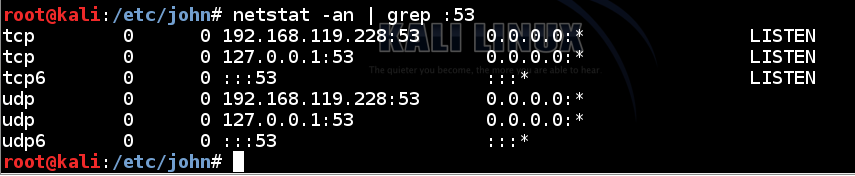
netstat -an | grep :53

In a Terminal window, execute the following command:
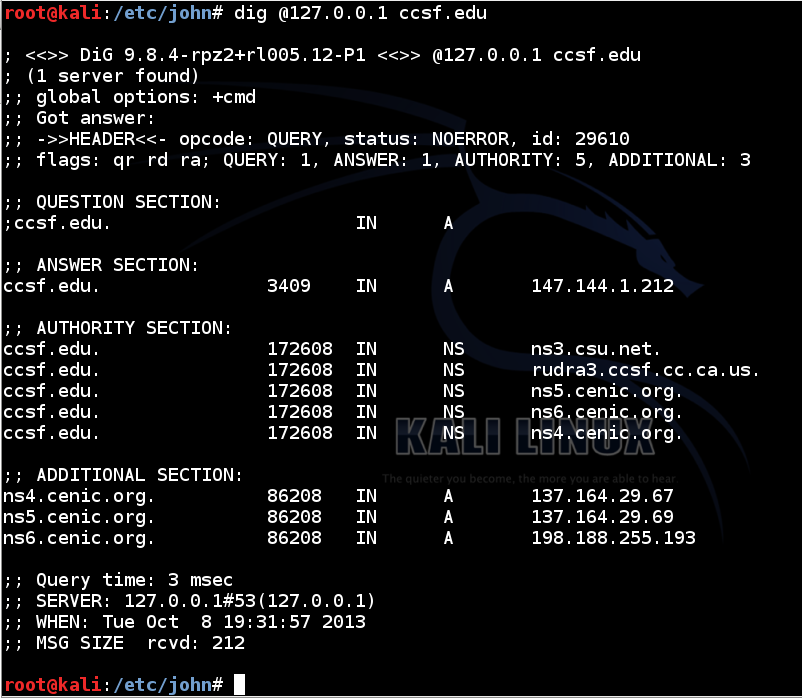
dig @127.0.0.1 ccsf.edu
You should see a non-authoritative answer of 147.144.1.212, as shown below.
wireshark
We laugh at danger. Click OK.
On the left side, click your eth0. Click Start.
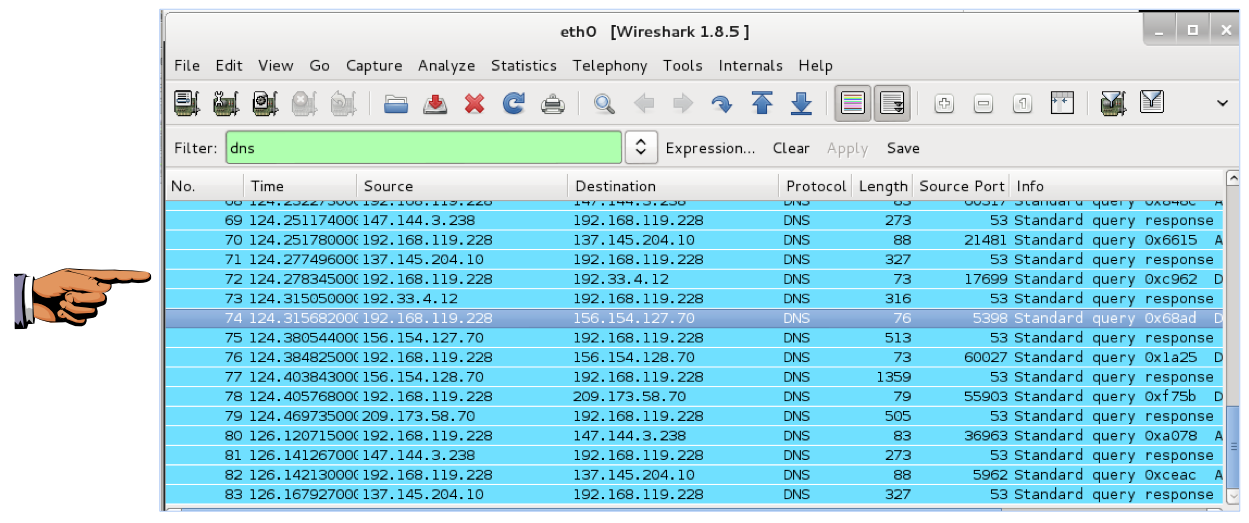
In the "Filter" bar, type dns and press Enter.
dig @127.0.0.1 attack.samsclass.info
dig @127.0.0.1 fog.ccsf.edu
dig @127.0.0.1 ftp.ccsf.edu
Look in the Info column, on the right side, and click a "Standard query..." packet.
In the middle pane, expand the "User Datagram Protocol..." line.
Right-click "Source port..." and click "Apply as Column", as shown below.
If necessary, scroll up until you find several "Standard query" packets. The Source Port for each packet should be visible as a column.
On Kali Linux, the ports are random, as shown below (ignore the port 53 values). Random ports are much more secure, making cache poisoning very difficult.
Click the taskbar at the bottom of your host computer's desktop, to make the host machine listen to the keyboard, instead of the virtual machine.
Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-DESKTOP IMAGE FOR FULL CREDIT!
On the host machine, not the virtual machine, click Start.
Type mspaint into the Search box and press the Enter key.
Click in the untitled - Paint window, and press Ctrl+V on the keyboard. The desktop appears in the Paint window.
In the upper left corner of the "untitled - Paint" window, click the little blue square icon (it looks like a floppy disk, something people used to use long ago--you might never have seen one).
Save the document with the filename "YOUR NAME Proj 3x", replacing "YOUR NAME" with your real name.
Send a Cc to yourself.