https://kali.training/topic/exercise-7-3-securing-the-kali-file-system/
In a Terminal window, execute this command:
sudo dpkg-reconfigure tzdata
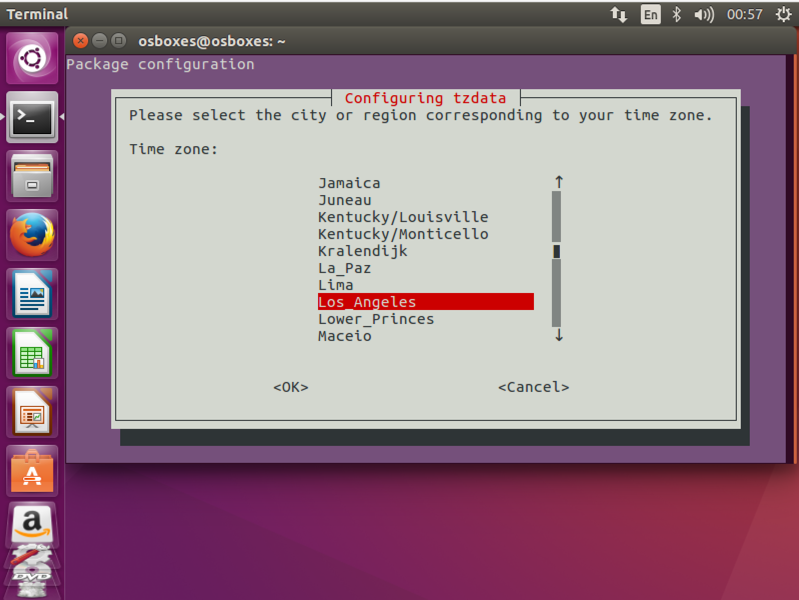
Use the arrow keys on the keyboard to highlight America. Then press Tab to highlight OK. Press Enter.
On the next screen, select Los_Angeles, as shown below. Then press Tab to highlight OK. Press Enter.

sudo apt-get update
sudo apt-get install tripwire -y
sudo tripwire --init
Execute these commands to get a list of files it shouldn't be monitoring:
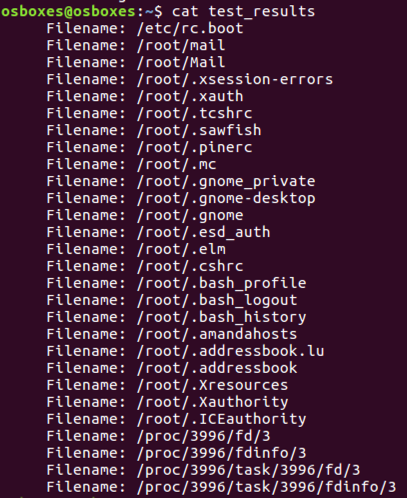
sudo tripwire --check | grep Filename > test_results
cat test_results
A list of files appears, as shown below.
Execute this command to adjust Tripwire's policy.
sudo nano /etc/tripwire/twpol.txt
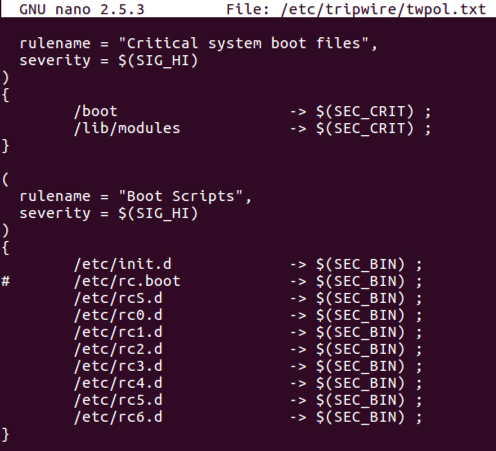
For example, the screen image below shows the file after commenting out /etc/rc.boot.
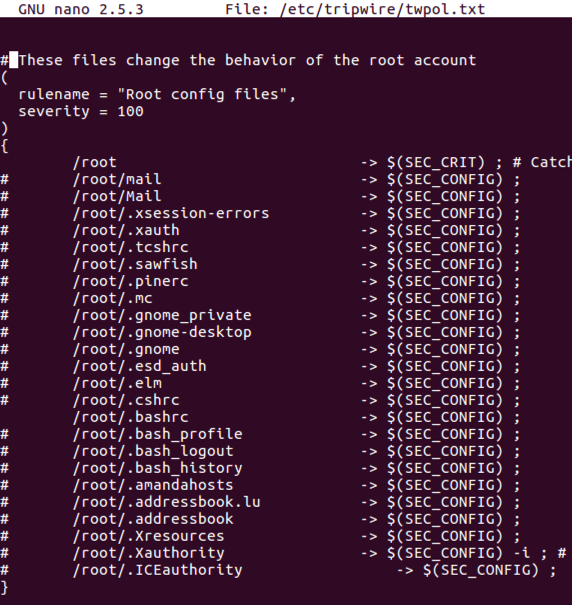
All the other lines I needed to comment out were in the "Root config files" section, as shown below.
