If hopper is not found, go here to get the free version:
https://samsclass.info/128/proj/com.stitcher.player-iOS7.0-(Clutch-2.0.4).ipa
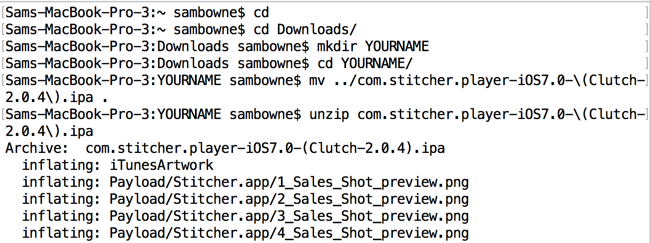
cd
cd Downloads
mkdir YOURNAME
cd YOURNAME
mv ../com.stitcher.player-iOS7.0-(Clutch-2.0.4).ipa .
unzip com.stitcher.player-iOS7.0-(Clutch-2.0.4).ipa

In the same Terminal window, execute these commands:
cd Payload/Stitcher.app
ls -l Sti*
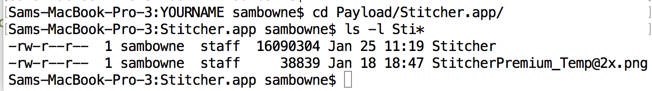
Navigate to the Stitcher app, which should be in a path like this:
~/Downloads/YOURNAME/Payload/Stitcher.app
A box pops up saying this is an ARM v7 file. Click Next.
Click OK.
Hopper opens, as shown below. Notice the named items, as labeled below.
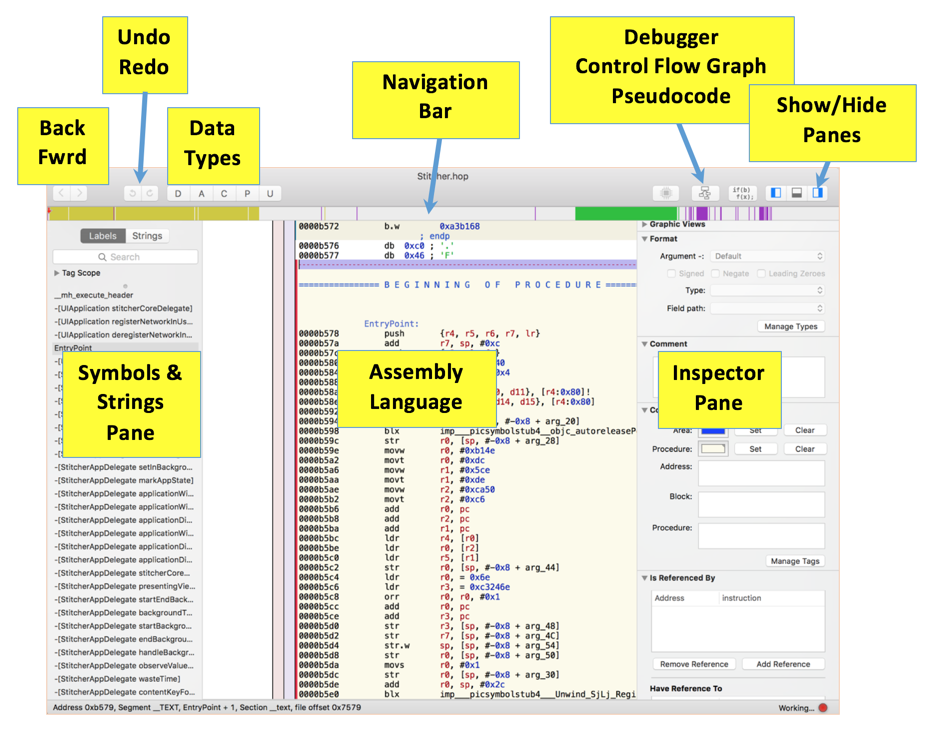
Hopper is big and complicated, but for now we'll only use a few of its simpler features.
