sudo apt install python3-venv -y
python3 -m venv ./cabby-env
source ./cabby-env/bin/activate
python -m pip install libtaxii
python -m pip install cabby
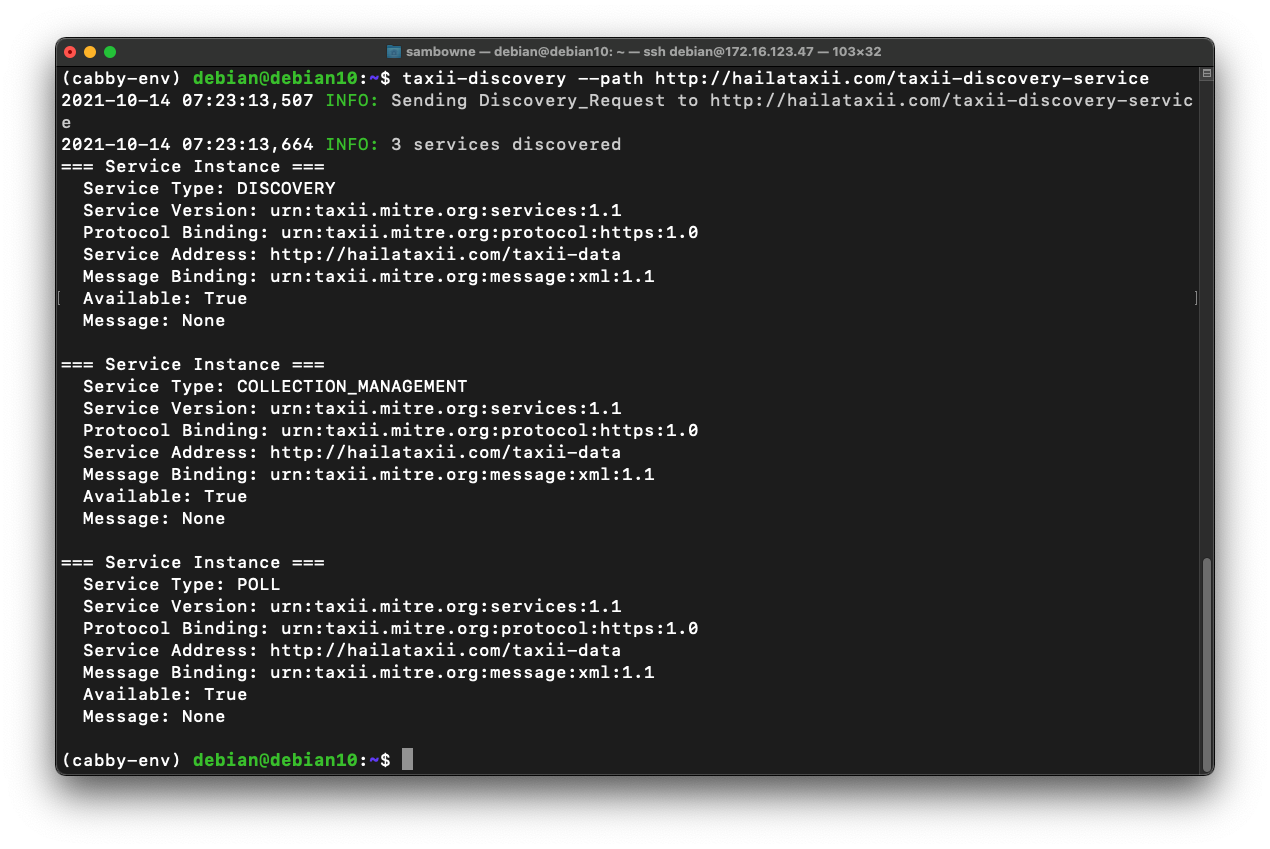
taxii-discovery --path http://hailataxii.com/taxii-discovery-service

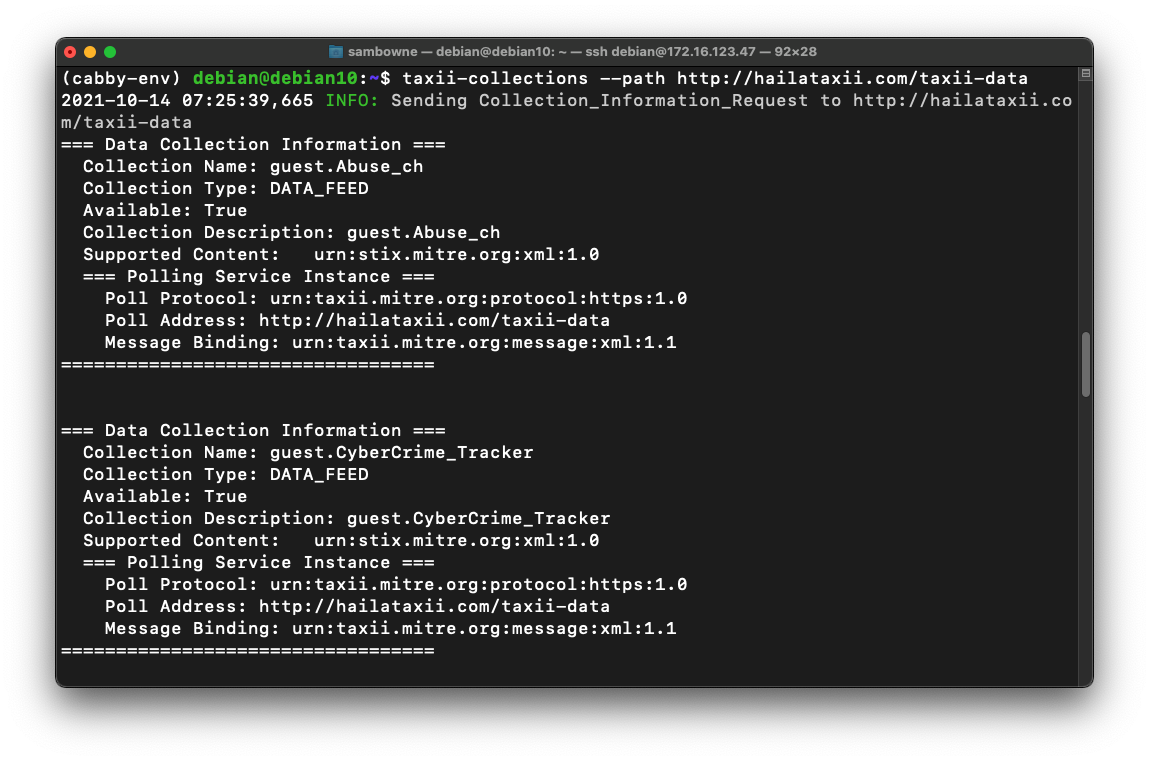
taxii-collections --path http://hailataxii.com/taxii-data
In your Linux machine, execute this command:
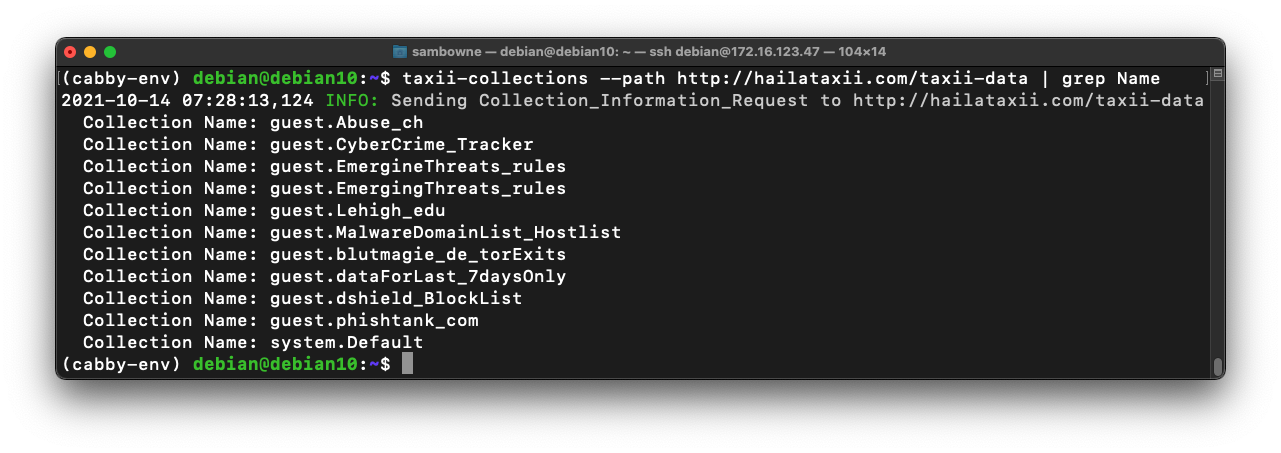
taxii-collections --path http://hailataxii.com/taxii-data | grep Name
