This is such a serious security flaw that the FTC punished Fandango and Credit Karma for doing the same thing in 2014.
From the Android home screen, click the circle at the bottom center.
Open Settings.
In Settings, click "Network & internet".
Click Wi-Fi.
Click AndroidWiFi.
Click Advanced.
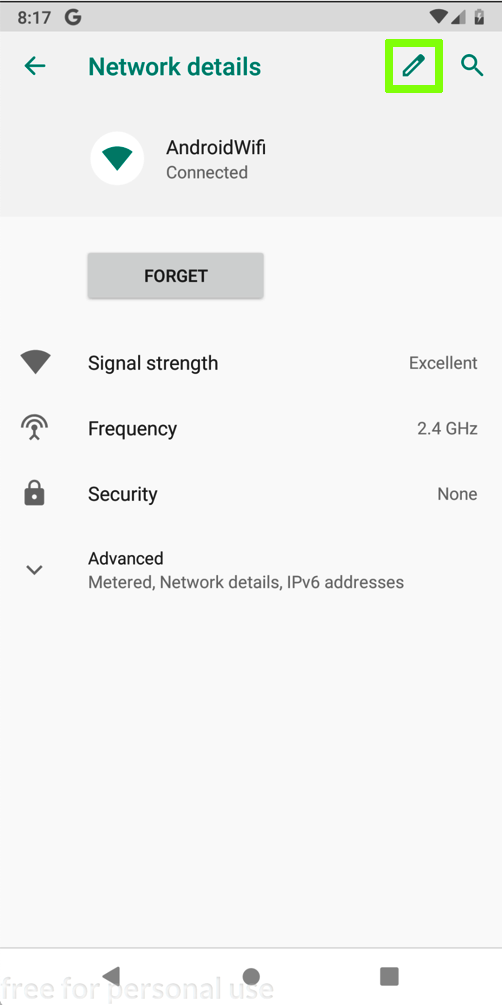
In the "Network details" screen, at the top right, click the Pencil icon.
In the "Proxy" field, click the down-arrow.
Click None.
Then click Save.
Install the app, as shown below.
If you can't get the app from Google Play, download my archived copy.

Click Wi-Fi.
Click AndroidWiFi.
Click Advanced.
In the "Network details" screen, at the top right, click the Pencil icon, outlined in green in the image below.
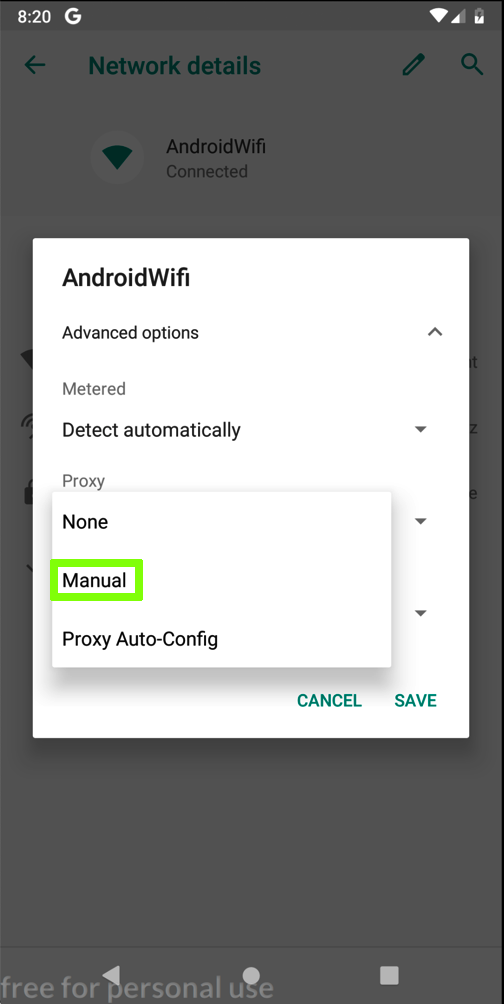
In the "AndroidWifi" box, in the "Advanced options" row, click the down-arrow.
In the "Proxy" field, click the down-arrow.
Click Manual, which is outlined in green in the image below.
