Accept the default selection of "Use Burp Defaults" and click "Start Burp".
In Burp, on the Proxy tab, click the "Intercept is on" button so it reads "Intercept is off".
Look at the top right of the Hackazon page and ensure that you see the "Sign In/Sign Up" link, as shown below. If you don't see it, click Logout.
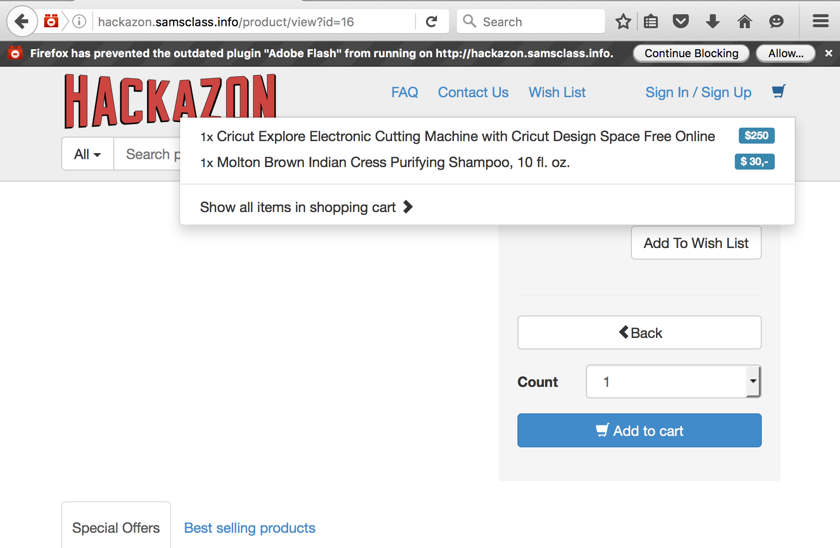
Click on any two items and add them to your cart, as shown below.

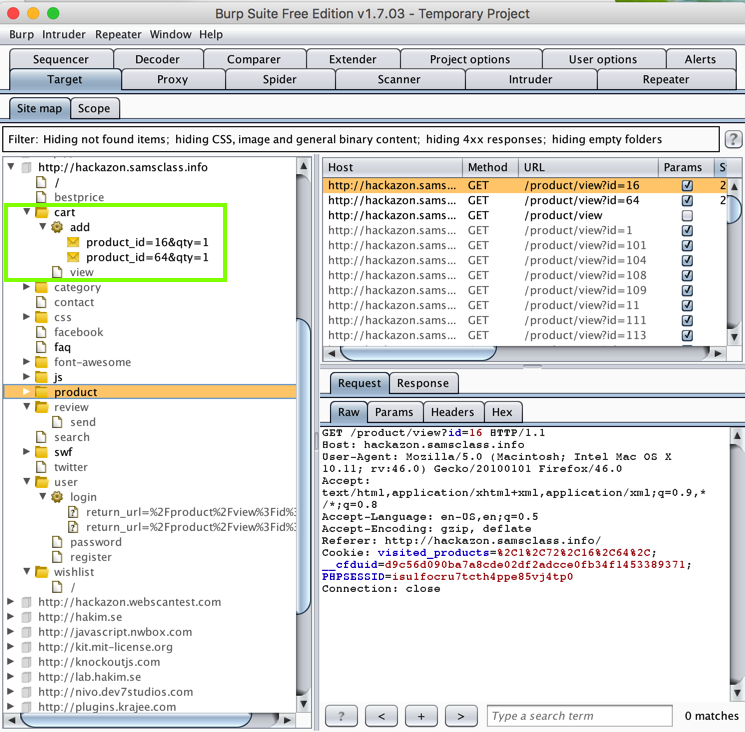
In Burp, on the "Site map" tab, expand http://hackazon.samsclass.info. Expand cart and add. You should see your two items, as outlined in green in the image below.
If a box pops up saying "... Would you like to modify the scope to include these items?", click Yes.