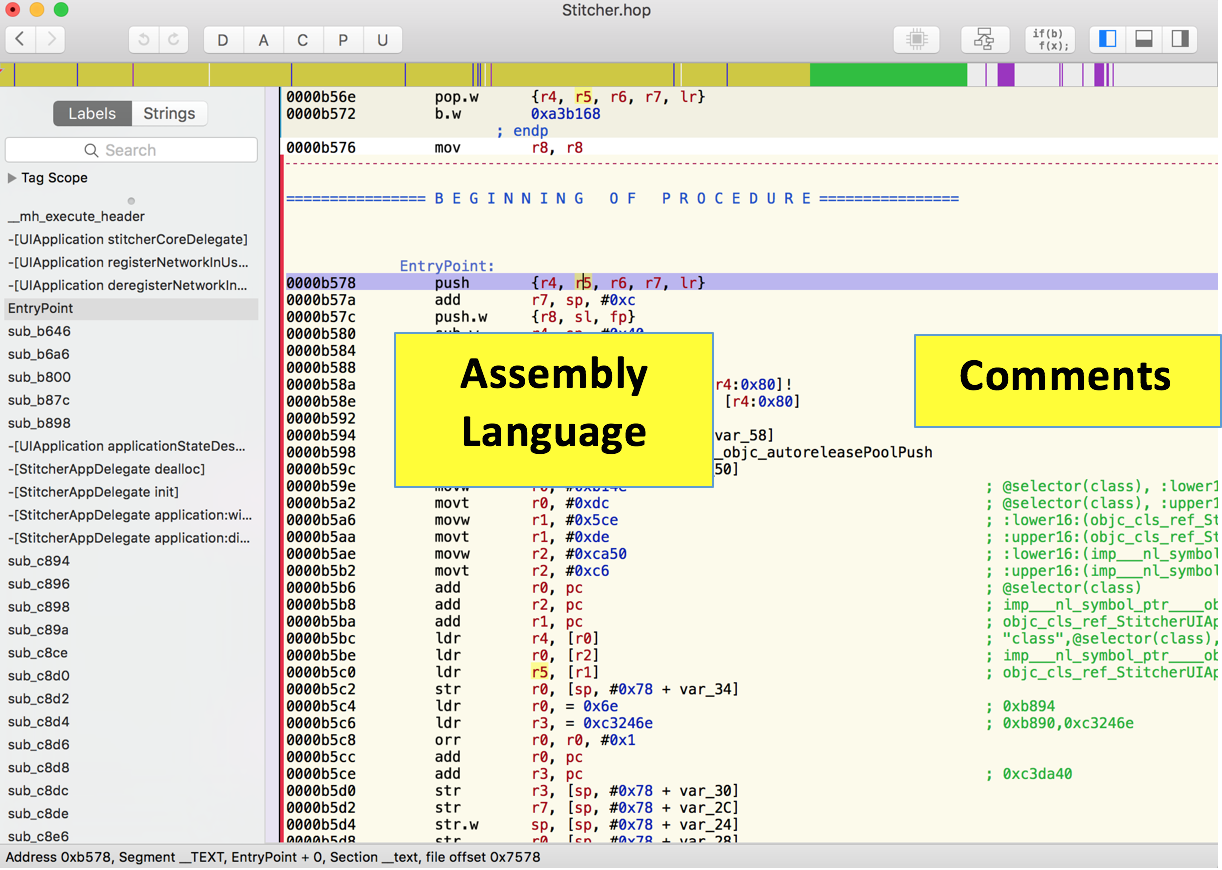
In its right pane, Hopper now shows assembly language instructions like "push" and "add" on the left, and helpful comments in green on the right, as shown below.
encrypt
Hopper shows the assembly language for this routine in the right pane, as shown below.
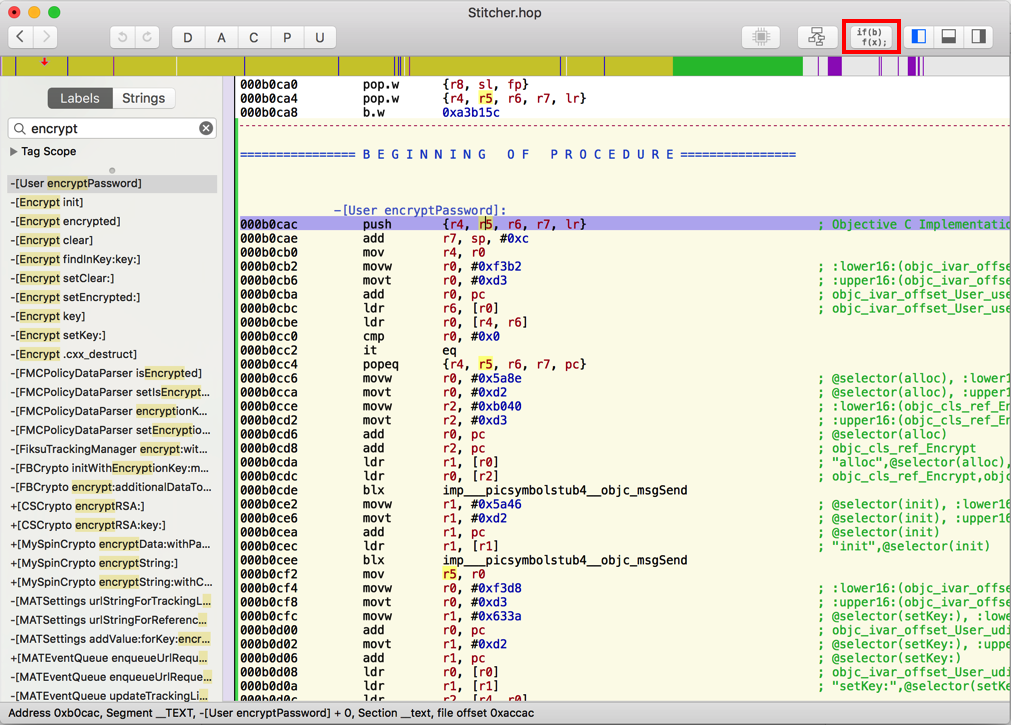
At the top right of the Hopper window, click the Pseudocode button (outlined in red in the image above).
