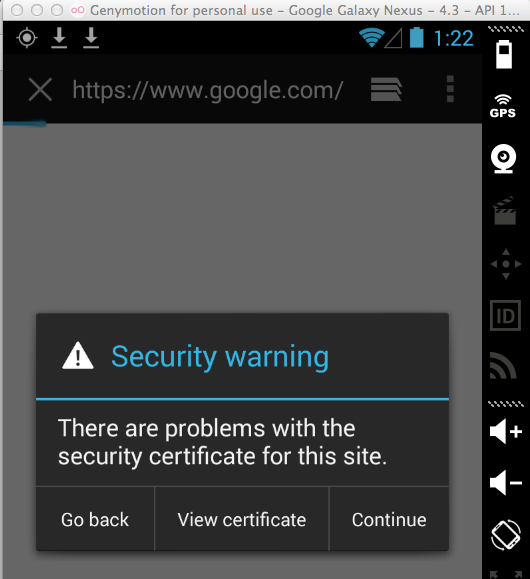
This practice may be illegal in the USA. Two American companies were sanctioned by the FTC in 2014 for making this same error:
FTC Final Orders with Fandango and Credit Karma Provide Guidance on Mobile App Security

So no HTTPS connections should be possible through the proxy.
Here's the app:

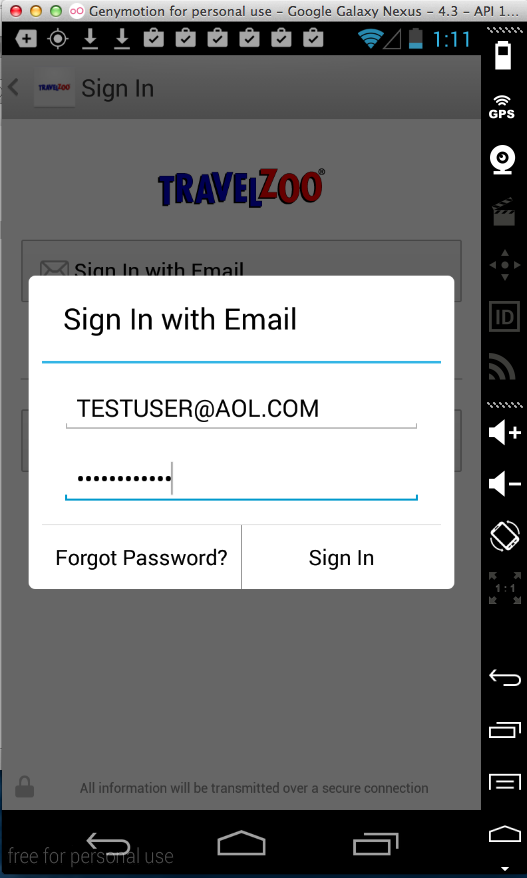