In Burp, click the Spider tab. After a few seconds, Burp finds some forms and pops up a box asking how to handle forms.
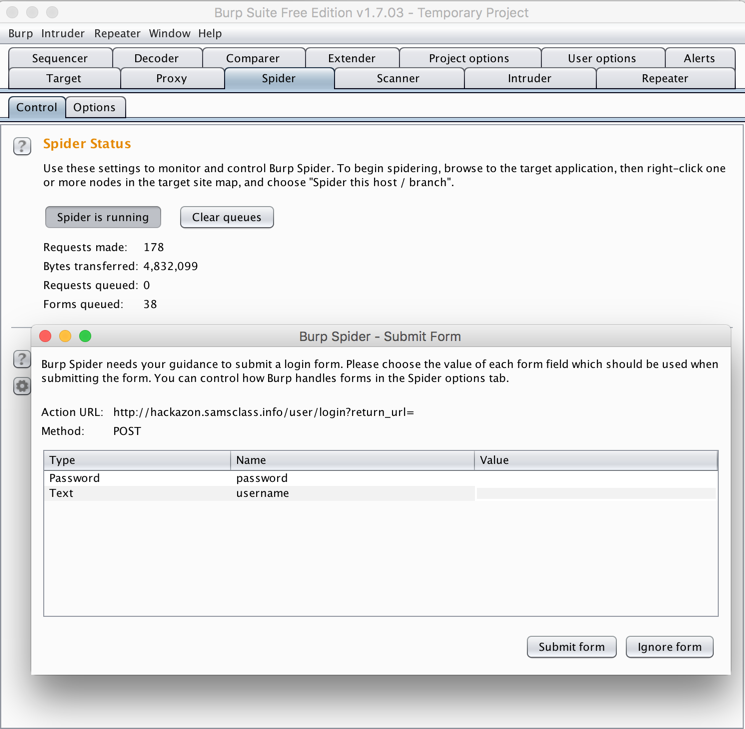
Click "Ignore this form" in this box, and all future boxes like it. There are a lot of them, perhaps 15.
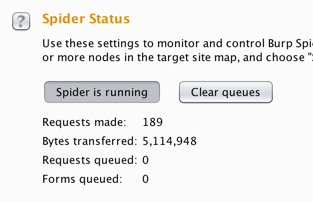
The spider should finish within a few seconds. You can tell it's done because the "Requests queued" and "Forms queued" values are zero, as shown below.
Click the "Spider is running" button to stop the spidering.
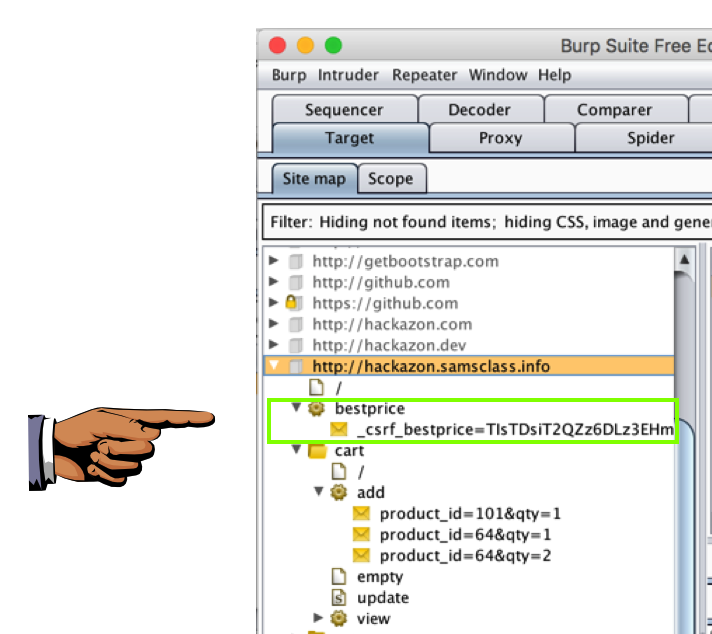
In Burp, on the Target tab, on the "Site map" sub-tab, expand bestprice. You should see an item beginning _csrf_bestprice, as shown below. This is a part of the application the spider found.