Hopper translates the assembly code into C-like pseudocode, as shown below.
This stuff is easier to read, but still not very helpful.
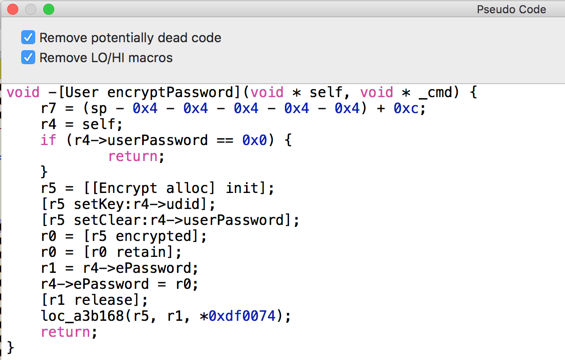
Close the "Pseudo Code" window and, in the left pane of Hopper, click the next method: -[Encrypt init].
Click the Pseudocode button again.
This pseudocode isn't very helpful either, as shown below.
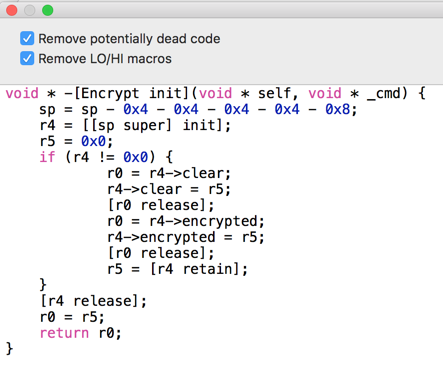
Continue generating pseudocode for each method until you get to -[Encrypt setClear].
This pseudocode is more interesting, as shown below.
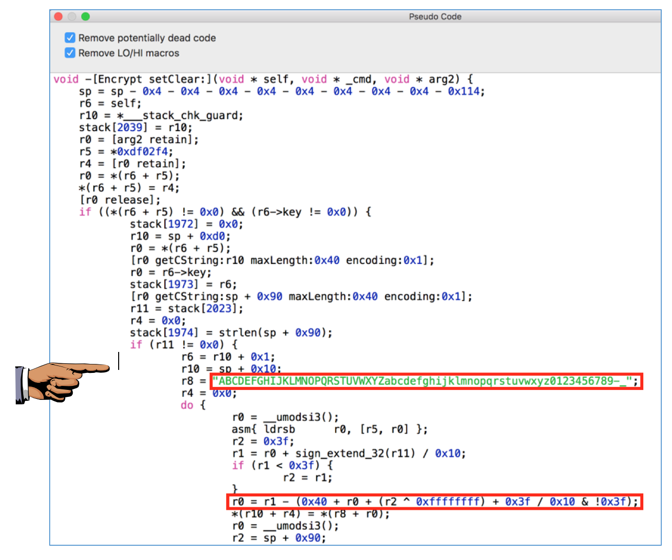
Notice the two lines outlined in red in the image above.
The first one defines a string of 64 characters including uppercase letters, lowercase letters, numbers, dash, and underscore. This looks like a lookup table of characters to use when encrypting.
The second one performs a calculation that loops through the numbers 0 through 63 (0x3f in hexadecimal).
It looks like the "encryption" involves shifting letters around a loop of those 64 characters, which is very similar to what the Android app did.
Capture a full-screen image.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 8a", replacing "YOUR NAME" with your real name.
A Quick Guide to Using Clutch 2.0 to Decrypt iOS Apps
Posted 1-25-17
Revised 2-2-17