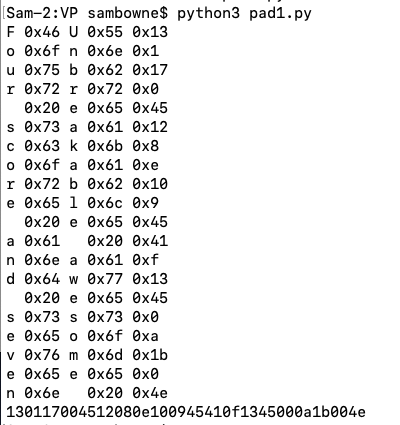

Unbreakable awesome secret secure system
Four score and seven
key = "Unbreakable awesome secret secure system"
plaintext = "Four score and seven"
i = 0
ciphertext = ""
for p in plaintext:
ip = ord(p)
k = key[i]
ik = ord(k)
inew = ip ^ ik
ciphertext += chr(inew)
print(p, hex(ip), k, hex(ik), hex(inew))
i += 1
print(ciphertext.encode("ascii").hex())

Decrypting uses the same operation, since XOR reverses itself:
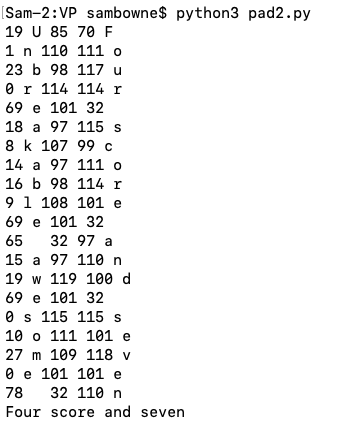
key = "Unbreakable awesome secret secure system"
ciphertext = bytes.fromhex("130117004512080e100945410f1345000a1b004e")
i = 0
plaintext = ""
for c in ciphertext:
k = key[i]
ik = ord(k)
ip = c ^ ik
p = chr(ip)
print(c, k, ik, ip, p)
plaintext += p
i += 1
print(plaintext)
C 105.1: Using a Known Key (5 pts)
Use this key:Decrypt this ciphertext:
C 105.2: Crib Drag (15 pts)
The key starts with:Both these ciphertexts were encrypted with the same key:
From the partial plaintexts, you can guess another letter or two, and use those letters to extend the key. Continue adding one or two letters at a time until you get the whole plaintext. This is called the crib drag attack.
Submit either of the plaintext messages as the flag.
Hint: Here's a script that lets you guess letters interactively.
C 105.3: Crib Drag (15 pts)
Both these ciphertexts were encrypted with the same key:One of the plaintext messages contains the flag.
C 105.4: Crib Drag (50 pts)
Both these ciphertexts were encrypted with the same key:One of the plaintext messages contains the flag.