The companies that make these apps were been notified long ago by CERT of this problem, but have failed to update their apps. This, in my opinion, makes them fair game for public humiliation.
Here are details of the CERT test and notification, from 9/3/2014:
Finding Android SSL Vulnerabilities with CERT Tapioca
This spreadsheet from CERT shows many vulnerable apps.
Android apps that fail to validate SSL
Here we will perform a very simple MITM attack using the Burp proxy and an untrusted certificate.
In a sane world, we'd have to use a special, poorly-written test app to demonstrate such a serious vulnerability. However, we'll use a real app, from a company that was warned long ago about this by CERT and who just ignored the warning and continued to endanger their customers.
This page should load without any error messages. If you see errors saying the certificate is untrusted, install the PortSwigger certificate as explained in project 1x.

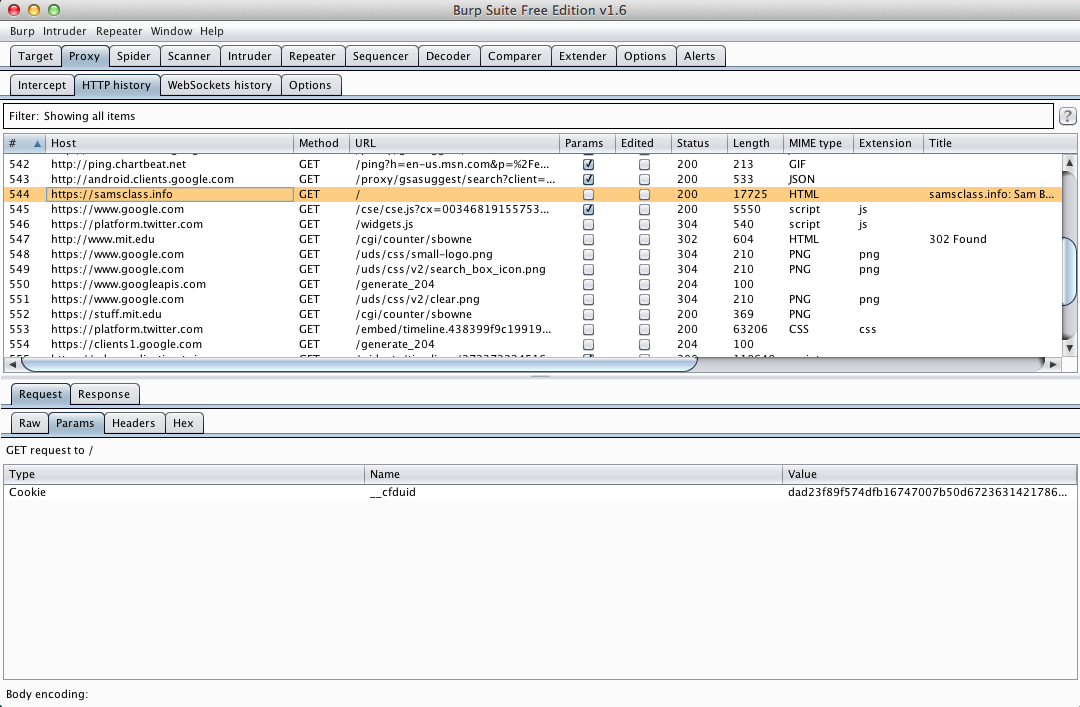
In Burp, on the Proxy tab, on the "HTTP history" sub-tab, you should see https://samsclass.info, as shown below.
Troubleshooting
If you see no HTTP history entries at all, check Project 1x for the instructions to set a proxy server inside Genymotion.If you see some HTTP history entries, but not https://samsclass.info, make sure the "Filter" bar near the top of the Burp HTTP History window shows the "Showing all items" message. If it does not, click it and click the "Show all" button.
When I prepared this project, "Snap Secure" was vulnerable. However, in response to publicity about this class project, they fixed their app.
So choose one of these apps to install instead:
Start the app. Log in.
Enter these fake credentials, replacing "YOURNAME" with your own name. Don't use any spaces in your name.:
The credentials are rejected, which is OK--what matters for us is how they were transmitted to the server.