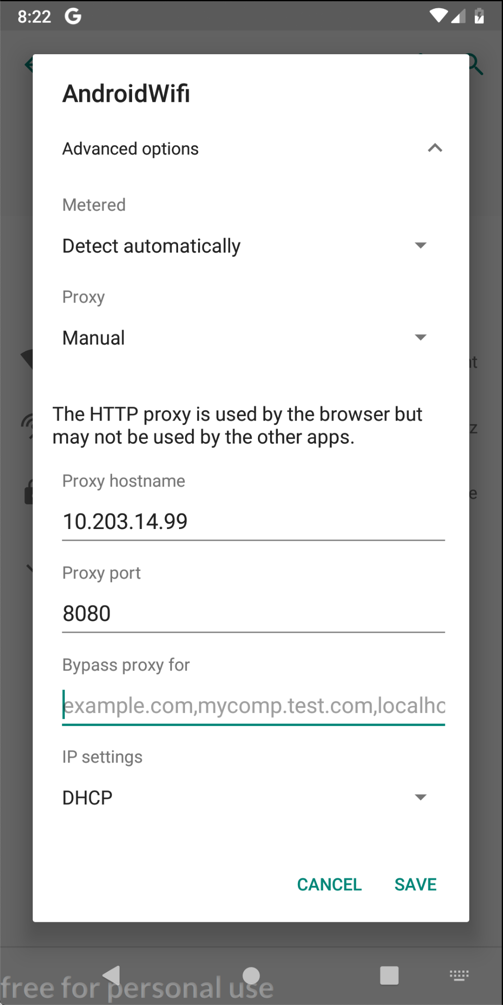
Enter the IP address and port number of the Burp proxy listener, as shown below.
On your Android device, click SAVE.
At the bottom center of the device, click the round Home button.
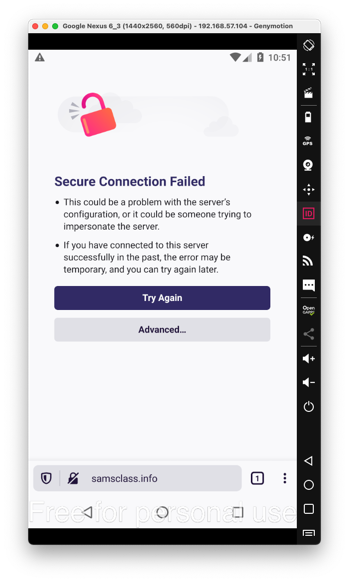
You should see an error message, as shown below. If you don't, remove the Portswigger certificate, with the steps in the gray box below.
This happens because Burp is performing a man-in-the-middle attack and Firefox notices it.
Removing the PortSwigger Certificate
On your Android device, in Settings, click "Security & location",
Advanced, "Encryption & credentials", "Clear credentials".Click OK.
Enter your PIN.
At the lower right of the home page, click the head icon.
Click the "Sign In or Sign Up" button.
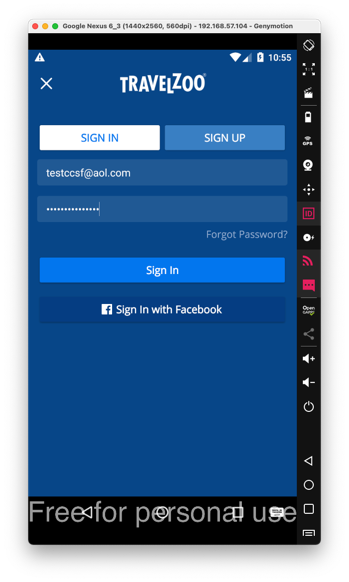
Click the "SIGN IN" button.
Enter an email address and password, as shown below, and click the "Sign In" button.
In Burp, on the Proxy tab, click the "HTTP Requests" sub-tab.
Find the POST method going to travelzoo.com.
The username and password appear in Burp, as shown below:
M 109.1: Parameter Name (10 pts)
Find the text covered by a green box in the image below. That's the flag.
If you can't get the app from Google Play, download my archived copy.
Enter any email and click the Next button.
Enter any password and click the "Sign In" button.
M 109.2: Server Name (10 pts)
In Burp, find the text covered by a green box in the image below. That's the flag.
If you can't get the app from Google Play, download my archived copy.
Launch Somnote. If it asks for permissions, grant them.
Click "LOGIN WITH EMAIL", and enter any email and password, and click the Login button.
M 109.3: Parameter Name (10 pts)
In Burp, find the text covered by a green box in the image below. That's the flag.