In the "Devices & Kernel information" section, replace this:
#
# Critical devices
#
(
rulename = "Devices & Kernel information",
severity = $(SIG_HI),
)
{
/dev -> $(Device) ;
/proc -> $(Device) ;
}
#
# Critical devices
#
(
rulename = "Devices & Kernel information",
severity = $(SIG_HI),
)
{
/dev -> $(Device) ;
/dev/pts -> $(Device) ;
#/proc -> $(Device) ;
/proc/devices -> $(Device) ;
/proc/net -> $(Device) ;
/proc/tty -> $(Device) ;
/proc/sys -> $(Device) ;
/proc/cpuinfo -> $(Device) ;
/proc/modules -> $(Device) ;
/proc/mounts -> $(Device) ;
/proc/dma -> $(Device) ;
/proc/filesystems -> $(Device) ;
/proc/interrupts -> $(Device) ;
/proc/ioports -> $(Device) ;
/proc/scsi -> $(Device) ;
/proc/kcore -> $(Device) ;
/proc/self -> $(Device) ;
/proc/kmsg -> $(Device) ;
/proc/stat -> $(Device) ;
/proc/loadavg -> $(Device) ;
/proc/uptime -> $(Device) ;
/proc/locks -> $(Device) ;
/proc/meminfo -> $(Device) ;
/proc/misc -> $(Device) ;
}
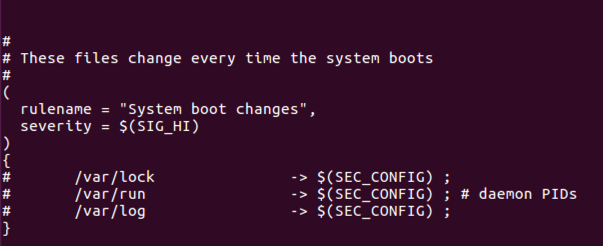
#
# These files change every time the system boots
#
(
rulename = "System boot changes",
severity = $(SIG_HI)
)
{
# /var/lock -> $(SEC_CONFIG) ;
# /var/run -> $(SEC_CONFIG) ; # daemon PIDs
# /var/log -> $(SEC_CONFIG) ;
}
Press Ctrl+X, Y, Enter to save the file.
sudo twadmin -m P /etc/tripwire/twpol.txt
Execute this command to initialize the Tripwire database:
sudo tripwire --init
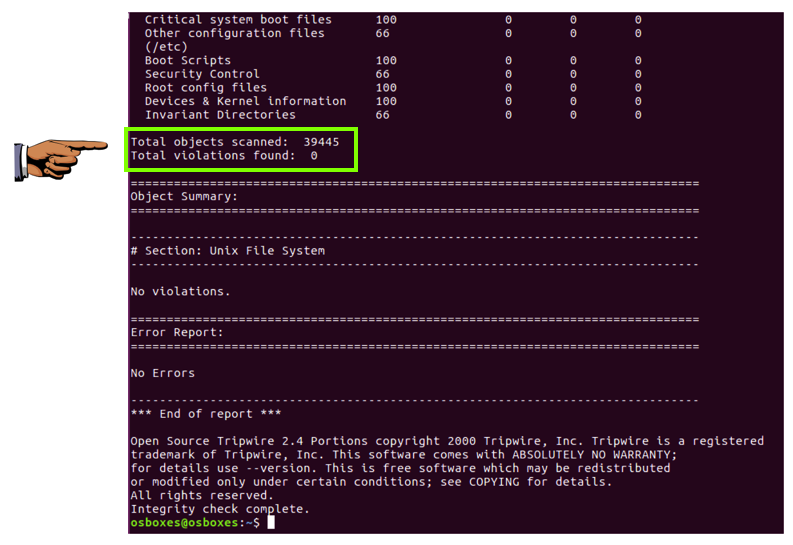
Execute this command to run a tripwire check:
sudo tripwire --check
Click the host computer's desktop. Press Shift+PrntScrn key to capture the entire desktop. If you are using a Mac, press Shift+Cmd+3
YOU MUST SUBMIT A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Save this image as a PNG file, named "Proj 7 from YOUR NAME"
Posted 9-19-16
Warning about Kali added 2-21-18
Warning about Ubuntu 18.04 adde 3-4-18
Sam Bowne