After installing a DNSCrypt client, you'll see that some private DNS traffic is now encrypted.
You cannot use Windows Server 2008. You need a more modern Windows version.

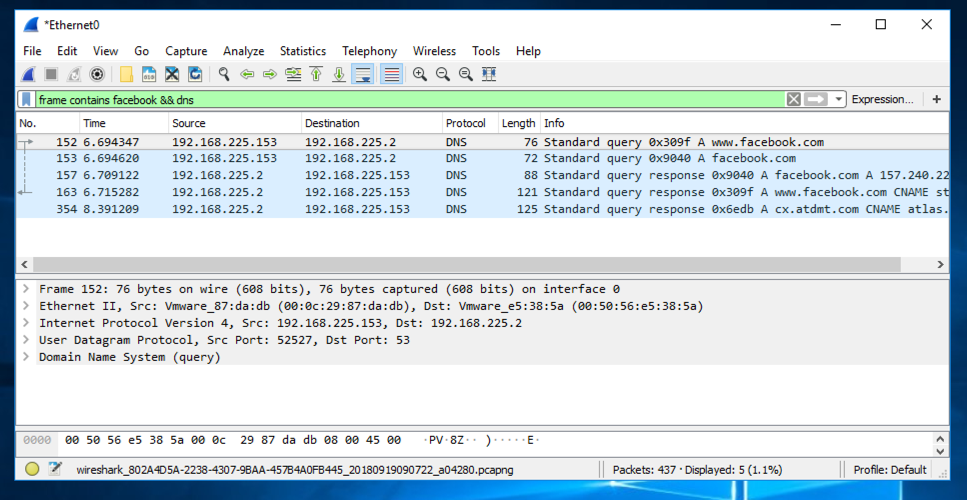
At the top of the Wireshark window, in the Filter: bar, enter this code:
frame contains facebook && dns
Now Wireshark will only show DNS traffic containing "facebook".
Open a web browser and go to
Wireshark should show DNS traffic resolving domain names at facebook, as shown below. You may need to expand the window, or scroll sideways, to see it.
From the Wireshark menu bar, click Capture, Stop.
Download the correct version for your system, 64-bit or32-bit, as shown below.
If you don't know which system you have,
open a Command Prompt and execute the
control system
command to find out.

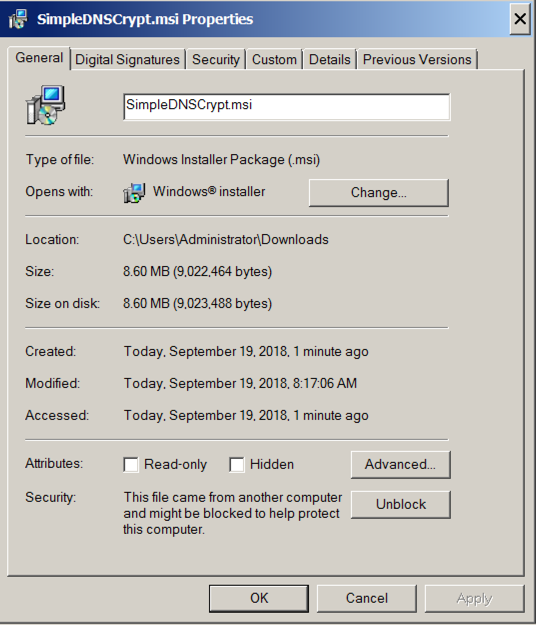
Run the installer. If it won't launch, right-click the file you downloaded and click Properties. At the bottom of the Properties sheet, click Unblock, as shown below. Then launch the installer again.