Save a whole-desktop image with a filename of "Proj 5a from YOUR NAME".
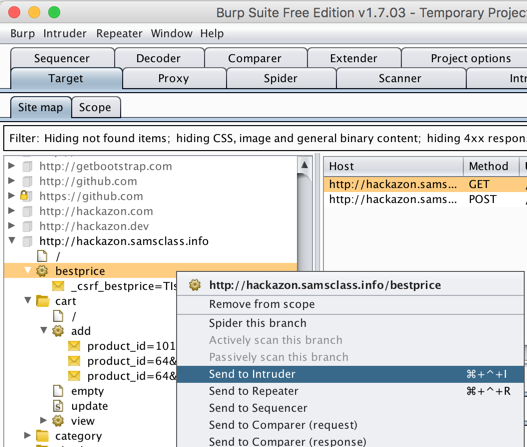
In Burp, click the Intruder tab. On the Target sub-tab, the Host: should be "hackazon.samsclass.info", as shown below.
Click the Positions sub-tab. In the GET line, double-click bestprice to highlight it. On the right side, click the "Add §" button. These "section marks" indicate where Burp Intruder will insert words.
Your screen should look like the image below.
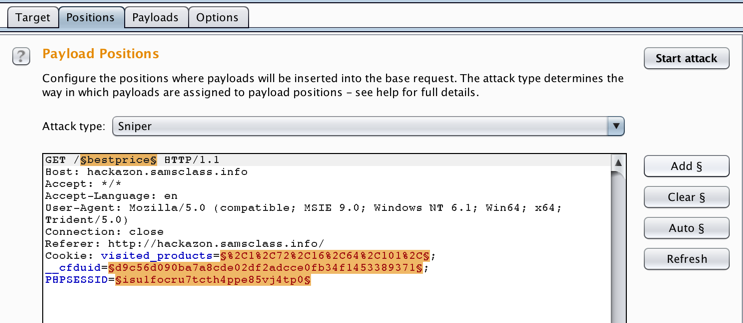
Carefully delete the word bestprice, preserving the section marks, as shown below.
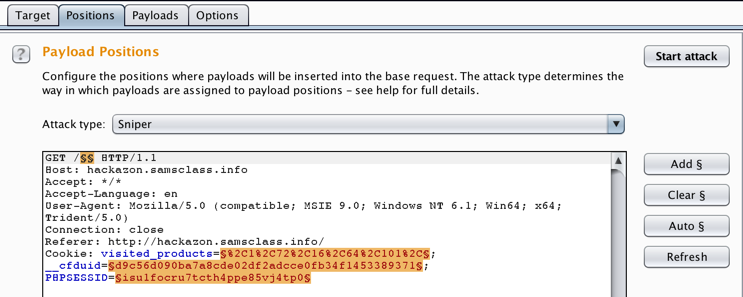
Click the "Start attack" button.
An error appears saying "Preset payload list is empty". Click the "Go back" button.
In Burp, click the Payloads sub-tab. There are no wordlists included in the free version of Burp.
Right-click the link below and save the file on your computer. This is a list of common directory names I got from the page listed in the Sources section at tne end of this project.
In Burp, in the "Payload Options (Simple List)" section, click the Load... button.
Browse to the "Directories_Common.wordlist" file on your computer and double-click it.
The word list populates, as shown below.
