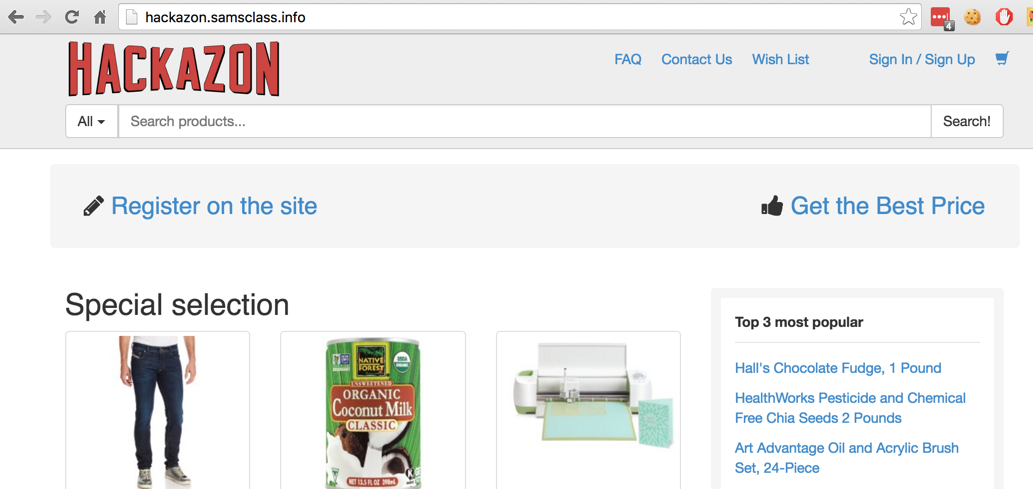
Explore the site bit--it's an imitation of Amazon, as shown below:

Click the "New User?" button and create an account using any username and password. Explore the personalized site a bit, then log out. Make a note of your username and password for later use.
Download and install the latest 64-bit Java version.
On the right side of the page, click "Download OWASP ZAP!".
On the next page, download the appropriate version for your OS.
Run the installer and install the software. If you are using a Mac, drag the "OWASP ZAP.app" icon into the Applications folder.
Troubleshooting
One student's ZAP refused to launch on Windows 10 from the desktop icon. To fix it, we changed the target from ZAP.exe to ZAP.bat.
A "Manage Add-ons" box appears. Click Close.
In the top right pane, enter a "URL to attack" of http://hackazon.samsclass.info, as shown below.
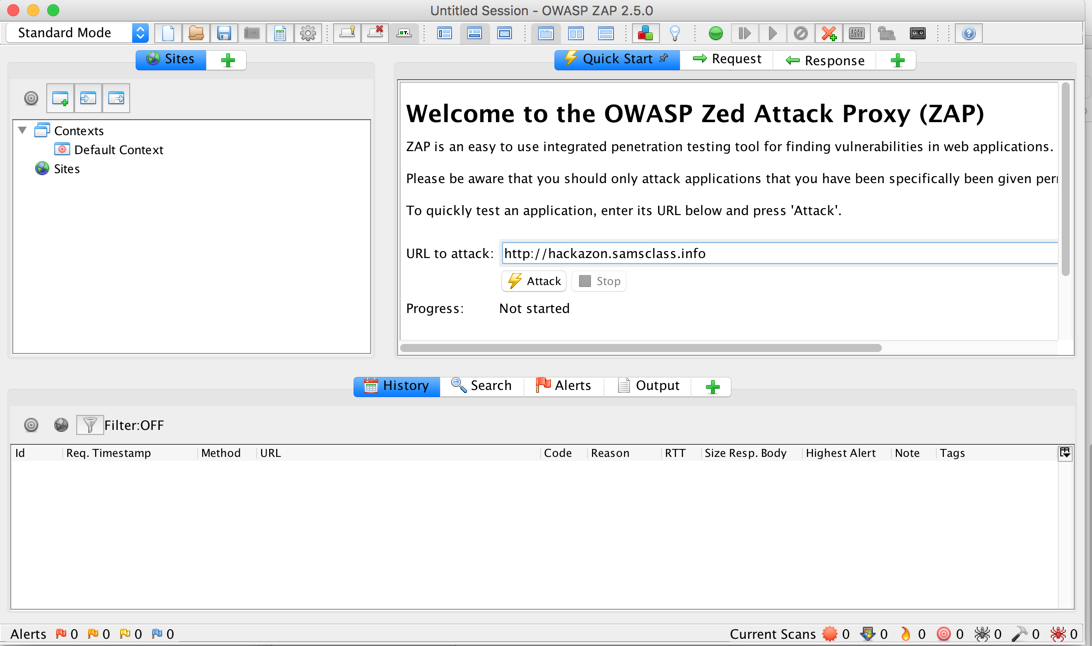
Click the Attack button. A series of messages scrolls by in the lower pane as ZAP attacks the site, searching for vulnerabilities.