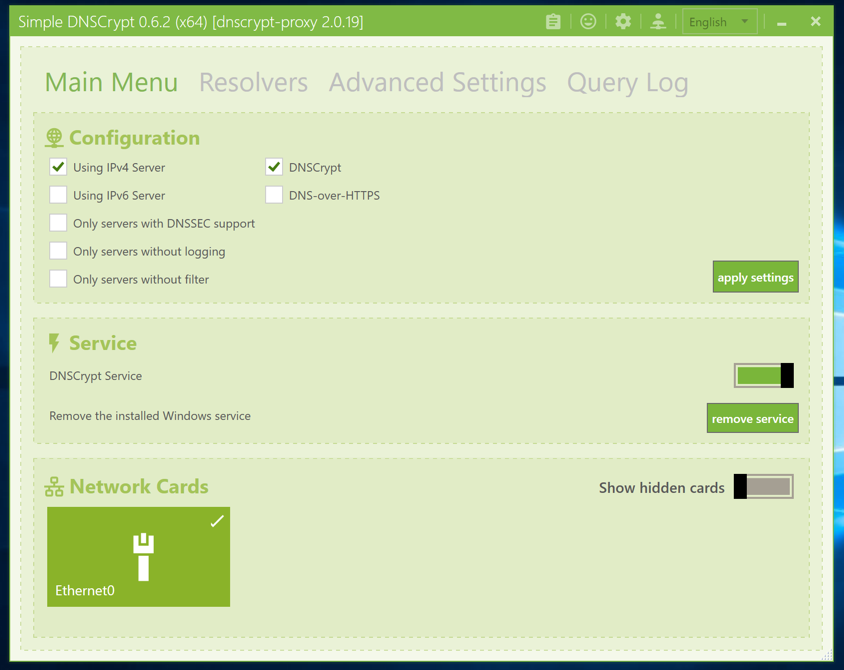
The "Simple DNSCrypt" window opens. On the "Main Menu" tab, make the adjustments shown belowe, and then click the "apply settings" button.
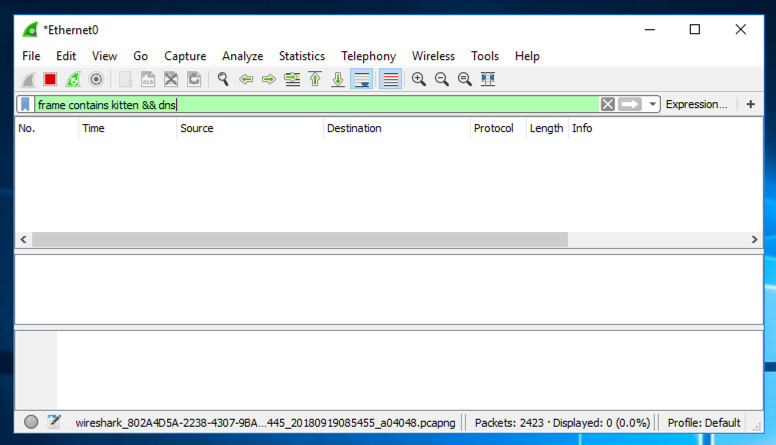
At the top of the Wireshark window, in the Filter: bar, enter this code:
frame contains kitten && dns
In a Web browser, go to
Wireshark doesn't find any packets containing "kitten", as shown below.
Now you have more privacy!
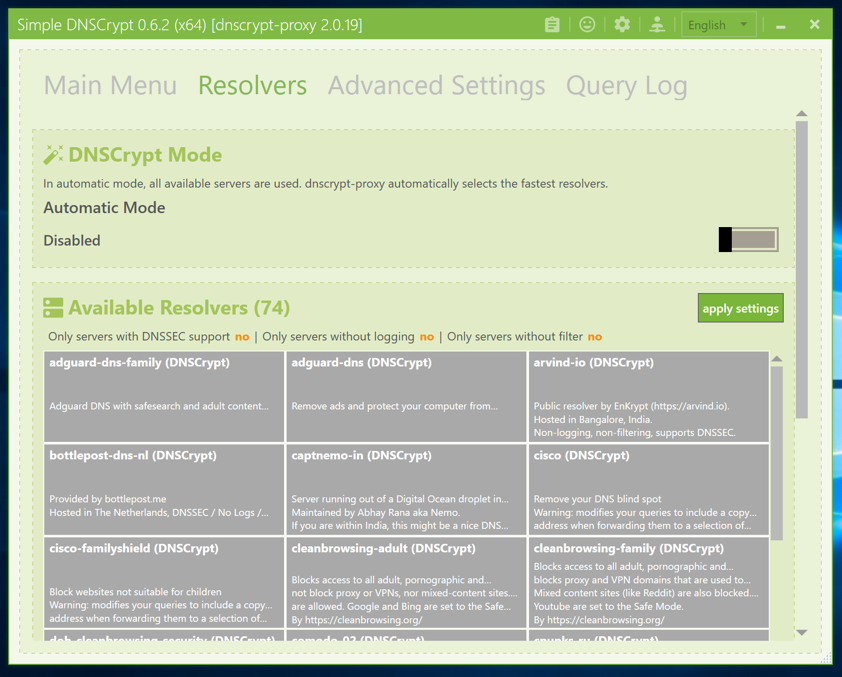
Scroll down and click the two Quad9 resolvers, as shown below.
