https://www.microsoft.com/en-us/download/details.aspx?id=52685
Click the red Download button.
Check the box next to vc_redist.x64.exe and click the Next button.
Double-click the file and install the software.
https://yara.readthedocs.io/en/v3.6.0/gettingstarted.html#installing-on-windows
Click the "Download Windows binaries" link.
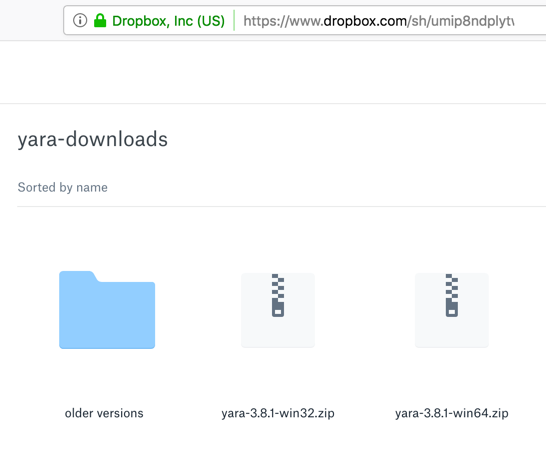
Click the appropriate version for your OS. If you are using Windows Server 2016, it's the 64-bit version, on the right side of the image below.

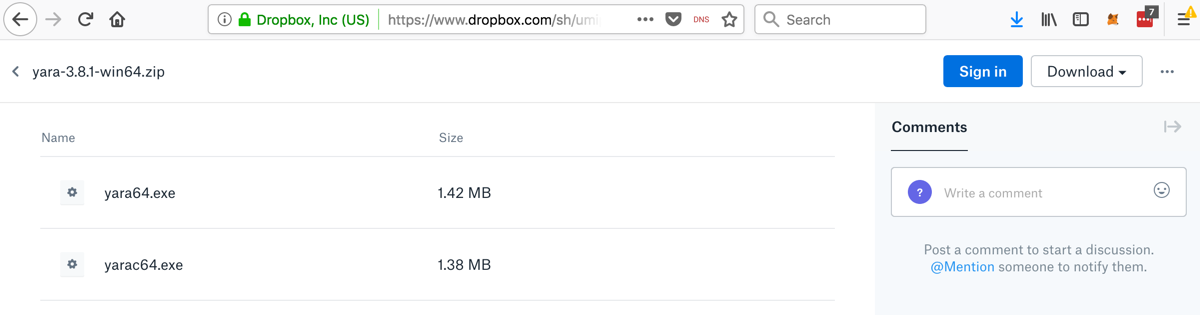
Two files appear, as shown below. On the right side, click Download, "Direct Download". Save the file in your Downloads folder.
Open File Explorer and navigate to your Downloads folder. Right-click the yara file and click "Extract All", Extract.
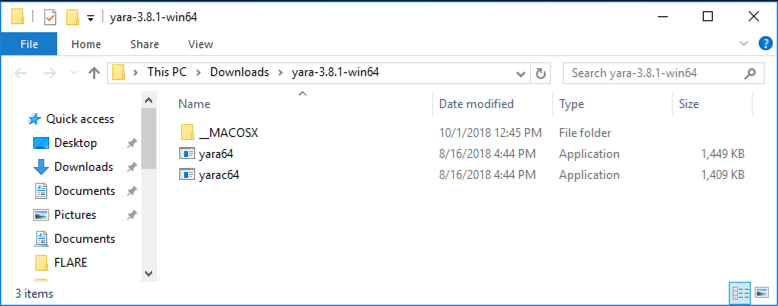
A folder appears containing the two files, as shown below.
Right-click "Command Prompt" and click "Run as Administrator".
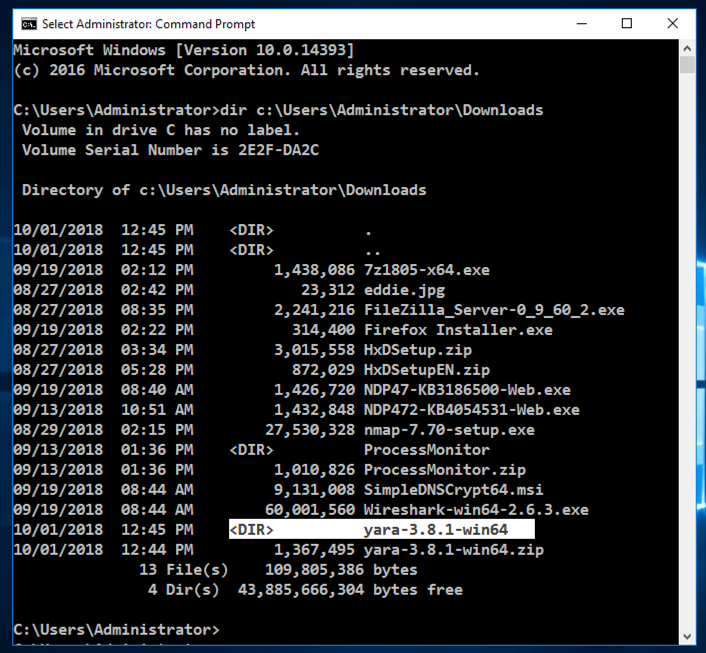
In the Administrator Command Prompt window, execute this command. If you are not logged in as "administrator", you will need to change the path to refer to your actual Downloads folder.