The "Spidering" phase should finish quickly, and an "Active Scan" tab should appear, with a lot of messages scrolling by, as shown below. If the "Spidering" phase takes a long time, like 45 minutes, that indicates that the server has been hacked and is full of spam, and Sam needs to restore it. This happened in Jan. 2019, an Sam fixed it on Jan. 31.
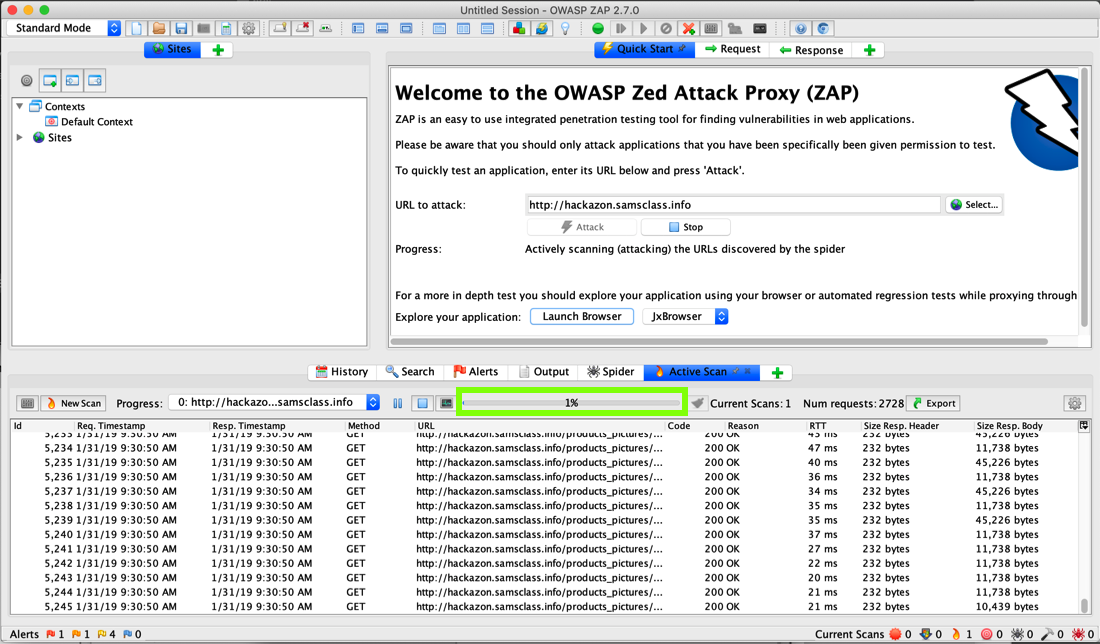
The "Active Scan" process takes some time. Notice the progress bar, outlined in green in the image above. It took about 20 minutes to get to 100% when I did it on 1-31-19.