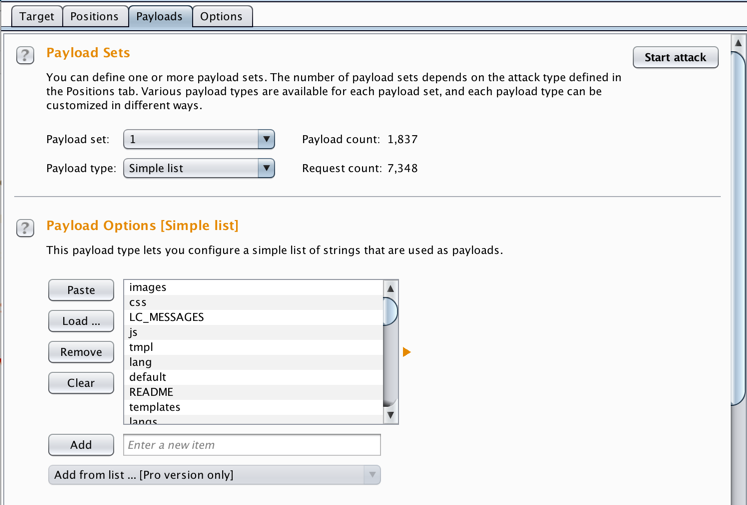
Click the "Start attack" button.
A message warns that this attack is throttled in the free version of Burp. Click OK.
A box pops up showing the attack in progress, as shown below. It's very slow, but it does show the HTTP response code for each request.
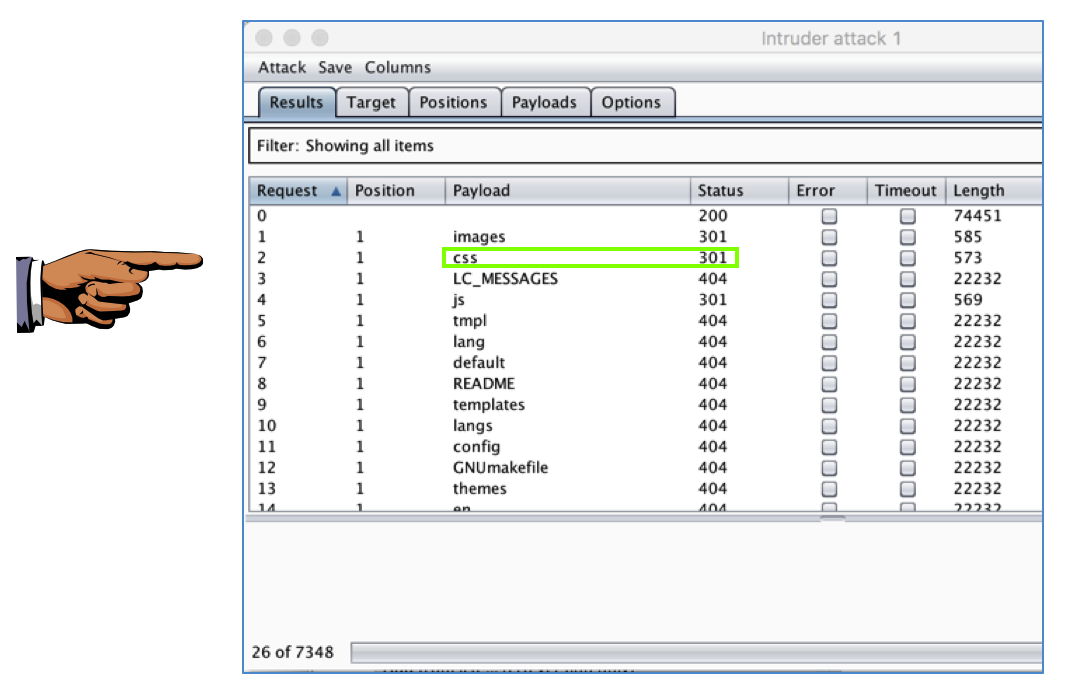
Save a whole-desktop image with a filename of "Proj 5b from YOUR NAME".
In the "Intruder: attack 1" window, click Attack, Pause. When the attack pauses, close the the "Intruder: attack 1" window.
Email the image to cnit.129s@gmail.com with a subject of "Project 5 from YOUR NAME".
Last modified 2-20-18