apt-get update
sudo apt-get install wget default-jdk -y
sudo su -
echo 'deb http://download.opensuse.org/repositories/home:/cabelo/Debian_9.0/ /' \
> /etc/apt/sources.list.d/home:cabelo.list
wget -nv https://download.opensuse.org/repositories/home:cabelo/Debian_9.0/Release.key \
-O Release.key
apt-key add - < Release.key
apt-get update
apt-get install owasp-zap -y
exit
owasp-zap
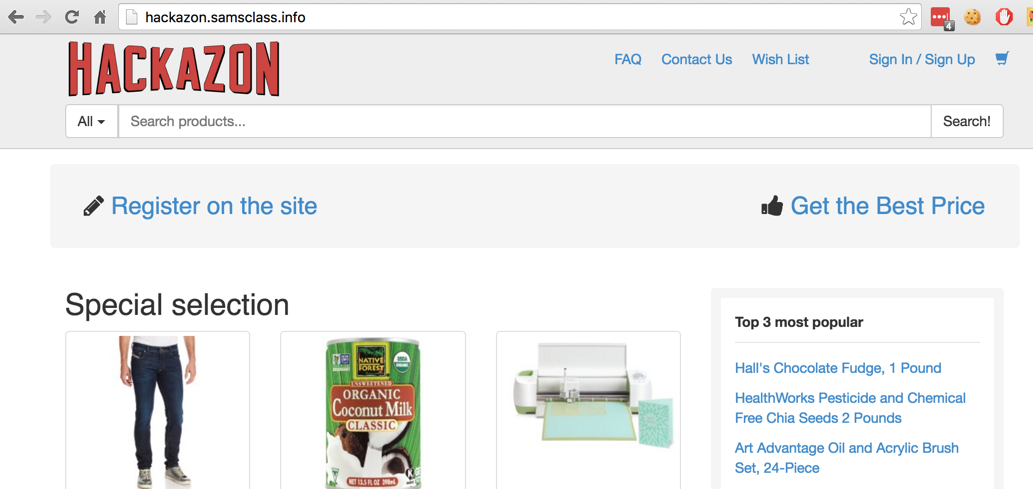
It's an imitation of Amazon, as shown below:

At the top right, click "Sign Up". Create an account using any username and password. Log out of Hackazon. Make a note of your username and password for later use.