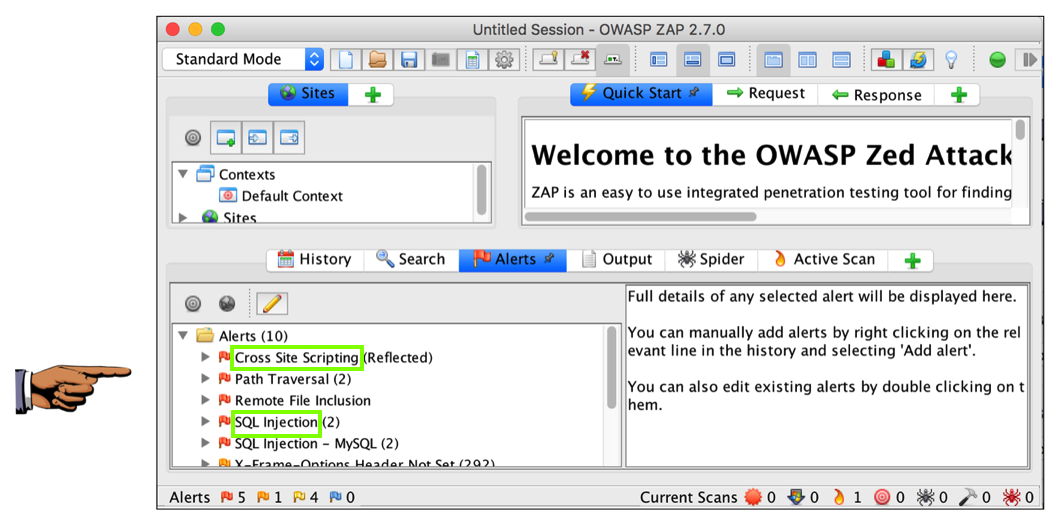
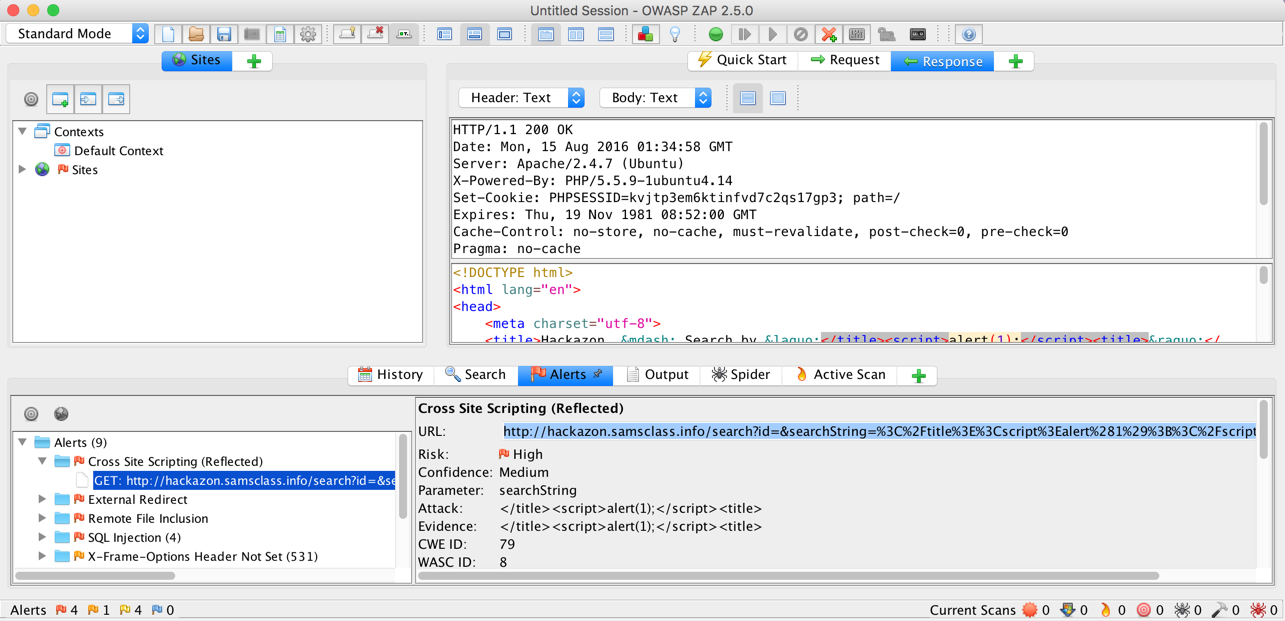
When the scan is at least 50% complete, in the lower pane, click the Alerts tab. You should see red flags, for "Cross Site Scripting" and "SQL Injection", as shown below.
Save a whole-desktop image with a filename of "Proj 4a from YOUR NAME".
In the lower left pane of ZIP, expand the "Cross Site Scripting (Reflected)" item, and click the URL. In the lower right pane, the entire URL is shown. In the lower right pane, triple-click the URL to highlight it, as shown below.
