You also need another machine to test the connection from, on the same network.
A firewall is a very powerful defense and every server should use one.
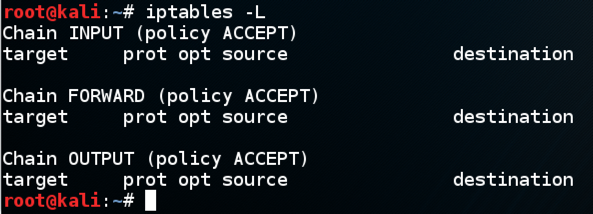
sudo iptables -L

If you see other rules, execute these commands to clear them:
sudo iptables -F
sudo iptables -X
sudo iptables -t nat -F
sudo iptables -t nat -X
sudo iptables -t mangle -F
sudo iptables -t mangle -X
sudo iptables -t raw -F
sudo iptables -t raw -X
sudo iptables -t security -F
sudo iptables -t security -X
sudo iptables -P INPUT ACCEPT
sudo iptables -P FORWARD ACCEPT
sudo iptables -P OUTPUT ACCEPT
On your Linux server, in a Terminal window, execute these commands:
sudo iptables -N TCP
sudo iptables -N UDP
sudo iptables -P FORWARD DROP
On your Linux server, in a Terminal window, execute this command:
sudo iptables -P OUTPUT ACCEPT
sudo iptables -P INPUT DROP
sudo iptables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
sudo iptables -A INPUT -i lo -j ACCEPT
sudo iptables -A INPUT -m conntrack --ctstate INVALID -j DROP
sudo iptables -A INPUT -p icmp --icmp-type 8 -m conntrack --ctstate NEW -j ACCEPT
sudo iptables -A INPUT -p udp -m conntrack --ctstate NEW -j UDP
sudo iptables -A INPUT -p tcp --syn -m conntrack --ctstate NEW -j TCP
sudo iptables -A INPUT -p udp -j REJECT --reject-with icmp-port-unreachable
sudo iptables -A INPUT -p tcp -j REJECT --reject-with tcp-reset
sudo iptables -A INPUT -j REJECT --reject-with icmp-proto-unreachable
On your Linux server, in a Terminal window, execute these commands:
sudo iptables -A TCP -p tcp --dport 80 -j ACCEPT
sudo iptables -A TCP -p tcp --dport 443 -j ACCEPT
sudo iptables -A TCP -p tcp --dport 22 -j ACCEPT
sudo iptables -A TCP -p tcp --dport 9999 -j ACCEPT
sudo iptables -A UDP -p udp --dport 53 -j ACCEPT
If you are using Ubuntu, execute these commands:
sudo apt-get update
sudo apt-get install git -y
git clone https://github.com/jaymzh/iptstate.git
cd iptstate
sudo apt-get install ncurses-dev libnetfilter-conntrack-dev -y
make
sudo make install
sudo iptstate
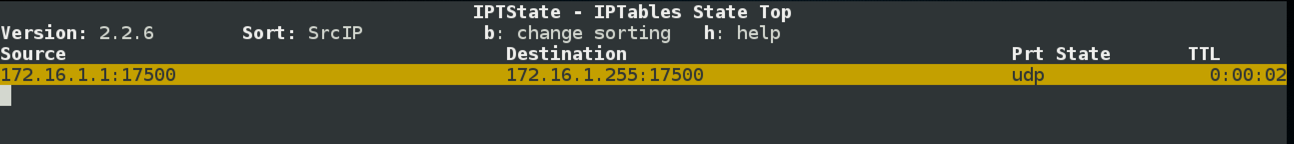
ifconfig
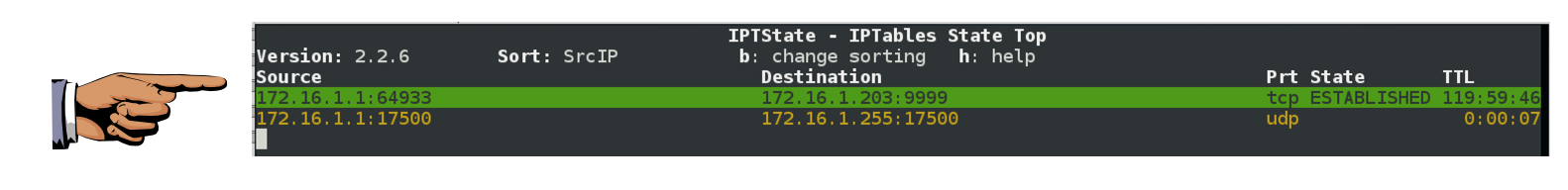
nc -nlvp 9999
If you are using Linux or the Mac, connect with nc this way, replacing the IP address with the IP address of your Linux server:
nc 172.16.1.203 9999
ncat 172.16.1.203 9999
sudo iptables -A OUTPUT -p tcp --tcp-flags ALL SYN -m state --state NEW -j DROP
Click the host computer's desktop. Press Shift+PrntScrn key to capture the entire desktop. If you are using a Mac, press Shift+Cmd+3
YOU MUST SUBMIT A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Save this image with the filename "Proj 7x from YOUR NAME"
What's the right way to prevent shell bounce back?
Saving Iptables Firewall Rules Permanently