A "Manage Add-ons" page appears. At the top right, click the X to close it.
The main ZAP window appears, as shown below.
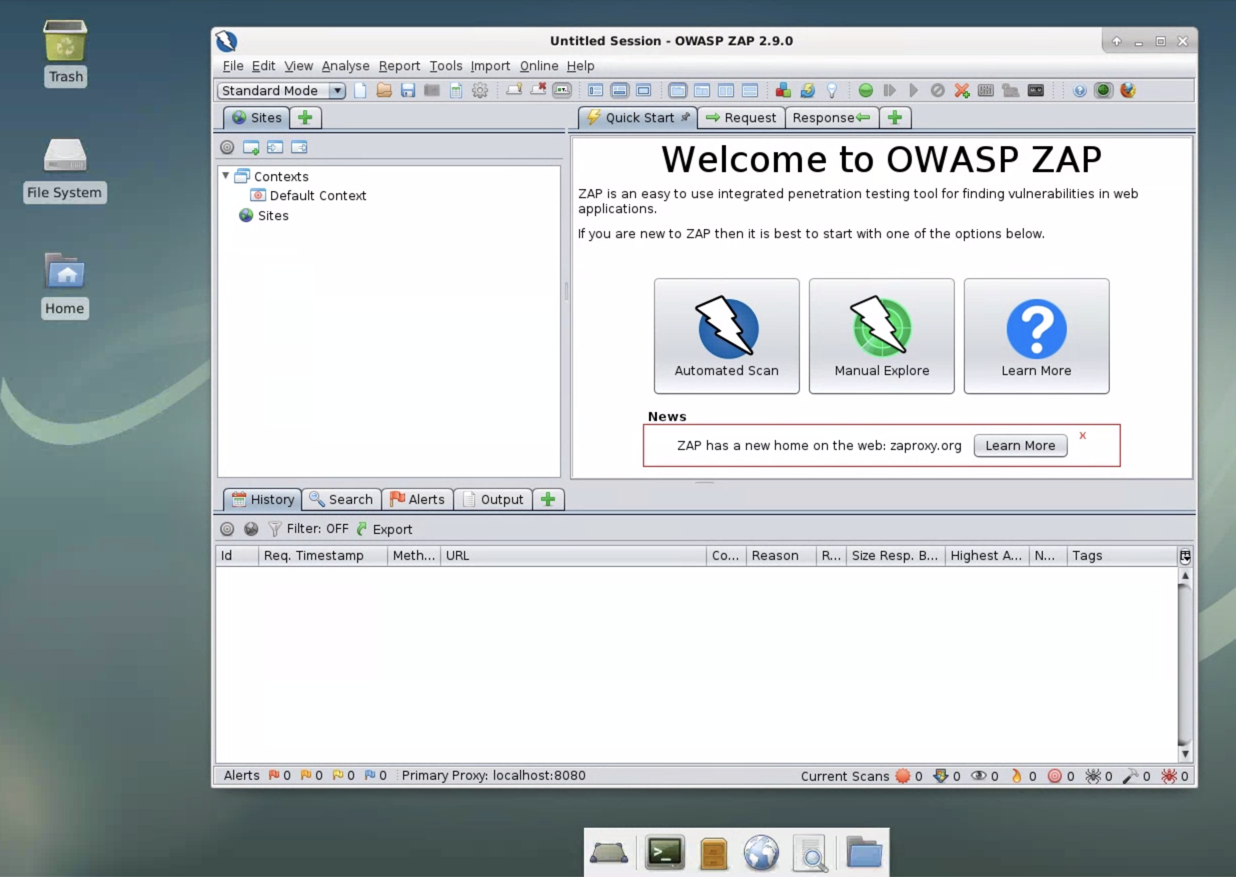
Click the "Automated Scan" button.
In the top right pane, enter a "URL to attack" of https://hackazons.samsclass.info, as shown below.
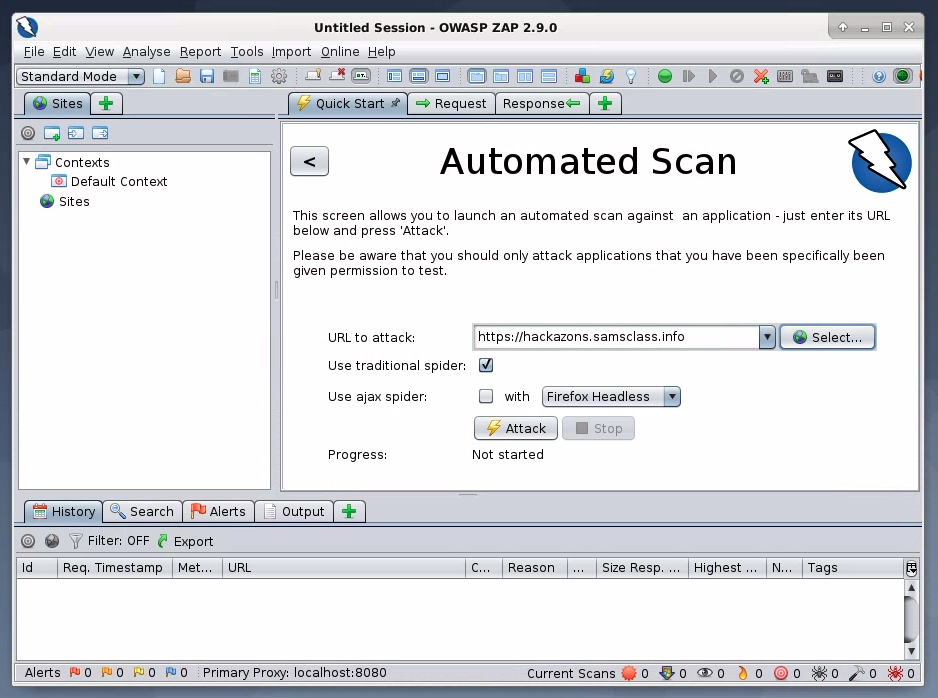
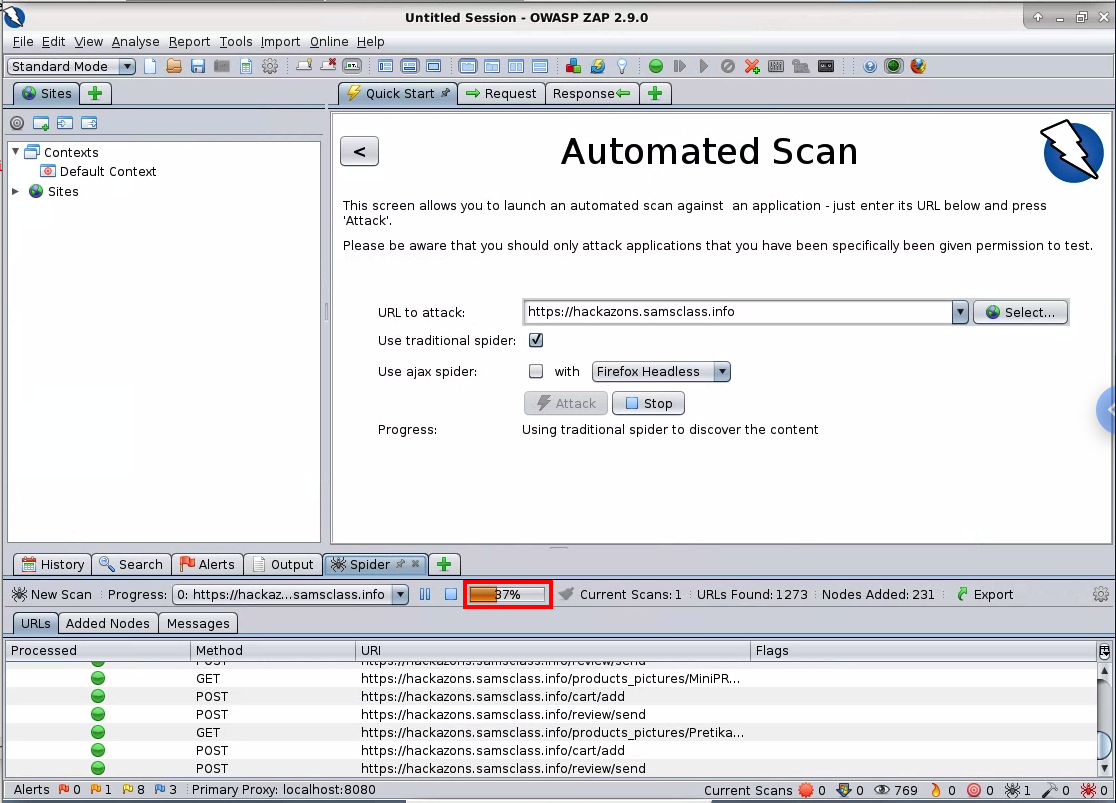
Click the Attack button. A series of messages scrolls by in the lower pane as ZAP attacks the site, searching for vulnerabilities.
You can see the progress of the scan in the bottom center, outlined in red in the image below. It takes about 7 minutes to finish.
Flag W 220.1: XSS Type (10 pts)
When the scan is complete, in the lower pane, click the Alerts tab. You should see five red flags, as shown below.
The flag is covered by a green box in the image below.
In the lower left pane of ZIP, expand the "Cross Site Scripting" item, and click the GET line. In the lower right pane, the entire URL is shown. In the lower right pane, highlight the URL. Press Ctrl+C to copy it.