taxii-poll --path http://hailataxii.com/taxii-data \
--collection guest.phishtank_com \
--begin 2018-05-25T02:00:00 \
--end 2018-05-25T02:10:00
taxii-poll --path http://hailataxii.com//taxii-data \
--collection guest.phishtank_com \
--begin 2018-05-25T02:00:00 \
--end 2018-05-25T02:10:00 > phish.txt
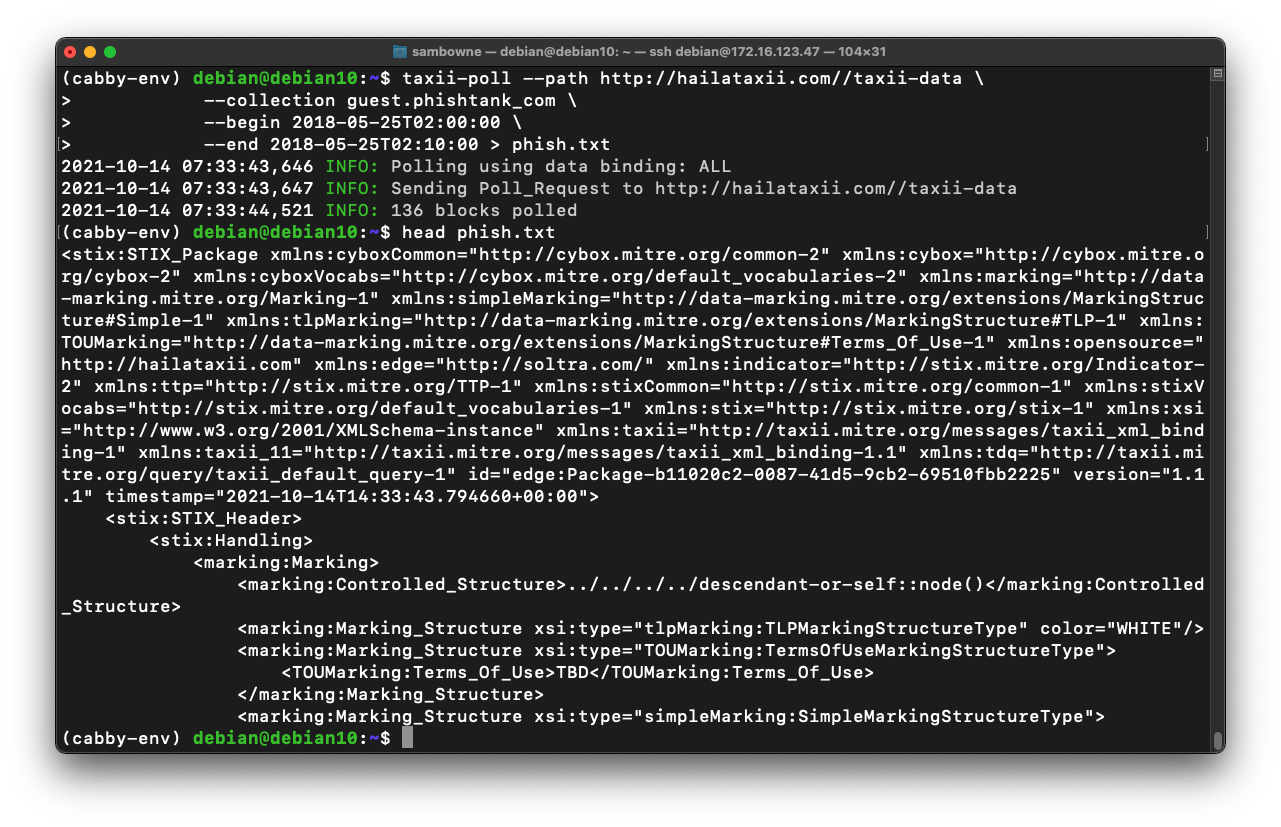
head phish.txt
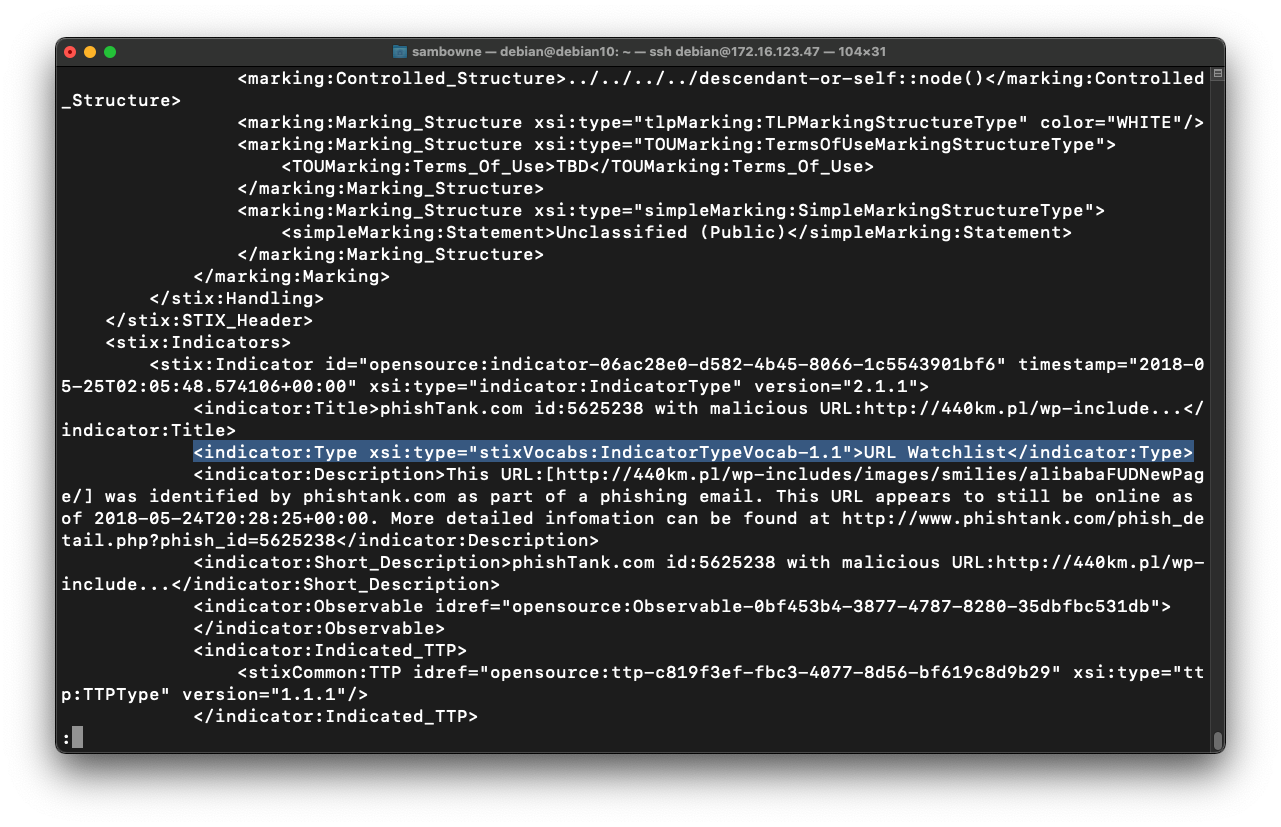
less phish.txt
This line shows what type of data is given in the object. We'll start with that information.