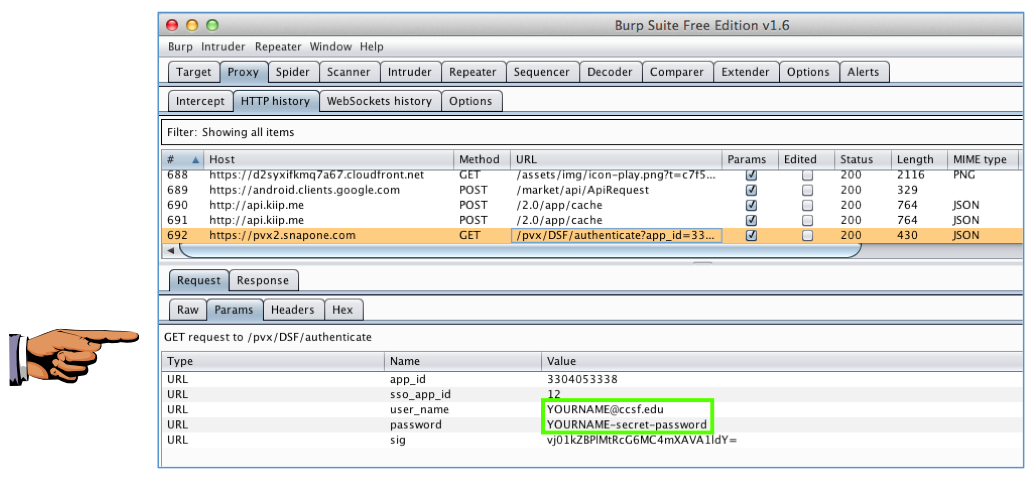
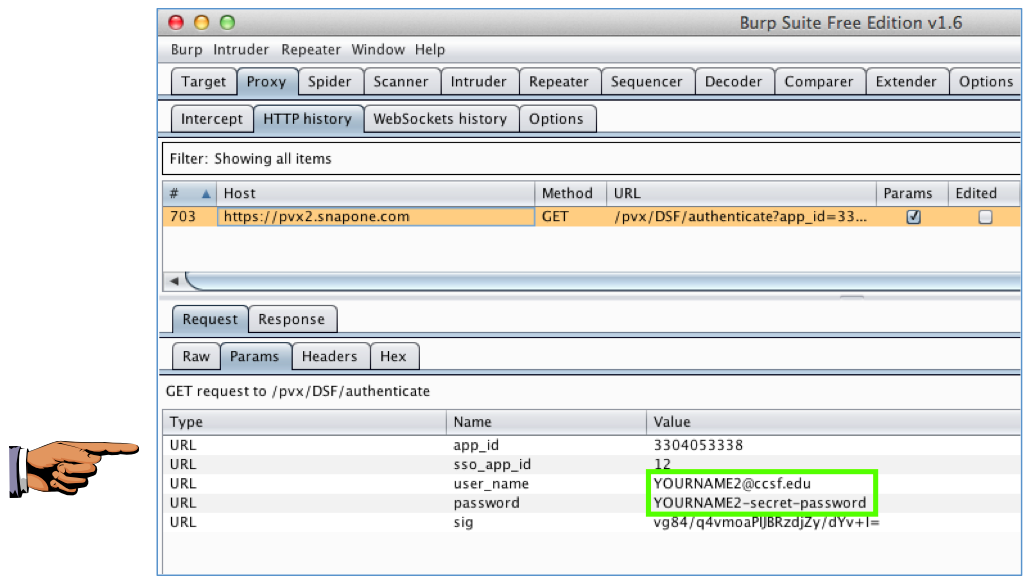
In Burp, examine the HTTP History. You should find a GET request to a snapone.com server containing your username and password, as shown below.
This is normal HTTPS interception by a trusted proxy, and does not demonstrate any security problem.
YOU MUST SUBMIT A FULL-DESKTOP IMAGE FOR FULL CREDIT
Save a screen image with the filename Proj 11xa from Your Name.