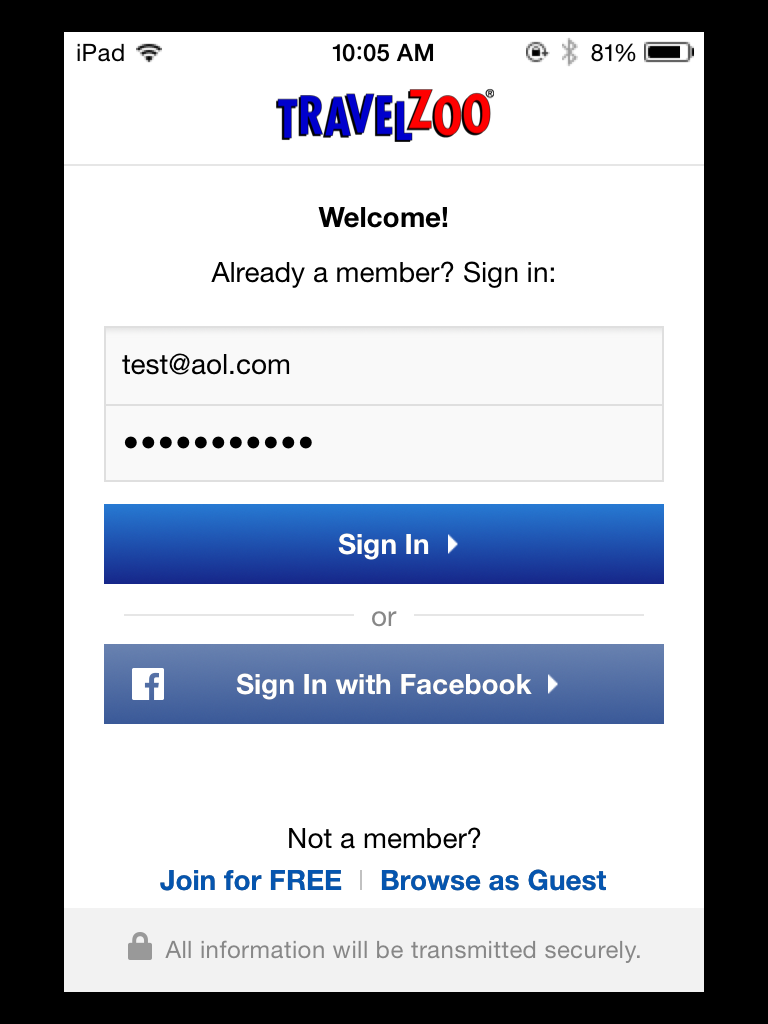
Sending test credentials:
Harvesting them from Burp via MITM attack:
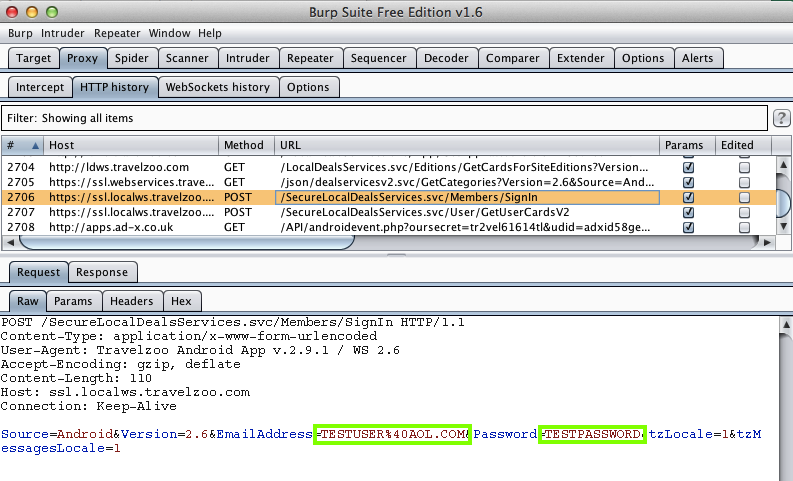
The MacBook Air is running Burp, a proxy listening on port 8080.
To test apps, I installed them on an iPad and connected it to the MacBook's wireless network. I configured the network settings to use the MacBook Air's IP address on port 8080 as an HTTP proxy.