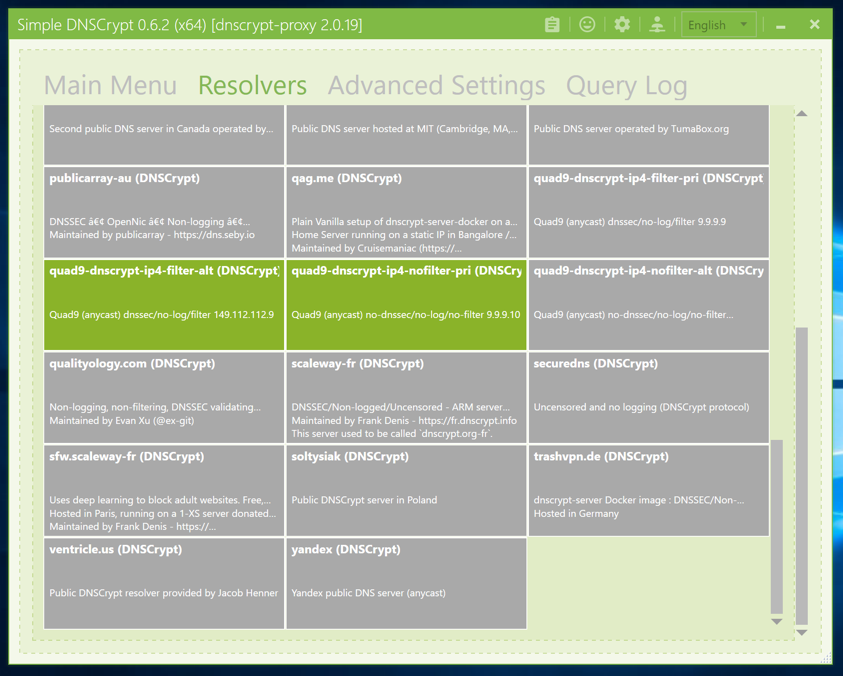
Scroll to the top. Click the slider on the right to disable Automatic Mode, as shown above. Click the "apply settings" button.
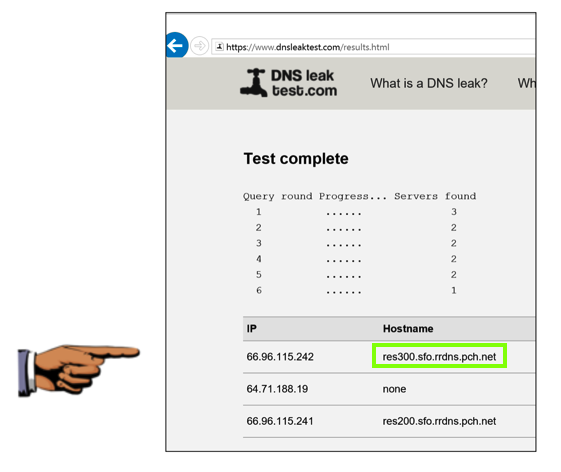
Click the "Extended Test" button.
You should at least one address ending in pch.net, as shown below. This is the Quad9 network, and it shows that you are using their DNSCurve system.
Capture a whole-desktop image.
Save the image with the filename "Your Name Proj 3x". Use your real name, not the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!