On your Cloud Server's desktop, open Firefox. Click in the Address bar. Press Ctrl+V to paste the URL and press Enter.
Flag W 220.2: Pop-Up Message (5 pts)
The injected script runs, popping up a box, as shown below. The flag is the message in the box, covered by a green box in the image below.
Copy the URL and paste it into Firefox. You see a login screen, as shown below. Nothing is obviously wrong here.
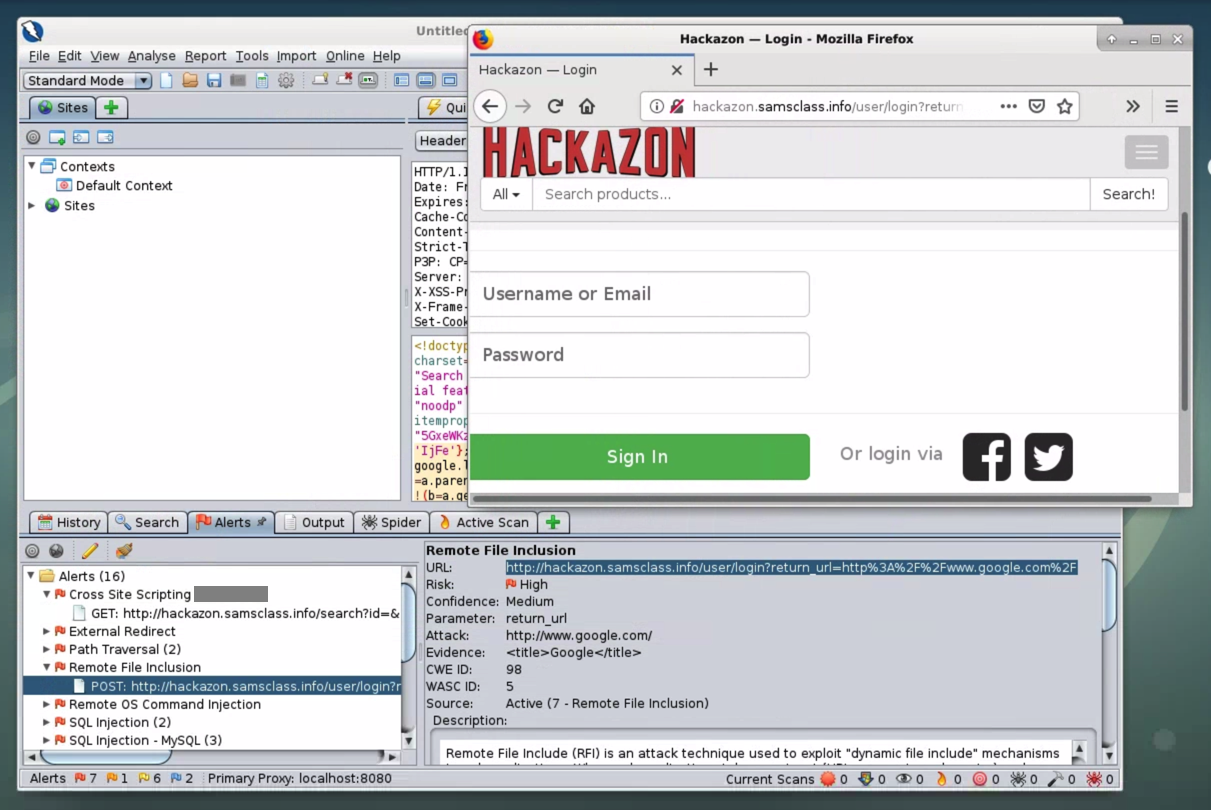
Flag W 220.3: Redirection (5 pts)
In Firefox, log in with the username and password you created at the start of this project.When the login is complete, your page redirects to a different site.
The URL of that site is the flag.
in Hackazon, at the top right, click Logout.