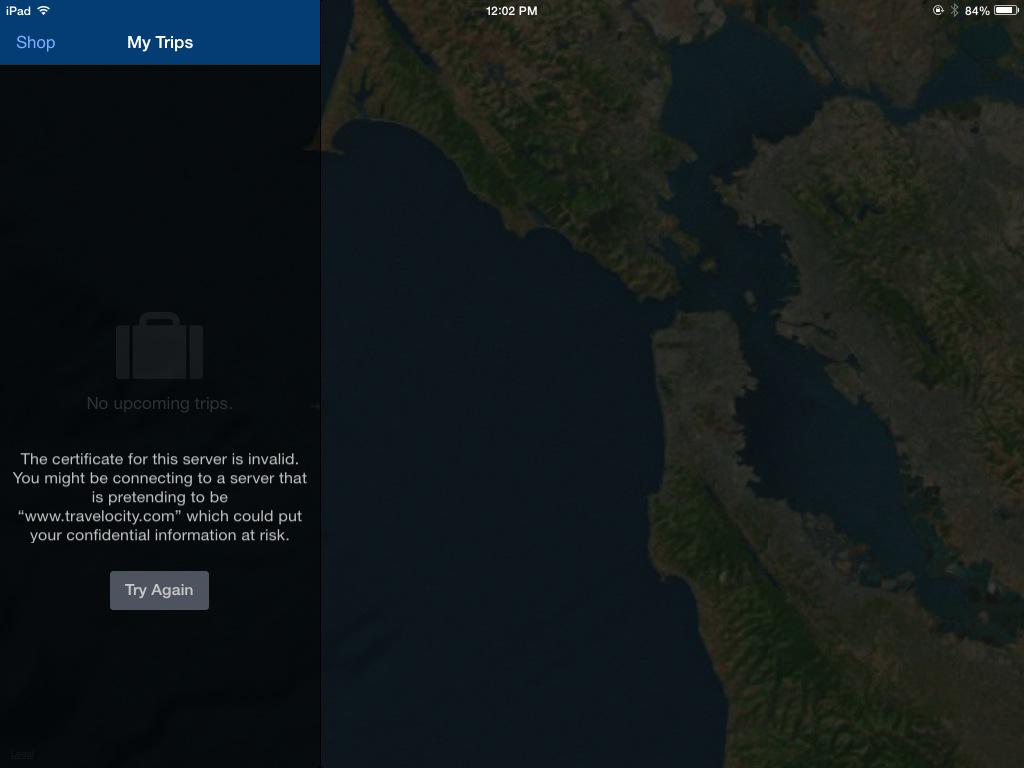
I did not install the PortSwigger certificate on the iPad, so HTTPS connections give a warning in a properly-written app, such as the Travelocity app:
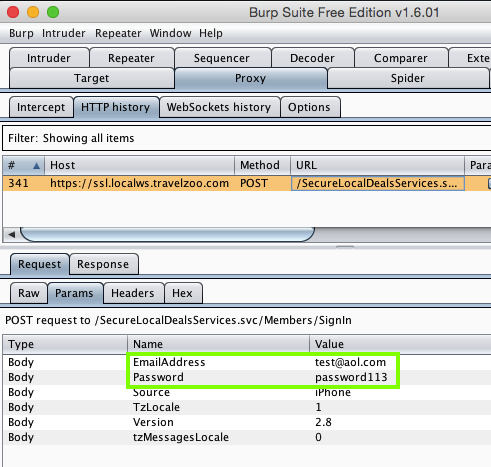
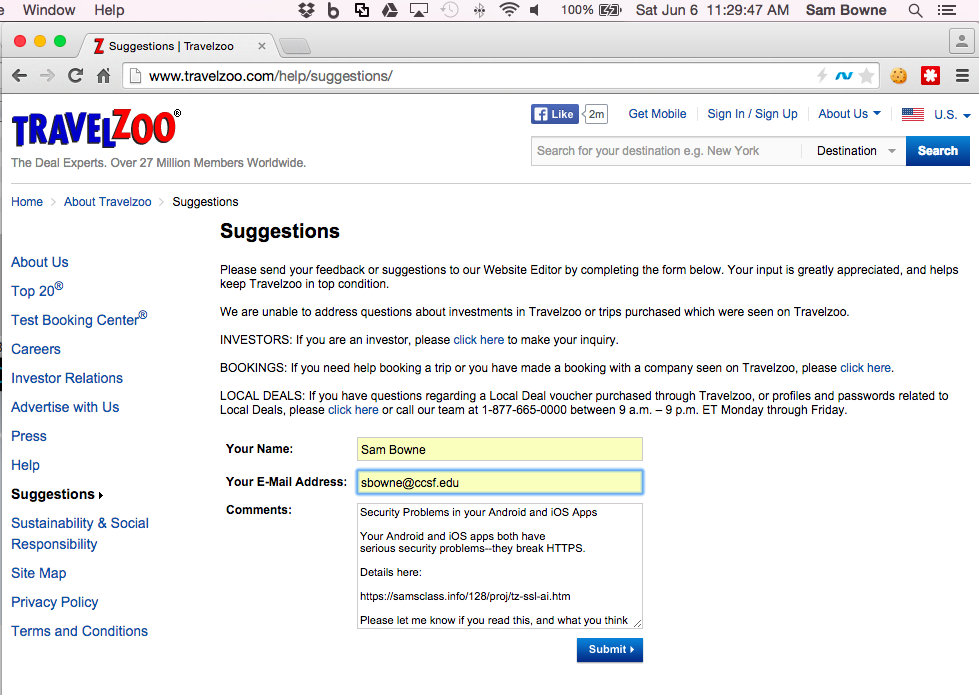
Here's the app I tested:
Sending test credentials:
Harvesting the data from Burp via MITM attack: