http://networking.ringofsaturn.com/Tools/dig.php
If you are using Windows, follow these instructions to install Dig.
If you can't install software on your device (such as iPad users), use this Web-based Dig tool:
http://networking.ringofsaturn.com/Tools/dig.php
dig
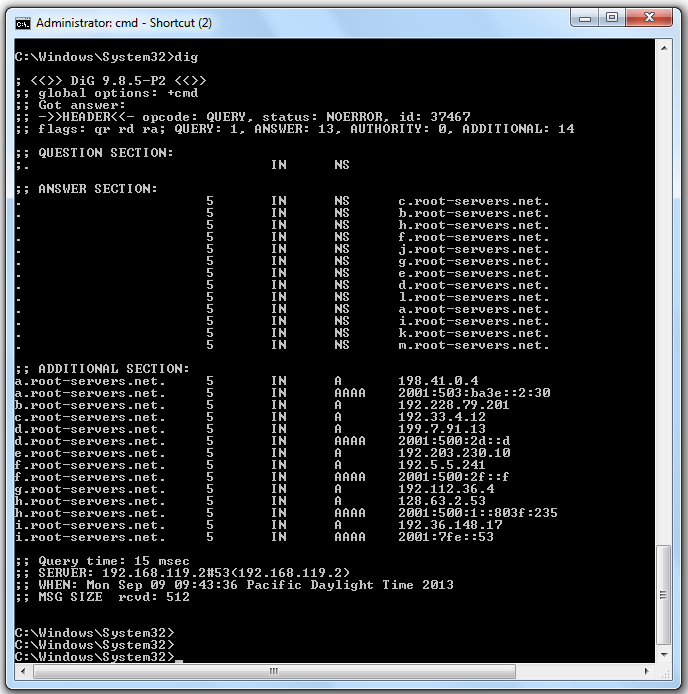
You see the authoritative root servers, as shown below.

The second field is the TTL. This should be a large number of seconds. If you are using VMware, as I did, you may see a lot of "5" values, as shown above. That is a defect of VMware.
The third field contains "IN", indicating that these are Internet records. DNS has the capacity to carry other types of data, but it's almost never used.
The fourth field contains "NS", indicating that these are Name Servers.
In the "ANSWER SECTION", the fifth field contains the names of the authoritative root servers.
In the "ADDITIONAL SECTION", the fifth field contains IP addresses for some of the servers.
At the bottom, this information is shown:
dig @8.8.8.8
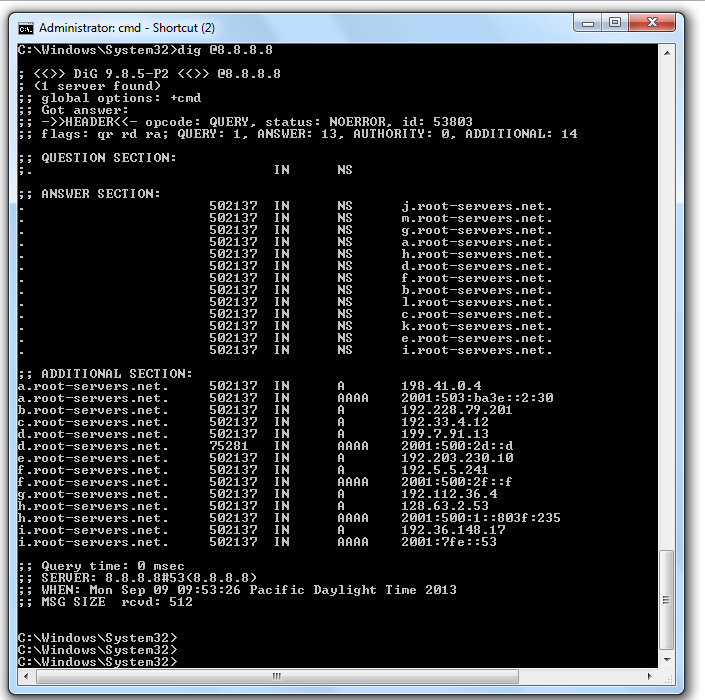
In a Command Prompt window, execute this command:
dig @8.8.8.8
They are counting down to zero.