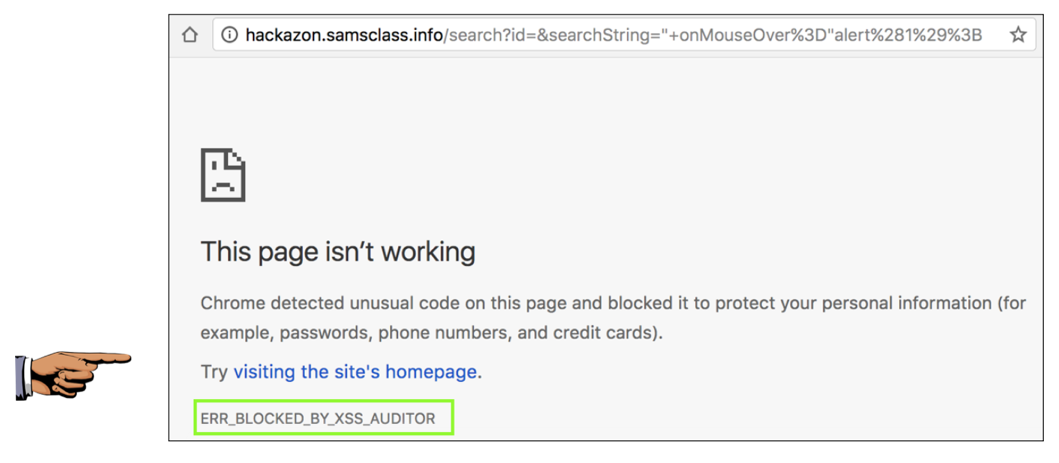
Copy the URL and paste it into Chrome. As shown below, this attack involves entering script into the search field. If it worked, there would be a pop-up box, but there is none.
Instead, chrome shows a "ERR_BLOCKED_BY_XSS_AUDITOR" message, as shown below.
This is what security professionals call a compensating control--even though the Web site has a security flaw, customers using Chrome are protected by their browser.
Save a whole-desktop image with a filename of "Proj 4b from YOUR NAME".
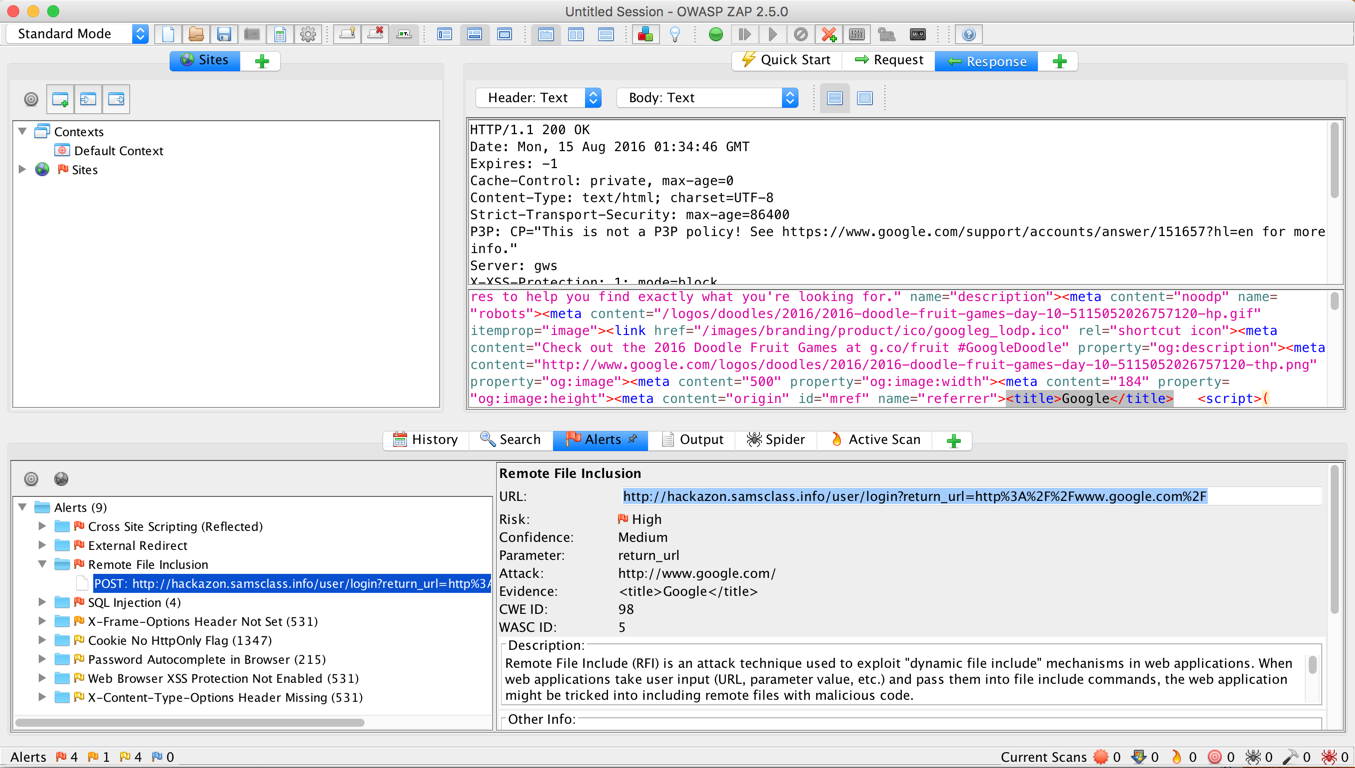
Copy the URL and paste it into Chrome. You see a login screen, as shown below. Nothing is obviously wrong here.
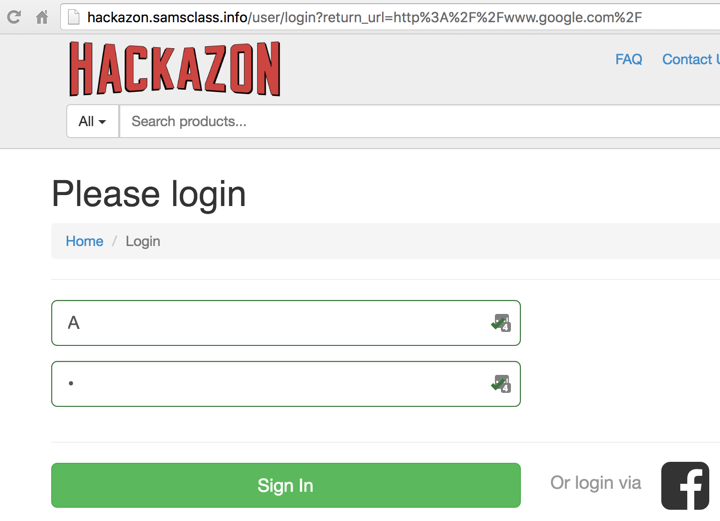
Now log in with the valid username and password you created at the start of this project. When the login is complete, your page redirects to google.com, not to Hackazon.
This is a serious vulnerability! The user could be redirected to a page that installs malware, or steals their credentials, or other evil things.
We'll use Chrome Developer Tools to document this vulnerability.
Open a new Chrome window and open hackazon.samsclass.info
You are currently logged in, as shown below.
At the upper right, click Logout.
From the Chrome menu bar, click View, Developer", "Developer Tools". In the Developer Tools pane, click the Network tab.