Press q to exit from "less".
wc -l phish.txt
grep indicator:Type phish.txt | wc -l
grep indicator:Type phish.txt | sort | uniq -c
less phish.txt
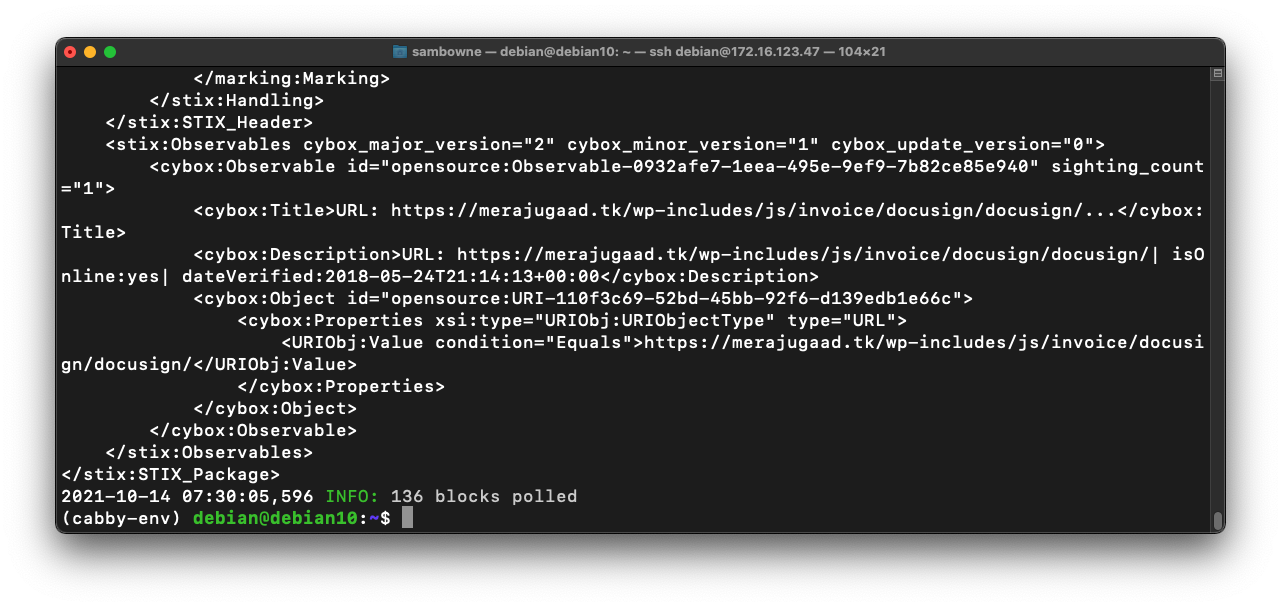
Notice that the next line contains a URL, highlighted in the image below.
All we need is a list of those URLs, without all the other information.
Press q to exit from "less".