dig @8.8.8.8 www.ccsf.edu
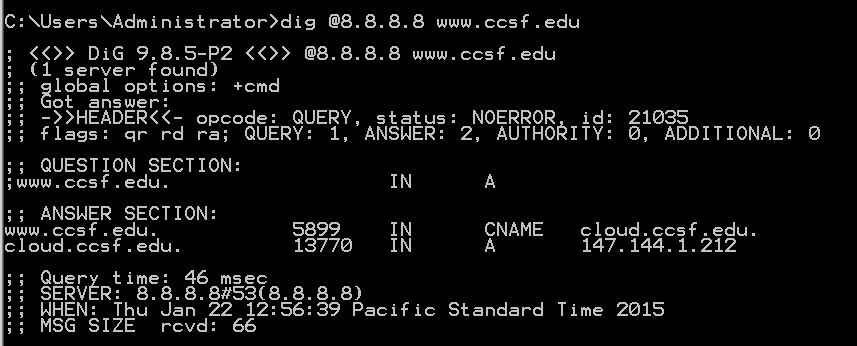
Notice that "QUESTION SECTION" shows
www.ccsf IN AThis indicates that dig performed a default query for the IN A record--the IPv4 internet address of the server.
The "ANSWER SECTION" shows that www.ccsf.edu is a CNAME (an alias).
The real FQDN of CCSF's Web server is "cloud.ccsf.edu".
The ANSWER section also resolves that FQDN, finding the IPv4 address "147.144.1.212".
Finally, in the top section of the response, notice the "flags: qr rd ra" message.
These flags indicate:
dig @ns3.ccsf.edu www.ccsf.edu
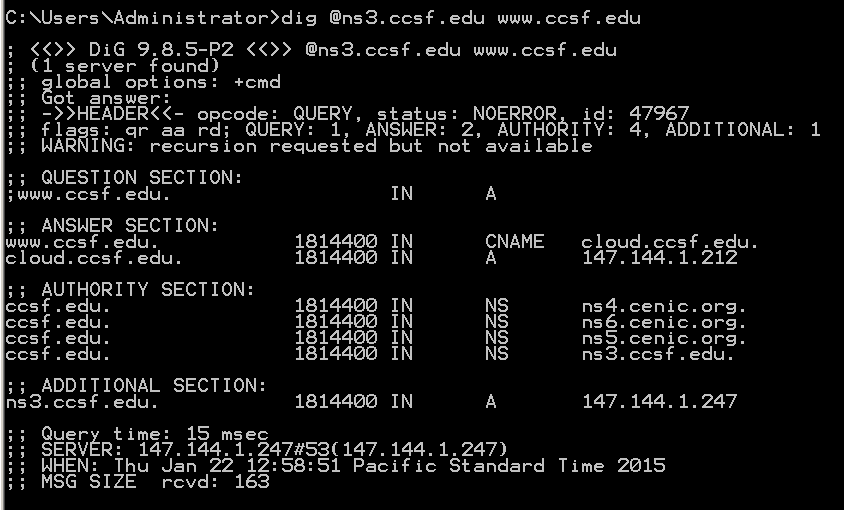
At the top left, notice the "flags: qr aa rd" message. The "aa" indicates that this is an authoritative response for the CCSF domain.
Note: If you are using Starbucks Wi-Fi, you won't see the "aa" flag.