Paste this into the URL bar in Chrome and then press Enter:
http://hackazon.samsclass.info/user/login?return_url=http%3A%2F%2Fwww.google.com%2F
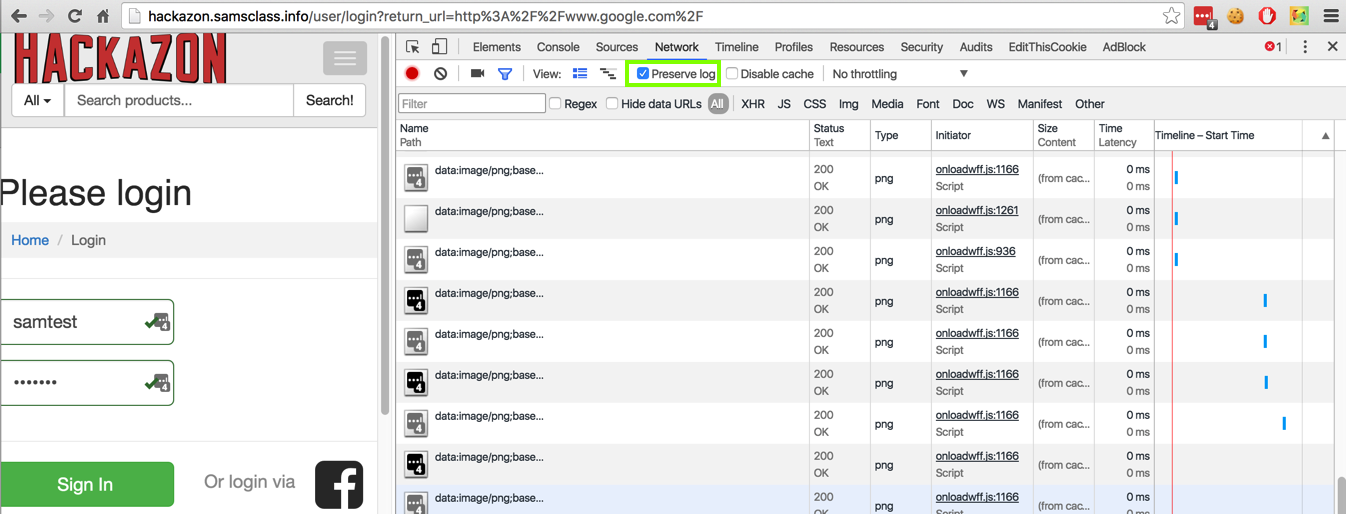
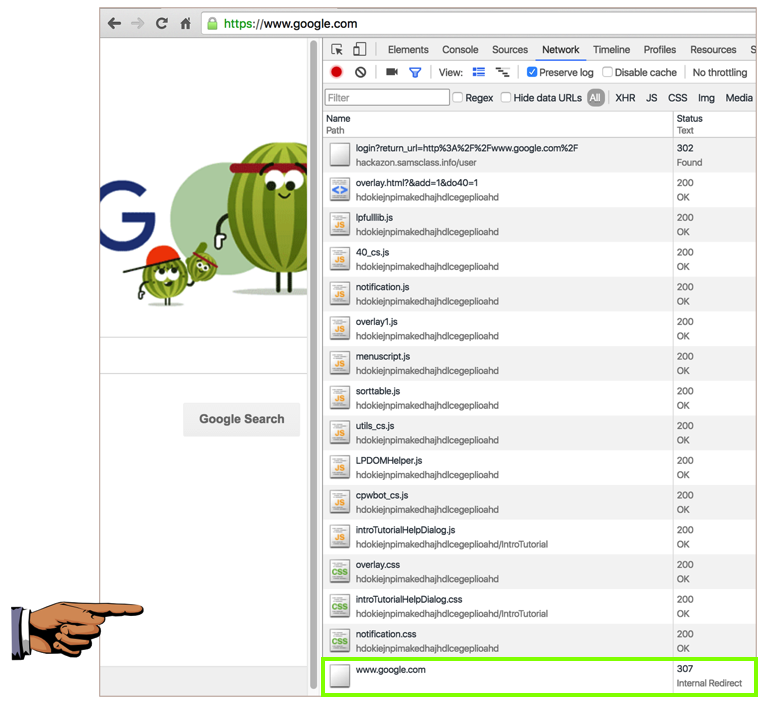
Log in with a valid name and password. Scroll through the Network items--you should see a hackazon login URL, followed by about 15 other elements, and then www.google.com with a status code of "307 Internal Redirect", as shown below. This is not a normal load of Google, which would show a 200 Status, and it demonstrates the vulnerability.
Save a whole-desktop image with a filename of "Proj 4c from YOUR NAME".
Copy the URL and paste it into Chrome. At the top right, click Logout.