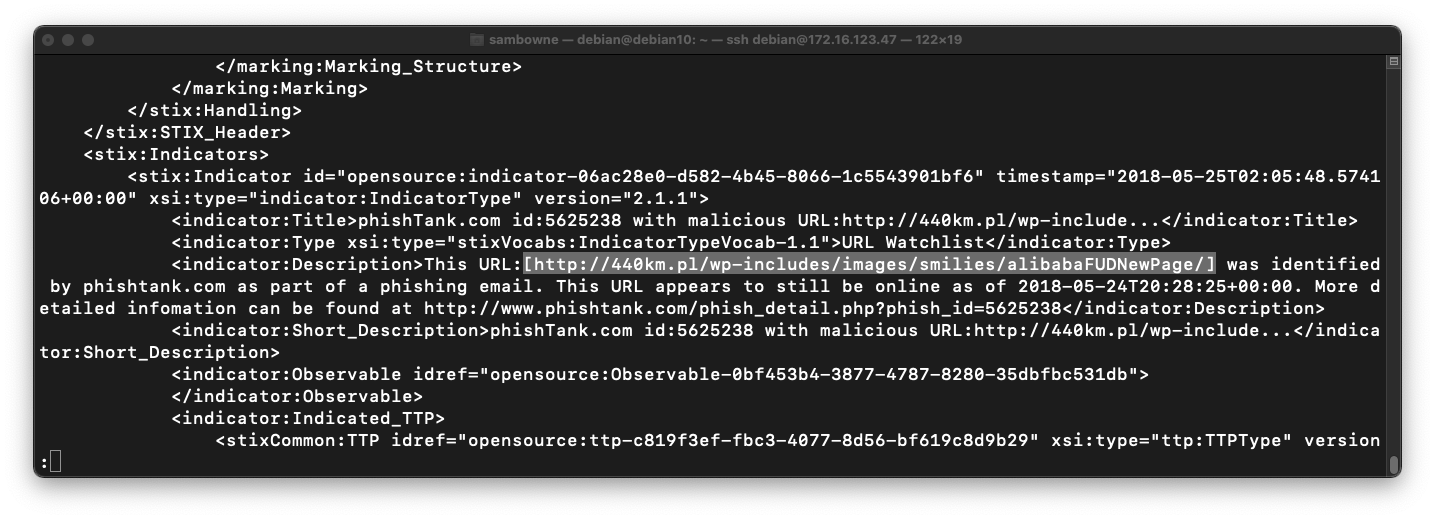
In your Linux machine, execute the following command:
grep indicator:Description phish.txt | head
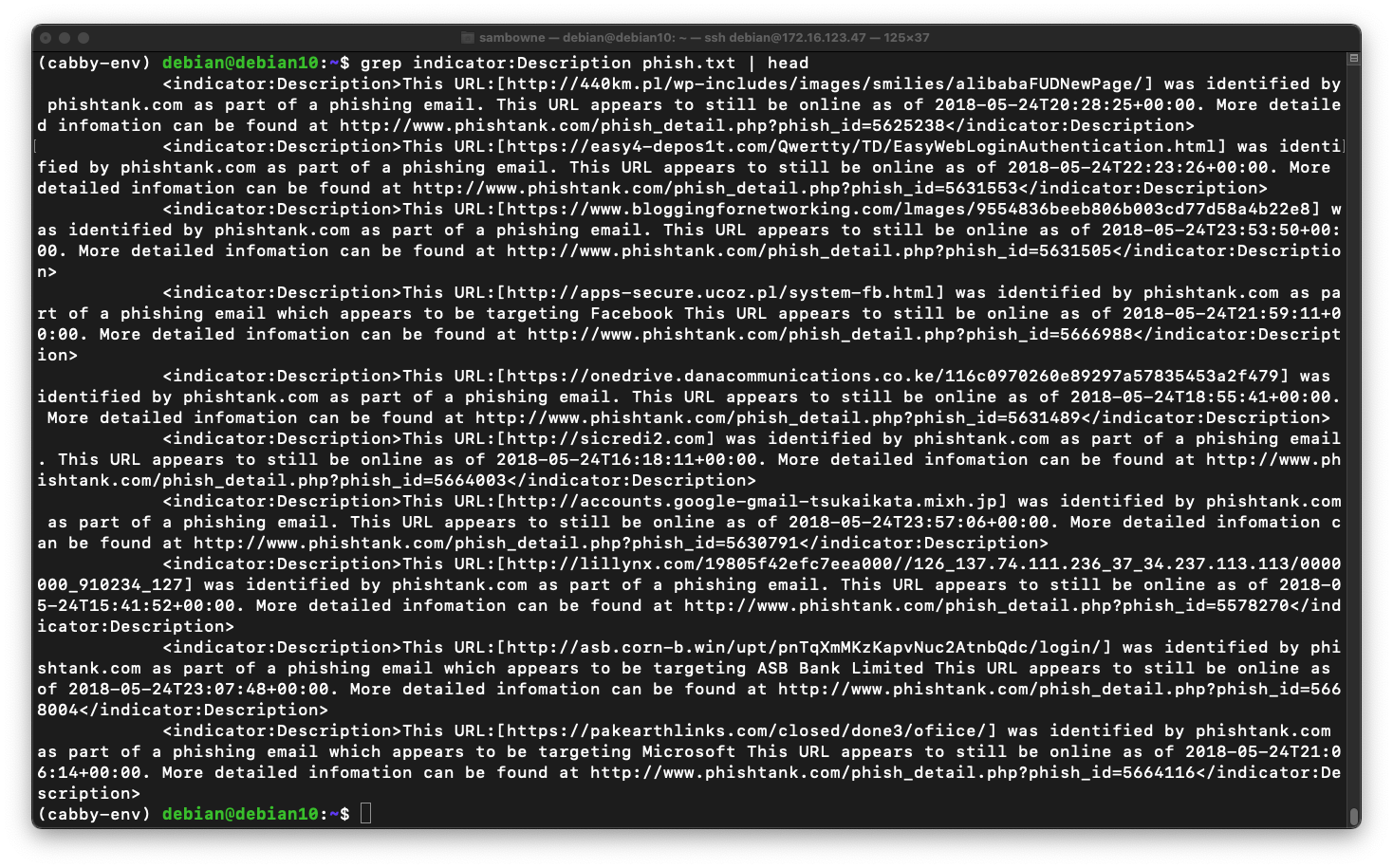
Execute this command to cut the lines at the delimiter "]" and keep only the first field, the text before that delimiter:
grep indicator:Description phish.txt | cut -d "]" -f 1 | head
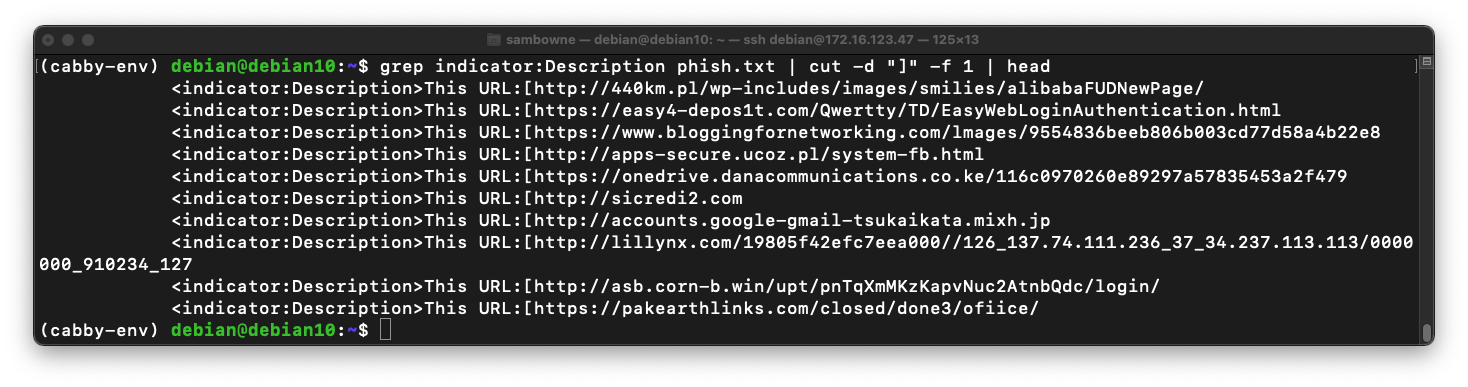
Execute this command to cut the lines at the delimiter "{" and keep only the second field, the text after that delimiter:
grep indicator:Description phish.txt | cut -d "]" -f 1 | cut -d "[" -f 2 | head