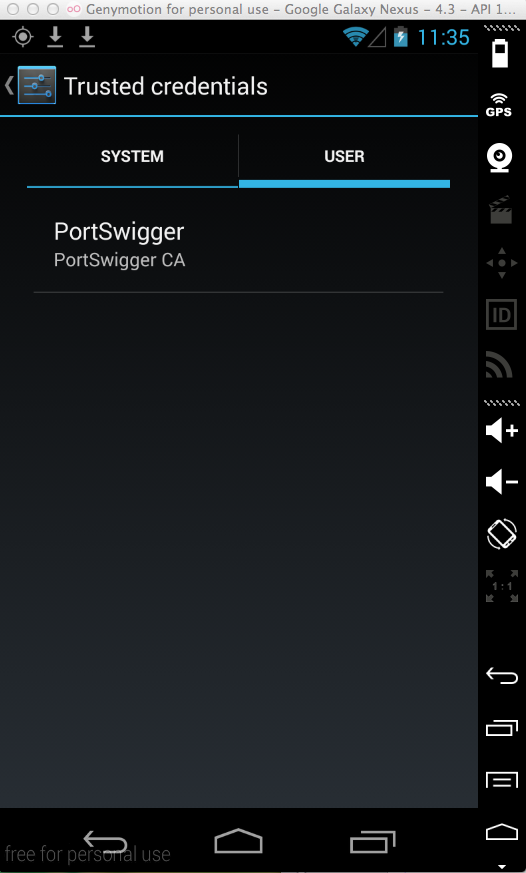
The PortSwigger certificate appears, as shown below.
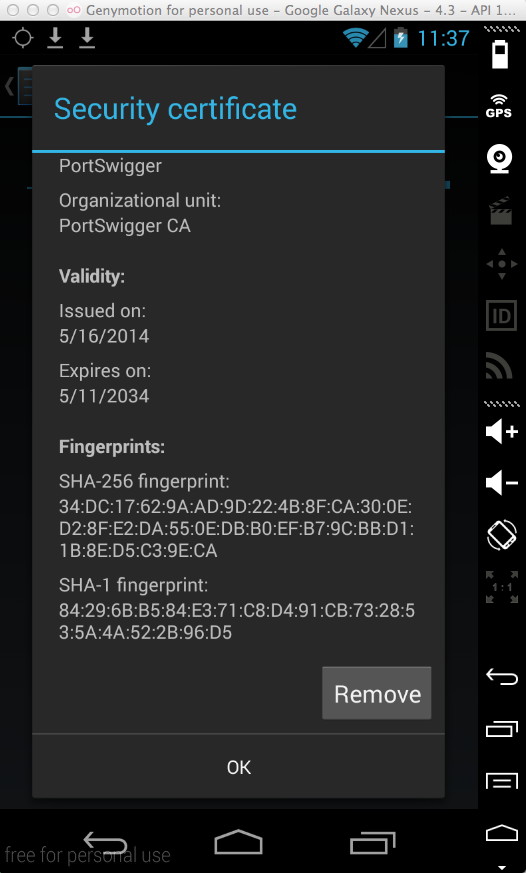
Click PortSwigger. A "Security certificate" page opens.
Scroll to the bottom and click the Remove button, as shown below. Click OK.
Click Home. Open the Web browser. In the URL bar, retype https://samsclass.info and press Enter.
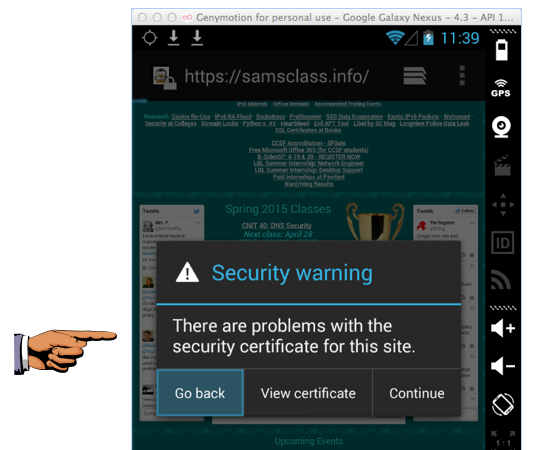
A "Security warning" box appears, as shown below. This indicates that the browser is properly implementing SSL security and detecting the MITM attack that Burp is performing.
In the Genymotion device, in the vulnerable app, sign in again, using these credentials, replacing "YOURNAME" with your own name. Don't use any spaces in your name.:
This is VERY WRONG. Burp is intercepting and opening HTTPS traffic with an untrusted certificate, and the app is ignoring it.
YOU MUST SUBMIT A FULL-DESKTOP IMAGE FOR FULL CREDIT
Save a screen image with the filename Proj 11xc from Your Name.
Email the image to cnit.128sam@gmail.com with a Subject line of Proj 11x from Your Name.
Android apps that fail to validate SSL