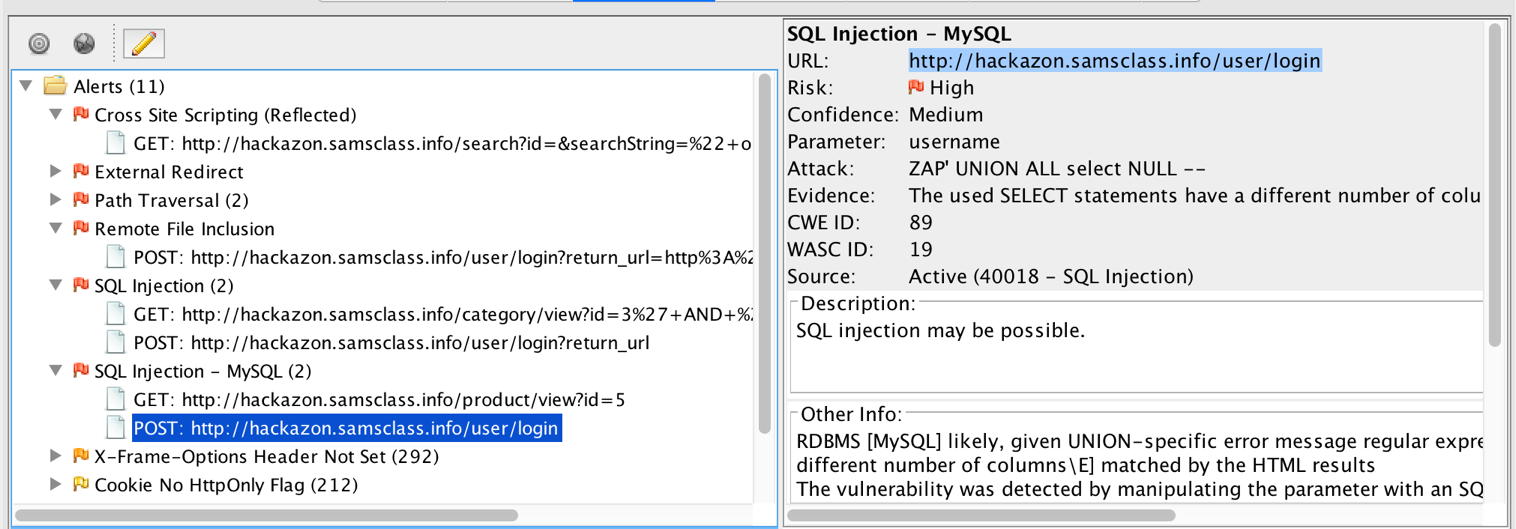
Paste the URL in again and press Enter. You see a login screen. Look at ZAP again--it specifies that the parameter is username and that the Attack is "ZAP' AND '1'='1' --".
To test the attack, enter this text into both the username and password fields, as shown below.
ZAP' AND '1'='1' --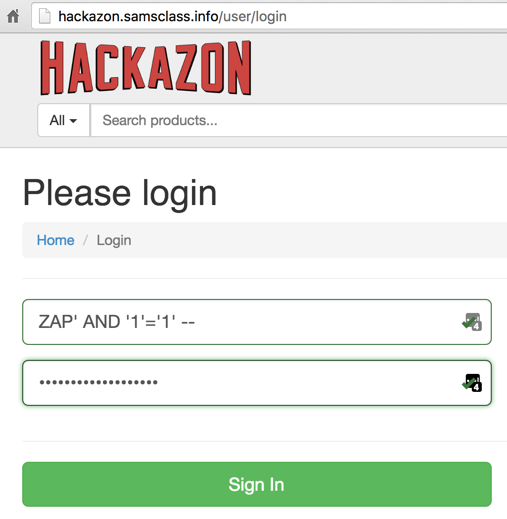
Click the "Sign In" button.
You see a big SQL error message, as shown below.
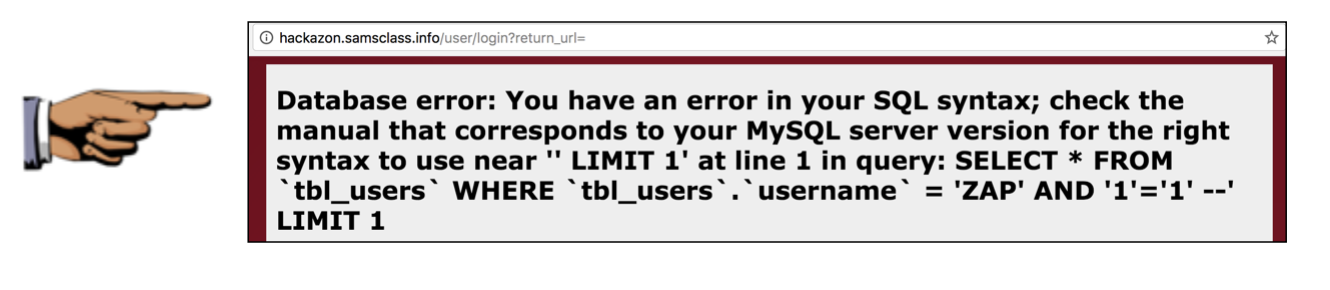
Save a whole-desktop image with a filename of "Proj 4d from YOUR NAME".
Email the image to cnit.129s@gmail.com with a subject of "Project 4 from YOUR NAME".
Updated 3-11-19