In the lower left pane of ZAP, expand the "SQL Injection - MySQL" item, and click the shorter POST request, as shown below.
In the lower right pane, carefully highlight the entire URL, as shown below.
Copy the URL and paste it into Firefox. Press Enter.
You see a login screen. Look at ZAP again--it specifies that the parameter is username and that the Attack is "ZAP' UNION ALL select NULL --".
To test the attack, enter this text into both the username and password fields, as shown below.
ZAP' AND '1'='1' --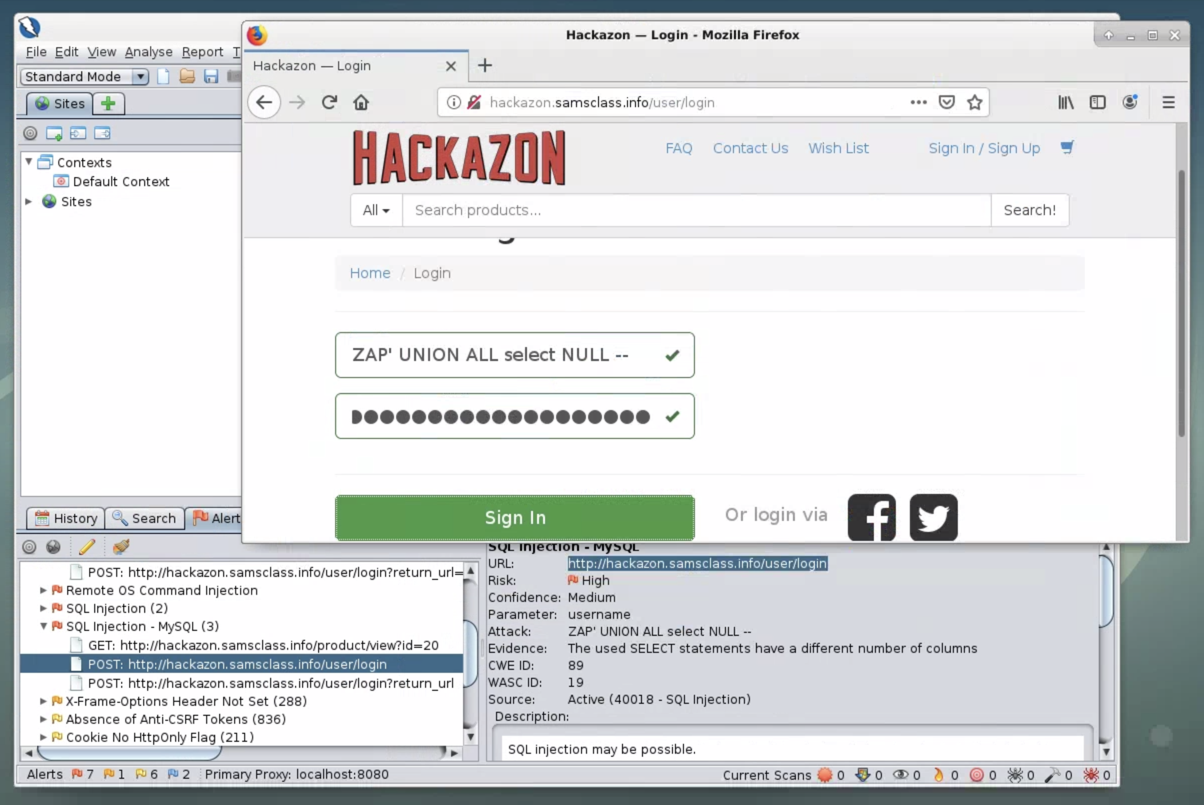
Flag W 220.4: SQL Error (5 pts)
Click the "Sign In" button.You see a big SQL error message. The flag is covered by a green box in the image below.
Updated 1-30-2020 to use a Cloud server
Typo fixed 2-2-2020
Java install added, cleaned up, moved to HTTPS target page 6-13-2020