dir c:\users\administrator\downloads\
In the Administrator Command Prompt window, execute these commands. You may need to change the folder name to match the correct folder on your system.
mkdir c:\yara
copy c:\users\administrator\downloads\yara-3.8.1-win64\yara*.* c:\yara
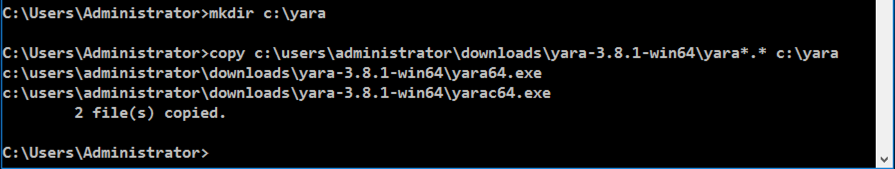
cd c:\yara
notepad test.yar
In Notepad, enter this text, as shown below.
rule ExampleRule
{
strings:
$my_text_string = "EVIL"
condition:
$my_text_string
}
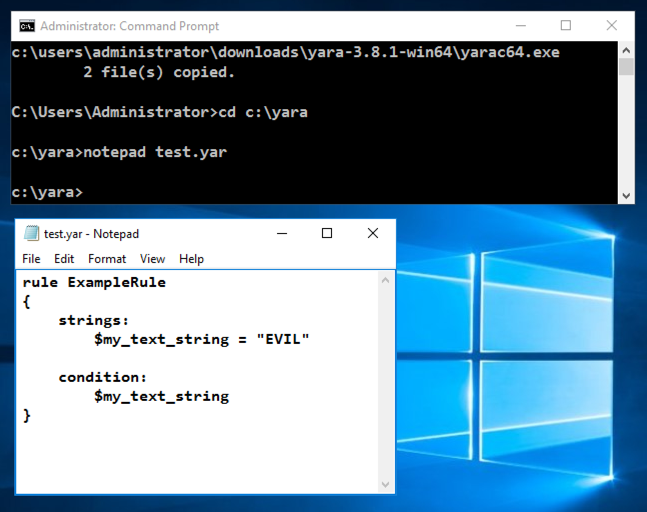
In Notepad, click File, Save.
Close the Notepad window.
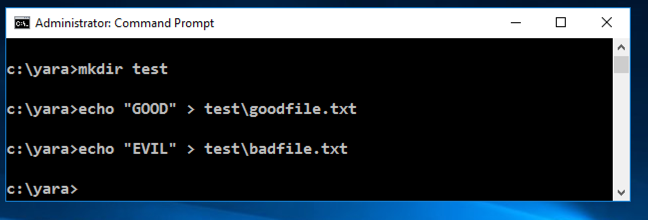
mkdir test
echo "GOOD" > test\goodfile.txt
echo "EVIL" > test\badfile.txt
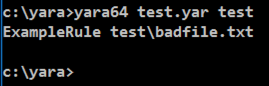
yara64 test.yar test
On your Windows machine, in a Web browser, go to
https://samsclass.info/126/proj/p11mine.htm
Scroll down to the "minesam.exe.zip" link, as shown below.
Right-click minesam.exe.zip and save the file in your Downloads folder.
Open File Explorer and navigate to your Downloads folder. Right-click the minesam.exe.zip file and click "Extract All", Extract.
A folder appears containing a minesam.exe file, as shown below.
https://raw.githubusercontent.com/Yara-Rules/rules/master/Packers/packer_compiler_signatures.yar
A page containing a set of Yara rules to detect executable files and packers opens, as shown below.
Right-click inside the Web page and click "Save Page As.... Save the page in your Downloads folder with its default name, which is packer_compiler_signatures.yar
cd c:\yara
move c:\users\administrator\downloads\minesam.exe\minesam.exe test
move c:\users\administrator\downloads\packer_compiler_signatures.yar .
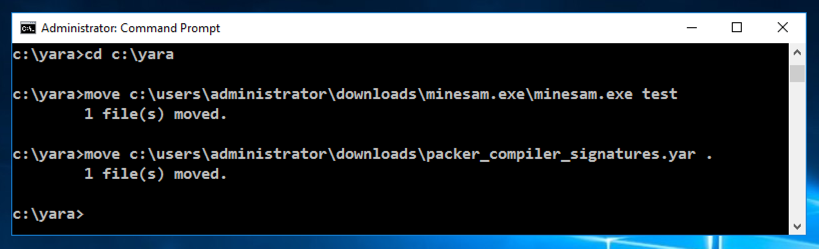
yara64 packer_compiler_signatures.yar test
Unzip it. It contains 100 files with two letter names, such as AA.
Scan those files with Yara and find the files containing "EVIL". Concatenate the filenames and enter them into the form below to record your success.
Scan those files with Yara and find the files containing three bytes of 0x04 in a row.
You may find this document helpful: " Writing YARA rules".
Concatenate the filenames and enter them into the form below to record your success.
Scan those files with Yara and find the files containing this pattern:
Posted 10-1-18
Visual C++ added 10-8-18