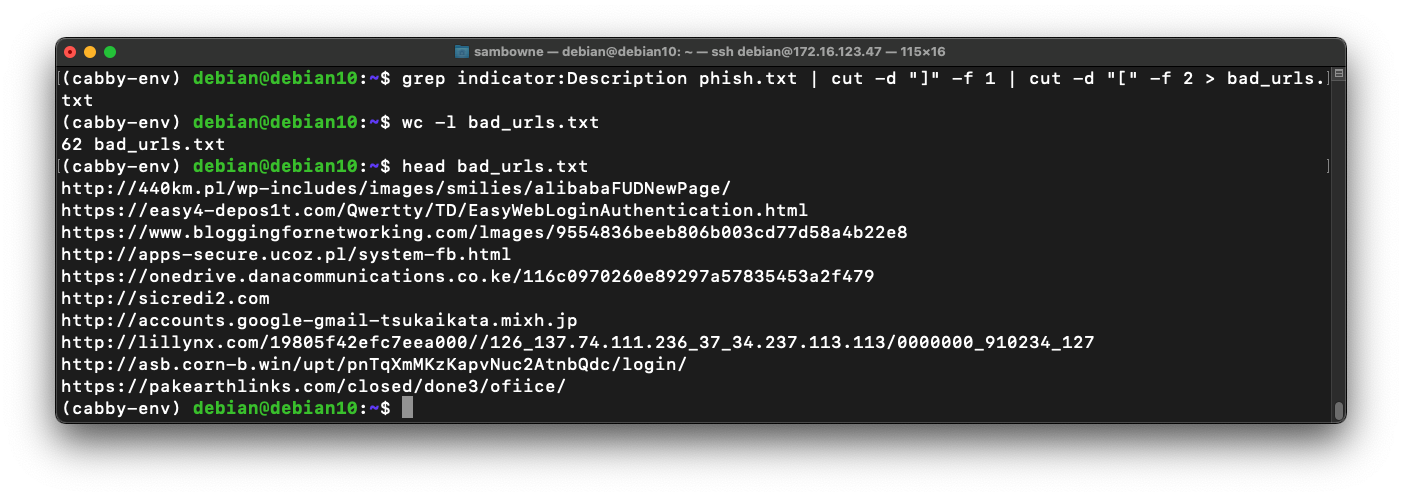
grep indicator:Description phish.txt | cut -d "]" -f 1 | cut -d "[" -f 2 > bad_urls.txt
wc -l bad_urls.txt
head bad_urls.txt

IR 382.1: Folder (10 pts)
One of the bad URLs begins with "organicplus". Find that URL.The flag is covered by a green rectangle in the image below.
IR 382.2: Chill (10 pts)
Poll the phishank for the entire date: Oct 12, 2021.One of the bad URLs contains "chill". The flag is that URL.
IR 382.3: Anomali Feeds (10 pts)
This command finds the services available on the "limo.anomali.com" threat intelligence server.Notice that this server requires you to include the username and password.
Get a list of the collections available from that server. Be careful to use the correct Service Address.Find the name of the feed containing "TOR". That name is the flag.
IR 382.4: C&C (10 pts)
Find the feed on the "limo.anomali.com" server that lists Command & Control servers (abbreviated as "C_C_Server").Find all the servers reported on Oct 12, 2021.
Find the IP address with the lowest number in the first octet. That IP address is the flag.
deactivate
Posted 10-14-21