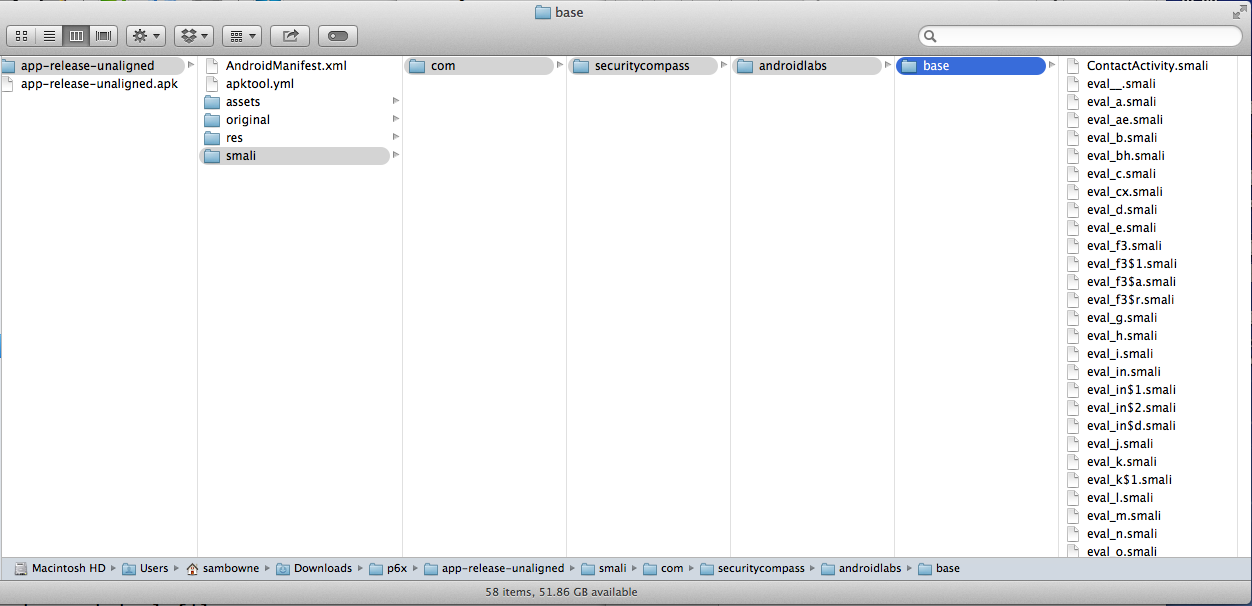
As you can see, almost all the filenames are now meaningless.
Look through the files and find one that is at least 2 KB in size. Open that file in a text editor.
When I did it, the eval_bh.smali file was 4 KB.
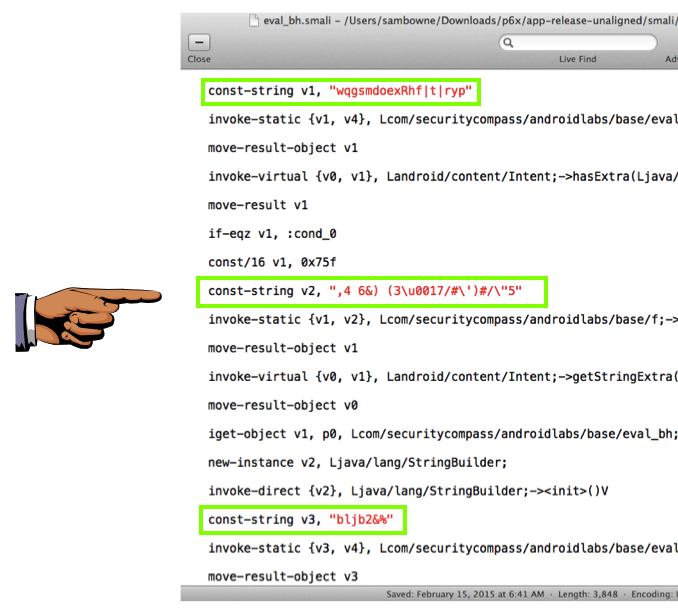
You should see "const-string" values which have been converted to unreadable ciphertext, as shown below.
Save a full-desktop image. On a Mac, press Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 6x", replacing "YOUR NAME" with your real name.
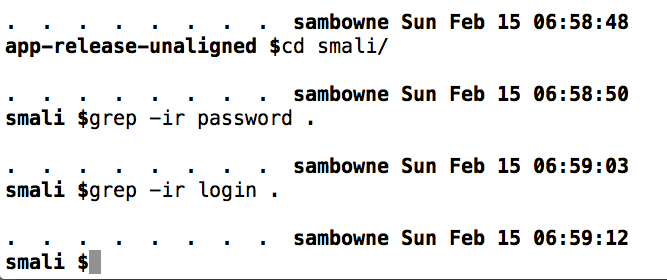
grep -ir password .