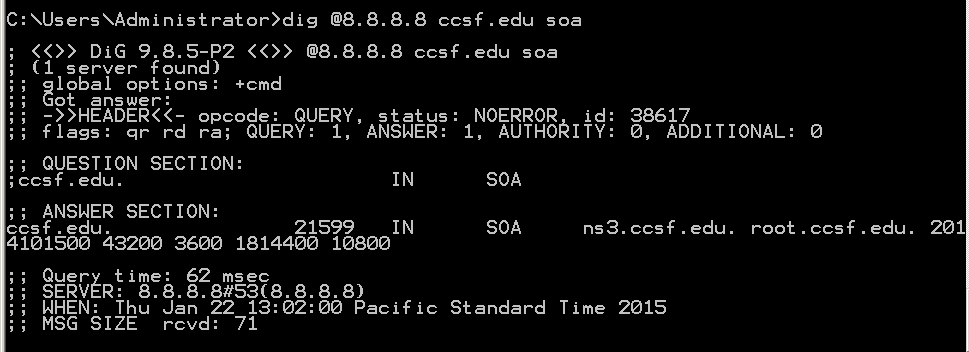
dig @8.8.8.8 ccsf.edu soa
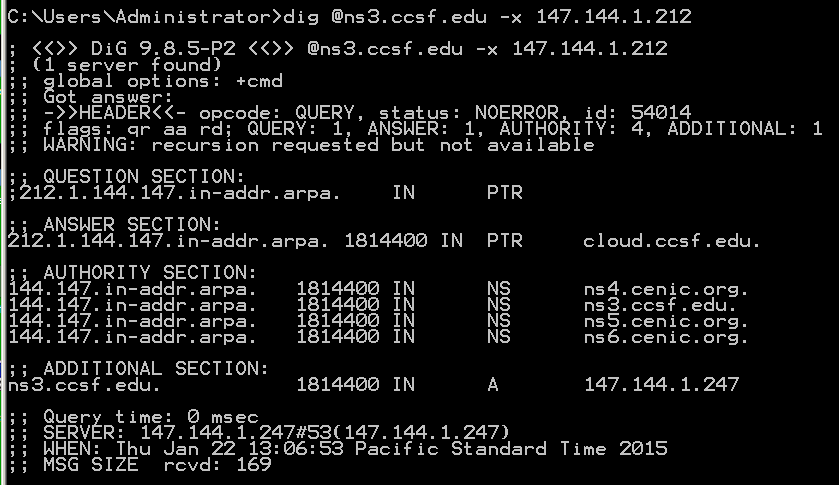
dig @ns3.ccsf.edu -x 147.144.1.212
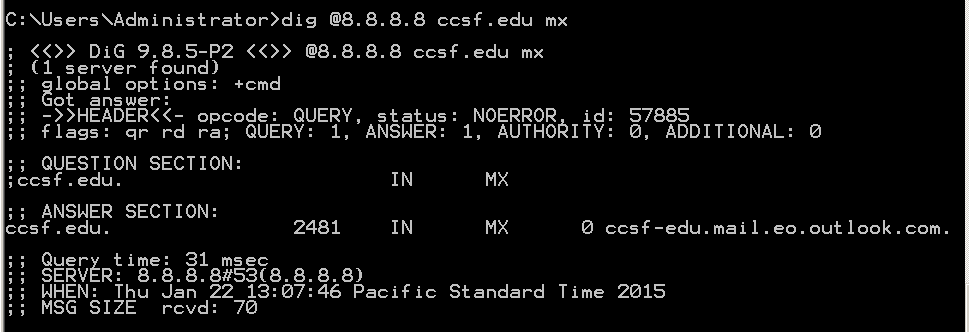
dig @8.8.8.8 ccsf.edu mx
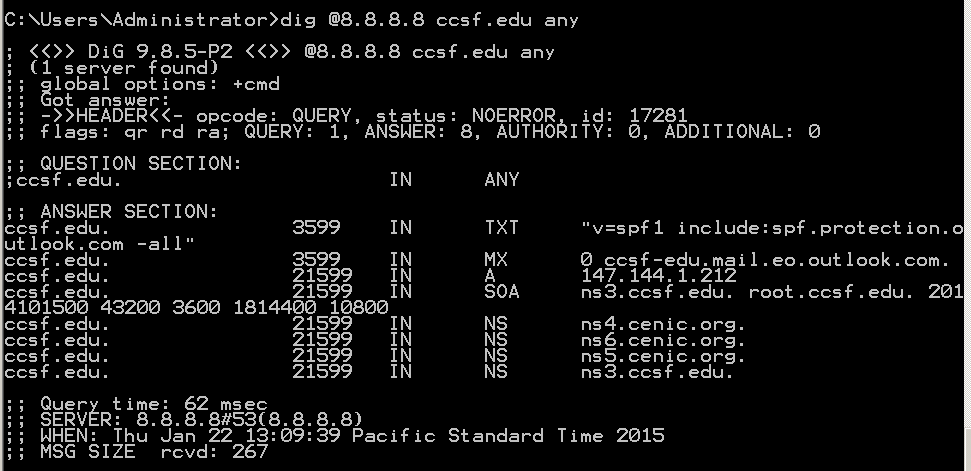
The "any" query finds all records on the server:
dig @8.8.8.8 ccsf.edu any
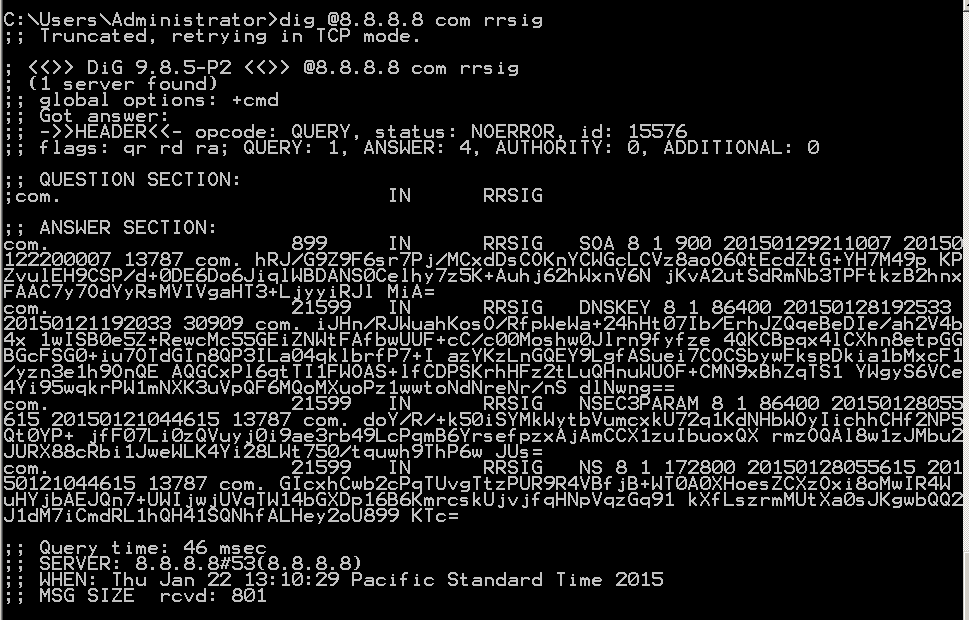
The RRSIG record finds DNSSEC signatures. For example, this query finds the signature of the .com top-level domain:
dig @8.8.8.8 com rrsig
Note: some networks block DNS over TCP. You may need to use this Web-based Dig tool:
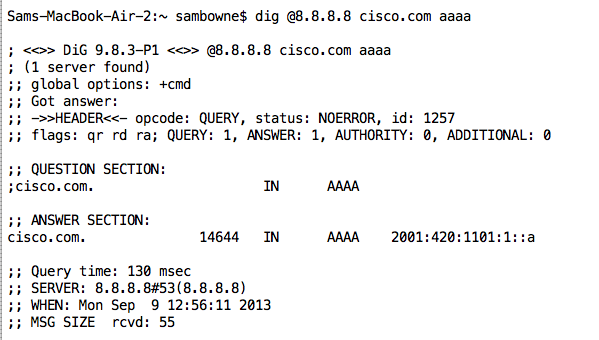
http://networking.ringofsaturn.com/Tools/dig.phpThe AAAA record finds IPv6 addresses, like this query that shows the IPv6 address for cisco.com:
dig @8.8.8.8 cisco.com aaaa
For more types, see http://en.wikipedia.org/wiki/List_of_DNS_record_types
A: What is the SOA for samsclass.info? B: What is the IPv4 address for juniper.com?
C: What is the IPv6 address for google.com?
D: What is the IPv4 address for sans.org, obtained from an authoritative server? Your screen image must show the "aa" flag.
E: How many records are signed at ietf.org?
Note: Questions D and E may require you to use this Web-based Dig tool, if the network you are using is filtered:
http://networking.ringofsaturn.com/Tools/dig.php
Attach the images. Send it to: cnit.40@gmail.com with a subject line of "Proj 3 From YOUR NAME", replacing "YOUR NAME" with your real name.
Send a Cc to yourself.
Grading note: For each item, the image is worth 3 pts. and the answer is worth 2 pts.